Identity Cloud Services - a new generation of identity services
This article focuses on Oracle Identity Cloud Services, a new generation of identity services that work both with cloud-based business applications and as part of systems deployed in an enterprise's IT infrastructure.

It would seem that there is not and there can be nothing unusual in Identity Management (IdM), it is a standard corporate technology, a means of automating secondary business processes of a company, minimizing risks associated with information security, reducing the labor costs of administrators and the Help Desk, and of increasing satisfaction. end users, of course. But the world is changing, and cloud solutions in the field of business applications require the development of IdM services.
')
Security is a top priority for Oracle cloud solutions. Oracle's goal is to create the most secure and reliable services for public cloud infrastructures and platforms designed for commercial and government organizations. Oracle's mission is to build secure infrastructure and platform services in a public cloud, in which Oracle customers are provided with reliable and manageable security for reliably executing workloads and building trusted, scalable cloud solutions.
To quote Larry Ellison. He recently said: “After five years, security from the main obstacle will be the main reason for the transition to the cloud.” In other words, if your business is not information security, then it is unlikely that you can protect your applications as a cloud solution provider can do for you. Oracle has been working in the field of information security for a long time, and, in addition to its own solutions, has the ability to apply many third-party solutions to keep your data safe and at the same time ensure compliance with international standards in the field of information security.

Considering what we want to write about today, this is by no means an elegant paradox - this is the near future of cloud computing taking into account current trends. After all, Oracle Identity Cloud Services will work just as well - both with cloud-based business applications and as part of systems deployed in an enterprise's IT infrastructure (Figure 1). IdM for Oracle Cloud protects the cloud technologies themselves, but the second block, called “Oracle IDCS” in the figure, is of particular interest to us - this is protection as a cloud service for other applications.
To begin with, how is the protection of the Oracle cloud itself ensured - and this is about 80 thousand virtual machines and 19 data centers around the world. 30 billion transactions pass through Oracle Cloud every day. Oracle is the second SaaS provider in the world, with Oracle regularly acquiring cloud service providers and constantly hiring specialists in this field - hundreds of specialists every year.

Figure 2 illustrates the locations of Oracle data centers. Green color indicates those data centers that will be commissioned before the end of 2016. Oracle data centers provide a high degree of accessibility - 99.999%, all of which have passed ISO certification.

