Emsisoft experts found another JavaScript extortionist
In early January, we wrote about the discovery of a security company, Emsisoft, which discovered an extortionist (ransomware), entirely written in JavaScript. The extortionist was called Ransom32. In the new case, we are also talking about the extortionist for JavaScript, which was called the RAA. The malicious program encrypts the user's files using the symmetric AES algorithm, and also installs another known malicious program in the user's system — the Pony password thief (Fareit). ESET antivirus products detect ransomware as JS / TrojanDropper.Agent .

Unlike Ransom32, RAA does not use the NW.js framework for its work. This framework allows you to develop JavaScript applications for Windows, OS X and Linux. To work with encryption functions, RAA uses the CryptoJS cryptographic library. It is used to encrypt user files. The Pony password thief installed into the user’s system is detected by ESET AV products as Win32 / PSW.Fareit.A .
')
Malware is usually distributed using a malicious attachment in an email message. This attachment is masked as a Word document (.doc). To disguise its malicious functions, the malware drops a special file into the% userprofile% \ documents directory and tries to open it using WordPad.
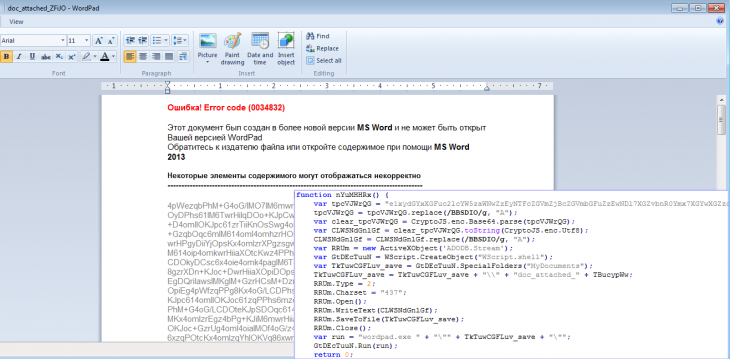
Fig. Fake damaged document being dumped to disk ( Emsisoft data ).
To ensure its survival in the system after a reboot, the extortionist is registered in the well-known Run section of the registry. The value of the parameter indicates the path to the original dropper.
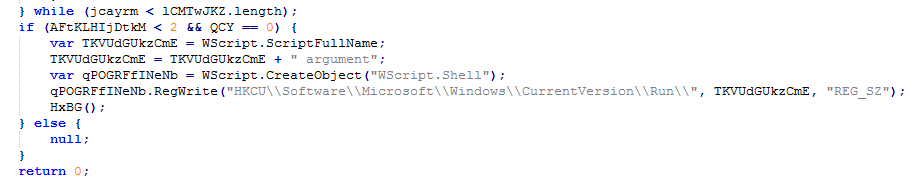
Fig. The malicious program creates a parameter for its autoload ( Emsisoft data ).
The Extortioner also removes the Volume Shadow Service (VSS) volume shadowing service. Such an operation is performed in order to ensure that the user cannot restore the original copies of the files after they are encrypted (File History setting). As a result of this, when trying to restore a file to its previous version, the operation fails, just like when trying to access System Restore.
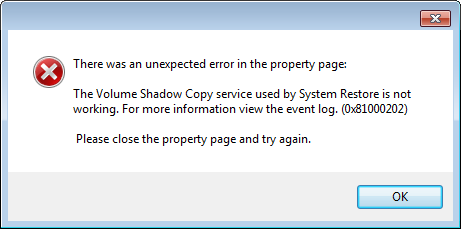
Fig. Error message when trying to recover an encrypted file using VSS ( Emsisoft data ).
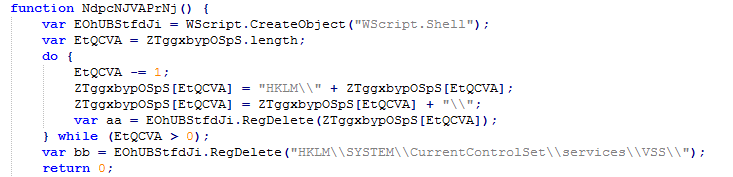
Fig. VSS service removal function ( Emsisoft data ).
The next step is to encrypt files using the CryptoJS library. Encrypted files receive an additional extension .locked.
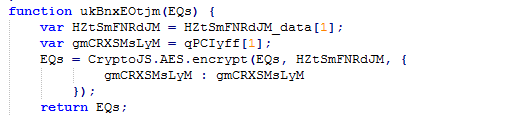
Fig. Encryption function ( Emsisoft data ).
Extortionist encrypts files with the following extensions .doc, .xls, .rtf, .pdf, .dbf, .jpg, .dwg, .cdr, .psd, .cd, .mdb, .png, .lcd, .zip, .rar .csv. Files that contain ".locked", "~" or "$" characters in the name are skipped.
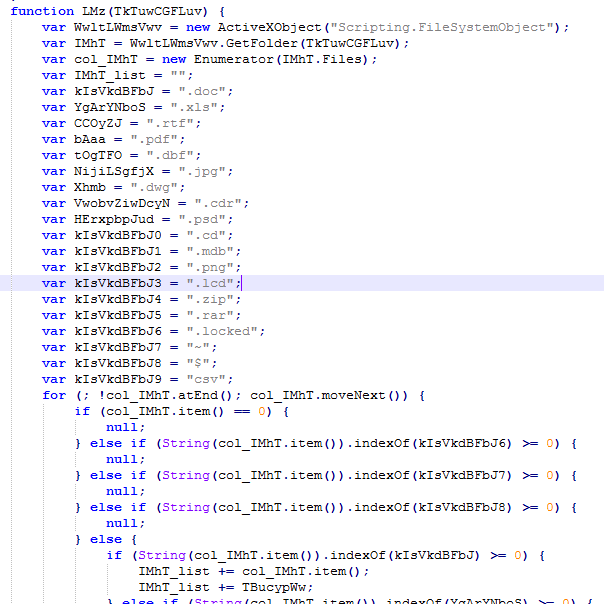
Fig. A list of file extensions for encryption and excluded by the lines in the names ( Emsisoft data ).
Files that are contained in the following directories are excluded from the encryption process Program Files, Program Files (x86), Windows, Recycle.Bin, Recycler, AppData, Temp, ProgramData, and Microsoft.
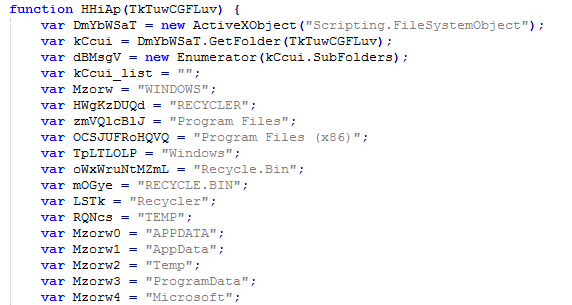
Fig. List of directories to exclude ( Emsisoft data ).
The redemption message is stored in a special file !!! README !!! [unique ID] .rtf, which is created on the desktop. From the user require a ransom in the amount of 0.39 bitcoins or $ 250. The contents of the file are shown below.

