Asus automatically updates BIOS / UEFI over HTTP without verification
Asus took up the old again. You can send any executable file or even BIOS firmware to an Asus computer under the guise of an update - this file will be automatically launched for execution with maximum privileges, and the firmware will be installed without any checks. Nothing needs to be done - the system will hack itself automatically.
In short: computers with Asus motherboards make requests to the remote server via HTTP on a regular basis. The reason is LiveUpdate software, which is pre-installed on Asus computers. It is responsible for downloading new BIOS / UEFI firmware and executable files. Updates are received in ZIP archives via pure HTTP, unpacked into a temporary folder, and the executable file is launched on behalf of the user. There is no file verification or authentication when loading them, which allows for a MiTM attack and a banal escalation of privileges to
NT AUTHORITY\SYSTEM .Asus has been distributing LiveUpdate with its laptops and PCs for a long time, more than ten years since Windows XP. During this time, the principle of its work has not changed. The client makes unencrypted HTTP requests to Asus update servers ( liveupdate01.asus.com or dlcdnet.asus.com , depending on the version).
')
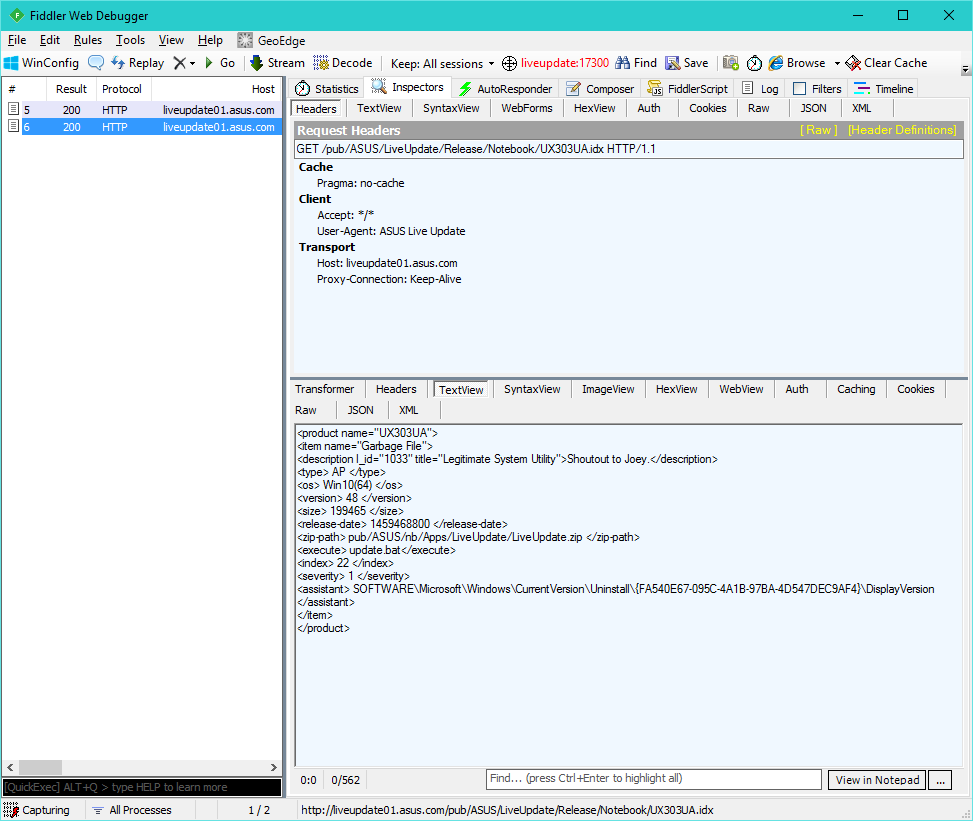
For example, on the UX303UA laptop, the latest version of LiveUpdate tries to reach the following addresses. It does this until it receives a response other than error 404.
