Example of a keepass database for a network administrator

We all store or store passwords from network devices in excel files. Of course, it also happens that you do not need to store anything, since the account on all devices is the same, I hope readers understand that I’m not talking about RADIUS or TACACS, but about the situation when the account is really the same.
When you start a network, it is not always possible to raise some NCM to control a new brainchild. When you have few devices and resources are limited, a text document or excel spreadsheet seems to be the best means of storing data, but deep down we all understand that this is not so.
')
Well, if your company has the resources and indicated a steady growth. In this case, at some point you are deploying a network management application. But someone, ultimately, remains at the level of “control-control”, due to lack of resources, and maybe for other reasons. For these people, this article. I will tell you how to get away from excel, make storing passwords more convenient, and get some automation on typical gestures. Note : all descriptions for Windows environment.
As you guessed from the header, I advise you to use a keepass database for storing credentials. I will not be waving colorful posters and agitate for keepass least because it has been done to me dozens of times before. I'll just show how I use it and how it helps me. Based on my experience, you already decide whether to export data from your favorite txt file. I said to export, and not carry it manually, because for this there are so many tools, and even the most confusing excel can be transferred to keepass very easily.
And so we begin. I keep the data in the form of devices broken down by device type, but this is not necessary, since the search in keepass finds combinations of characters even in the middle of a word (but unfortunately regexp does not know how). For a start, I create a sample device template. I add new fields to standard fields, depending on devices, for example, for Cisco devices, this field is enable. I also add common fields, for example lan, in which the ip address of the local interface will live. If you are going to export data, then templates should be thought out in advance. Despite the possibility of mass editing, it is better to provide everything at once. For each type of device, I provide my own template, because it is obvious that the server will not have to connect to Windows via ssh, and to the Cisco router via RDP. That is why I propose to develop storage templates that would not produce extra empty fields. In principle, for simple data storage, this is enough, but I promised automation and here it is.
We will need the KPEnhancedEntryView plugin. This extension allows you to view and edit the database from a single window. To install, download the plug-in file from the official keepass website and simply copy it to the folder with the installed program.
Keepass with this plugin understands links like CMD: // for running the windows command line. The field values can be transferred as variables, which is what I use.
Important! In the PATH variable from the Windows environment, you must add the paths to the applications that you will use. For example, I use putty and psexec, so I added the paths to these programs to the variable
Next, you can form application launch commands with parameters directly from Keepass. In order for the string to be perceived as a link, it must be started with the < symbol and ended with the > symbol. Below is the line for connecting to the device via ssh using putty:
<cmd://PuTTY.exe -ssh {S:isp1} -l {USERNAME} -pw {PASSWORD}> Due to the internal variables, the string will be passed to the CMD as follows:
PuTTY.exe -ssh 97.161.16.54 -l user1 -pw 1234567890 The string wrapped in <> is perceived as a link and now when you click on this link via keepass, the putty program will be automatically called and the device parameters will be transferred to it. The passed parameters can be any keepass fields. Parameters should be wrapped in braces {} . For standard parameters, the names are reserved, for example {USERNAME} and {PASSWORD}. If you created the parameter, you should add a Latin letter S with a colon to its name at the beginning, this is how it looks for the transfer of the lan parameter: {S: lan} . In this simple way, you can run the client application to connect using any protocol from telnet to rdp.
