Vulnerabilities of corporate information systems - 2015: inside is worse than outside

Maximum risk level of vulnerabilities due to lack of security updates (proportion of vulnerable systems)
In 2015, the company's network infrastructures were better protected from an outside attacker than in previous years, but the level of protection from an intruder remained extremely low. The leader of network perimeter vulnerabilities is old versions of software, and in internal networks there are flaws in managing accounts and passwords. The number of employees who follow external links has increased, and the security level of every third of the wireless networks is rated “below average”. Such observations were made in a study of Positive Technologies based on penetration tests conducted in 2015. Below we present the main results of the study.
')
Initial data
The study used the test results of 17 information systems of large Russian and foreign companies. The largest share is made by financial sector companies (35%). Equal shares are represented by industrial, telecommunication and IT companies (18% each), and among the tested ones are one transport company and one state organization. Most of the enterprises studied included many subsidiaries and branches located in different cities and countries; the number of active nodes available on their network perimeter was in the hundreds. In addition to penetration testing, staff awareness of information security issues was assessed in 24% of projects.
Overall results
In 76% of the systems studied, an attacker was able to gain complete control over certain critical resources. Moreover, in 35% of systems, this level of privilege can be obtained on behalf of any external violator. Failed to gain control over any critical resources in 24% of projects. In general, there is a tendency to increase the overall level of protection of critical resources, compared with 2013 and 2014.
In half of the systems studied, it is possible to obtain complete control over the entire corporate infrastructure. At the same time, in 19% of cases such privileges can be obtained from an external intruder, and in another 31% of companies - on behalf of an internal violator from the user's network segment.
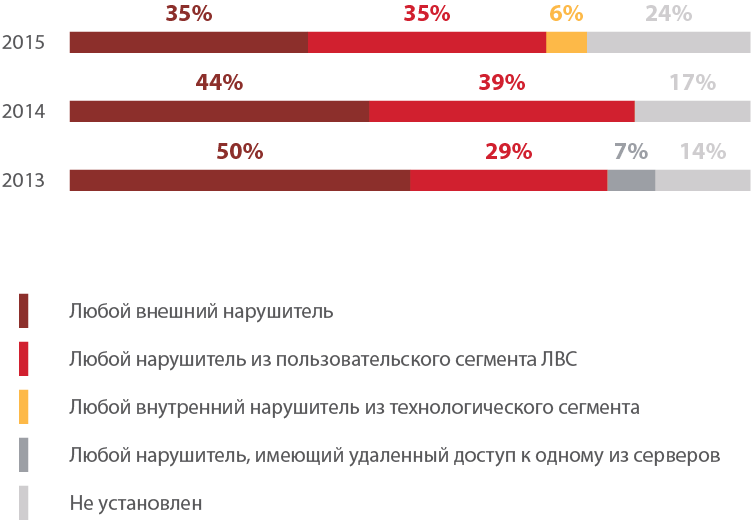
Minimum level of access required for the violator to gain full control over certain critical resources
As in previous years, high-risk vulnerabilities were discovered in almost every corporate infrastructure. Since 2013, there has been a growth trend in the share of organizations whose corporate infrastructure is exposed to critically dangerous vulnerabilities associated with the use of outdated software versions and the lack of security updates. The average age of the most outdated unspecified updates is 73 months (more than six years).
Disadvantages of network perimeter protection
Compared to 2014, the overall security level of the network perimeter increased: in almost half of the projects where work was carried out, there were no deficiencies that would allow access to critical resources from external networks. The complexity of the attacks has also increased: in order to gain access to the internal network resources, it is enough for an external intruder to have low qualifications only in 46% of cases (versus 61% in 2014).
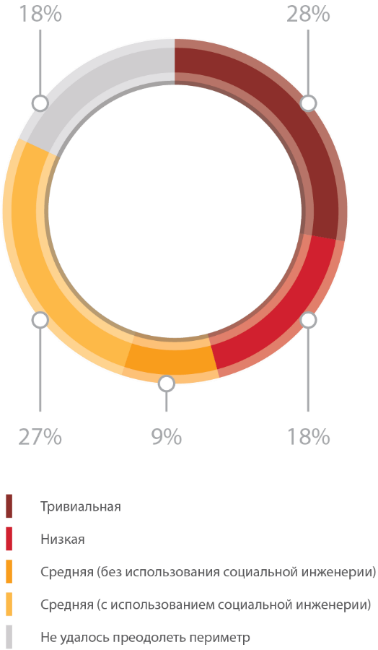
The difficulty of overcoming the perimeter
In 54% of projects where external penetration testing was carried out, maximum privileges were obtained in any business-critical systems, in 27% of cases - full control over the entire infrastructure of the company.
In 55% of systems, to overcome the network perimeter without using social engineering methods required a medium or low qualification, or completely trivial actions of the offender. On average, in order to gain access to the internal network resources, as in 2014, two different vulnerabilities were required to be exploited.
In overcoming the network perimeter in 47% of cases, the attack vector was based on the exploitation of vulnerabilities in web applications . In general, vulnerabilities of various levels of risk in the code of web applications were found in 69% of the systems studied. For example, the “Download arbitrary files” vulnerability was detected in 56% of projects, and the “Implementation of SQL statements” was possible in 44%.
The other 53% of the attacks that resulted in access to the resources of the internal network were accounted for using dictionary credentials . This vulnerability was most common in 2014, and in 2015, 78% of the systems were detected on the network perimeter. In all these systems, simple passwords of privileged users were detected. In 44% of companies, vocabulary credentials were used to access public web applications.
All the systems studied revealed weaknesses associated with the use of vulnerable software versions on the network perimeter; these are mostly outdated versions of web servers (78%) and application software (67%).