- http://liveupdate01.asus.com/pub/ASUS/LiveUpdate/Release/Notebook/UX303UA.ide
- http://liveupdate01.asus.com/pub/ASUS/LiveUpdate/Release/Notebook/UX303UA.idx
- http://dlcdnet.asus.com/pub/ASUS/LiveUpdate/Release/Eee%20Book/UX303UA.ide
- http://dlcdnet.asus.com/pub/ASUS/LiveUpdate/Release/Eee%20Book/UX303UA.idx
These “.idx” files are quite complex, they allow you to download various updates, including flashing the BIOS via WinFlash (if the program is installed) and installing the drivers.
For example, here is an entry in the XML file of the updated ACPI driver for ET1602 laptop:
<item name="ATK0110 ACPI Utility"> <description l_id="1033" title="ATK0110 ACPI Utility">ATK0110 ACPI Utility</description> <description l_id="1028" title="ATK0110 ACPI Utility">ATK0110 ACPI Utility</description> <description l_id="2052" title="ATK0110 ACPI Utility">ATK0110 ACPI Utility</description> <type> driver </type> <hwid version="1043.2.15.37" date="08/13/2004"> ACPI\ATK0110 </hwid> <os> WinXP </os> <version> 1043.2.15.37 </version> <size> 837015 </size> <release-date> 1219104000 </release-date> <zip-path> pub/ASUS/DigitalHome/DAV/B202/ACPI_V104321537.zip </zip-path> <execute> .\AsusSetup.exe </execute> <index> 1 </index> </item> Here the cool thing is the procedure for unpacking and automatically launching the .exe file for execution.
These are flowers. Imagine that you can easily and easily reflash the BIOS.
<item name="BIOS 210"> <description l_id="1033" title="BIOS 210">To solve the issue which charge speed will be slower when battery capacity is above 60%</description> <description l_id="1028" title="BIOS 210">解決當電池容量大於60%時,充電速度變慢的問題</description> <description l_id="2052" title="BIOS 210">解决当电池容量大于60%时,充电速度变慢的问题</description> <type> BIOS </type> <os></os> <version> 210 </version> <size> 2717731 </size> <release-date> 1422628620 </release-date> <zip-path> pub/ASUS/nb/X453MA/X453MAAS210.zip </zip-path> <execute> X453MAAS.210 </execute> <index> 1 </index> </item> There is no procedure for verifying the authenticity of this XML file.
In the task scheduler, the frequency is set to perform the task once an hour, in addition, the update program constantly contacts the LiveUpdate server via HTTP. The resulting file will be unpacked and launched for execution, whatever it is.
The vulnerability was discovered by security specialist Morgan [ indrora ] Gangwere.
The timeline of events from the moment of discovery of vulnerability on April 27 until the moment of public disclosure of information is very funny:
From the vendor that brought you a vulnerable cloud storage platform comes ___ ____ __ __ __ / _ \___ ___ ____/ / / / /__ ___/ /__ _/ /____ / // / -_) _ `/ _ / /_/ / _ \/ _ / _ `/ __/ -_) /____/\__/\_,_/\_,_/\____/ .__/\_,_/\_,_/\__/\__/ Because popping SYSTEM /_/ is easy when you trust HTTP Or, "How I learned to stop worrying and execute arbitrary executables from HTTP" Affected software: LiveUpdate (any version? 3.3.5 tested) Vulnerability: HTTP MITM to SYSTEM execution + more. CVSS: est. 9.3 CVSS:3.0/AV:A/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:N (NB: This assumes "Hijack some HTTP" is easy and you're local) Timeline: 2016-04-27 Initial discovery 2016-04-28 Attempt to contact vendor (security@asus.com - bounce) 2016-04-28 Disclosure to MSFT MSRC attempting vendor coordination 2016-05-09 Attempt to contact vendor (via phone; told to go away) 2016-05-10 Disclosure to CERT/CC (tracked as VU#215055) 2016-05-11 CERT/CC attempts to contact vendor 2016-05-24 CERT/CC: No response from vendor 2016-06-01 CERT/CC: Disclose at will 2016-06-03 Public disclosure As you can see, the hacker twice tried to contact the vendor. The first time he wrote to the address
security@asus.com , but received an automatic fail-over. Delivery to the following recipient failed permanently: security@asus.com Technical details of permanent failure: Google tried to deliver your message, but it was rejected by the server for the recipient domain asus.com by mg.asus.com. [103.10.4.32]. The error that the other server returned was: 550 #5.1.0 Address rejected. Then he phoned but was told ... not to call anymore.
