Learning is light: the TC MUK program for the training of information security specialists
Information security is one of the most important areas in IT. The dynamic development of the industry requires businesses to be ready for new challenges, fully justifying the need to invest in the training and development of information security professionals .
In connection with the rapid development of information technologies in general and information security as a science in particular, the information security specialist needs to solve the problem of maintaining his qualifications. This statement is true not for the first year, however nowadays the following conclusions about the solution of this problem differ significantly from those that were relevant before. One of the main reasons for these differences is the completed transition from a risk-based approach to the construction of automated systems to the normative one.
')
In the era of risk-based approach, the focus was on building a business model and determining the necessary and sufficient conditions for meeting the security policy requirements. Created protection systems were piece goods, demanded mainly by government agencies and major commercial organizations. To complete the work in the field of security, it was enough for a specialist to have a developed mathematical apparatus, which students of technical colleges of higher education receive as part of higher professional education.
With all the variety of created business models and requirements of security policies, the conditions for their implementation in the overwhelming majority of cases are the same. This fact resulted in a transition to a normative approach to the construction of protection systems, when specialists focus on searching, analyzing and adapting a suitable family of open security standards.
Subtleties of learning
In connection with the above, a specialist in the field of information security should specialize in one of the following areas:
- implementation of the requirements of national laws and / or regulators (for example, access to state or trade secrets);
- use of certified information security tools of specific manufacturers (design, commissioning, etc.);
- recognized international vendor-independent certification.
Training in the first two areas is carried out by a number of educational institutions within the framework of both higher and secondary vocational education. But these areas bind a specialist to employers in a particular country, and more specifically, allow them to conduct their activities only within the framework of national laws and standards.
Advantages of international and vendor-independent certifications
If we talk about the third area, it initially focuses on international open standards and security methodologies in the hope that developed and developing countries seek to harmonize their national laws and standards with international ones in connection with the fundamental advantages of the latter. A specialist with such qualifications is ready to adapt his experience to work in any country and confirm his qualifications to any employer, which, other things being equal, gives him an advantage over other job seekers. Due to a number of reasons, the domestic IT market belatedly adopts international security standards. However, the acceleration of the globalization process inevitably leads to a natural result - an increasing number of specialists in the field of information security are looking for evidence of their experience in internationally recognized certifications.
The wide distribution in Ukraine of international certifications that depend on specific manufacturers (Microsoft, Cisco, HP and others) is primarily related to the requirements of the manufacturers themselves to ensure a guaranteed level of service quality in the sale, design, commissioning and maintenance of solutions created using their technology. Preparation for the exams for such certification consists in memorizing to a greater degree the multitude of technology-specific facts and, to a lesser extent, the principles of their use.
Universal principles that allow you to create effective protection systems without reference to the technologies of specific manufacturers remain in such certifications “behind the scenes”, which does not suit those who claim to be a security expert in their specialization. It is precisely these principles that make it possible to reveal the preparation for vendor-independent certifications, and their successful acquisition and maintenance - to confirm the actual experience of working as an information security specialist.
Course features
The MUK Training Center offers a unified training program for the automation / information security divisions. Its uniqueness lies in the fact that it:
- developed in accordance with the newest family of open standards of training and ISO / IEC Standart 17024;
- examines the practical aspects of the application of the dominant international information security standards (ISO \ IEC 27000-series) and information system survey methodologies (COBIT);
- prepares to obtain globally recognized vendor-independent certifications from leading operators (CompTIA, ISACA, ISC2);
- uses modern methods of adult education from State University of New York;
- supports the concept of continuous learning (Continuous Professional Education).
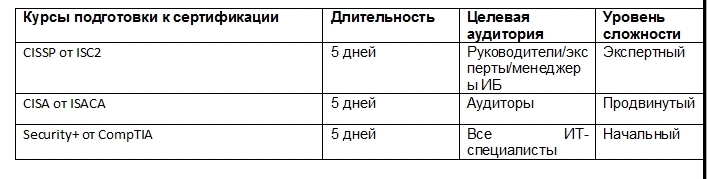
An intensive course of training for all IT professionals meets the requirements of the American National Standards Institute ( www.ansi.org ) to a minimum set of knowledge and skills in the basics of information security. He will prepare for the exam for international certification status of Security + from the leading provider of vendor-independent IT certifications Computing Technology Industry Association (CompTIA). CompTIA certifications are counted in undergraduate / graduate and professional retraining programs in most higher education institutions in developed countries.
Information system auditors will be able to prepare for certification status Certified Information Systems Auditor (CISA) from the largest international professional association of auditors Information Systems Audit and Control Association (ISACA).
Middle and senior executives MUK Training Center is preparing to obtain certifications that are the gold standard in the field of information security - Certified Information Systems Security Professional (CISSP) from the ISC2 consortium and Certified Information Systems Manager (CISM) from the largest international professional association of auditors Information Systems Audit and Control Association (ISACA).
Curriculum levels
A growing number of universities in developed countries include CISSP, CISM and CISA certifications from ISC2 and ISACA operators, for example, Capella University or Vanguard Institute of Technology, in their graduate programs.
All courses of the program are updated in accordance with the concepts of continuous learning of the listed operators. This means that passing these courses is also relevant for current holders of these certifications as a measure for obtaining status points.
