One unobvious vulnerability of some VKontakte groups
Suppose a certain organization has a task - to register an official group or a VKontakte page. The question immediately arises - from which account to do it? What if users go to an employee’s page, see a nudity, dismemberment there and that's all? The personal page after all should not meet corporate standards. An idea arises - to register a new “work” account.
New accounts on vk.com should be tied to the phone. Personal phone numbers of employees, as a rule, are already used for their personal pages, and it’s not very correct for a working account to use non-working SIM cards. In this situation, it seems a logical decision to go to the subway and buy a new SIM card to link it to a working account.
As a result, Simka is bought, an account is registered from which the community is being created. After this, the development, filling and promotion of the organization’s representation in the social network begins.
')
The group grows, news is written, users actively like, comment and repost. There is even a whole staff of moderators and community administrators to support all sufferers. But in all this idyll there is a vulnerable link - the account of the creator of the community.
The "working" SIM card safely lain in the drawer of the table for a couple of years, as unnecessary. The money on it was expropriated by the operator with the help of automatically connected services. The number has been disabled for inactivity.
The working account in the social network all this time has been authorized in the working browser on the working computer. But then the need for it disappeared, as other employees took up the administration.
Vulnerability lies in the sim card. Operators quickly return inactive phone numbers to the market. And if this number gets to a curious lover of social networks, then there is a non-zero probability that he wants to restore the account to which this number was attached earlier. And the social network itself will help him with its reminders.
Here you need to understand that the account of the creator of the group gives you the opportunity to administer it. Moderators of the group can degrade administrators. Administrators can be removed by other administrators, and the creator of the group can manage all of them combined.
At one point, our wonderful corporate group can turn into a pumpkin with a hat advertising.
Ordinary mortals who do not have access to the Singer’s house do not have the ability to change information about the creator of the groups. Therefore, you need to contact technical support VKontakte.
They offer to go through not the easiest quest to compose a strange-looking piece of paper and sign it with the big bosses.
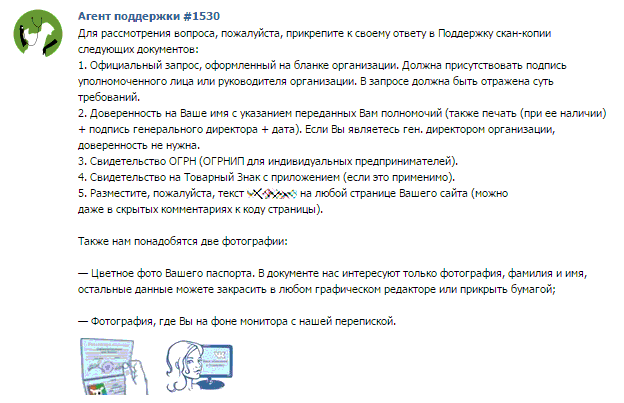
If you manage to collect all this, the account will be successfully changed. Thus, the vulnerability will be eliminated.
I suggest that anyone who could be in this situation check the security of the creator’s account. After all, no one wants to lose what is acquired by overworking =)
A little catch
New accounts on vk.com should be tied to the phone. Personal phone numbers of employees, as a rule, are already used for their personal pages, and it’s not very correct for a working account to use non-working SIM cards. In this situation, it seems a logical decision to go to the subway and buy a new SIM card to link it to a working account.
As a result, Simka is bought, an account is registered from which the community is being created. After this, the development, filling and promotion of the organization’s representation in the social network begins.
')
It takes several years
The group grows, news is written, users actively like, comment and repost. There is even a whole staff of moderators and community administrators to support all sufferers. But in all this idyll there is a vulnerable link - the account of the creator of the community.
The "working" SIM card safely lain in the drawer of the table for a couple of years, as unnecessary. The money on it was expropriated by the operator with the help of automatically connected services. The number has been disabled for inactivity.
The working account in the social network all this time has been authorized in the working browser on the working computer. But then the need for it disappeared, as other employees took up the administration.
What is the vulnerability?
Vulnerability lies in the sim card. Operators quickly return inactive phone numbers to the market. And if this number gets to a curious lover of social networks, then there is a non-zero probability that he wants to restore the account to which this number was attached earlier. And the social network itself will help him with its reminders.
Here you need to understand that the account of the creator of the group gives you the opportunity to administer it. Moderators of the group can degrade administrators. Administrators can be removed by other administrators, and the creator of the group can manage all of them combined.
At one point, our wonderful corporate group can turn into a pumpkin with a hat advertising.
What to do?
Ordinary mortals who do not have access to the Singer’s house do not have the ability to change information about the creator of the groups. Therefore, you need to contact technical support VKontakte.
They offer to go through not the easiest quest to compose a strange-looking piece of paper and sign it with the big bosses.

If you manage to collect all this, the account will be successfully changed. Thus, the vulnerability will be eliminated.
Total
I suggest that anyone who could be in this situation check the security of the creator’s account. After all, no one wants to lose what is acquired by overworking =)
UPD.
the “Development” stream does not correspond to the topic of the note, but it is in it that the Information Security hub is locatedSource: https://habr.com/ru/post/304646/
All Articles