High-Density WiFi. Part 3: About technology. Part 4: About Money
" Go to my team and you will never be second"
Jose Mourinho

Now let's talk about each block from which the correct HD WiFi networks of Aruba are built. Let's start with the most important block of HD WiFi infrastructure - the block of radio environment optimization, without which the HD network operation is impossible in principle. Once again, briefly recall the main difficulties of building HD WiFi networks:
')
To ensure that the network functions normally in a complex HD environment and each user is provided with the maximum level of service, Aruba has several built-in optimization mechanisms, briefly summarized in the table below:
Table 1. WiFi optimization mechanisms
The main burden of optimizing the radio part of the network rests on the ARM mechanism, which provides the following functionality of the WiFi network:
Another very important mechanism for optimizing the radio environment when deploying HD WiFi is Cell Size Reduction (CSR), which allows for artificially overestimating the threshold of sensitivity of a point (RST, Receive Sensitivity Tuning-Based Channel Reuse) to provide some immunity to interference like ACI and, in part, CCI. Sensitivity to receive (Receiving Sensitivity) points determines the minimum signal level at which the device can receive and decode a WiFi frame. If the WiFi frame comes with a signal level below the threshold, then the dot does not decode it and treats it as noise on the channel. In the case of HD WiFi, the signal level both at the point and at the client will always be quite high due to the close distance between them and the main network failures occur due to interference, and not the signal level. Therefore, the RST algorithm measures the signal levels between the point and the clients associated with it and sets the sensitivity level of the points based on the weakest signal level from the clients associated with the point. The process is dynamic, the sensitivity level adjusts to the current radio environment. Thus, the signal from remote points and clients not associated with this point is ignored and the channel can be reused at this point.
Another mechanism that allows to save the resource of the radio environment is the imposition of restrictions on non-obligatory broadcasts, multicasts, and “chatty” protocols. For example, to send a request to all devices in the ARP domain is expensive and not always necessary. The Aruba network can convert Broadcast traffic into a unicast request for a specific client (“broadcast-filter-arp”) or, if the network starts a broadcast storm, filter all Broadcast / Multicast traffic (“broadcast-filter-all”). It is necessary to use this mechanism with care so as not to filter out all the useful traffic, for example, the broadcast-filter-all command line should only be used together with broadcast-filter-arp.
Chatty protocols also eat up a lot of resources and Aruba in its HD networks strongly recommends restricting their traffic using ACLs, for example:
In conclusion of the talk about radio optimization, I would like to mention such an important point as roaming. And not just roaming, but inter-band roaming, when the client moves from the 5Ghz to 2.4Ghz range and back as it moves along the WiFi infrastructure. Such a task often arises when moving from closed rooms (where 5Ghz is more commonly used now) to open rooms (where 2.4Ghz is more often used). As a rule, most vendors cope with fast roaming within the range, but as soon as
in most cases, a delay of several seconds occurs and the connection is broken. The problem of fast inter-band roaming is quite complex and there may be several reasons why the connection is interrupted. Most often this is due to the limitations and features of the client. But, if the client is modern and supports such extensions of the 802.11 standard as 802.11r, 802.11k and / or 802.11v (allowing you to cache the data of authentication / authorization sessions and “see” the network topology around you), then the vendor from the Premier League, as a rule It has technologies that allow you to organize inter-band roaming without interruption of communication. In Aruba, this technology calls ClientMatch. It allows, under certain conditions, to quickly “transfer” the client to a new channel without the standard procedure of scanning the air, which significantly reduces the time for the client to move to a new point.
Now let's talk about an equally important solution block - the integrated firewall system. In the wireless world of Aruba is known, including the high level of security of its solutions. Aruba is the first vendor to support the 802.11i standard (WPA2), the first vendor to have integrated Wirelss IPS (WIPS), one of the first vendors to receive FIPS certificates (allowing them to sell their solutions to the US government), one of the first vendors to receive certification ICSA, the first vendor to integrate a full-fledged firewall into its wireless solution. The main principle on which the security system of Aruba is built is that anyone using a wireless network can be an employee with a laptop, a hired contractor, a guest, a barcode reader, a printer, a VoIP phone, or an attacker who tries to hack the network, but if the user is logged on , logged in and authenticated in accordance with the policy attached to his role, then ANY user actions should not lead to a breach of information security.
