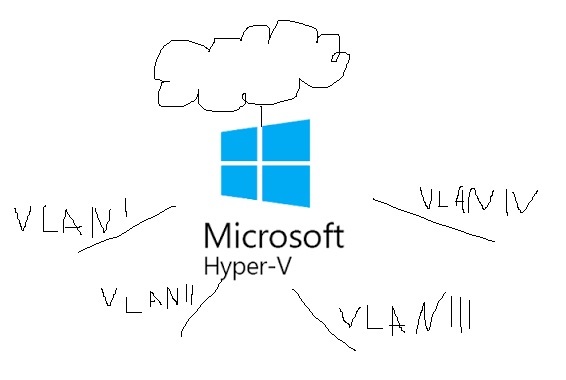
Gateway Virtualization with Hyper-v
After the comrade's stories about the burned-down router and the subsequent facac, it was decided to protect themselves from such situations by creating a backup gateway. Since the financing of it in my current company is not in the top ten of the most important things for the management, we will use virtual machines with Ubuntu 14.04 LTS for Hyper-v as gateways, and 2 hardware assembled from shit and sticks , as iron what was in stock. This was said not in order to hear words of sympathy, but in order to emphasize that it does not require much funding to create a reservation for the main gateway.
Iron Requirements:
- processor with support for virtualization and x64
- 2 network cards with 802.1q support
Imagine that we already have a system builder with installed windows hyper-v server 2012 r2 and a second-generation virtual machine. Let's start with the hyper-v host settings.
')
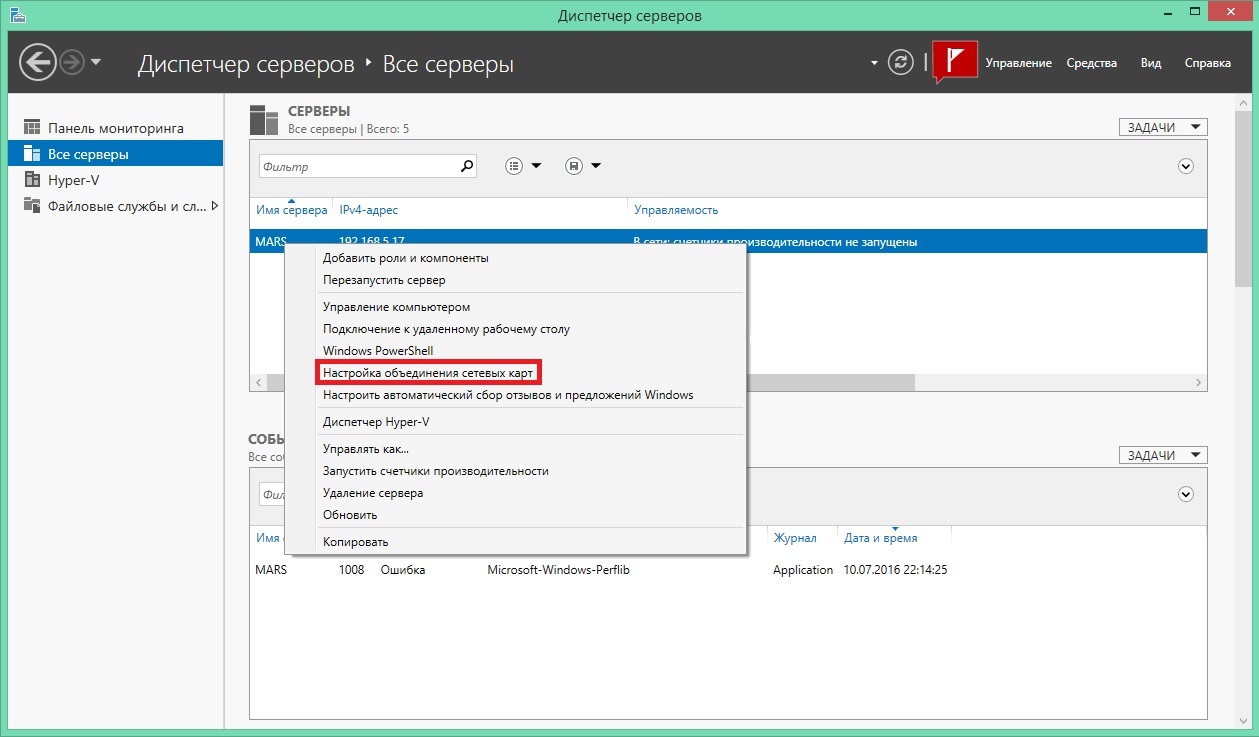
The first step is to configure the union network cards. Open the Server Manager snap-in, right-click on our server and select "Networking pooling configuration":
all manipulations with snap windows are carried out under windows 8.1
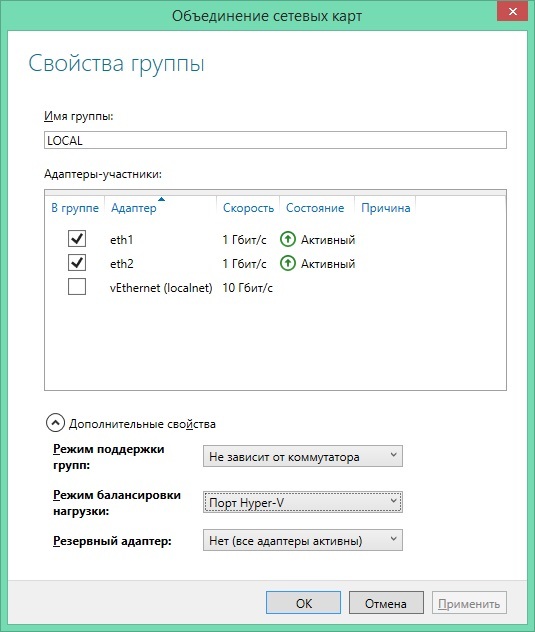