Figure 3 reflects the power of Oracle data centers. The company has made significant investments as a cloud provider and shows a serious approach. Oracle Exadata is used to store data in Oracle data centers, the Big Data Appliance is used to work with the Big Data, and the ZFS Storage Appliance is used to store data. In addition, SPARC servers with an M7 processor are used to differentiate memory areas.
Oracle provides security mechanisms that allow you to control who and under what conditions can access the data — control is extremely tight. In addition to physical security, logical protection, disk encryption, antivirus and antispam, various levels of network protection are also used. To provide access and access control, Oracle IDM products (more precisely, Identity & Access Management) are used, which allow you to implement such things as creating accounts, assigning privileges, authorization, auditing, periodically checking the redundancy of authority when granting access (so-called certification access). For access to applications using two-factor authentication. The Oracle Cloud service network is separate from the Oracle corporate network and requires separate credentials for access - Oracle employees who have access to the corporate network do not have access to the Oracle Cloud network and need to explicitly access the cloud. request credentials to gain access to the components of the Oracle Cloud; all these requests are checked by the responsible persons.
Periodically, Oracle performs vulnerability analysis and penetration tests, and on a daily basis, Oracle performs scans — almost 2 million IP addresses are scanned every week, 518 scans are performed every week. Security information and Event Management, or SIEM (McAfee products), are used to automatically correlate security events and identify correlation-based threats. Individual sources (servers, routers, etc.) send logs to collectors, then logs are sent to Enterprise Security Manager (ESM) for normalization and aggregation, Enterprise Log Manager (ELM) for long-term storage. McAfee Global Threat Intelligence data is shared with ESM. The Advanced Correlation Engine (ACE) detects threats and security events in accordance with normalized ESM data.
To protect cloud computing, Oracle uses the best security services — securely accessing the network using VPNs, preventing data leakage using Bastion Hosts, and more ... The Oracle Cloud network provides reliable protection against traditional security issues such as interception attacks, IP spoofing and port scan. Network protection devices are widely used, including network communications monitoring and control devices both at the external and internal borders of the network.
Encryption is widely used to access Oracle Cloud network services. Customers get access to services through encrypted protocols, the connection is formed using strong encryption. In addition, Oracle Cloud ensures that applications comply with international legal requirements, including the requirements of the PCI DSS standard, which are especially in demand by Russian customers. In general, it is a powerful echeloned protection at all levels: from the level of processors to the physical level and the application level.
The solution, which will soon appear under the already mentioned name Identity Cloud Services (IDCS), will allow Oracle customers to protect using cloud-based security products as applications that are hosted locally and cloud applications. Identity Cloud Services is designed to manage both identifiers and access to all types of Oracle Cloud services. A key feature of IDCS is common identifiers for users, services, and applications.
For managing users — that is, the SCIM standard is used to create users, retrieve data, organize search queries among users, a list of users. Standards are also used to integrate cloud and local applications: SAML federated interoperability standards — federated SSO, which enables the transfer of profile attributes, OIDC — authentication for OAuth, and the OAuth standard, which provides delegated authorization from service to service and transmission of identifiers.
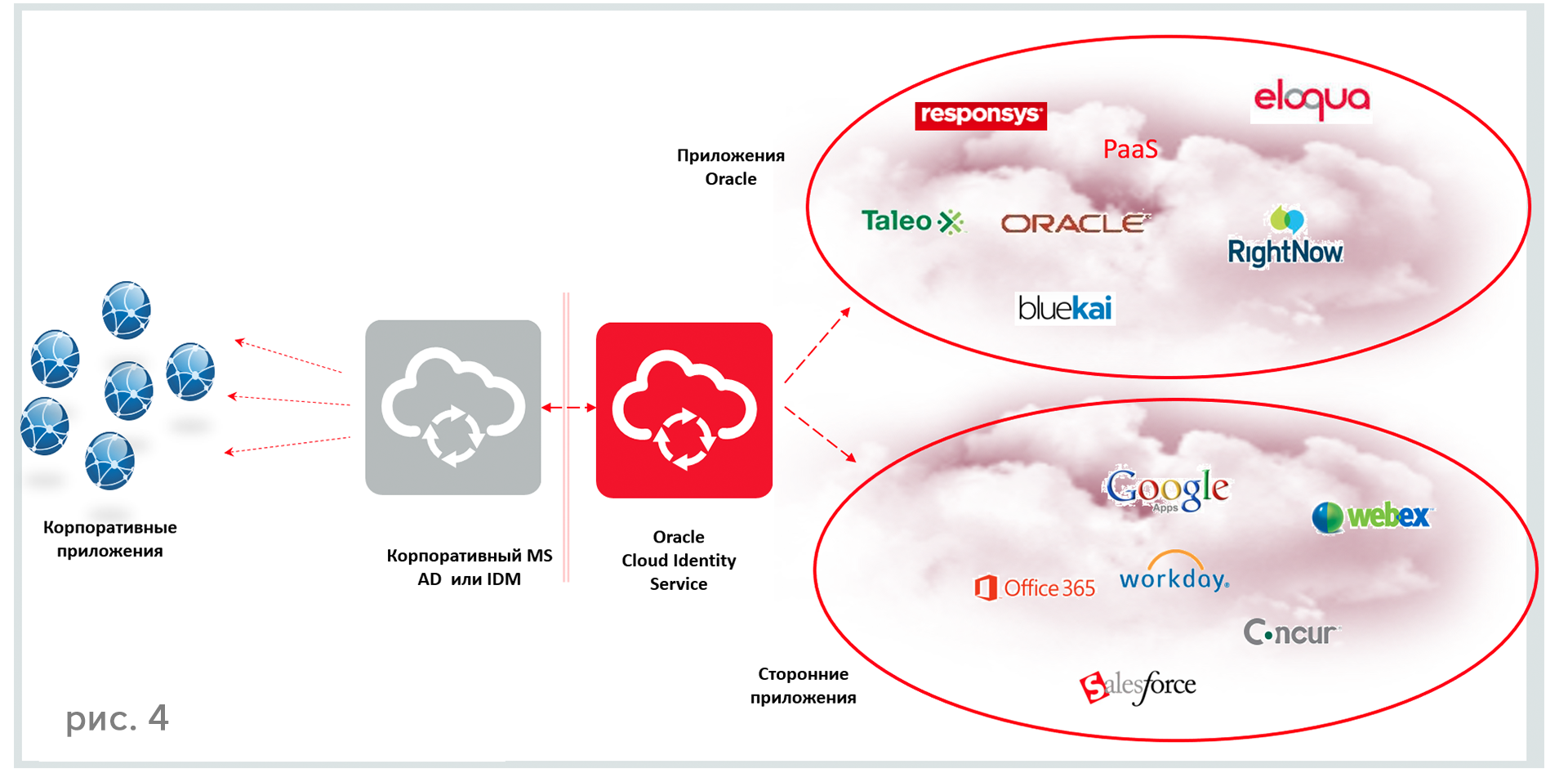
Figure 4 reflects the planned functionality of Oracle Identity Cloud Services, there are two types of solutions: a corporate solution with a set of applications for which one-time security is provided, with IdM, etc., and a cloud infrastructure, and these two environments need to be connected in order not to it was necessary to immediately migrate to the cloud, and it was possible to use technologies from both the corporate solution and the cloud — to take the best of both worlds.
When a user receives an Identity Cloud Services administrator account, he must select a set of applications, bind these applications to users, synchronize the list of users with the local repository, organize the list of roles that will be used in applications, create groups of users who will get access to the applications, - that is, to actually do all that IdM is doing now.
It is this workflow that will be implemented in IDCS. In terms of managing applications, IDCS offers the following options: choosing from a list of pre-registered applications or registering new ones (OAuth or SAML), entering an administrative account in the application, linking domain user groups to an application, registering, generating identifiers and keys, describing and adding resources, management of authorization methods in the OAuth specification, connection of the SP profile, and provision of access to users and groups of users to the application.
Next, work with users. You can activate, deactivate the user, force the user to reset the password at the entrance, bind certain policies to change the password to the user, etc. When the user logs into his own system, he is provided with self-service capabilities: a list of available applications, registration of an account for applications, changing his own Attributes - so he did not bother the administrator.
Finally, on the internal capabilities of the service instance. The user can configure notifications of end users and administrators, register identity providers, enable federated SSO, select IdP, register trusted partners (OAuth and SAML), change password policy, describe connection parameters with corporate LDAP directory for account synchronization, assign users with administrative rights , change the appearance of the graphical interface, enable diagnostic mode, and work with network security (i.e., with a list of addresses that can allow access to the system, etc.), and configure SSO.
The task management toolkit allows you to select tasks from a predefined list.
As resources for studying IdM and IDCS, we recommend (articles on IDCS will appear as official announcements appear):

