ThinkPwn vulnerability in computer firmware was more serious than it seemed before
A few days ago, we wrote about the 0day Local Privilege Escalation (LPE) vulnerability in the UEFI firmware of Lenovo ThinkPad notebooks, which was the subject of an interesting study of the security recorder under the nickname Cr4sh. The demonstrated exploitation vector of the vulnerability allows you to disable the built-in hardware protection called SPI Protected Ranges, which is used to protect the chip's SPI flash-memory from data recording. The vulnerability itself is present in one of the UEFI firmware drivers called SystemSmmRuntimeRt and allows you to execute arbitrary privileged SMM code in the system.

In turn, Lenovo issued a security notification in which it indicated that it did not develop the vulnerable driver, as it requests the manufacturers of BIOS / UEFI firmware, which, in turn, use the operating time of Intel and AMD. After that, it became clear that the range of laptops and computers vulnerable to ThinkPwn is not limited to Lenovo. Although, apart from Lenovo, none of the manufacturers of computers and motherboards mentioned the vulnerability, it became known that Hewlett-Packard Pavilion notebooks, computers with motherboards from GIGABYTE (Z68-UD3H, Z77X-UD5H, Z87MX-D3H, and others) were susceptible to it, Fujitsu LIFEBOOK laptops, as well as Dell.
')
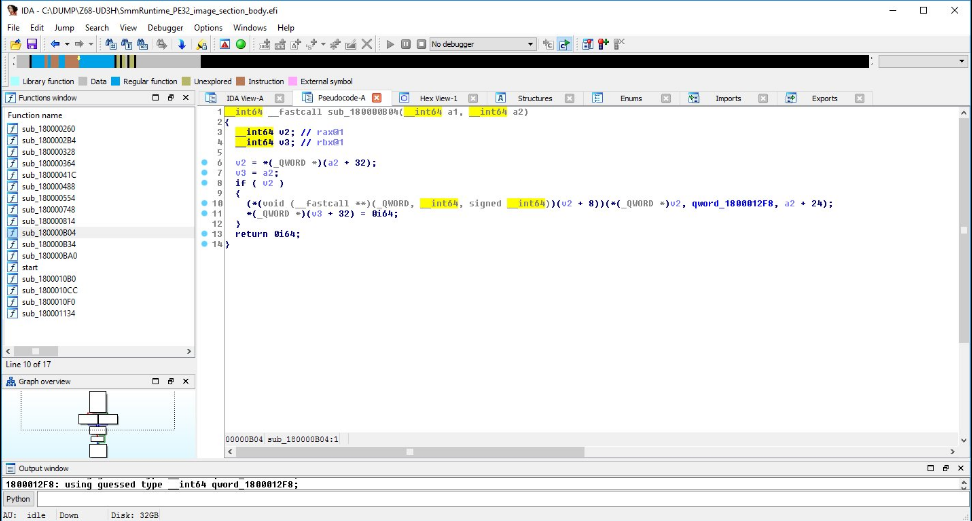
Fig. The decompiled code of the vulnerable driver from the flash-memory of the Gigabyte Z68-UD3H motherboard chip. (Cr4sh twitter)

Fig. Demonstration of successful exploit on a laptop Dell Latitude E6430.
The vulnerability of ThinkPwn was fixed by Intel back in 2014, however, UEFI manufacturers still use the vulnerable version of the driver in the production of firmware. The full scale of coverage of this vulnerability of computers is not entirely clear, as none of the UEFI vendors commented on this situation. Obviously, we are talking about a significant number of different models of computers from different manufacturers, among them, Lenovo, Hewlett-Packard, GIGABYTE, Fujitsu, and Dell.
As we indicated earlier, the ThinkPwn exploit uses a 0day vulnerability in SystemSmmRuntimeRt to execute its SMM code, which helps the exploit bypass the SMM LockBox security measure used to secure the UEFI Boot Script Table system structure. This structure is the key to reset the SPI Protected Range registers when the computer is in S3 sleep mode. By modifying the structure fields that are responsible for maintaining the SPI Protected Range registers with an SMM code, they can be subsequently loaded with zero values into the SPI registers themselves.
ThinkPwn allows you to disable the write protection of the SPI flash-memory chip, which allows attackers to embed their backdoor or rootkit there to compromise the work of any OS at the lowest level. This, in turn, can lead to bypassing the secure boot technology of Secure Boot or such authentic technologies as Virtual Secure Mode and Credential Guard on Windows 10.

In turn, Lenovo issued a security notification in which it indicated that it did not develop the vulnerable driver, as it requests the manufacturers of BIOS / UEFI firmware, which, in turn, use the operating time of Intel and AMD. After that, it became clear that the range of laptops and computers vulnerable to ThinkPwn is not limited to Lenovo. Although, apart from Lenovo, none of the manufacturers of computers and motherboards mentioned the vulnerability, it became known that Hewlett-Packard Pavilion notebooks, computers with motherboards from GIGABYTE (Z68-UD3H, Z77X-UD5H, Z87MX-D3H, and others) were susceptible to it, Fujitsu LIFEBOOK laptops, as well as Dell.
')

Fig. The decompiled code of the vulnerable driver from the flash-memory of the Gigabyte Z68-UD3H motherboard chip. (Cr4sh twitter)

Fig. Demonstration of successful exploit on a laptop Dell Latitude E6430.
The vulnerability of ThinkPwn was fixed by Intel back in 2014, however, UEFI manufacturers still use the vulnerable version of the driver in the production of firmware. The full scale of coverage of this vulnerability of computers is not entirely clear, as none of the UEFI vendors commented on this situation. Obviously, we are talking about a significant number of different models of computers from different manufacturers, among them, Lenovo, Hewlett-Packard, GIGABYTE, Fujitsu, and Dell.
As we indicated earlier, the ThinkPwn exploit uses a 0day vulnerability in SystemSmmRuntimeRt to execute its SMM code, which helps the exploit bypass the SMM LockBox security measure used to secure the UEFI Boot Script Table system structure. This structure is the key to reset the SPI Protected Range registers when the computer is in S3 sleep mode. By modifying the structure fields that are responsible for maintaining the SPI Protected Range registers with an SMM code, they can be subsequently loaded with zero values into the SPI registers themselves.
ThinkPwn allows you to disable the write protection of the SPI flash-memory chip, which allows attackers to embed their backdoor or rootkit there to compromise the work of any OS at the lowest level. This, in turn, can lead to bypassing the secure boot technology of Secure Boot or such authentic technologies as Virtual Secure Mode and Credential Guard on Windows 10.
Source: https://habr.com/ru/post/305254/
All Articles