Settings may vary by infrastructure. Card merging is done to make the gateway available in the event of a network card or switch failing.
Next, create virtual switches for the local network and the Internet. This can be done via the hyper-v dispatcher snap-in or via powershell.
Open the snap-in, select our server, and in the right-hand part of the snap-in click “virtual switch manager”. We need to create 2 external virtual switches.
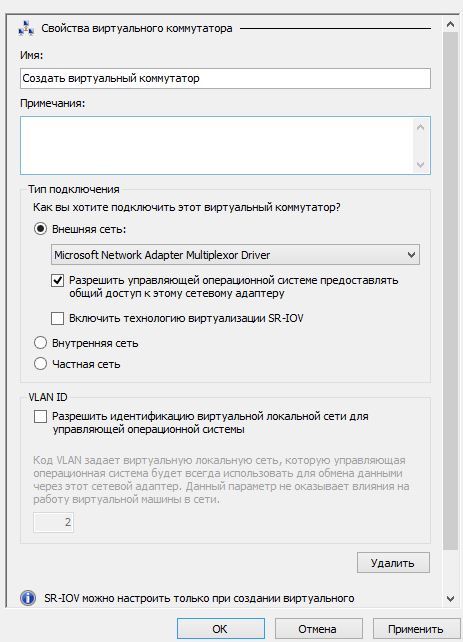
Assign a name to the switch and select the appropriate network cards. Microsoft networkadapter multiplexor driver - our united network card. There are cases when network cards are called the same and they differ only in the number at the end. To determine compliance, you can use the powershell cmdlet get-netadapter and determine the card by mac address or up-down status. For the virtual switch of the Internet, uncheck the "allow the control operating system ..." option, for the local network we reserve, of course, if you do not have a separate network card to control the hypervisor. This option is required so that the hypervisor operating system can use this network card to access the network.
You can also create a virtual switch via powershell's new-vmswitch cmdlet.
Next, you need to create network adapters for our virtual machine. Via a snap-in, or powershell cmdlet add-vmnetworkadapter.