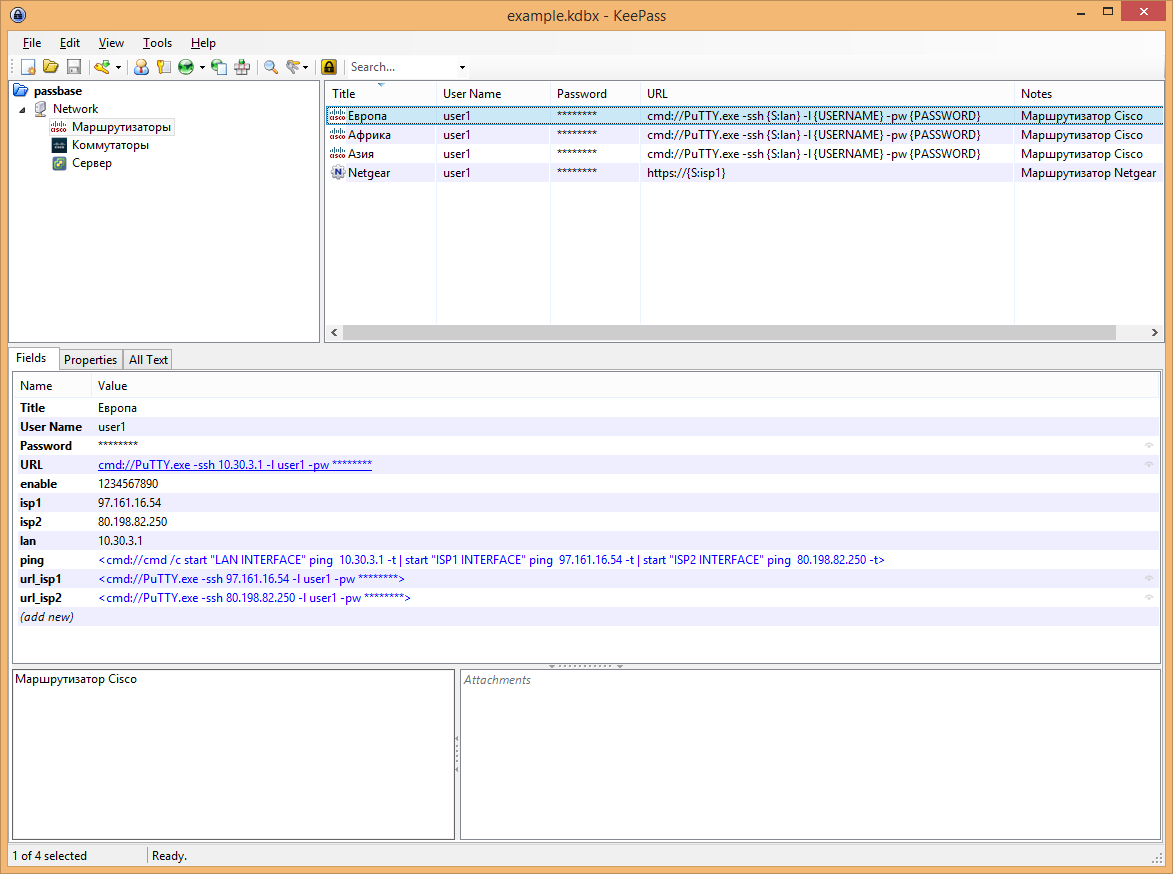
I also use these links to automate the tracing of devices. For example, ping all ip addresses of a device:
<cmd://cmd /c start "LAN INTERFACE" ping {S:lan} -t | start "ISP1 INTERFACE" ping {S:isp1} -t | start "ISP2 INTERFACE" ping {S:isp2} -t> I use psexec so I can get help data from remote windows hosts
<cmd://psexec \\{S:lan} cmd.exe /k tracert -d 8.8.8.8> You can run applications on a remote host to test network bandwidth (after installing it there)
<cmd://psexec \\{S:lan} cmd.exe /k iperf -s> In addition, I attach a base template so that you can substitute your data there and see how it works. Template base
Password from the base habrahabr
PS Another advantage of the KPEnhancedEntryView plug-in, which you will definitely appreciate, is that it makes it easy to leave notes and file attachments for each device.
UPD A couple of edits based on the discussion in the comments
MrJeos when sending a password in the application launch parameters, it can be seen in the task list
cmepthuk There is a mitm script to keepass the application. Disable automatic updates or download the latest version of the application where this vulnerability has been fixed.
Source: https://habr.com/ru/post/304680/
All Articles