The evolution of threats and defense strategies
Hacker attacks and their opposing corporate security systems are becoming more complex and sophisticated. “Bad guys” create powerful infrastructures for their malicious campaigns. Cybercriminals are constantly improving technologies and methods of identity theft and intellectual property, and their network attacks can go unnoticed.

A Cisco information security report tells us that commercial browsers can be caused by regular browsers - this problem is now widespread. More than 85% of the organizations reviewed in the study installed malicious browser extensions, that is, almost every company encountered this problem.
')
In addition, last year, popular botnets affected the interests of a number of organizations. The analysis showed that the vast majority of such malware (91.3%) uses the domain name system (DNS) to attack. Revealed "fraudulent" DNS service, working in a network of customers. And the customers did not even know that their DNS servers were used by their own employees within the framework of the existing infrastructure of the domain name system.

One of the trends of the past year is the wide distribution of the HTTPS protocol. Although encryption helps protect users, there is also a downside: it becomes more difficult for developers to track threats. In addition, some types of malware can exchange encrypted data on different ports.
In the world, the proportion of aging IT infrastructure is growing. According to the study, 92% of the analyzed devices are running software with known vulnerabilities. In addition, 31% of the equipment has reached the phase of “discontinuing sales”, and 8% is at the “end of life cycle” stage.
In 2015, managers became less confident in their information security tools and processes than a year earlier. For example, last year 59% of organizations claimed that their security infrastructure was “very modern” versus 64% of respondents a year earlier. This motivates organizations to improve their protection systems, which should not only confront external threats.
Protecting corporate resources and valuable information is also necessary from internal threats. In particular, as evidenced by the results of a study conducted by the Ponemon Institute and the company Fasoo, the disorder of employees is the main cause of the leaks. It was she who caused more than half of the incidents (56%). In 37% of cases, a leak occurs as a result of loss or theft of a device. 35% of incidents due to a third party error. Only in 22% of cases does confidential information disappear through the fault of intruders who are not associated with the company.
Often the secrets fall into the hands of employees who should not have access to them. Uncontrolled dissemination of confidential information within the company is observed in 73% of cases. Often, organizations simply do not know exactly where the most sensitive documents are located and who can access them. Over half of the companies are allowed to use free services for storing and sharing files. In 77% of companies, they have never arranged an audit of how their confidential documents are stored.
In the next five years, the need for adaptive integrated solutions will lead to the creation of a scalable, integrated security architecture for threats. Such a “detection and response” architecture can respond much faster to known and new threats. It will be based on a monitoring platform that is context sensitive and continuously updated to assess threats, correlate local and global data, and optimizes protection.
It is the monitoring capabilities that should provide protection against a larger number of attack vectors and internal threats. In addition, such a platform can be the basis on which all solution providers can work and to which they can contribute.
To better understand the actual and potential benefits of this architecture, consider the six principles of integrated protection.
1. Broader network infrastructure and information security architecture to combat the growing volume of increasingly complex threats.
Over the past 25 years, the formula for the traditional model of information security was: “I see a problem, I buy a box”. But such solutions often represent a collection of technologies from different suppliers. They do not interact with each other.
An integrated threat protection architecture is a detection and response platform that offers more capabilities and responds to threats faster by automatically gathering more data. Such a platform monitors the information security environment and not only notifies of suspicious events and policy violations, but also creates a clear picture of events in the network.
2. “Best-in-class” information security technologies alone cannot cope with the current and future environment of threats. They only complicate the network infrastructure.
Organizations are investing in "best-in-class" security technology, but do they know how these solutions really work? As practice shows, numerous security technologies do not work as well as expected, and the consequences can be disastrous.
3. Analysis of encrypted traffic will require an integrated threat protection mechanism capable of detecting encrypted data about malicious activities that point products pass through.
The volume of encrypted web traffic is growing. And it complicates tracking threats. The solution is to obtain more detailed information about what is happening on devices or in network infrastructures. Embedded security systems can help overcome this problem.
4. Open APIs are essential for an integrated threat protection architecture.
For multi-vendor solutions, a common platform is needed that provides monitoring, context, and management capabilities. Creating an integration platform can improve automation and improve the quality of information provided by information security products.
5. For an integrated threat protection architecture, less hardware and software is required to be installed and monitored.
Providers of information security systems should strive to create the most functional solutions and provide as many opportunities as possible on one platform. This will help simplify and defragment the security environment, which leaves too many opportunities for intruders.
6. Automation and coordination functions in an integrated threat protection architecture can reduce detection, deterrence and recovery time.
Reducing the number of false positives allows IB services to focus on the most important. Contextualization helps assess whether these events require an immediate response. Specialists can receive automated reports and more detailed data analytics systems.
It is difficult to overestimate the importance of intra-industry cooperation. It is necessary not only to develop a future integrated threat defense architecture, but also to track down ever more active and trained cybercriminals. Attackers are becoming more experienced in deploying their hard-to-find solutions ...
What specific steps should organizations take to introduce practical information security methods?
According to the study, the top three most popular protection tools include firewalls, DLP systems and authentication tools. 52% of companies use standardized security policies.
Organizations need expert help. This confirms the growing practice of attracting third-party companies to conduct inspections and respond to incidents. The organizations' point of view on outsourcing is gradually changing: large enterprises, including in Russia, use it more often for auditing, recommendations and consultations.
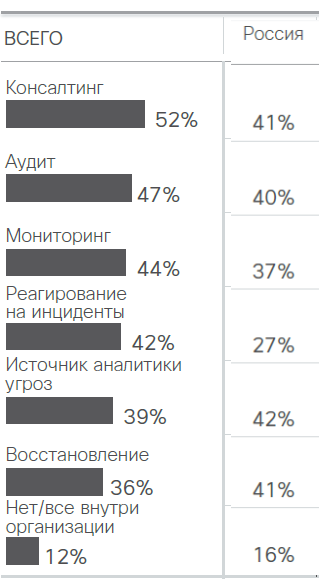
What security services are performed by third parties — on average in the world and in Russia.
Security solutions providers should consider the impact that active joint and continuous work of industry participants can have in fighting cybercrime, curbing the ability of attackers to generate revenue and reducing the likelihood of future attacks.
Businesses should further examine their readiness to repel attacks, and security professionals need to contain the rising costs of technology support and maintenance. The confidence of customers in the reliability of their “defense” will increase as tools are deployed, allowing not only to detect threats, but also to neutralize the consequences of their influence, as well as to receive information necessary to prevent external attacks and internal incidents in the future.

