Who should be afraid of among malware
Try asking yourself the question - what type of malware is the most dangerous? Have you thought that they are cryptographers? You are not alone - this is the way most of the conference participants are responding, as are the representatives of the management of companies with whom we are talking about purchasing protective equipment. In the meantime, you need to be afraid not to encrypt
In essence, the problem of encryptors is to a large extent the problem of specialists who excessively exaggerate the capabilities of antiviruses. A lot of customers believe that anti-malware anti-virus software is sufficient. "The anti-virus should prevent the penetration of malware into the local network / computer." Strangely enough, but the obvious thing is that no antivirus can know every single one of the malware’s attention when choosing protection tools.
Typical opinion about antiviruses and cryptographers:
Antivirus detects only what is inherent in its algorithms - and nothing more. Protection from cryptographers is a ban on installing / running unknown programs, a ban on transferring executable files in attachments is fairly well-known measures. and of course user training. When using these measures, risks are reduced to a fairly acceptable. But alas, quite often it happens like this :
But some statistics. How many new, previously unknown cryptographers are added to the anti-virus database per day?
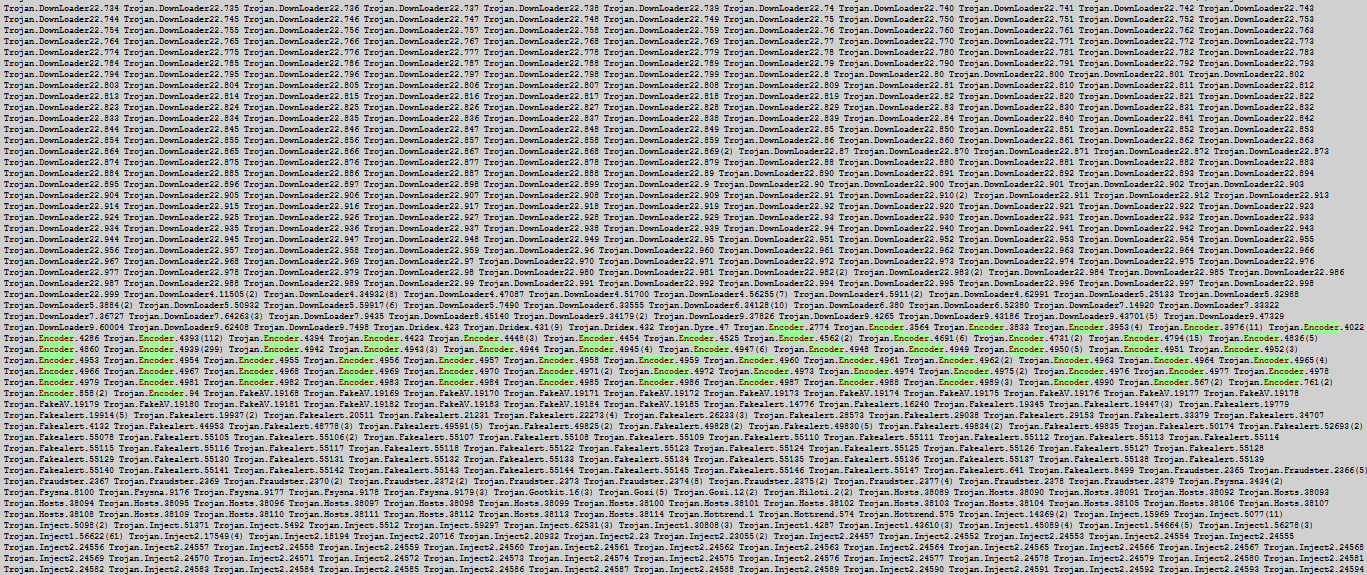
A couple of tens, sometimes less. And let's say representatives of Trojan.DownLoader?

And this is not all representatives - just with an even smaller font size, the words began to merge.
And about the most dangerous.
After reading about viral news, readers immediately have a question - everything is of course scary, but how did the malicious program penetrate the computer? And here the droppers come on the scene.
There is a lot of similar news, but the essence is the same. An unknown malicious file penetrates the computer, downloads the modules needed by the attacker or extracts them from itself, cleans the logs and deletes itself. As a result, after detecting malicious activity, the component of the malicious complex responsible for penetration does not fall into the hands of analysts of the anti-virus industry, the penetration method remains unknown and infection can occur again and again - possibly with new components, again unknown to the anti-virus protection system.
Naturally droppers can be distributed in traditional ways - for example, attachments to mail, but this is not necessary and you should not count on it.
In connection with the foregoing. Protect logs from unauthorized cleaning and store them in places where an intruder cannot reach them. Only in this way will information about the distribution of malicious programs appear in the news.
In essence, the problem of encryptors is to a large extent the problem of specialists who excessively exaggerate the capabilities of antiviruses. A lot of customers believe that anti-malware anti-virus software is sufficient. "The anti-virus should prevent the penetration of malware into the local network / computer." Strangely enough, but the obvious thing is that no antivirus can know every single one of the malware’s attention when choosing protection tools.
Typical opinion about antiviruses and cryptographers:
Good antivirus catches without problems.
Antivirus detects only what is inherent in its algorithms - and nothing more. Protection from cryptographers is a ban on installing / running unknown programs, a ban on transferring executable files in attachments is fairly well-known measures. and of course user training. When using these measures, risks are reduced to a fairly acceptable. But alas, quite often it happens like this :
I stopped supporting the office alone - the chief accountant is trying to open a letter - “We are suing you” - they do not give antivirus and firewall.
So she turned off the antivirus and tried to open the attachment - the benefit of the antivirus cleared the file.
So this smart Madama - went to the mail from home and copied the file to her and opened it.
Smart, che.
Well, Khan's home archive photo \ porn.
In the end, I am guilty of not warning.
And the type of huge red table is not a warning?
')
ZySy 2 These evil Pinocchio chopped off backup server.
Like what it is and flashes.
But some statistics. How many new, previously unknown cryptographers are added to the anti-virus database per day?

A couple of tens, sometimes less. And let's say representatives of Trojan.DownLoader?

And this is not all representatives - just with an even smaller font size, the words began to merge.
And about the most dangerous.
After reading about viral news, readers immediately have a question - everything is of course scary, but how did the malicious program penetrate the computer? And here the droppers come on the scene.
the BackDoor.Apper.1 Trojan is distributed using a dropper, which is a Microsoft Excel document containing a special macro. This macro collects bytes and runs a self-extracting archive. The archive, in turn, contains an executable file that has a valid digital signature from Symantec, and a dynamic library that contains the main functionality of the backdoor. The Trojan registers in an autoload an executable file, which after its launch loads the malicious library into the memory of the attacked computer.
By registering its own application at startup, the trojan deletes the source file.
There is a lot of similar news, but the essence is the same. An unknown malicious file penetrates the computer, downloads the modules needed by the attacker or extracts them from itself, cleans the logs and deletes itself. As a result, after detecting malicious activity, the component of the malicious complex responsible for penetration does not fall into the hands of analysts of the anti-virus industry, the penetration method remains unknown and infection can occur again and again - possibly with new components, again unknown to the anti-virus protection system.
Naturally droppers can be distributed in traditional ways - for example, attachments to mail, but this is not necessary and you should not count on it.
In connection with the foregoing. Protect logs from unauthorized cleaning and store them in places where an intruder cannot reach them. Only in this way will information about the distribution of malicious programs appear in the news.
Source: https://habr.com/ru/post/304758/
All Articles