Unwanted DNS Unlocker uses the DNS hijack method to trick users
Our technical support specialists record a variety of user requests. One of these requests was very interesting for analysis. The situation was that we detected malicious activity in the user's system, which was manifested in the DNS hijack technique. It is used to redirect user’s DNS requests to special DNS servers. The peculiarity of the situation was that the malware used a special method for the operation hijack, which hid the malicious activity from the user's eyes.

Thus, the user could not see the settings of the DNS servers in the GUI interface of the network settings. In addition, it will also indicate that the system uses the DHCP protocol to obtain the settings. An unwanted application that performs similar operations on the system is called DNS Unlocker .
')
The DNS Unlocker application sets the victim's network settings in such a way that they point to fake DNS server addresses. When a web browser visits the victim of google-analytics.com, a fake DNS server will point to a malicious address with JavaScript content embedded there. This is done in order to advertise, which is inserted into the web page DNS Unlocker, relied on Google Analytics. Typically, a user with DNS Unlocker installed will see advertisements with a note at the bottom of a web page that says "Ads by DNSUnlocker" (Fig. 1) or something similar in a variety of other options (Fig. 2).
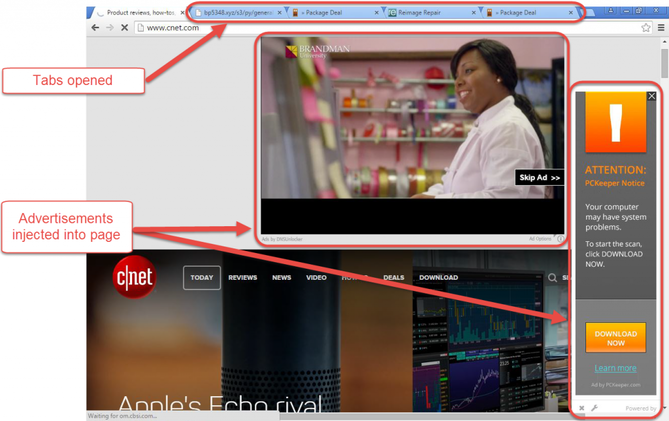
Fig. 1. Advertising content embedded in a web page.
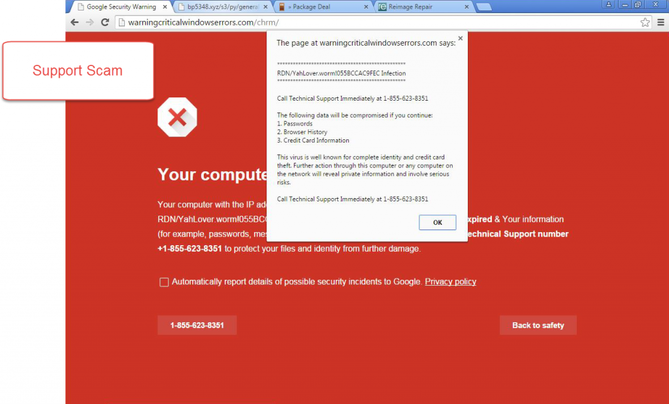
Fig. 2. Phishing message to intimidate the user.
Malicious software that uses DNS address spoofing mechanisms in Windows settings is not new, besides, such instances are not even worthy of detailed coverage. However, DNS Unlocker incorporates an interesting feature that distinguishes it from other similar examples. It is used to secretly change the DNS settings in such a way that the user will not notice. The user will not be able to see the new TCP / IPv4 settings in the control panel, which are responsible for the fields of static DNS records. As a rule, when specifying the DNS server address, its address should be displayed in the list of Preferred DNS Servers settings, provided that the Use the following DNS server addresses check box is selected. In addition, the user can pay attention to the setting "Alternative DNS-server." When using DHCP to get DNS addresses (used in most configurations of home and office environments), the setting “Obtain DNS server address automatically” is active.
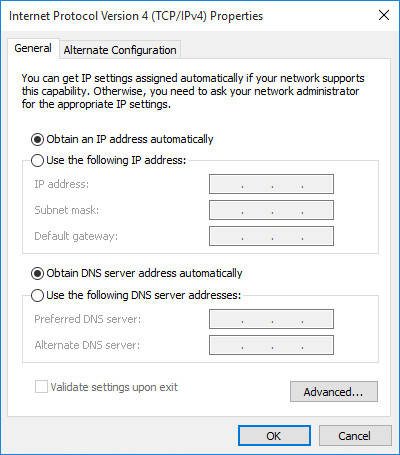
Fig. 3. TCP / IPv4 network settings with typical settings.
The peculiarity of the technique used by DNS Unlocker is that the static DNS address specified by it is not displayed in the list of network settings, besides, it indicates that the user receives DNS addresses automatically. The ipconfig / all command will also indicate the use of DHCP, but it will also display statically set DNS addresses. When using the ipconfig tool, however, it is impossible to establish which network connections use DHCP and which static addresses. The network settings GUI does not display the static part and assures the user of the use of DHCP. Below we answer the question why this happens, that is, what causes the static entry to not appear in the GUI interface of the network settings.
Consider the registry key that is responsible for configuring network interfaces.
HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ Tcpip \ Parameters \ Interfaces \
This registry key captures the settings of network interfaces, each of which is specified by a GUID. The settings section for each network adapter can contain the DhcpNameServer and NameServer parameters . The parameter NameServer is of interest to us. Usually, if you configure a static DNS server, use the network settings of the control panel (or use the netsh command to do this). In this case, the static server addresses will be stored in the NameServer registry parameter with the symbol “,” as a separator for the value elements.
192.168.1.21,192.168.1.22
Now consider the case when the space separator is used as the address separator in this parameter.
192.168.1.21 192.168.1.22
This small change allows you to hide the addresses of the DNS servers being used from the GUI interface of the network settings, since, in fact, one of them is the main and the second is additional. For a user, this fact means receiving advertisements embedded in websites visited by the user.
Since Windows assumes that the addresses of the primary and secondary DNS servers are already set, setting the user to new values will only add them to the end of the list of items already existing there, as shown below.
192.168.1.21 192.168.1.22,208.67.222.123,208.67.220.123
It can be seen that Windows uses the symbol “,” as a separator, while the first elements still use a space.
The question is why Windows allows this behavior of its system component. We do not have a reliable answer to this question. Our hypothesis is the assumption that the DhcpNameServer parameter uses a list with a space as separators, and the NameServer copies its behavior. In addition, according to Microsoft itself on the TechNet website, if the NameServer parameter is present , it has a higher priority than the DhcpNameServer .
If the value of the NameServer is valid, it takes precedence over the value of the DhcpNameServer.
Source: technet.microsoft.com/en-us/library/cc962470.aspx .
Since the value of the DhcpNameServer parameter is allowed to have a space character as a separator, the same can be allowed for NameServer . In addition, the TechNet resource indicates that the space character is allowed to separate the elements of the value of the NameServer parameter. In fact, this property of the registry key is not standard and the GUI interface of the control panel does not know how to handle this value. The control panel uses only the comma symbol as a separator between the Preferred and Alternate DNS servers. It is worth noting that other Windows applications that work with this registry parameter work fine with a space as a separator. The same applies to the parameter value on the Advanced TCP / IP Settings tab.
Worst of all, this feature uses unwanted applications to redirect user’s DNS requests to the resources they need. It is used as the hijack DNS method and forces the user to work with spoofed DNS servers. We call them hidden because the user will not be able to see them in the settings of the network connections of the control panel.
Now that we’ve dealt with the DNS hijack, let's look at other areas in the TCP / IPv4 network settings GUI interface of the control panel. We will be interested in the TCP / IP advanced settings window on the DNS tab. The upper part of the tab contains a list that defines the order in which DNS servers are used and allows you to specify the use of more than two IP addresses as them. Each address must use its own separate line. Now, in the case where the DNS was intercepted and hidden, the TCP / IP settings will look like this.

