Be wary of online invoices with a cryptographer: a recently discovered threat has already manifested itself in different countries

Just a few days ago, we received a notification from the Spanish electricity company Endesa, in which we were warned about a new online fraud, hitting victims with fake emails. Cyber criminals sent false accounts to Spanish users, allegedly on behalf of Endesa, at the opening of which they were subjected to cyber attack. Unfortunately, cyber-criminals managed to successfully launch their attacks, and even continue them in other countries. Now it is very difficult to estimate the number of people who received such “letters of happiness” and the proportion of those who fell victim to this attack.
Over the past few hours, a new focus of such an attack has been discovered. The state-owned electric company PGE (Poland) also came under the attention of this network of cyber-criminals who used this method of attack at the international level. Like the incident in Spain, in this case, the criminals also infect important and sensitive information belonging to home and corporate users, after the infected file is opened, in which it is supposed to be an electricity bill (which is too expensive for users).
')
We are confronted with massive frauds that cross state borders and have a very lucrative goal: to make you pay a ransom for the return of access to your personal files.
In both cases, the attack works identically: sending false bills allegedly on behalf of a well-known power company in order to infect the computers of naive victims with the help of Cryptolocker Locky. Although this attack has so far reached only Spain and Poland, it is spreading rapidly and may soon be in any other country in the world. Below are some tips to help combat this threat:
Online scam with the account: step by step:
1. In both analyzed cases, this letter arrives by e-mail, and the subject of the letter contains the name of the electric power company that operates in the respective country.
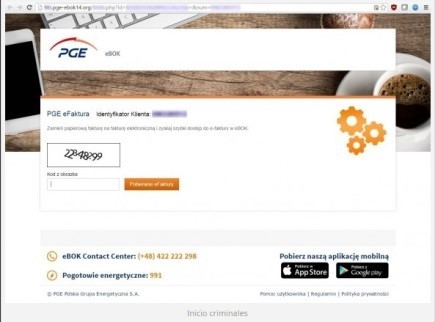
2. In both countries, the letter contains a false invoice. After analyzing the situation with the PGE, we see that the message may look somewhat chaotic, when Polish letters are randomly inserted into the text of the letter.
3. When the user wants to see the bill in more detail, he clicks a button in the letter itself with a text like “See. Your account and consumption volume ”, which is below the total statistics of electricity consumption, then goes to a false website, which looks like the website of the company, on whose behalf the attackers allegedly act.
4. The user is asked to fill in the Captcha field on the site in order to gain access to the Zip file. Users think they are performing a secure action, but in fact, their cyber security is controlled by a very powerful encryption cipher.
5. After the user fills in the Captcha field, he is offered to download a zip file.
6. This zip-file contains a file with a java-script, and if the user opens it, the script downloads and runs the encryption tool.
7. Once the malware is executed, the user will be blocked from accessing his personal files. Locky is an aggressive kidnapper who returns access to personal information only after paying a ransom.
Each time there are more individual attacks, sharpened for a specific user. Their creators manage to successfully conduct their attacks using the names of well-known and prestigious companies, as a result of which trusting users easily fall into the trap.
One thing is clear: if you are not protected from this type of cryptographer, your personal and corporate files may be exposed to the risk of blocking access.
Source: https://habr.com/ru/post/303042/
All Articles