Fig. Text with redemption payment instructions ( Emsisoft data ).
At the beginning, we indicated that the extortionist executes a file of another malicious program on the user's system - Pony, which is a password hijacker. The Pony executable file is stored at the following location% userprofile% \ documents \ st.exe. It is included in the extortioner's JS-dropper and encoded using base64. The malware specializes in stealing sensitive user data, such as passwords from various services.
Malware samples have the following SHA1 identifiers:
RAA: 2c0b5637701c83b7b2aeabdf3120a89db1dbaad7
Pony: 822bf6d0eb04df65c072b51100c5c852761e7c9e
Unfortunately, decrypting user files that have been encrypted by the RAA is currently not possible, which, once again, speaks of the importance of using data backup in a timely manner.

Unlike Ransom32, RAA does not use the NW.js framework for its work. This framework allows you to develop JavaScript applications for Windows, OS X and Linux. To work with encryption functions, RAA uses the CryptoJS cryptographic library. It is used to encrypt user files. The Pony password thief installed into the user’s system is detected by ESET AV products as Win32 / PSW.Fareit.A .
')
Malware is usually distributed using a malicious attachment in an email message. This attachment is masked as a Word document (.doc). To disguise its malicious functions, the malware drops a special file into the% userprofile% \ documents directory and tries to open it using WordPad.

Fig. Fake damaged document being dumped to disk ( Emsisoft data ).
To ensure its survival in the system after a reboot, the extortionist is registered in the well-known Run section of the registry. The value of the parameter indicates the path to the original dropper.

Fig. The malicious program creates a parameter for its autoload ( Emsisoft data ).
The Extortioner also removes the Volume Shadow Service (VSS) volume shadowing service. Such an operation is performed in order to ensure that the user cannot restore the original copies of the files after they are encrypted (File History setting). As a result of this, when trying to restore a file to its previous version, the operation fails, just like when trying to access System Restore.

Fig. Error message when trying to recover an encrypted file using VSS ( Emsisoft data ).

Fig. VSS service removal function ( Emsisoft data ).
The next step is to encrypt files using the CryptoJS library. Encrypted files receive an additional extension .locked.

Fig. Encryption function ( Emsisoft data ).
Extortionist encrypts files with the following extensions .doc, .xls, .rtf, .pdf, .dbf, .jpg, .dwg, .cdr, .psd, .cd, .mdb, .png, .lcd, .zip, .rar .csv. Files that contain ".locked", "~" or "$" characters in the name are skipped.

Fig. A list of file extensions for encryption and excluded by the lines in the names ( Emsisoft data ).
Files that are contained in the following directories are excluded from the encryption process Program Files, Program Files (x86), Windows, Recycle.Bin, Recycler, AppData, Temp, ProgramData, and Microsoft.

Fig. List of directories to exclude ( Emsisoft data ).
The redemption message is stored in a special file !!! README !!! [unique ID] .rtf, which is created on the desktop. From the user require a ransom in the amount of 0.39 bitcoins or $ 250. The contents of the file are shown below.

Fig. Text with redemption payment instructions ( Emsisoft data ).
At the beginning, we indicated that the extortionist executes a file of another malicious program on the user's system - Pony, which is a password hijacker. The Pony executable file is stored at the following location% userprofile% \ documents \ st.exe. It is included in the extortioner's JS-dropper and encoded using base64. The malware specializes in stealing sensitive user data, such as passwords from various services.
Malware samples have the following SHA1 identifiers:
RAA: 2c0b5637701c83b7b2aeabdf3120a89db1dbaad7
Pony: 822bf6d0eb04df65c072b51100c5c852761e7c9e
Unfortunately, decrypting user files that have been encrypted by the RAA is currently not possible, which, once again, speaks of the importance of using data backup in a timely manner.
Source: https://habr.com/ru/post/303752/
All Articles