Fig. 4. Tab with advanced DNS settings for TCP / IP protocol, which uses the option with a space as a separator.
It can be seen that in the settings on the screenshot above there are two addresses, separated by a space. In that case, if you try to click on the "Add ..." button to add two addresses, separated by a space, the system will display an error message indicating the wrong IP address. In the case of an attempt to add additional addresses of DNS servers to the already indicated hidden ones, they will be added in the GUI interface of the TCP / IP properties tab as separate lines.
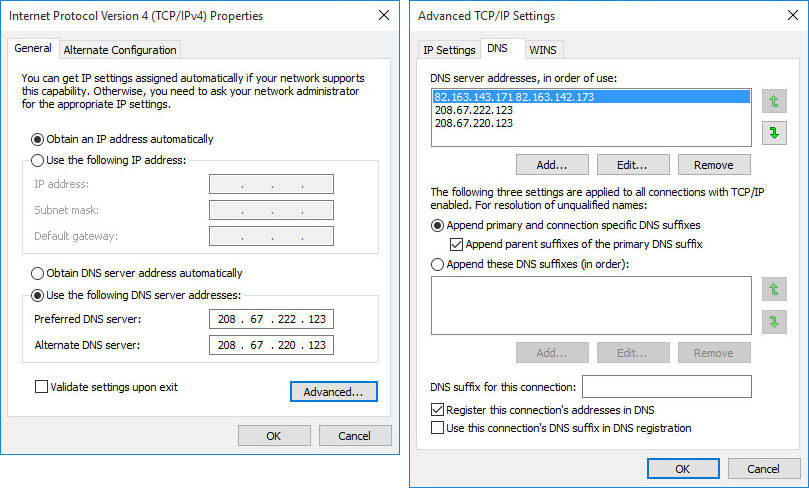
Fig. 5. Manually set addresses of DNS servers, when previously “hidden” records were already included.
Fortunately, the user can delete malicious DNS entries on the DNS tab on the TCP / IP advanced settings page.
Our specialists reported this problem to the Microsoft Security Response Center (MSRC) on May 10, 2016. MSRC recognized the problem, but did not classify it as a vulnerability, since modifying the registry value requires administrative rights. They sent the question to other development teams for reviewing the fix in future releases.
Conclusion
Note that Windows itself can work normally with the value of the NameServer parameter, which uses spaces instead of a comma as a separator. In turn, unwanted applications can use this method to hide the DNS settings in the system. It has been observed in the use of DNS Unlocker since December 2015 and works on all Windows OS, starting with Windows XP. It is interesting to note that a semicolon can be used as a separator for the DNS hijack method, however, we did not observe the use of this option in other types of malicious or unwanted software as of May 31, 2016.
Indicators of compromise
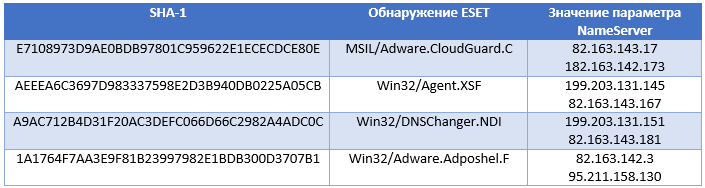
The DNS Unlocker version described above is detected by ESET as MSIL / Adware.CloudGuard.C . It uses the following IP addresses for DNS spoofing:
The following IP addresses are used as HTTP servers to inject malicious JavaScript content that displays ads on web pages.
The following malware samples use this technique.