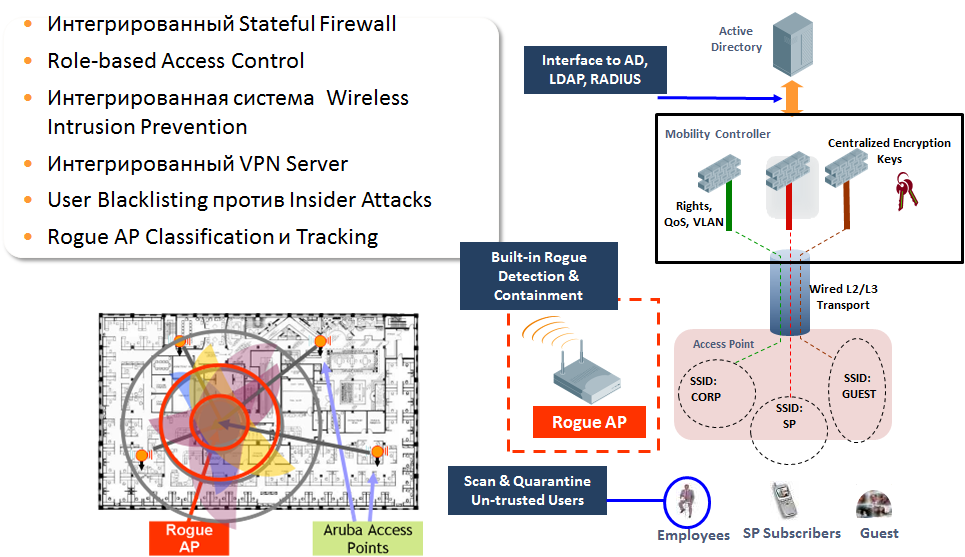
Figure 7. Network Security System
Many devices, with a mass of diverse applications, collected in one place require a deep understanding of traffic from the network operator to ensure the appropriate quality of service and level of security. To ensure this, a full-fledged NG FW is built into the Aruba solutions, which is able to define network applications, include them in the traffic control rules of the wireless infrastructure and can:
Figure 8. NGFW
The use of a functional firewall built into the wireless infrastructure allows you to cut off attacks on the network directly at the access level, instead of pulling parasitic traffic to a detached security system and back, loading internal network resources.
Since the HD WiFi infrastructure operates mainly under maximum load, and, besides, there are great chances in the crowd to go unnoticed, there is a temptation to take advantage of the situation and try to hack the network. Therefore, the next, extremely important part of the network security system in HD WiFi is Wireless IPS. The main functionality of Aruba WIPS is summarized in the following table:
Table 2. Functional Aruba WIPS
As can be seen from the table, some of the functions of this system are present in the basic software solutions Aruba, the other part opens with an additional license.
Monitoring of the radio environment can be organized in two different ways - using regular access points and using specialized monitoring points. In the first case, the regular points will allocate certain periods of time between the transmission of client traffic to scan channels for information security threats. In the second case, the specialized point-monitor (hereinafter referred to as the monitor) does not transmit client traffic in general and devotes all the time to scanning the radio. Each approach has its advantages and what approach to use is to be determined in each specific case, depending on the conditions and the task. Comparison of some aspects of the work of WIPS with different approaches are given in Table 3, which summarizes the main functions of WIPS that are important when implementing HD WiFi networks.
Table 3. Description of the main functions of WIPS
A few more recent comments on the implementation of WIPS in HD networks:
Before talking about the next solution block, I would like readers to ask themselves a question - why do people need a net at the stadium? What are they doing to her? If you look at the traffic profile, the answer becomes obvious - they mostly consume and distribute photos and videos. They shoot themselves, the field, the neighbors, make videos and put it all conditionally on Instagram / Facebook and during breaks they watch what their friends put on Instagram / Facebook. Therefore, the traffic in HD WiFi is not only a lot, but it is also specifically profiled, with the vast majority of multimedia content in the stream. And this type of traffic, as is known, is sensitive not only to the band, but also to delays and other parameters of network quality. And this traffic can be generated in a variety of ways and applications.
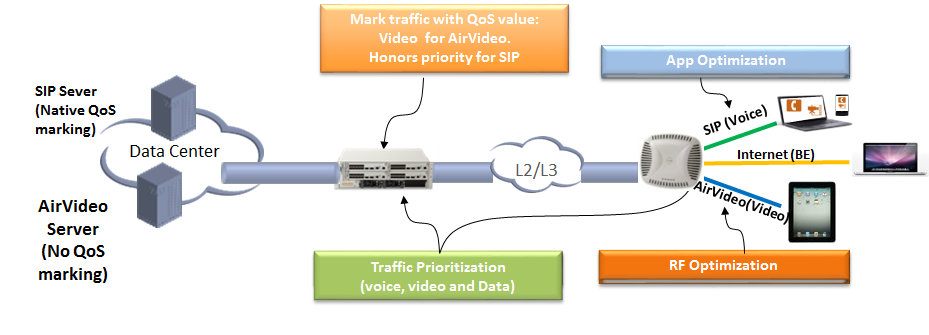
Figure 9. QoS for tagged and untagged traffic
Therefore, the HD WiFi solution should provide appropriate QoS not only for the types of traffic, but for the applications that generate this traffic. The Aruba Application Fingerprinting technology and DPI’s built-in solution allow you to classify traffic according to the protocols of all (6) levels of the OSI model and then, using appropriate policies, apply the necessary rules to the traffic. Including, setting the required QoS parameters on multimedia streams with appropriate subsequent processing, for example, increasing the bandwidth for multimedia traffic. Key components of the Application Fingerprinting Multimedia Quality Optimization Technology include:
The last block of the HD WiFi solution, which is worth mentioning, is an intelligent infrastructure management system, including network security management systems, with which we will begin.
