Intel is going to fight microprocessor-level exploits
Intel has published a preliminary specification of the new concept of protection against exploits with the involvement of a microprocessor. In his post , which is devoted to a new technology called Control-flow Enforcement Technology (CET), explains the model of protection against exploits, which one way or another use the methods of ROP . ROP is typically used to bypass DEP in the system. This protective measure (DEP) is also implemented using a microprocessor and marks the virtual memory data RW pages as non-executable (NX).

CET introduces the concept of a shadow stack of calls (shadow stack), which is conducted by the microprocessor itself and which stores information on return addresses for further use by the ret instruction. When returning a thread from a particular function, the microprocessor will check the return address that is stored on the thread stack with the one that is stored on the shadow stack and, if they do not match, will generate an exception that is processed by the OS. CET defines interfaces for the OS that will automate this process and effectively deal with exploits using ROP.
')
Under the shadow stack, a separate region of virtual memory will be allocated, which will be labeled as such at the level of PTE elements of the page tables. Thus, the microprocessor will block any attempts of one or another code to gain access to this stack (for example, via the mov instruction). The microprocessor will store a pointer to the shadow stack in the known task state segment structure to track this field when the stream context and its process are switched. The fields of this structure are also partially used by Windows for the process maintenance mechanism and context switching.
For the activation of CET at the microprocessor level, there will be a special flag of the register cr4 called CR4.CET. It will also be allocated a whole set of special MSR registers that will control the behavior of CET: IA32_U_CET, IA32_S_CET, IA32_PL3_SSP, IA32_PL2_SSP, IA32_PL1_SSP, IA32_PL0_SSP, IA32_INTERRUPT_SSP_TABLE_ADDR. The current address of the shadow stack of the thread will be recorded by a new microprocessor register called SSP (Shadow Stack Pointer).
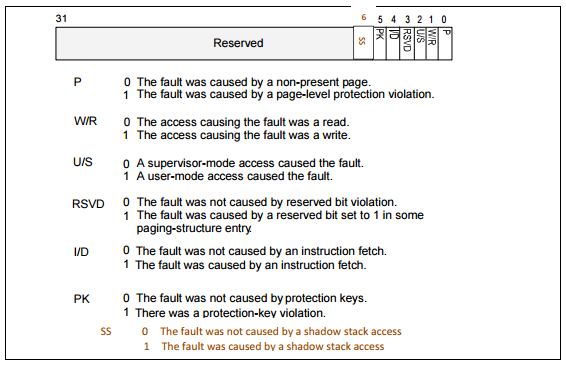
Fig. The format of the error code of a known page fault exception, which is generated by the microprocessor when an attempt is made to access a stream to a page not intended for it. The sixth bit set as a result of the exception speaks of an attempt to access the stream to a virtual memory page with a shadow stack.
Shadow stack can be controlled using the instructions of the microprocessor, the rules for the use of which is regulated by the OS. Some of them are listed below.
In the case of its activity, CET will respond to the following microprocessor instructions that change the flow of code execution: CALL, INT n / INTO / INT3, JMP, RET, SYSCALL, SYSENTER, SYSEXIT, SYSRET, IRET / IRETD. As you can see, these instructions apply to the mechanisms for calling functions and exiting them, as well as for calling system services and exiting them, calling interrupts and exiting them.

Fig. Part of the pseudocode call function call instructions. It can be seen that in the event of CET activity, the return address is stored on the shadow stack.

Fig. The pseudocode part of the exit instruction from the ret function. It is seen that in case of mismatch of addresses on the thread stack and the shadow stack, an exception is generated.
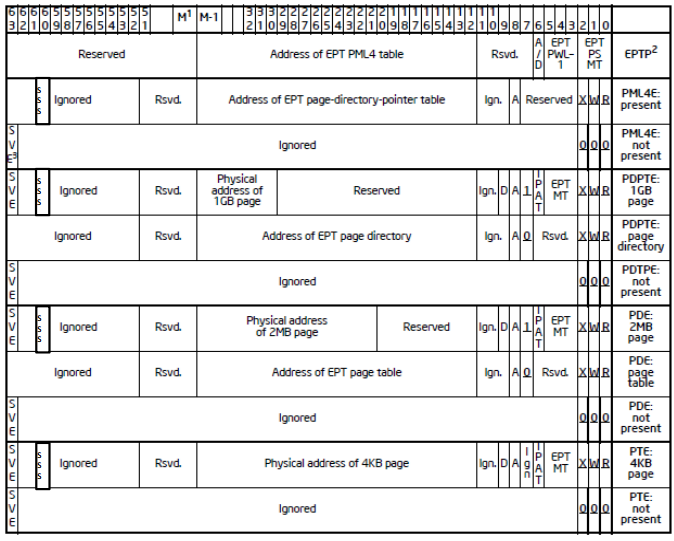
Fig. The elements of the tables of the Extended Page Table (EPT), in which the page of the shadow stack is marked with the 59th bit of the SSS. Used to identify the pages of the shadow stack at the page table level.
Recall that the specific anti-ROP exploit functions are contained in the free EMET tool. To do this, use settings such as Caller Check, SimExecFlow, MemProt, and StackPivot. The first two allow EMET to control the flow of execution and calling Windows API functions, as well as to verify the legitimacy of the caller’s code. The MemProt function prevents the thread from modifying the protection attributes of the stack page, and StackPivot recognizes situations of modifying the esp register using the stack pivoting method.