These requirements are met not only by the certification program, but also by many others. In the event of a steady demand for training services on this topic, the authors of the program plan to include training courses for EC-ethics hacking certification, computer incidents investigation from GIAC, and business continuity from the British Standarts Institute.
More information about training courses in the field of information security can be found at . The most up-to-date information about the MUK training center can always be found on our website . Contact information for countries can be found here .
In connection with the rapid development of information technologies in general and information security as a science in particular, the information security specialist needs to solve the problem of maintaining his qualifications. This statement is true not for the first year, however nowadays the following conclusions about the solution of this problem differ significantly from those that were relevant before. One of the main reasons for these differences is the completed transition from a risk-based approach to the construction of automated systems to the normative one.
')
In the era of risk-based approach, the focus was on building a business model and determining the necessary and sufficient conditions for meeting the security policy requirements. Created protection systems were piece goods, demanded mainly by government agencies and major commercial organizations. To complete the work in the field of security, it was enough for a specialist to have a developed mathematical apparatus, which students of technical colleges of higher education receive as part of higher professional education.
With all the variety of created business models and requirements of security policies, the conditions for their implementation in the overwhelming majority of cases are the same. This fact resulted in a transition to a normative approach to the construction of protection systems, when specialists focus on searching, analyzing and adapting a suitable family of open security standards.
Subtleties of learning
In connection with the above, a specialist in the field of information security should specialize in one of the following areas:
- implementation of the requirements of national laws and / or regulators (for example, access to state or trade secrets);
- use of certified information security tools of specific manufacturers (design, commissioning, etc.);
- recognized international vendor-independent certification.
Training in the first two areas is carried out by a number of educational institutions within the framework of both higher and secondary vocational education. But these areas bind a specialist to employers in a particular country, and more specifically, allow them to conduct their activities only within the framework of national laws and standards.
Advantages of international and vendor-independent certifications
If we talk about the third area, it initially focuses on international open standards and security methodologies in the hope that developed and developing countries seek to harmonize their national laws and standards with international ones in connection with the fundamental advantages of the latter. A specialist with such qualifications is ready to adapt his experience to work in any country and confirm his qualifications to any employer, which, other things being equal, gives him an advantage over other job seekers. Due to a number of reasons, the domestic IT market belatedly adopts international security standards. However, the acceleration of the globalization process inevitably leads to a natural result - an increasing number of specialists in the field of information security are looking for evidence of their experience in internationally recognized certifications.
The wide distribution in Ukraine of international certifications that depend on specific manufacturers (Microsoft, Cisco, HP and others) is primarily related to the requirements of the manufacturers themselves to ensure a guaranteed level of service quality in the sale, design, commissioning and maintenance of solutions created using their technology. Preparation for the exams for such certification consists in memorizing to a greater degree the multitude of technology-specific facts and, to a lesser extent, the principles of their use.
Universal principles that allow you to create effective protection systems without reference to the technologies of specific manufacturers remain in such certifications “behind the scenes”, which does not suit those who claim to be a security expert in their specialization. It is precisely these principles that make it possible to reveal the preparation for vendor-independent certifications, and their successful acquisition and maintenance - to confirm the actual experience of working as an information security specialist.
Course features
The MUK Training Center offers a unified training program for the automation / information security divisions. Its uniqueness lies in the fact that it:
- developed in accordance with the newest family of open standards of training and ISO / IEC Standart 17024;
- examines the practical aspects of the application of the dominant international information security standards (ISO \ IEC 27000-series) and information system survey methodologies (COBIT);
- prepares to obtain globally recognized vendor-independent certifications from leading operators (CompTIA, ISACA, ISC2);
- uses modern methods of adult education from State University of New York;
- supports the concept of continuous learning (Continuous Professional Education).
An intensive course of training for all IT professionals meets the requirements of the American National Standards Institute ( www.ansi.org ) to a minimum set of knowledge and skills in the basics of information security. He will prepare for the exam for international certification status of Security + from the leading provider of vendor-independent IT certifications Computing Technology Industry Association (CompTIA). CompTIA certifications are counted in undergraduate / graduate and professional retraining programs in most higher education institutions in developed countries.
Information system auditors will be able to prepare for certification status Certified Information Systems Auditor (CISA) from the largest international professional association of auditors Information Systems Audit and Control Association (ISACA).
Middle and senior executives MUK Training Center is preparing to obtain certifications that are the gold standard in the field of information security - Certified Information Systems Security Professional (CISSP) from the ISC2 consortium and Certified Information Systems Manager (CISM) from the largest international professional association of auditors Information Systems Audit and Control Association (ISACA).
Curriculum levels

A growing number of universities in developed countries include CISSP, CISM and CISA certifications from ISC2 and ISACA operators, for example, Capella University or Vanguard Institute of Technology, in their graduate programs.
All courses of the program are updated in accordance with the concepts of continuous learning of the listed operators. This means that passing these courses is also relevant for current holders of these certifications as a measure for obtaining status points.
These requirements are met not only by the certification program, but also by many others. In the event of a steady demand for training services on this topic, the authors of the program plan to include training courses for EC-ethics hacking certification, computer incidents investigation from GIAC, and business continuity from the British Standarts Institute.
More information about training courses in the field of information security can be found at . The most up-to-date information about the MUK training center can always be found on our website . Contact information for countries can be found here .
Source: https://habr.com/ru/post/302738/
All Articles