The core of the security management system is the ClearPass platform, which can
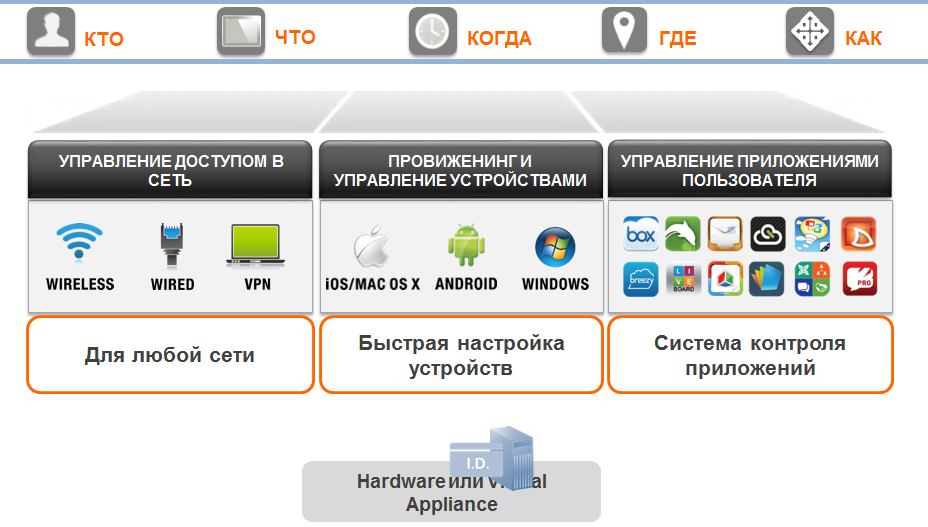
Figure 10. Aruba ClearPass
Using ClearPass in HD WiFi makes it much easier to control access to the network. If we correctly design the access system, the client portal and correctly configure management policies and devices provisioning, then the task of ensuring security at the network’s border actually comes down to applying the developed policies to the network and tracking incidents, followed by analysis.
In order to manage complex HD WiFi infrastructure, search for and solve potential problems, a network management system is needed in which this would be done simply and clearly. There is such a system in Aruba, it is called Airwave and it provides:
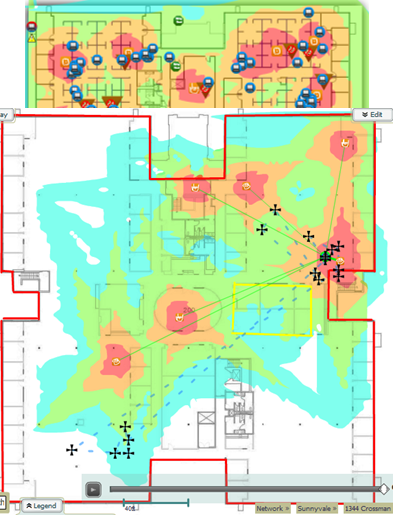
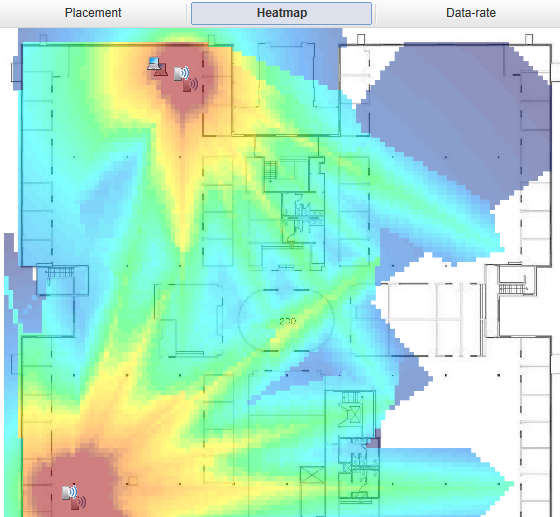
Figure 11. An example of “heat charts” in Airwave
And the last thing I would like to mention in this technological part is about people. No supertechnologies will save the project if it is made with “curved” hands. No solutions will work normally if they are set up, configured and launched without a proper understanding of the purpose and essence of the task. Therefore, the conclusion is simple - do not save on the service! As the classic said, “so that it would not be excruciatingly painful afterwards,” it is better to let a person who has such experience and resources do the HD WiFi network.
“It doesn't matter what they are talking about - it is always about money”
Todd's second law
Now the most important question - why do we need HD WiFi? Well, really - why, by and large, the WiFi network in the stadium? So that users can online throw their selfy online? What is the use of this to the stadium owner, who has borne the cost of
And it will bear the cost of its
Why does the stadium owner need all this? The answer is very simple - HD WiFi can and should be monetized, i.e. earn money on it. At the same time, the old-fashioned way to sell guest accounts along with tickets now works poorly. The crisis, people save on everything and push along with the ticket also “just access to the network” becomes difficult. Moreover, no one has canceled mobile 3G / LTE networks and mobile operators are building their infrastructure also taking into account the potential congestion. Therefore, the need to monetize the network with the help of additional services that will
And here the vendors from the Premier League again compare favorably with all other manufacturers of WiFi "iron". First, most of them have ready-made service platforms on which you can deploy additional services for users of your network and, secondly, as a rule, they have a developed partner network that complements the ability to monetize HD WiFi with different proprietary applications.