Any problem must be solved in its entirety. Technical means of protection is only part of the equation. Do not forget that the human factor plays a huge role. Information security specialists need to constantly develop and improve ways to counteract social engineering (methods of obtaining the necessary access to information based on the characteristics of people's psychology), in particular, to conduct training aimed at increasing knowledge in the field of information security of ordinary employees. In our company, we conduct ongoing training in which we cover the basics of identifying methods of social engineering.
Alexey Pulin, Traffic Inspector Technical Support Specialist
The evolution of threats: major changes and facts
A Cisco information security report tells us that commercial browsers can be caused by regular browsers - this problem is now widespread. More than 85% of the organizations reviewed in the study installed malicious browser extensions, that is, almost every company encountered this problem.
')
In addition, last year, popular botnets affected the interests of a number of organizations. The analysis showed that the vast majority of such malware (91.3%) uses the domain name system (DNS) to attack. Revealed "fraudulent" DNS service, working in a network of customers. And the customers did not even know that their DNS servers were used by their own employees within the framework of the existing infrastructure of the domain name system.

One of the trends of the past year is the wide distribution of the HTTPS protocol. Although encryption helps protect users, there is also a downside: it becomes more difficult for developers to track threats. In addition, some types of malware can exchange encrypted data on different ports.
In the world, the proportion of aging IT infrastructure is growing. According to the study, 92% of the analyzed devices are running software with known vulnerabilities. In addition, 31% of the equipment has reached the phase of “discontinuing sales”, and 8% is at the “end of life cycle” stage.
In 2015, managers became less confident in their information security tools and processes than a year earlier. For example, last year 59% of organizations claimed that their security infrastructure was “very modern” versus 64% of respondents a year earlier. This motivates organizations to improve their protection systems, which should not only confront external threats.
Internal threats
Protecting corporate resources and valuable information is also necessary from internal threats. In particular, as evidenced by the results of a study conducted by the Ponemon Institute and the company Fasoo, the disorder of employees is the main cause of the leaks. It was she who caused more than half of the incidents (56%). In 37% of cases, a leak occurs as a result of loss or theft of a device. 35% of incidents due to a third party error. Only in 22% of cases does confidential information disappear through the fault of intruders who are not associated with the company.
Often the secrets fall into the hands of employees who should not have access to them. Uncontrolled dissemination of confidential information within the company is observed in 73% of cases. Often, organizations simply do not know exactly where the most sensitive documents are located and who can access them. Over half of the companies are allowed to use free services for storing and sharing files. In 77% of companies, they have never arranged an audit of how their confidential documents are stored.
Integration and cooperation
In the next five years, the need for adaptive integrated solutions will lead to the creation of a scalable, integrated security architecture for threats. Such a “detection and response” architecture can respond much faster to known and new threats. It will be based on a monitoring platform that is context sensitive and continuously updated to assess threats, correlate local and global data, and optimizes protection.
It is the monitoring capabilities that should provide protection against a larger number of attack vectors and internal threats. In addition, such a platform can be the basis on which all solution providers can work and to which they can contribute.
To better understand the actual and potential benefits of this architecture, consider the six principles of integrated protection.
Made wisely
1. Broader network infrastructure and information security architecture to combat the growing volume of increasingly complex threats.
Over the past 25 years, the formula for the traditional model of information security was: “I see a problem, I buy a box”. But such solutions often represent a collection of technologies from different suppliers. They do not interact with each other.
An integrated threat protection architecture is a detection and response platform that offers more capabilities and responds to threats faster by automatically gathering more data. Such a platform monitors the information security environment and not only notifies of suspicious events and policy violations, but also creates a clear picture of events in the network.
There is safety in numbers
2. “Best-in-class” information security technologies alone cannot cope with the current and future environment of threats. They only complicate the network infrastructure.
