Security Week 23: all passwords were stolen, not by TeamViewer, Lenovo asks to remove the vulnerable utility
 The topic of passwords does not let go. New plums from Vkontakte , Twitter , Tumblr and MySpace have been added to recent leaks from LinkedIn . Mark Zuckerberg was hacked into Twitter and Pintest, it turned out that the password was “dadada”, and this is of course an epic fail.
The topic of passwords does not let go. New plums from Vkontakte , Twitter , Tumblr and MySpace have been added to recent leaks from LinkedIn . Mark Zuckerberg was hacked into Twitter and Pintest, it turned out that the password was “dadada”, and this is of course an epic fail.Indeed, " astrologers have announced a month of leaks ." In part, this may be due to the actions of a single hacker, who merges into the Darqube not the freshest, but voluminous bases, inexpensively. The profile media also plays a similar role: if last fall everyone was digging the issue of encryption to exhaustion, in the winter they spoke about the Apple and FBI case, now special attention is paid to passwords - the information space works that way.
But the topic is important. Arstechnica estimates that over 600 million passwords have been leaked in the last month. Yes, this is really not the latest hacking, but password auditing is worth doing . Especially that legion of people who have the password 123456. All the rest can be guided by a reasonable period of password change with an interval of a maximum of two years, preferably more often (based on a typical drainage age of 4 years). How to protect yourself is also understandable, it is not clear how to finally start doing it. Options for improving the situation discussed in the comments to the previous series. My approach to decreasing reliability: (1) Password Manager and one-time passwords everywhere (2) Difficult and different passwords on critical services (Basic social networks, payment systems) (3) Less complex and easier to remember passwords with variations on non-critical services (forums and others ). And of course, two-factor authorization wherever possible.
Previous episodes of the series are available by tag .
TeamViewer eliminates hacking your own servers, users complain about intercepting remote access
News
')
Suppose one of the many leaks has your password, but the old one, which has not been used in a particular service for a long time. All is well? Yes, if you are not in the habit of protecting different services with the same password, and forgetting where else such a password can be used. Apparently, something similar happened with the users of the remote access service to computers (and even smart TVs) TeamViewer: they began to complain massively about the theft of accounts. And remote access to a home or work computer is a golden key to almost all data. It happened to one of the victims: through TeamViewer, we got access to PayPal, bought an Xbox card and a pants .
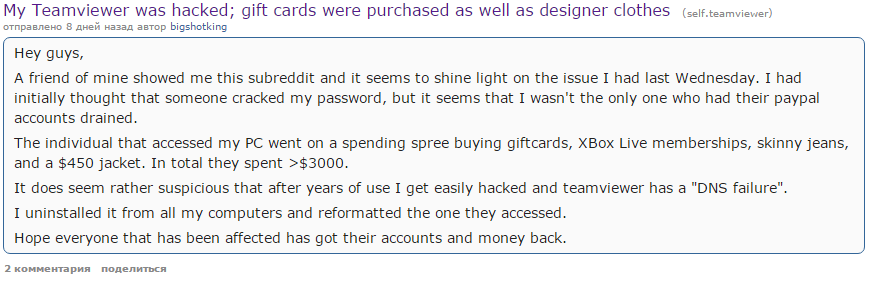
Naturally, users tend to blame TeamViewer for all sins, especially since the leak coincided (did it?) With a DDoS attack on the company's servers. But the organizers of the service are against: there was no leak on their side. Troy Hunt, owner of the site Haveibeenpwned - aggregator of data on "merged" accounts - is inclined to see a direct link between massive leaks and burglary TeamViewer. Just take the e-mail and password from the merged databases and select them to other services. Welcome to the new harsh reality. More precisely not new. But still, great!
Lenovo (again) has a critical vulnerability in service software
News More news with vulnerability details. Lenovo advisory .
Lenovo recommends uninstalling the Accelerator application, “to speed up the launch of Lenovo utilities.” As it turned out, the software update module integrated into the application regularly contacts the server, without using any protective measures. As a result, it becomes possible to spoof the response from the server and slip malware instead of legitimate updates. The vulnerability was so serious that the solution offered is the only and the most radical one: delete the application, manually or with the help of a special utility.
This is not the first news about vulnerabilities in Lenovo proprietary software. Earlier this year, a share password was found in the file-sharing utility ShareIT. Earlier, they discovered a hole in the Lenovo System Update, a driver and software update utility for corporate line notebooks. Frustration to users adds the fact that we are usually not talking about vital utilities, but rather on the extra-imposed bloatware.
As I wrote earlier, you cannot say that Lenovo is bad, while other vendors are fine. The source of the news was the study of the company Duo Security, where in addition to Lenovo got Acer, Asus, Dell and HP. It is noteworthy that the Lenovo Solution Center software, which is installed on corporate laptops and PCs, communicates with the update servers with the observance of all precautions, unlike its counterpart for consumer models. However, Lenovo’s response was quick and correct: they didn’t deny the existence of the problem and offered a solution (albeit a disadvantage for themselves).
What else happened:
A serious NTP vulnerability has been discovered and patched .
New vulnerabilities in Android, again in Mediaserver .
Patch of a serious vulnerability in Chrome, the built-in PDF viewer was guilty .
Intel has proposed a hardware implementation of protection against exploits. An interesting approach to solving a very ancient and very dangerous problem.
 Antiquities:
Antiquities:“Clock”
Dangerous virus. The boot sector of the floppy disk is affected when accessing it and the MBR of the hard drive when booting from an infected floppy disk. Depending on its internal counter, it restarts the computer or changes the hard drive settings (on those controllers, where possible). Intercepts int 8, 13h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 21.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/303082/
All Articles