Creating a network adapter is easy and, I think, does not require a description. If your network uses VLANs, then you need to configure the interfaces for each network. This can be done in several ways:
The first method is not for us, because in the server core version and I was unable to open these settings in graphical mode, and manually editing the registry can break something. And if I'm not mistaken, this method is not recommended by Microsoft itself.
The second method is convenient and simple. We can create the number of network adapters we need and specify the vlan we need in the settings.
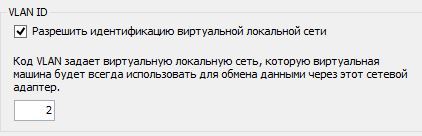
The only thing that this method is inconvenient for, when a new vlan appears, the addition of a network adapter is possible only when the virtual machine is turned off.
The third way suits us all. On it and stop.
In order for traffic from all vlans that we want to route, we need to configure the trunk on the network interface card of the virtual machine. This can be done only through powershell.
It so happened that when I got a job, only 1 vlan was used on the network, and all the equipment that was on the network, including the server and the PC, went without a tag. When setting up a trunk, I could not understand for a long time why untagged traffic does not reach my virtual machine until I came across a post in which I saw the powershell command with vlan 0, therefore 0 is specified as the native vlan.
Next, we need to configure the virtual machine.
Let's start with the addressing.
Example file / etc / network / interfaces
further allow our virtual machine to do forwarding. Change the value of net.ipv4.ip_forward to 1 in the /etc/sysctl.conf file and apply the changes by executing the sysctl -p /etc/sysctl.conf command.
And the final touch is to configure nat with iptables.
where xxx.xxx.xxx.xxx is your ip address. Although in my case dhcp is used, the external address is always assigned to one.
For dynamic addresses, use
In order to keep iptables rules after a reboot, install the iptables-persistent package. The name may differ depending on the distribution.
Now users have access to the Internet and everything works, it remains only to set up replication. This is done through the same hyper-v dispatcher snap-in. Open the snap-in, select our hypervisor and go to the hyper-v parameters through the action panel. In the parameters, select the configuration of replication. Further details:
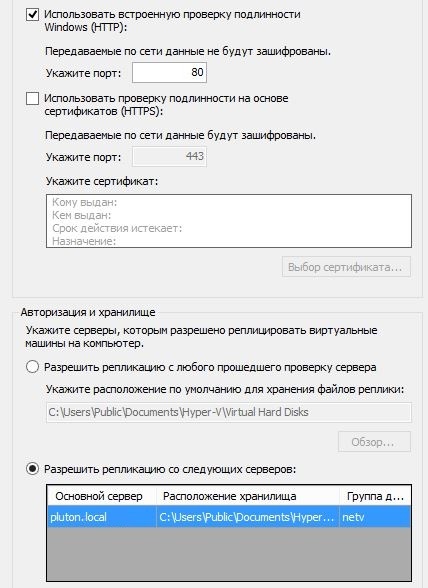
Turn on the cue.
Use Integrated Windows Authentication - less secure. It works only in the active directory domain and does not require additional settings.
Using certificate based verification (HTTPS) is more secure. Use it in paranoia mode and outside the domain.
You can allow replication from all hyper-v servers or from specified servers only. We choose the second option and indicate there a server replica with hyper-v installed. A group can have an arbitrary name. Next, do the same settings on the server replica.
To avoid a problem when switching to a server replica, virtual switches should be named the same as on the main server.

Iron Requirements:
- processor with support for virtualization and x64
- 2 network cards with 802.1q support
Imagine that we already have a system builder with installed windows hyper-v server 2012 r2 and a second-generation virtual machine. Let's start with the hyper-v host settings.
')
The first step is to configure the union network cards. Open the Server Manager snap-in, right-click on our server and select "Networking pooling configuration":

all manipulations with snap windows are carried out under windows 8.1

Settings may vary by infrastructure. Card merging is done to make the gateway available in the event of a network card or switch failing.
Next, create virtual switches for the local network and the Internet. This can be done via the hyper-v dispatcher snap-in or via powershell.
Open the snap-in, select our server, and in the right-hand part of the snap-in click “virtual switch manager”. We need to create 2 external virtual switches.

