XSS vulnerability still persists for wordpress
During regular inspections and studies, the security of the XSS vulnerability was discovered that affects the WordPress Jetpack plugin installed on more than a million WordPress sites. Vulnerability can be easily used with wp-comments, and therefore it is recommended to update your plugin as quickly as possible, if you have not already done so.

The security vulnerability is in the shortcode of the built-in Jetpack module, so if you have not activated it on the site, you will not be affected by this problem. An attacker could use this vulnerability by leaving a comment, a prepared shortcode, to run malicious Javascript code on a vulnerable site. Since this is a Cross-Site Scripting (XSS) vulnerability, it can allow an attacker to steal administrator credentials, insert SEO spam into the affected page, and redirect visitors to malicious websites.
')
This vulnerability is very similar to the bbPress vulnerability, which was described last week, on the source site of another copy of the text, carelessly replaced by some HTML tags.

In this case, the vulnerability investigation begins with
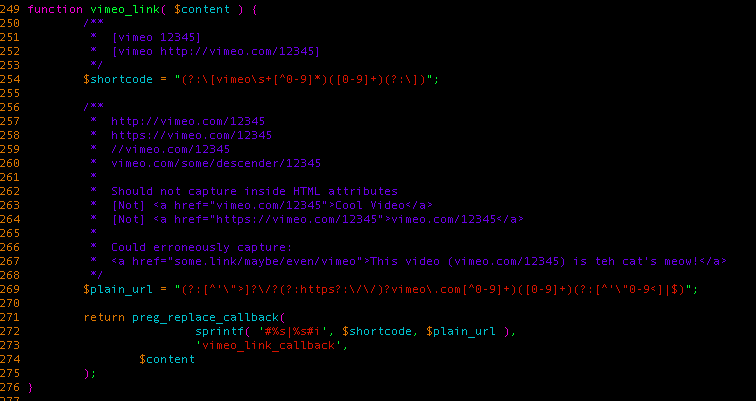
As you can see from the above regular expressions, a
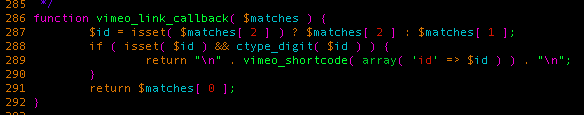
As a result, an HTML tag is returned that contains the embedded Vimeo video. Let's look at what the result looks like by sending a comment containing a

Wow, what happened there? It looks like the title attributes, ending, and single quotes have disappeared. All that had to be done was a working example that was supposed to show that we could close our header attributes accordingly and insert new arbitrary event handlers to prove our concept. As we have said, it is very easy to use.
The authors of the study worked with the Jetpack team and they immediately responded, keeping us updated on updates all this time.
If you are using a vulnerable version of this plugin, update as soon as possible! If it is not possible to do this for certain, you can use Sucuri Firewall or equivalent technology to solve the problem.

The security vulnerability is in the shortcode of the built-in Jetpack module, so if you have not activated it on the site, you will not be affected by this problem. An attacker could use this vulnerability by leaving a comment, a prepared shortcode, to run malicious Javascript code on a vulnerable site. Since this is a Cross-Site Scripting (XSS) vulnerability, it can allow an attacker to steal administrator credentials, insert SEO spam into the affected page, and redirect visitors to malicious websites.
')
Read more
This vulnerability is very similar to the bbPress vulnerability, which was described last week, on the source site of another copy of the text, carelessly replaced by some HTML tags.

In this case, the vulnerability investigation begins with
comment_text , which is used when displaying the content of comments. Vimeo_link used in such a way that it can dynamically change the output of comments.
As you can see from the above regular expressions, a
vimeo shortcode is searched for inside comments. If matches are found, they will be passed to the function vimeo_link_callback
As a result, an HTML tag is returned that contains the embedded Vimeo video. Let's look at what the result looks like by sending a comment containing a
<a title='[vimeo 123]'>abc :
Wow, what happened there? It looks like the title attributes, ending, and single quotes have disappeared. All that had to be done was a working example that was supposed to show that we could close our header attributes accordingly and insert new arbitrary event handlers to prove our concept. As we have said, it is very easy to use.
The authors of the study worked with the Jetpack team and they immediately responded, keeping us updated on updates all this time.
If you are using a vulnerable version of this plugin, update as soon as possible! If it is not possible to do this for certain, you can use Sucuri Firewall or equivalent technology to solve the problem.
Source: https://habr.com/ru/post/302328/
All Articles