It would seem that there is not and there can be nothing unusual in Identity Management (IdM), it is a standard corporate technology, a means of automating secondary business processes of a company, minimizing risks associated with information security, reducing the labor costs of administrators and the Help Desk, and of increasing satisfaction. end users, of course. But the world is changing, and cloud solutions in the field of business applications require the development of IdM services.
')
Security is a top priority for Oracle cloud solutions. Oracle's goal is to create the most secure and reliable services for public cloud infrastructures and platforms designed for commercial and government organizations. Oracle's mission is to build secure infrastructure and platform services in a public cloud, in which Oracle customers are provided with reliable and manageable security for reliably executing workloads and building trusted, scalable cloud solutions.
To quote Larry Ellison. He recently said: “After five years, security from the main obstacle will be the main reason for the transition to the cloud.” In other words, if your business is not information security, then it is unlikely that you can protect your applications as a cloud solution provider can do for you. Oracle has been working in the field of information security for a long time, and, in addition to its own solutions, has the ability to apply many third-party solutions to keep your data safe and at the same time ensure compliance with international standards in the field of information security.

Considering what we want to write about today, this is by no means an elegant paradox - this is the near future of cloud computing taking into account current trends. After all, Oracle Identity Cloud Services will work just as well - both with cloud-based business applications and as part of systems deployed in an enterprise's IT infrastructure (Figure 1). IdM for Oracle Cloud protects the cloud technologies themselves, but the second block, called “Oracle IDCS” in the figure, is of particular interest to us - this is protection as a cloud service for other applications.
IdM in Oracle Cloud
To begin with, how is the protection of the Oracle cloud itself ensured - and this is about 80 thousand virtual machines and 19 data centers around the world. 30 billion transactions pass through Oracle Cloud every day. Oracle is the second SaaS provider in the world, with Oracle regularly acquiring cloud service providers and constantly hiring specialists in this field - hundreds of specialists every year.

Figure 2 illustrates the locations of Oracle data centers. Green color indicates those data centers that will be commissioned before the end of 2016. Oracle data centers provide a high degree of accessibility - 99.999%, all of which have passed ISO certification.