CET introduces the concept of a shadow stack of calls (shadow stack), which is conducted by the microprocessor itself and which stores information on return addresses for further use by the ret instruction. When returning a thread from a particular function, the microprocessor will check the return address that is stored on the thread stack with the one that is stored on the shadow stack and, if they do not match, will generate an exception that is processed by the OS. CET defines interfaces for the OS that will automate this process and effectively deal with exploits using ROP.
')
Under the shadow stack, a separate region of virtual memory will be allocated, which will be labeled as such at the level of PTE elements of the page tables. Thus, the microprocessor will block any attempts of one or another code to gain access to this stack (for example, via the mov instruction). The microprocessor will store a pointer to the shadow stack in the known task state segment structure to track this field when the stream context and its process are switched. The fields of this structure are also partially used by Windows for the process maintenance mechanism and context switching.
It has been established that it has been decided to use it. In the case of the CET, it is not the case. The return instructions (eg RET)
For the activation of CET at the microprocessor level, there will be a special flag of the register cr4 called CR4.CET. It will also be allocated a whole set of special MSR registers that will control the behavior of CET: IA32_U_CET, IA32_S_CET, IA32_PL3_SSP, IA32_PL2_SSP, IA32_PL1_SSP, IA32_PL0_SSP, IA32_INTERRUPT_SSP_TABLE_ADDR. The current address of the shadow stack of the thread will be recorded by a new microprocessor register called SSP (Shadow Stack Pointer).

Fig. The format of the error code of a known page fault exception, which is generated by the microprocessor when an attempt is made to access a stream to a page not intended for it. The sixth bit set as a result of the exception speaks of an attempt to access the stream to a virtual memory page with a shadow stack.
Shadow stack can be controlled using the instructions of the microprocessor, the rules for the use of which is regulated by the OS. Some of them are listed below.
- INCSSP - increase the SSP shadow stack pointer by one step, i.e., by 4 bytes in a 32-bit system and by 8 bytes in a 64-bit one.
- RDSSP - read the value of the SSP pointer in the specified register.
- SAVESSP — save the current “shadow stack context” on the shadow stack and align the SSP pointer with 8 bytes.
- RSTORSSP - the command is similar to the previous one, i.e. it writes the value of the saved stack marker to the SSP.
- WRSS — write the value of the passed argument in the virtual memory using the SSP pointer.
In the case of its activity, CET will respond to the following microprocessor instructions that change the flow of code execution: CALL, INT n / INTO / INT3, JMP, RET, SYSCALL, SYSENTER, SYSEXIT, SYSRET, IRET / IRETD. As you can see, these instructions apply to the mechanisms for calling functions and exiting them, as well as for calling system services and exiting them, calling interrupts and exiting them.

Fig. Part of the pseudocode call function call instructions. It can be seen that in the event of CET activity, the return address is stored on the shadow stack.

Fig. The pseudocode part of the exit instruction from the ret function. It is seen that in case of mismatch of addresses on the thread stack and the shadow stack, an exception is generated.

Fig. The elements of the tables of the Extended Page Table (EPT), in which the page of the shadow stack is marked with the 59th bit of the SSS. Used to identify the pages of the shadow stack at the page table level.
Recall that the specific anti-ROP exploit functions are contained in the free EMET tool. To do this, use settings such as Caller Check, SimExecFlow, MemProt, and StackPivot. The first two allow EMET to control the flow of execution and calling Windows API functions, as well as to verify the legitimacy of the caller’s code. The MemProt function prevents the thread from modifying the protection attributes of the stack page, and StackPivot recognizes situations of modifying the esp register using the stack pivoting method.
Source: https://habr.com/ru/post/303086/
All Articles