Returning to Aruba, I must say that it has not just a platform, but a whole service infrastructure that allows the flexible implementation of various additional services over an HD WiFi network. This infrastructure includes
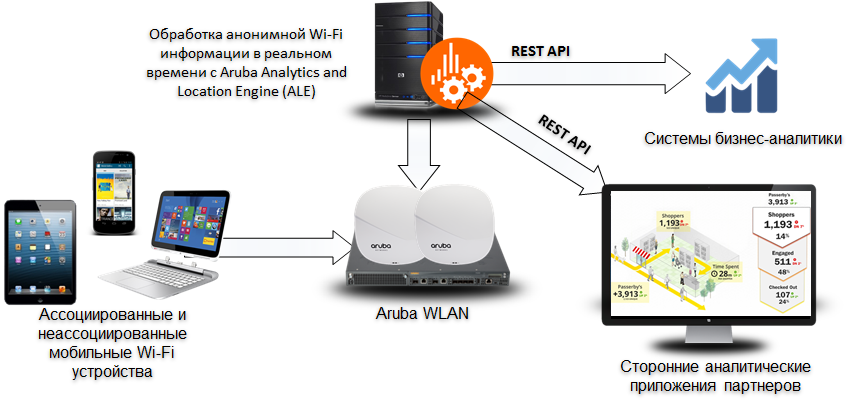
Figure 12. Analytics and Location Engine
The presence of these tools makes it necessary to rethink the very purpose of introducing a WiFi network. For example, geo-positioning data allows you to implement a service for interactive user routing within a network, such an “in-door GPS”. This is extremely useful and, as practice proves, the demanded service, for example, in large stores, where, according to statistics, the main reason for refusals from a planned purchase is the inability of the buyer to find the right product on the shelves. From personal experience, the main question for sales assistants in Auchan / Okay / Leroy-Merlin stores is “Where can I find it?”. The presence of additional infrastructure from Bluetooth beacons allows making geo-positioning very accurate, up to 1 meter and, accordingly, routing and navigation inside the store is also very accurate and substantive. For example, the presence of beacons under the seats of chairs in one of the stadiums made it possible to implement geolocation services, the flesh to a specific seat.
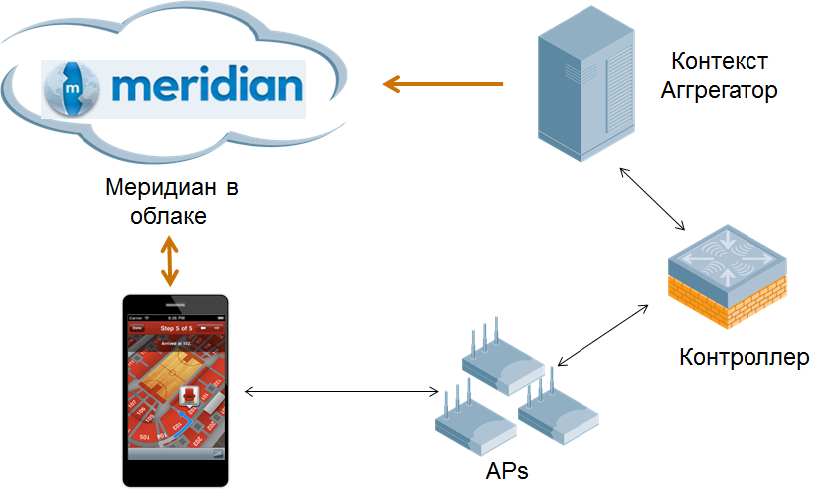
Figure 13. Meridian Platform
Another popular way to monetize geo-positioning data is to use an advertising model when a user, passing by certain places on the map, receives pop-up contextual advertising, tied specifically to the place where he is now. For example, if you go to a large shopping center, then as an advertisement, pop-up windows may appear about the sales in the stores that you pass by. The Meridian service platform provides subscribers with access to the API, with which developers can make almost any application based on geolocation data and maps loaded into the platform. Further, in addition to intelligent routing / navigation in the room and contextual advertising, the use of this data is limited only by your imagination.
Another approach to monetizing WiFi networks is to use an affiliate model. Premier division vendors, as already mentioned above, usually build partnerships with many developers of specialized applications that can be integrated into a deployed HD WiFi infrastructure. For example, YinzCam is a long-time Aruba partner in specialized applications for sports events. Using their solutions, YinzCam can provide additional services to fans, such as repeating key moments and / or the whole match, viewing game moments from different angles of different cameras, ordering food and drinks, loyalty programs for fans, etc.

Figure 14. YinzCam applications
Another example of monetization with the help of an advertising model is the use of solutions such as the RaGaPa advertising platform. Using this platform, they can disassemble HTTP traffic and insert contextual advertising in it, which is specific to this advertising company and is stored in the specialized RaGaPa cloud.