Poc
Based on the logic of auto-update, you can run any file with a valid signature.
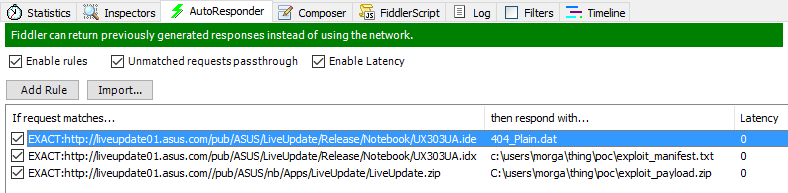
To demonstrate the attack with escalation of privileges, Morgan Gangver used SysInternals PSEXEC. He compiled a fake "update."
<product name="UX303UA"> <item name="Garbage File"><description l_id="1033" title="Legitimate System Utility">Shoutout to Joey.</description> <type> AP </type> <os> Win10(64) </os> <version> 48 </version> <size> 199465 </size> <release-date> 1459468800 </release-date> <zip-path> pub/ASUS/nb/Apps/LiveUpdate/LiveUpdate.zip </zip-path> <execute> update.bat</execute> <index> 22 </index> <severity> 1 </severity> <assistant> SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FA540E67-095C-4A1B-97BA-4D547DEC9AF4}\DisplayVersion </assistant> </item> </product> A copy of psexec, a fictional whoami and a script to run are packed into the “update” archive.
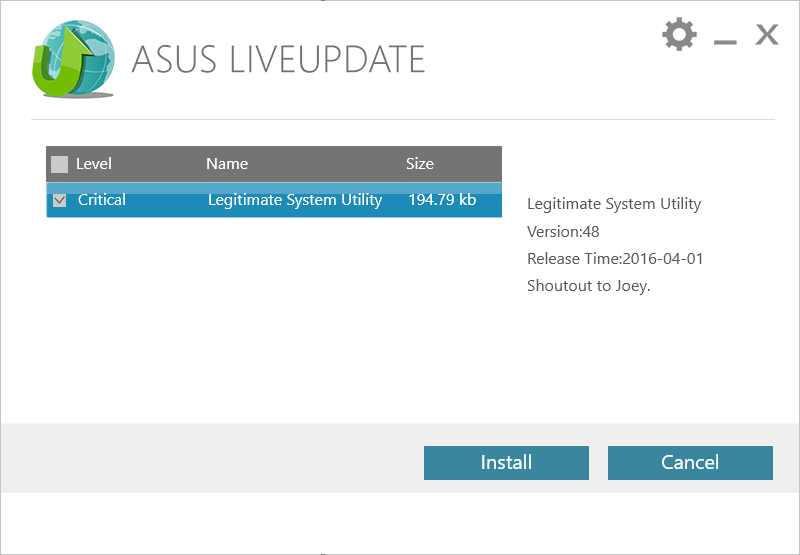
Asus LiveUpdate immediately sees a "critical" update.

Receiving a "critical" update, it is immediately assigned to execution with all the rights.

Here is the result.

Thus, we launched arbitrary code for execution as
NT AUTHORITY\SYSTEM , simply giving it to the system in response to an HTTP call. Everything else does LiveUpdate for you.In general, the awful, in terms of security, firmware upgrade procedure is peculiar not only to Asus motherboards, but also to hardware from other manufacturers. The firmware of many routers, for example, are updated in an unsafe way.
Source: https://habr.com/ru/post/302660/
All Articles