Where to get logins or VoIP to help
 Penetration testing always begins with gathering information about the infrastructure. Available nodes with open ports and vulnerable services, valid credentials and other information that allows you to "move forward" and compromise the system is interesting in the first place. When testing with the black-box method, the question very often arises: “where can I get the logins?”. In the article I want to tell where else you can get logins at the stage of collecting information. Welcome under cat.
Penetration testing always begins with gathering information about the infrastructure. Available nodes with open ports and vulnerable services, valid credentials and other information that allows you to "move forward" and compromise the system is interesting in the first place. When testing with the black-box method, the question very often arises: “where can I get the logins?”. In the article I want to tell where else you can get logins at the stage of collecting information. Welcome under cat.Conducting an audit by the black-box method, we do not know absolutely nothing about the infrastructure. So this time: access is granted only to the internal segment of the company's network without any additional information. Scanning the network, many available hosts were found where login credentials were required. But we don’t have them - this is logical at the initial stage. Where to get logins for the further selection of passwords? There are several ways, everyone chooses to taste. For example, you can use ready-made dictionaries or search for information in public sources - most likely, some mailing addresses of employees are posted on the company's website. Based on them, you can make a dictionary of logins. Or, nevertheless, look into the corporate directory of phones?
At the reception of the secretary in free access was a telephone set by all well-known company "Cisco". A quick look through the menu of the device found an available corporate directory of phones. Leaving the “Name”, “Last Name” and “Number” fields empty, I searched the catalog and the phone obediently gave information about subscribers. Retrieving information from the phone while standing at the reception is non-comfortably, so from the adjacent tab of the menu I learned the URL of the CUCM server, from where the phone directory pulls.

Returning for the laptop and clicking on the URL
https: // XXXXXXXXXXXXXX: 8443 / ccmcip / xmldirectorylist.jspI received an XML document with caller names and their internal phone numbers.
')
The available parameters were "l" (lastname), "f" (firstname) and "n" (number). The "start" parameter allows you to navigate through the directory. In just 1 query, you can get 30 values.
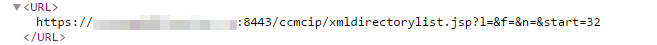
The required information was in “Prompt”, “Name” and “Telephone”. Number of entries (displayed and total):
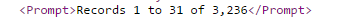
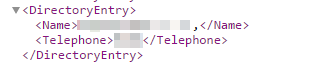
Last name, first name and subscriber number:
It remains the case for small - pull it all out of the catalog. For this, a small Python script was prepared that parses the XML document according to the specified parameters.
As a result of the script, I recognized the names and surnames of users, which allowed me to create an accurate vocabulary of logins. Phone numbers can be used when generating passwords.
Cherry on the cake: in addition to the names and names of users, I also received the names of the service accounts, which somehow ended up on another (second) CUCM server, and this is much more interesting.
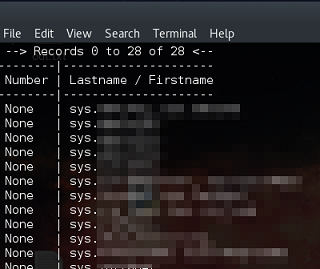
As a summary
A publicly accessible corporate telephone directory provides an attacker with a good set of input data with which he can compromise the target system.
Script
Python script for parsing XML on github: Download
Source: https://habr.com/ru/post/303058/
All Articles