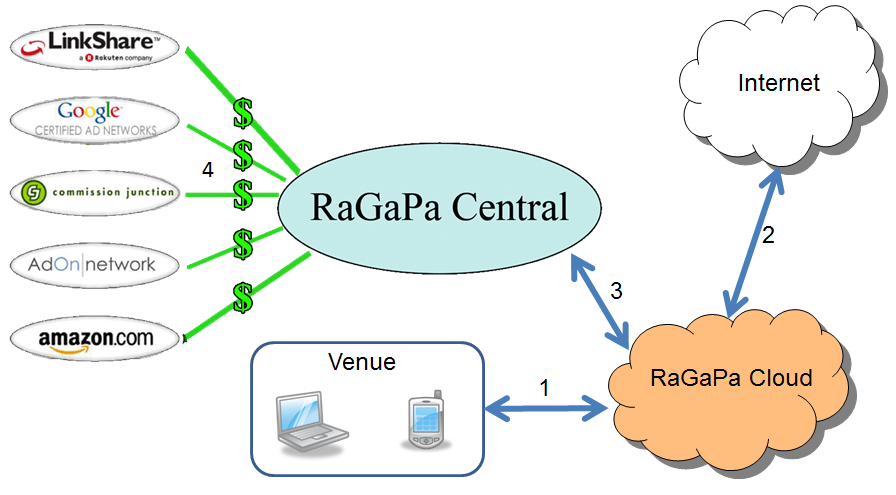
Figure 15. RaGaPa Solution
Summarizing the above, I would like to emphasize once again the following key idea - you should not consider the HD WiFi infrastructure as the next “cost center” that will eat up the resources of your company. With the right approach, HD WiFi infrastructure can become a serious "profit generating center."
Jose Mourinho

Now let's talk about each block from which the correct HD WiFi networks of Aruba are built. Let's start with the most important block of HD WiFi infrastructure - the block of radio environment optimization, without which the HD network operation is impossible in principle. Once again, briefly recall the main difficulties of building HD WiFi networks:
')
- WiFi works in the unlicensed spectrum - a huge number of interference sources
- Often WiFi networks intersect each other, competing for radio resource
- Many non-WiFi devices can affect the WiFi network, reducing its performance (Bluetooth, AV Systems, etc.)
- Radio environment in HD networks is very dynamic, changing extremely fast and surging
To ensure that the network functions normally in a complex HD environment and each user is provided with the maximum level of service, Aruba has several built-in optimization mechanisms, briefly summarized in the table below:
Table 1. WiFi optimization mechanisms
| Optimal distribution of radio channels | Optimum customer distribution | Optimal power management | Optimal access control |
|
|
|
|
The main burden of optimizing the radio part of the network rests on the ARM mechanism, which provides the following functionality of the WiFi network:
- Distributes clients optimally to radio channels available on the network, not to access points (Spectrum Load Balancing), when the key parameter for channel selection is the number of clients per channel, not the number of clients per access point
- Switches dual-band clients that support both 2.4Ghz and 5Ghz bands to the 5Ghz band (Band Steering)
- Sets each client temporary restrictions on access to the environment, evenly distributing the load between them (Air-Time Fairness)
Another very important mechanism for optimizing the radio environment when deploying HD WiFi is Cell Size Reduction (CSR), which allows for artificially overestimating the threshold of sensitivity of a point (RST, Receive Sensitivity Tuning-Based Channel Reuse) to provide some immunity to interference like ACI and, in part, CCI. Sensitivity to receive (Receiving Sensitivity) points determines the minimum signal level at which the device can receive and decode a WiFi frame. If the WiFi frame comes with a signal level below the threshold, then the dot does not decode it and treats it as noise on the channel. In the case of HD WiFi, the signal level both at the point and at the client will always be quite high due to the close distance between them and the main network failures occur due to interference, and not the signal level. Therefore, the RST algorithm measures the signal levels between the point and the clients associated with it and sets the sensitivity level of the points based on the weakest signal level from the clients associated with the point. The process is dynamic, the sensitivity level adjusts to the current radio environment. Thus, the signal from remote points and clients not associated with this point is ignored and the channel can be reused at this point.
Another mechanism that allows to save the resource of the radio environment is the imposition of restrictions on non-obligatory broadcasts, multicasts, and “chatty” protocols. For example, to send a request to all devices in the ARP domain is expensive and not always necessary. The Aruba network can convert Broadcast traffic into a unicast request for a specific client (“broadcast-filter-arp”) or, if the network starts a broadcast storm, filter all Broadcast / Multicast traffic (“broadcast-filter-all”). It is necessary to use this mechanism with care so as not to filter out all the useful traffic, for example, the broadcast-filter-all command line should only be used together with broadcast-filter-arp.
Chatty protocols also eat up a lot of resources and Aruba in its HD networks strongly recommends restricting their traffic using ACLs, for example:
- Limit which devices users can work with in the HD domain (for example, in the CLI using the local-valid users firewall command)
- Disable IPv6 if not needed
- Disable netbios-ns, netbios-dgm, mDNS, UPnP and SSDP if they are not needed (most of the devices that actually use these protocols are “wired” computers and can easily do without them in a wireless network)
- Try to filter out various random errors (for example, filter the 68 UDP port in advance so that the client cannot accidentally become a DHCP server)
- Ban STP
In conclusion of the talk about radio optimization, I would like to mention such an important point as roaming. And not just roaming, but inter-band roaming, when the client moves from the 5Ghz to 2.4Ghz range and back as it moves along the WiFi infrastructure. Such a task often arises when moving from closed rooms (where 5Ghz is more commonly used now) to open rooms (where 2.4Ghz is more often used). As a rule, most vendors cope with fast roaming within the range, but as soon as
- the client switches between channels in different ranges and
- the client is experiencing delay-sensitive traffic (for example, a voice or video call) at the time of the channel transition,
in most cases, a delay of several seconds occurs and the connection is broken. The problem of fast inter-band roaming is quite complex and there may be several reasons why the connection is interrupted. Most often this is due to the limitations and features of the client. But, if the client is modern and supports such extensions of the 802.11 standard as 802.11r, 802.11k and / or 802.11v (allowing you to cache the data of authentication / authorization sessions and “see” the network topology around you), then the vendor from the Premier League, as a rule It has technologies that allow you to organize inter-band roaming without interruption of communication. In Aruba, this technology calls ClientMatch. It allows, under certain conditions, to quickly “transfer” the client to a new channel without the standard procedure of scanning the air, which significantly reduces the time for the client to move to a new point.