The most common vulnerabilities on the network perimeter
Disadvantages of internal network protection
As in previous years, within all projects, it was possible to obtain maximum privileges in critical systems when testing on behalf of an internal attacker (for example, an ordinary employee located in a user network segment). At the same time, full control over the infrastructure was obtained in 71% of cases. The results obtained coincide with the figures for 2013.
On average, if you have access to the internal network, the attacker needs to exploit four different vulnerabilities, which is one step more than in the previous year and one step less than in 2013, in order to control critical resources. However, the complexity of the implementation of attacks has decreased significantly - in 82% of cases, it was enough for a violator to have a low-level qualification to access critical resources; the same indicator in 2014 was only 56%.
The most common vulnerability of internal network resources is the use of dictionary passwords. This deficiency was found in all projects without exception. In 91% of cases, the use of weak passwords for privileged accounts was revealed.

Vocabulary passwords in the internal network
All systems also revealed weaknesses in the protection of service protocols, which could lead to interception and redirection of network traffic. The insufficient level of protection of privileged accounts and the shortcomings of anti-virus protection are still common in the internal network of companies: vulnerabilities in each of these categories were found in 91% of systems.
The level of security of internal networks is still extremely low. Despite some improvements (for example, the average level of cryptographic protection has increased, user awareness of information security issues has increased), the measures applied are still not enough to counter attackers. The most common scenario for the development of an attack in the internal network has not changed much since 2014 and consists of only three main stages. As before, for a successful attack, it is enough to use widespread and well-known types of vulnerabilities.

The most common internal network vulnerabilities
Lack of awareness of employees in matters of information security
In general, the level of awareness of employees in information security issues is higher than in 2014, but still remains quite low: in none of the tested systems it was rated as acceptable, although the share of companies for which the level of awareness of employees was reduced by half rated as extremely low (25% vs. 50% in 2014).
In 2015, an average of 24% of users made a fake link (in 2014, it was 20%). The proportion of subjects who entered their credentials in a deliberately false form of authentication or downloaded the executable file did not change: the indicator remained at the level of 15%.

The share of recorded events relative to the total number of sent messages
Disadvantages of wireless security
As part of this work, a search is made for deficiencies in the use of access points and Wi-Fi client devices for the 2.4 and 5 GHz bands using 802.11a / b / g / n technologies, as well as deficiencies in the architecture and organization of wireless access. Only for 33% of systems, the level of security of wireless networks was rated as “acceptable”.
Among the identified shortcomings, it is worth noting the use of the WPS mechanism to simplify the process of setting up a wireless network. To connect to the access point using a special PIN-code, consisting only of numbers. The intruder can pick up the PIN and connect to the access point.
Also revealed the facts of using unauthorized access points ; if they are connected to a local area network, the attacker has the ability to gain access to internal networks. A number of systems have detected the lack of protection for individual wireless networks , which can lead to the interception of important information. Common vulnerabilities can also include the use of standard accounts to access the web-based network management interface.
As part of one of the projects, it was found that almost all of the company's wireless networks are accessible outside the controlled area, while the public domain user account data were stored in open form on the network perimeter resources. Thus, any external intruder can connect to the wireless network and carry out attacks on LAN resources.
Conclusion
In order to reduce the risks of compromising critical systems from outsiders, it is recommended that particular attention be paid to resources available from external networks. As practice shows, the overwhelming majority of successful attacks are based on exploiting vulnerabilities not from official websites of organizations and their servers, but from any other company resources that should not be available on the network perimeter (for example, DBMS, unused debugging interfaces, remote access interfaces or management interfaces). infrastructure service interfaces such as LDAP). Interfaces for accessing such resources may be opened for connection by administrators by mistake; Often, representatives of large companies responsible for security cannot say exactly how much and what resources of an organization are available from external networks.
To protect against attacks on web applications, it is recommended to use application-level firewalls with effective correlation rule settings. To monitor resources on the network perimeter, it is recommended to ensure regular scanning of resources available from external networks (for example, once a month). For timely detection and elimination of vulnerabilities in the code of critical web applications, it is necessary to regularly analyze their security, using either the black or gray box method or the white box method with a detailed analysis of the source codes. Such work is important to carry out not only at each stage of the application development, but also in relation to the systems put into operation, with the subsequent control over the elimination of the identified vulnerabilities.
Regarding protection of corporate systems against attacks by an intruder, it is necessary to introduce a password policy prohibiting the use of simple passwords, providing mandatory two-factor authentication for privileged users of critical systems, as well as requirements for regular password changes (for example, once every 60 days). It is also necessary to pay special attention to outdated versions of software, to open data transfer protocols and to storing important information in open form on servers and workstations of employees. In addition to basic information security measures, information security audit and penetration testing by external and internal violators should be carried out on a regular basis.
Read the full text of the study at www.ptsecurity.ru/research/analytics
Authors: Dmitry Katalkov, Evgeny Gnedin, Information Security Analytics, Positive Technologies
Source: https://habr.com/ru/post/304738/
All Articles