Assign a name to the switch and select the appropriate network cards. Microsoft networkadapter multiplexor driver - our united network card. There are cases when network cards are called the same and they differ only in the number at the end. To determine compliance, you can use the powershell cmdlet get-netadapter and determine the card by mac address or up-down status. For the virtual switch of the Internet, uncheck the "allow the control operating system ..." option, for the local network we reserve, of course, if you do not have a separate network card to control the hypervisor. This option is required so that the hypervisor operating system can use this network card to access the network.
You can also create a virtual switch via powershell's new-vmswitch cmdlet.
Next, you need to create network adapters for our virtual machine. Via a snap-in, or powershell cmdlet add-vmnetworkadapter.
Creating a network adapter is easy and, I think, does not require a description. If your network uses VLANs, then you need to configure the interfaces for each network. This can be done in several ways:
- creating virtual interfaces at the hypervisor host level
- creating interfaces at the virtual machine level
- creating subinterfaces at the virtual machine level
The first method is not for us, because in the server core version and I was unable to open these settings in graphical mode, and manually editing the registry can break something. And if I'm not mistaken, this method is not recommended by Microsoft itself.
The second method is convenient and simple. We can create the number of network adapters we need and specify the vlan we need in the settings.
The only thing that this method is inconvenient for, when a new vlan appears, the addition of a network adapter is possible only when the virtual machine is turned off.
The third way suits us all. On it and stop.
In order for traffic from all vlans that we want to route, we need to configure the trunk on the network interface card of the virtual machine. This can be done only through powershell.
Set-VMNetworkAdapterVlan -Trunk -AllowedVlanIdList "100" -VMName "router" -VMNetworkAdapterName "localnet" -NativeVlanId 0 It so happened that when I got a job, only 1 vlan was used on the network, and all the equipment that was on the network, including the server and the PC, went without a tag. When setting up a trunk, I could not understand for a long time why untagged traffic does not reach my virtual machine until I came across a post in which I saw the powershell command with vlan 0, therefore 0 is specified as the native vlan.
Next, we need to configure the virtual machine.
Let's start with the addressing.
Example file / etc / network / interfaces
# The loopback network interface auto lo iface lo inet loopback auto eth0 iface eth0 inet static address 192.168.0.1 netmask 255.255.255.0 # 100 vlan auto eth0.100 iface eth0.100 inet static address 192.168.100.1 netmask 255.255.255.0 vlan_raw_device eth0 #internet auto eth1 iface eth1 inet dhcp further allow our virtual machine to do forwarding. Change the value of net.ipv4.ip_forward to 1 in the /etc/sysctl.conf file and apply the changes by executing the sysctl -p /etc/sysctl.conf command.
And the final touch is to configure nat with iptables.
iptables -t nat -A POSTROUTING -o eth1 -j SNAT --to-source xxx.xxx.xxx.xxx where xxx.xxx.xxx.xxx is your ip address. Although in my case dhcp is used, the external address is always assigned to one.
For dynamic addresses, use
iptables -t nat -A POSTROUTING -o eth1 -j MASQUERADE In order to keep iptables rules after a reboot, install the iptables-persistent package. The name may differ depending on the distribution.
Now users have access to the Internet and everything works, it remains only to set up replication. This is done through the same hyper-v dispatcher snap-in. Open the snap-in, select our hypervisor and go to the hyper-v parameters through the action panel. In the parameters, select the configuration of replication. Further details:

Turn on the cue.
Use Integrated Windows Authentication - less secure. It works only in the active directory domain and does not require additional settings.
Using certificate based verification (HTTPS) is more secure. Use it in paranoia mode and outside the domain.
You can allow replication from all hyper-v servers or from specified servers only. We choose the second option and indicate there a server replica with hyper-v installed. A group can have an arbitrary name. Next, do the same settings on the server replica.
To avoid a problem when switching to a server replica, virtual switches should be named the same as on the main server.
Source: https://habr.com/ru/post/305388/
All Articles