Now let's talk about an equally important solution block - the integrated firewall system. In the wireless world of Aruba is known, including the high level of security of its solutions. Aruba is the first vendor to support the 802.11i standard (WPA2), the first vendor to have integrated Wirelss IPS (WIPS), one of the first vendors to receive FIPS certificates (allowing them to sell their solutions to the US government), one of the first vendors to receive certification ICSA, the first vendor to integrate a full-fledged firewall into its wireless solution. The main principle on which the security system of Aruba is built is that anyone using a wireless network can be an employee with a laptop, a hired contractor, a guest, a barcode reader, a printer, a VoIP phone, or an attacker who tries to hack the network, but if the user is logged on , logged in and authenticated in accordance with the policy attached to his role, then ANY user actions should not lead to a breach of information security.

Figure 7. Network Security System
Many devices, with a mass of diverse applications, collected in one place require a deep understanding of traffic from the network operator to ensure the appropriate quality of service and level of security. To ensure this, a full-fledged NG FW is built into the Aruba solutions, which is able to define network applications, include them in the traffic control rules of the wireless infrastructure and can:
- Monitor traffic flows based on information in layers 2-7 of the OSI model
- Identify specific users and applications that they use and build security policies based on this information.
- Apply group policies defined in the AAA infrastructure
- Link traffic processing rules to the time of day, device type, user and application
- Disconnect users from the network when trying to bypass security rules
- Control the bandwidth of a specific connection and limit it to specific applications.
- Implement two-factor authentication

Figure 8. NGFW
The use of a functional firewall built into the wireless infrastructure allows you to cut off attacks on the network directly at the access level, instead of pulling parasitic traffic to a detached security system and back, loading internal network resources.
Since the HD WiFi infrastructure operates mainly under maximum load, and, besides, there are great chances in the crowd to go unnoticed, there is a temptation to take advantage of the situation and try to hack the network. Therefore, the next, extremely important part of the network security system in HD WiFi is Wireless IPS. The main functionality of Aruba WIPS is summarized in the following table:
Table 2. Functional Aruba WIPS
| Function | Base OS | With RF Protect license |
| Wireless detection | XXXXXXX | - |
| Air monitors | XXXXXXX | - |
| Rogue classification | XXXXXXX | - |
| Wired Rogue Containment | XXXXXXX | - |
| Wireless rogue containment | XXXXXXX | - |
| IDS Attack Signatures | - | XXXXXXX |
| Spectrum Analysis | - | XXXXXXX |
| Total watch | - | XXXXXXX |
| Tarpiting | - | XXXXXXX |
| Advanced Rogue Classification | - | XXXXXXX |
| L3 Rogue Classification | XXXXXXX | - |
| 802.11 Infrastructure Attack Detection | - | XXXXXXX |
| Impersonation detection | - | XXXXXXX |
| Authorized Client Monitoring | - | XXXXXXX |
| Malformed Packet Checks | - | XXXXXXX |
| Event correlation | - | XXXXXXX |
| Monitored AP Encryption | XXXXXXX | - |
| Ad-Hoc Network (IBSS) APs | - | XXXXXXX |
| L3 AP Wired Containment | XXXXXXX | - |
| Protect Windows Bridge | - | XXXXXXX |
| Protect Valid Station | - | XXXXXXX |
| Protect My SSID | - | XXXXXXX |
| WIP Configuration Wizard | - | XXXXXXX |
As can be seen from the table, some of the functions of this system are present in the basic software solutions Aruba, the other part opens with an additional license.
Monitoring of the radio environment can be organized in two different ways - using regular access points and using specialized monitoring points. In the first case, the regular points will allocate certain periods of time between the transmission of client traffic to scan channels for information security threats. In the second case, the specialized point-monitor (hereinafter referred to as the monitor) does not transmit client traffic in general and devotes all the time to scanning the radio. Each approach has its advantages and what approach to use is to be determined in each specific case, depending on the conditions and the task. Comparison of some aspects of the work of WIPS with different approaches are given in Table 3, which summarizes the main functions of WIPS that are important when implementing HD WiFi networks.
