Virus living exclusively in PLC
I came across an interesting article about information security in the field of industrial automation. Since the subject was not found in the Russian-speaking segment of the Internet, it was decided to translate the article into the great and powerful Russian language. In general, we will talk about very banal things. Since this is my first translation, sometimes there can be a nostalgic memory of Promt. Comments and corrections are accepted in the LAN or in the comments.
This article does not have the character of "attribution" of authorship. Only translation and some personal thoughts about it.
Authors: Ralf Spenneberg, Maik Brüggemann, Hendrik Schwartke
Source: OpenSource Security Ralf Spenneberg
Modern industrial processes are controlled by programmable logic controllers (PLCs). Many PLCs sold today have Ethernet ports onboard and can communicate via IP. Taking Siemens SIMATIC S7-1200 as a basis, we will demonstrate a virus. This vulnerability does not require any additional PC for distribution. The worm lives and works only in the PLC. It scans the network for new targets (PLC), attacks them and replicates itself on the found targets. The main, main program running on the affected PLC is not modified. The affected device begins to scan the network in search of a new target. We will analyze the effect of the virus on the target and possible methods for reducing negative consequences.
')
IT systems are critical components in modern industrial processes. These processes would not have been possible without modern communication networks. Unfortunately, with the use of IT systems and communication networks in industrial systems, the user is exposed to attacks that have long been known in IT. These hacker attacks can harm industrial systems in many ways. They can lead to large financial losses, but at the same time can have a negative impact on the lives and health of others. The effectiveness of these attacks has been demonstrated by Stuxnet . Siemens PLCs have been modified to prevent Iran from enriching nuclear fuel. The virus spread through station PCs, exploiting MS Windows vulnerabilities. The PLC software was modified so that the centrifuges used in the process were destroyed. The worm needed a computer to spread and attack the PLC through the PC. This article will demonstrate a virus / worm that spreads only through a PLC. PC or server is not required. The worm can be brought to the station via an already compromised PLC. The virus spreads to the following PLCs by copying itself and infecting the rest of the PLCs, working simultaneously with the user program.
The experiments were conducted on Siemens SIMATIC S7-1200v3. The virus was written in the programming language ST.
2015, BlackHat, USA 2015 - Maylwar launched at the PLC .
They implemented an intermediate server using the PLC communication capabilities. We use similar capabilities to implement the protocol used to distribute a virus program. Using this protocol, the worm can spread directly from the PLC to another PLC. The worm does not require further support from the system. Instead of using the already well-known Simatic S7-300, we used the new S7-1200v3 in our work.
The controller architecture is simple. It is based on a central processing unit (CPU) and optional expansion modules for digital and analog I / O. The CPU is responsible for starting and controlling the operating system of the PLC and starts the user program. Also, the CPU is responsible for communication (switching) with additional devices and controls the process.
The process image stores the status of all inputs / outputs. The user program runs cyclically. The process status is updated by the CPU at the beginning and at the end of each cycle. The cycle is limited by the cycle time. If the limit is reached, the PLC stops the user program and generates an error.

A user program consists of Program Organization Units (POU). They contain instructions for monitoring and controlling the PLC. The program for Siemens SIMATIC S7-1200 consists of:
- Organization Blocks - Organization Block (OB) - Where the user program is introduced.
- Data Block (DB) - The data block is global memory.
- Function (FC) - functions
- Function Block - functions with stored local memory.
This article also uses the TCON and TDISCON system functions. Using these functions, you can initialize or break a TCP connection with an arbitrary system. Data can be sent and received using the TRCV and TSEND commands.
Computer worms have been known since 1988 and are a well-known type of malware. Each virus attack can be described in the following phases:
- definition of a possible goal
- spread to target
- use of purpose
- execution of malicious code
On the PLC, the worm must perform the same function. The article demonstrates the implementation of each of the necessary steps.