Thus, the user could not see the settings of the DNS servers in the GUI interface of the network settings. In addition, it will also indicate that the system uses the DHCP protocol to obtain the settings. An unwanted application that performs similar operations on the system is called DNS Unlocker .
')
The DNS Unlocker application sets the victim's network settings in such a way that they point to fake DNS server addresses. When a web browser visits the victim of google-analytics.com, a fake DNS server will point to a malicious address with JavaScript content embedded there. This is done in order to advertise, which is inserted into the web page DNS Unlocker, relied on Google Analytics. Typically, a user with DNS Unlocker installed will see advertisements with a note at the bottom of a web page that says "Ads by DNSUnlocker" (Fig. 1) or something similar in a variety of other options (Fig. 2).

Fig. 1. Advertising content embedded in a web page.

Fig. 2. Phishing message to intimidate the user.
Malicious software that uses DNS address spoofing mechanisms in Windows settings is not new, besides, such instances are not even worthy of detailed coverage. However, DNS Unlocker incorporates an interesting feature that distinguishes it from other similar examples. It is used to secretly change the DNS settings in such a way that the user will not notice. The user will not be able to see the new TCP / IPv4 settings in the control panel, which are responsible for the fields of static DNS records. As a rule, when specifying the DNS server address, its address should be displayed in the list of Preferred DNS Servers settings, provided that the Use the following DNS server addresses check box is selected. In addition, the user can pay attention to the setting "Alternative DNS-server." When using DHCP to get DNS addresses (used in most configurations of home and office environments), the setting “Obtain DNS server address automatically” is active.