Table 3. Description of the main functions of WIPS
| Feature / Description | How does the access point | How the monitor works |
| Channel scan | All allowed channels, including those not in the current domain, must be configured in “scan mode” in the ARM profile. | All allowed + rare channels (for example, 4.9Ghz) are scanned, where the scan goes with an increment of 5 Mhz to search for "enemy" points in the intervals between standard channels (in MHz these are frequencies 2412-2484 and 4900-5895, with an increment of 5 MHz ). All scanned channels must be configured in 'scan mode' in the AM profile. |
| Scan methods | About every 10 seconds, the access point switches from processing data on the home channel to scanning other ranges, approximately 100 ms, which allows you not to lose buoys on the home channel. At the same time, the point spends an average of 70ms on the scanned channel, which does not guarantee the detection of an enemy point on the buoy (the buoy from it may pass unnoticed). Therefore, the point is able to detect enemy points and other service personnel or responses to special tests. | The monitor divides the channels into four groups - active, regulatory, all regulatory and rare and spends 500, 250, 200 and 100 ms on each type of channels, respectively, and the scan time of each type of channels is adjusted. By default, active and regulatory channels are preferred. |
| Wireless containment | If an enemy access point is found on a channel, the customer point will not change the home channel in order to suppress it. But if there are currently no clients on the point and the “rouge aware” parameter is set in the ARM profile, then it will change the channel and will suppress the enemy point. If the enemy point is found on the home channel, then the point will also effectively suppress its work (send de-authorization to its clients) even if clients are associated with the point. | If the access point is defined as an enemy, AM will continually return to its channel for suppression. For example, if an enemy point is detected on channel 1, then the channel scanning scheme will look something like 1, 6, 1, 2, 1, 11, 1, 3, 1, 6, 1 ... It is important that when an enemy point is detected AM does not cease to search for violators and scan other channels. |
| Tarpitting | This method of countering enemy points is more effective than Wireless Containment sending de-authorization to customers. If the detected point is classified as an enemy, then when it is suppressed, customers are forced to switch to a false channel or SSID:
| Similarly. |
| IDS signature attack detection | 100% coverage of the entire network infrastructure. The hotspot checks traffic for signs of attack during customer service. In addition, IDS signalists are checked during the scanning of other channels, which is also safe, because at this moment there is no serving access point on the home channel through which you can attack the network. | Less than 100% infrastructure coverage, because the monitor is not constantly on all channels, but scans them all in turn. More likely to detect an attack on the active channel, because the monitor spends more time on it, but this can be changed by settings (set the time for scanning channels manually) |
| Supported IDS signatures | All signal signals (100%). Some signaling systems (eg, AP Spoofing) require WIPS to work in hybrid mode in order to successfully detect an attack. | 90% + signatures, since some attacks, for example, AP Spoofing or Premature EAP Success / Failure, only WIPS based on points in the hybrid mode are detected (because they require additional information, which is only on regular access points, not on monitors). |
| Wired containment | An access point can suppress enemy points in the wired infrastructure (ARP Poisoning) if they are on the same wired network as the enemy device that the point hears on the radio. | Similarly. |
A few more recent comments on the implementation of WIPS in HD networks:
- If WIPS is based on a regular access point, then you have the entire network infrastructure covered by default; if specialized monitors are used, Aruba recommends a point-monitor ratio of at least 4: 1 (at least 4 monitors for 4 access points). At the same time, as well as access points, monitors must also be physically correctly positioned so that there are no gaps in the coverage in WIPS.
- Scanning the radio for searching for attacks / enemy points should be configured so as not to interfere with the transmission of audio / video streams that are sensitive to delays, i.e. should be suspended while active transmission of such traffic on the channel. In Aruba, this is configured in the ARM profiles.
Before talking about the next solution block, I would like readers to ask themselves a question - why do people need a net at the stadium? What are they doing to her? If you look at the traffic profile, the answer becomes obvious - they mostly consume and distribute photos and videos. They shoot themselves, the field, the neighbors, make videos and put it all conditionally on Instagram / Facebook and during breaks they watch what their friends put on Instagram / Facebook. Therefore, the traffic in HD WiFi is not only a lot, but it is also specifically profiled, with the vast majority of multimedia content in the stream. And this type of traffic, as is known, is sensitive not only to the band, but also to delays and other parameters of network quality. And this traffic can be generated in a variety of ways and applications.

Figure 9. QoS for tagged and untagged traffic
Therefore, the HD WiFi solution should provide appropriate QoS not only for the types of traffic, but for the applications that generate this traffic. The Aruba Application Fingerprinting technology and DPI’s built-in solution allow you to classify traffic according to the protocols of all (6) levels of the OSI model and then, using appropriate policies, apply the necessary rules to the traffic. Including, setting the required QoS parameters on multimedia streams with appropriate subsequent processing, for example, increasing the bandwidth for multimedia traffic. Key components of the Application Fingerprinting Multimedia Quality Optimization Technology include:
- Dynamic Multicast Optimization (DMO), which allows you to convert multicast traffic into unicast on the fly and transfer it to wireless clients without occupying the band who do not need this traffic
- Secure Signaling Awareness, providing DPI for signaling VoIP protocols (SIP, MS Lync)
- Call Protection , which adapts the radio environment using ARM and delays scanning of the radio environment if there is an active call on the point
- Full Visibility, providing full voice monitoring and reporting on the controller
- Highly Scalable, balancing load on available channels and points based on prioritization of voice and video traffic
The last block of the HD WiFi solution, which is worth mentioning, is an intelligent infrastructure management system, including network security management systems, with which we will begin.
The core of the security management system is the ClearPass platform, which can
- control user access to the network (identify the user and authorize him in different ways to different types of access, cancel certain types of user access, etc.)
- set access and network connection options for devices (for example, band limits)
- control applications installed on clients and remotely manage client devices (for example, delete data from devices, install certain patches on them, etc.)