Figure 3 reflects the power of Oracle data centers. The company has made significant investments as a cloud provider and shows a serious approach. Oracle Exadata is used to store data in Oracle data centers, the Big Data Appliance is used to work with the Big Data, and the ZFS Storage Appliance is used to store data. In addition, SPARC servers with an M7 processor are used to differentiate memory areas.
Oracle provides security mechanisms that allow you to control who and under what conditions can access the data — control is extremely tight. In addition to physical security, logical protection, disk encryption, antivirus and antispam, various levels of network protection are also used. To provide access and access control, Oracle IDM products (more precisely, Identity & Access Management) are used, which allow you to implement such things as creating accounts, assigning privileges, authorization, auditing, periodically checking the redundancy of authority when granting access (so-called certification access). For access to applications using two-factor authentication. The Oracle Cloud service network is separate from the Oracle corporate network and requires separate credentials for access - Oracle employees who have access to the corporate network do not have access to the Oracle Cloud network and need to explicitly access the cloud. request credentials to gain access to the components of the Oracle Cloud; all these requests are checked by the responsible persons.
Periodically, Oracle performs vulnerability analysis and penetration tests, and on a daily basis, Oracle performs scans — almost 2 million IP addresses are scanned every week, 518 scans are performed every week. Security information and Event Management, or SIEM (McAfee products), are used to automatically correlate security events and identify correlation-based threats. Individual sources (servers, routers, etc.) send logs to collectors, then logs are sent to Enterprise Security Manager (ESM) for normalization and aggregation, Enterprise Log Manager (ELM) for long-term storage. McAfee Global Threat Intelligence data is shared with ESM. The Advanced Correlation Engine (ACE) detects threats and security events in accordance with normalized ESM data.
To protect cloud computing, Oracle uses the best security services — securely accessing the network using VPNs, preventing data leakage using Bastion Hosts, and more ... The Oracle Cloud network provides reliable protection against traditional security issues such as interception attacks, IP spoofing and port scan. Network protection devices are widely used, including network communications monitoring and control devices both at the external and internal borders of the network.
Encryption is widely used to access Oracle Cloud network services. Customers get access to services through encrypted protocols, the connection is formed using strong encryption. In addition, Oracle Cloud ensures that applications comply with international legal requirements, including the requirements of the PCI DSS standard, which are especially in demand by Russian customers. In general, it is a powerful echeloned protection at all levels: from the level of processors to the physical level and the application level.
IdM as a service
The solution, which will soon appear under the already mentioned name Identity Cloud Services (IDCS), will allow Oracle customers to protect using cloud-based security products as applications that are hosted locally and cloud applications. Identity Cloud Services is designed to manage both identifiers and access to all types of Oracle Cloud services. A key feature of IDCS is common identifiers for users, services, and applications.
For managing users — that is, the SCIM standard is used to create users, retrieve data, organize search queries among users, a list of users. Standards are also used to integrate cloud and local applications: SAML federated interoperability standards — federated SSO, which enables the transfer of profile attributes, OIDC — authentication for OAuth, and the OAuth standard, which provides delegated authorization from service to service and transmission of identifiers.

Figure 4 reflects the planned functionality of Oracle Identity Cloud Services, there are two types of solutions: a corporate solution with a set of applications for which one-time security is provided, with IdM, etc., and a cloud infrastructure, and these two environments need to be connected in order not to it was necessary to immediately migrate to the cloud, and it was possible to use technologies from both the corporate solution and the cloud — to take the best of both worlds.
When a user receives an Identity Cloud Services administrator account, he must select a set of applications, bind these applications to users, synchronize the list of users with the local repository, organize the list of roles that will be used in applications, create groups of users who will get access to the applications, - that is, to actually do all that IdM is doing now.
It is this workflow that will be implemented in IDCS. In terms of managing applications, IDCS offers the following options: choosing from a list of pre-registered applications or registering new ones (OAuth or SAML), entering an administrative account in the application, linking domain user groups to an application, registering, generating identifiers and keys, describing and adding resources, management of authorization methods in the OAuth specification, connection of the SP profile, and provision of access to users and groups of users to the application.
Next, work with users. You can activate, deactivate the user, force the user to reset the password at the entrance, bind certain policies to change the password to the user, etc. When the user logs into his own system, he is provided with self-service capabilities: a list of available applications, registration of an account for applications, changing his own Attributes - so he did not bother the administrator.
Finally, on the internal capabilities of the service instance. The user can configure notifications of end users and administrators, register identity providers, enable federated SSO, select IdP, register trusted partners (OAuth and SAML), change password policy, describe connection parameters with corporate LDAP directory for account synchronization, assign users with administrative rights , change the appearance of the graphical interface, enable diagnostic mode, and work with network security (i.e., with a list of addresses that can allow access to the system, etc.), and configure SSO.
The task management toolkit allows you to select tasks from a predefined list.
As resources for studying IdM and IDCS, we recommend (articles on IDCS will appear as official announcements appear):
- www.facebook.com/russianidmclub (page of the club of Russian architects IdM)
- www.easyoraidm.ru (Oracle Identity Governance blog)
- security-orcl.blogspot.ru (the pre-sale team’s team on information security in the Moscow office of Oracle)
Source: https://habr.com/ru/post/304700/
All Articles