Fig. 3. TCP / IPv4 network settings with typical settings.
The peculiarity of the technique used by DNS Unlocker is that the static DNS address specified by it is not displayed in the list of network settings, besides, it indicates that the user receives DNS addresses automatically. The ipconfig / all command will also indicate the use of DHCP, but it will also display statically set DNS addresses. When using the ipconfig tool, however, it is impossible to establish which network connections use DHCP and which static addresses. The network settings GUI does not display the static part and assures the user of the use of DHCP. Below we answer the question why this happens, that is, what causes the static entry to not appear in the GUI interface of the network settings.
Consider the registry key that is responsible for configuring network interfaces.
HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ Tcpip \ Parameters \ Interfaces \
This registry key captures the settings of network interfaces, each of which is specified by a GUID. The settings section for each network adapter can contain the DhcpNameServer and NameServer parameters . The parameter NameServer is of interest to us. Usually, if you configure a static DNS server, use the network settings of the control panel (or use the netsh command to do this). In this case, the static server addresses will be stored in the NameServer registry parameter with the symbol “,” as a separator for the value elements.
192.168.1.21,192.168.1.22
Now consider the case when the space separator is used as the address separator in this parameter.
192.168.1.21 192.168.1.22
This small change allows you to hide the addresses of the DNS servers being used from the GUI interface of the network settings, since, in fact, one of them is the main and the second is additional. For a user, this fact means receiving advertisements embedded in websites visited by the user.
Since Windows assumes that the addresses of the primary and secondary DNS servers are already set, setting the user to new values will only add them to the end of the list of items already existing there, as shown below.
192.168.1.21 192.168.1.22,208.67.222.123,208.67.220.123
It can be seen that Windows uses the symbol “,” as a separator, while the first elements still use a space.
The question is why Windows allows this behavior of its system component. We do not have a reliable answer to this question. Our hypothesis is the assumption that the DhcpNameServer parameter uses a list with a space as separators, and the NameServer copies its behavior. In addition, according to Microsoft itself on the TechNet website, if the NameServer parameter is present , it has a higher priority than the DhcpNameServer .
If the value of the NameServer is valid, it takes precedence over the value of the DhcpNameServer.
Source: technet.microsoft.com/en-us/library/cc962470.aspx .
Since the value of the DhcpNameServer parameter is allowed to have a space character as a separator, the same can be allowed for NameServer . In addition, the TechNet resource indicates that the space character is allowed to separate the elements of the value of the NameServer parameter. In fact, this property of the registry key is not standard and the GUI interface of the control panel does not know how to handle this value. The control panel uses only the comma symbol as a separator between the Preferred and Alternate DNS servers. It is worth noting that other Windows applications that work with this registry parameter work fine with a space as a separator. The same applies to the parameter value on the Advanced TCP / IP Settings tab.
Worst of all, this feature uses unwanted applications to redirect user’s DNS requests to the resources they need. It is used as the hijack DNS method and forces the user to work with spoofed DNS servers. We call them hidden because the user will not be able to see them in the settings of the network connections of the control panel.
Now that we’ve dealt with the DNS hijack, let's look at other areas in the TCP / IPv4 network settings GUI interface of the control panel. We will be interested in the TCP / IP advanced settings window on the DNS tab. The upper part of the tab contains a list that defines the order in which DNS servers are used and allows you to specify the use of more than two IP addresses as them. Each address must use its own separate line. Now, in the case where the DNS was intercepted and hidden, the TCP / IP settings will look like this.

Fig. 4. Tab with advanced DNS settings for TCP / IP protocol, which uses the option with a space as a separator.
It can be seen that in the settings on the screenshot above there are two addresses, separated by a space. In that case, if you try to click on the "Add ..." button to add two addresses, separated by a space, the system will display an error message indicating the wrong IP address. In the case of an attempt to add additional addresses of DNS servers to the already indicated hidden ones, they will be added in the GUI interface of the TCP / IP properties tab as separate lines.

Fig. 5. Manually set addresses of DNS servers, when previously “hidden” records were already included.
Fortunately, the user can delete malicious DNS entries on the DNS tab on the TCP / IP advanced settings page.
Our specialists reported this problem to the Microsoft Security Response Center (MSRC) on May 10, 2016. MSRC recognized the problem, but did not classify it as a vulnerability, since modifying the registry value requires administrative rights. They sent the question to other development teams for reviewing the fix in future releases.
Conclusion
Note that Windows itself can work normally with the value of the NameServer parameter, which uses spaces instead of a comma as a separator. In turn, unwanted applications can use this method to hide the DNS settings in the system. It has been observed in the use of DNS Unlocker since December 2015 and works on all Windows OS, starting with Windows XP. It is interesting to note that a semicolon can be used as a separator for the DNS hijack method, however, we did not observe the use of this option in other types of malicious or unwanted software as of May 31, 2016.
Indicators of compromise
The DNS Unlocker version described above is detected by ESET as MSIL / Adware.CloudGuard.C . It uses the following IP addresses for DNS spoofing:
- 203.131.145
- 203.131.150 - 199.203.131.152
- 163.142.2 - 82.163.142.7
- 163.142.66 - 82.163.142.70
- 163.142.130 - 82.163.142.189
- 163.143.131 - 82.163.143.190
- 211.158.129 - 95.211.158.135
- 211.158.145 - 95.211.158.151
The following IP addresses are used as HTTP servers to inject malicious JavaScript content that displays ads on web pages.
- 163.143.23 - 82.163.143.250
- 88.193.133 - 209.88.193.141
The following malware samples use this technique.

Source: https://habr.com/ru/post/302544/
All Articles