- much more associated with:

Figure 10. Aruba ClearPass
Using ClearPass in HD WiFi makes it much easier to control access to the network. If we correctly design the access system, the client portal and correctly configure management policies and devices provisioning, then the task of ensuring security at the network’s border actually comes down to applying the developed policies to the network and tracking incidents, followed by analysis.
In order to manage complex HD WiFi infrastructure, search for and solve potential problems, a network management system is needed in which this would be done simply and clearly. There is such a system in Aruba, it is called Airwave and it provides:
- Integrated mobile network management:
- Centralized, multivendor, multi-infrastructure management and monitoring of wireless / wired infrastructure
- Visual visualization of wireless / wired infrastructure with network maps


Figure 11. An example of “heat charts” in Airwave
And the last thing I would like to mention in this technological part is about people. No supertechnologies will save the project if it is made with “curved” hands. No solutions will work normally if they are set up, configured and launched without a proper understanding of the purpose and essence of the task. Therefore, the conclusion is simple - do not save on the service! As the classic said, “so that it would not be excruciatingly painful afterwards,” it is better to let a person who has such experience and resources do the HD WiFi network.
Part 4. About money
“It doesn't matter what they are talking about - it is always about money”
Todd's second law
Now the most important question - why do we need HD WiFi? Well, really - why, by and large, the WiFi network in the stadium? So that users can online throw their selfy online? What is the use of this to the stadium owner, who has borne the cost of
- design and development of an HD WiFi network,
- purchase equipment HD WiFi network,
- setting up HD WiFi network and putting it into operation
And it will bear the cost of its
- support and
- upgrade?
Why does the stadium owner need all this? The answer is very simple - HD WiFi can and should be monetized, i.e. earn money on it. At the same time, the old-fashioned way to sell guest accounts along with tickets now works poorly. The crisis, people save on everything and push along with the ticket also “just access to the network” becomes difficult. Moreover, no one has canceled mobile 3G / LTE networks and mobile operators are building their infrastructure also taking into account the potential congestion. Therefore, the need to monetize the network with the help of additional services that will
- helpful to many
- simple and easy to use and
- will not cost much.
And here the vendors from the Premier League again compare favorably with all other manufacturers of WiFi "iron". First, most of them have ready-made service platforms on which you can deploy additional services for users of your network and, secondly, as a rule, they have a developed partner network that complements the ability to monetize HD WiFi with different proprietary applications.
Returning to Aruba, I must say that it has not just a platform, but a whole service infrastructure that allows the flexible implementation of various additional services over an HD WiFi network. This infrastructure includes
- Analytical engine (Analytics and Location Engine, ALE), which allows analyzing data received from a WiFi network (for example, customer geolocation data) using a variety of parameters,
- Bluetooth beacons that make geo-positioning very accurate
- as well as the mobile application platform Meridian, on the basis of which you can build a variety of user services.

Figure 12. Analytics and Location Engine
The presence of these tools makes it necessary to rethink the very purpose of introducing a WiFi network. For example, geo-positioning data allows you to implement a service for interactive user routing within a network, such an “in-door GPS”. This is extremely useful and, as practice proves, the demanded service, for example, in large stores, where, according to statistics, the main reason for refusals from a planned purchase is the inability of the buyer to find the right product on the shelves. From personal experience, the main question for sales assistants in Auchan / Okay / Leroy-Merlin stores is “Where can I find it?”. The presence of additional infrastructure from Bluetooth beacons allows making geo-positioning very accurate, up to 1 meter and, accordingly, routing and navigation inside the store is also very accurate and substantive. For example, the presence of beacons under the seats of chairs in one of the stadiums made it possible to implement geolocation services, the flesh to a specific seat.

Figure 13. Meridian Platform
Another popular way to monetize geo-positioning data is to use an advertising model when a user, passing by certain places on the map, receives pop-up contextual advertising, tied specifically to the place where he is now. For example, if you go to a large shopping center, then as an advertisement, pop-up windows may appear about the sales in the stores that you pass by. The Meridian service platform provides subscribers with access to the API, with which developers can make almost any application based on geolocation data and maps loaded into the platform. Further, in addition to intelligent routing / navigation in the room and contextual advertising, the use of this data is limited only by your imagination.
Another approach to monetizing WiFi networks is to use an affiliate model. Premier division vendors, as already mentioned above, usually build partnerships with many developers of specialized applications that can be integrated into a deployed HD WiFi infrastructure. For example, YinzCam is a long-time Aruba partner in specialized applications for sports events. Using their solutions, YinzCam can provide additional services to fans, such as repeating key moments and / or the whole match, viewing game moments from different angles of different cameras, ordering food and drinks, loyalty programs for fans, etc.

Figure 14. YinzCam applications
Another example of monetization with the help of an advertising model is the use of solutions such as the RaGaPa advertising platform. Using this platform, they can disassemble HTTP traffic and insert contextual advertising in it, which is specific to this advertising company and is stored in the specialized RaGaPa cloud.

Figure 15. RaGaPa Solution
Summarizing the above, I would like to emphasize once again the following key idea - you should not consider the HD WiFi infrastructure as the next “cost center” that will eat up the resources of your company. With the right approach, HD WiFi infrastructure can become a serious "profit generating center."
Source: https://habr.com/ru/post/303450/
All Articles