Organizations are investing in "best-in-class" security technology, but do they know how these solutions really work? As practice shows, numerous security technologies do not work as well as expected, and the consequences can be disastrous.
Immunity against hidden threats
3. Analysis of encrypted traffic will require an integrated threat protection mechanism capable of detecting encrypted data about malicious activities that point products pass through.
The volume of encrypted web traffic is growing. And it complicates tracking threats. The solution is to obtain more detailed information about what is happening on devices or in network infrastructures. Embedded security systems can help overcome this problem.
Together - stronger
4. Open APIs are essential for an integrated threat protection architecture.
For multi-vendor solutions, a common platform is needed that provides monitoring, context, and management capabilities. Creating an integration platform can improve automation and improve the quality of information provided by information security products.
Less is more
5. For an integrated threat protection architecture, less hardware and software is required to be installed and monitored.
Providers of information security systems should strive to create the most functional solutions and provide as many opportunities as possible on one platform. This will help simplify and defragment the security environment, which leaves too many opportunities for intruders.
Cut off the excess
6. Automation and coordination functions in an integrated threat protection architecture can reduce detection, deterrence and recovery time.
Reducing the number of false positives allows IB services to focus on the most important. Contextualization helps assess whether these events require an immediate response. Specialists can receive automated reports and more detailed data analytics systems.
What is the strength in, brother?
It is difficult to overestimate the importance of intra-industry cooperation. It is necessary not only to develop a future integrated threat defense architecture, but also to track down ever more active and trained cybercriminals. Attackers are becoming more experienced in deploying their hard-to-find solutions ...
Useful tips
What specific steps should organizations take to introduce practical information security methods?
- Learn, and learn again. Employee training is a very important safety measure. They must be able to detect and prevent security threats, such as phishing attempts. ABC Security - never click on links or email attachments, especially if the letter came from an unknown sender. Mail and web are two main sources of infection.

According to a Cisco study, almost all organizations (97%) conduct information security training for their employees at least once a year. - For remote access to the corporate network, you must use at least two-factor authentication.
- Do not give users local administrative rights. Attackers often enjoy the fact that someone has special privileges.
- Do not forget about backing up all (not only critical) data and documents. Create a business continuity plan.
- Do not forget about the audit of the use of privileged rights, including administrative and service accounts.
- Important data on the network should be separated into a separate segment and carefully monitored.
- Line up a technologically strong defense. Install firewalls to protect your network and web applications.
- Deploy intrusion detection and prevention systems (IPS / IDS), checking incoming and outgoing traffic for possible threats and attacks and blocking them.
- Use advanced Advanced Malware Protection class solutions to protect client systems and networks.
- Use vulnerability scanners.
- Do not forget about monitoring logs, scanning web applications and the network - in 24x7 mode.
- Use intelligent security solutions to protect against the latest threats.
- Encrypt email messages.
- To protect client systems, use solutions with behavioral analysis functions.
- Check host-level network connections for suspicious communications.
- Monitor host level DNS activity.
According to the study, the top three most popular protection tools include firewalls, DLP systems and authentication tools. 52% of companies use standardized security policies.
Organizations need expert help. This confirms the growing practice of attracting third-party companies to conduct inspections and respond to incidents. The organizations' point of view on outsourcing is gradually changing: large enterprises, including in Russia, use it more often for auditing, recommendations and consultations.

What security services are performed by third parties — on average in the world and in Russia.
Conclusion
Security solutions providers should consider the impact that active joint and continuous work of industry participants can have in fighting cybercrime, curbing the ability of attackers to generate revenue and reducing the likelihood of future attacks.
Businesses should further examine their readiness to repel attacks, and security professionals need to contain the rising costs of technology support and maintenance. The confidence of customers in the reliability of their “defense” will increase as tools are deployed, allowing not only to detect threats, but also to neutralize the consequences of their influence, as well as to receive information necessary to prevent external attacks and internal incidents in the future.
Source: https://habr.com/ru/post/304764/
All Articles