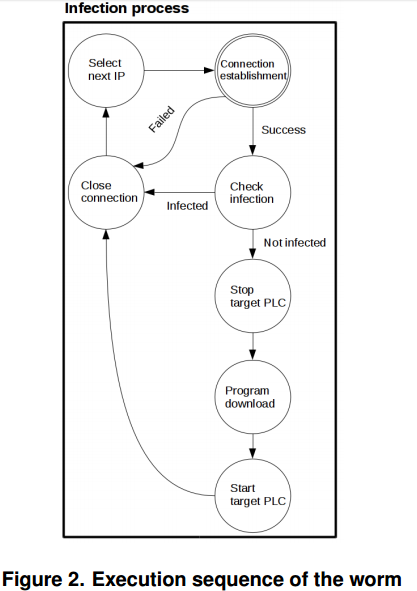
Like any other worm, the virus was written with some special features. The development took into account the specific limitations and conditions of the PLC. The condition should not be violation of the maximum cycle time. The virus should interrupt its execution for a few milliseconds. Execution can be continued during the following cycles. At the beginning of each cycle, the virus code was called again. This allowed not to violate the maximum cycle time.
Phased code execution is shown in the picture below. The execution of the virus began with the initialization of the connection with a possible goal. First of all after the connection, the virus checked whether the target was already digitized. If no infection was detected, the virus stops the user's program from running on purpose in order to allow the transfer of its own code.
After copying and running the infected PLC directly, the worm continues to search for the next possible target.
The virus begins scanning for possible targets. Siemens SIMATIC PLCs can be recognized by TCP port 102. This port can be closed using an external firewall. No other service uses this port. The S7-1200 initializes a TCP connection using TCON. The use of this command is shown in Listing 3, line 4. The IP address and port are written in line 9.
As soon as the block is called up - the PLC will try to establish communication. This happens asynchronously. The following cycles confirm the connection status. Return Value DONE (line 5) - signals whether the connection is established. If TRUE, the infection continues. If the IP address and port are unavailable - no error is displayed. Each cycle increases the counter reading by 1.

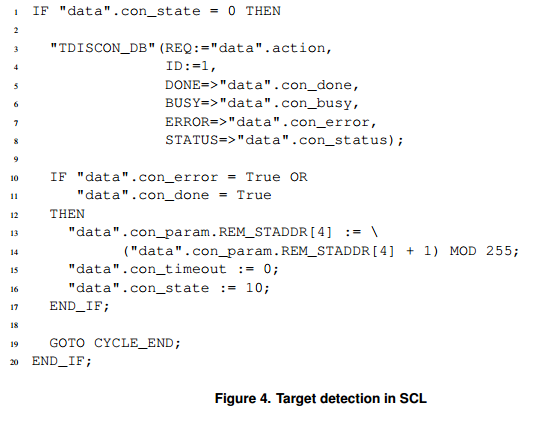
If after 200 cycles the connection was not established, the worm executes the following code. Although the connection was not established, the TDISCON unit is called to free the line for the next connection. In line 13, the IP address is incremented. Thereby, all 24 subnets are scanned for open port 102 / TCP.
During the infection phase, the worm copies itself to the attacked PLC. Typically, the software is loaded onto the controller using the Siemens TIA-Portal software. The worm mimics TIA-Portal and implements the proprietary Siemens protocol. For the analysis of the protocol and its subsequent implementation, we used Wireshark.
In this article, the protocol will be named S7CommPlus. This is a binary protocol that uses the TPKT and ISO8073 protocols. Both of these protocols use port 102 / TCP.
S7CommPlus main functions:
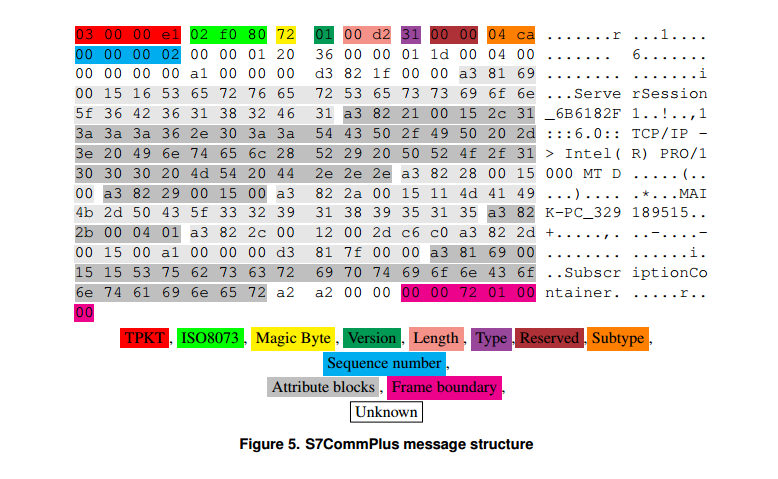
Each message used by S7CommPlus has the same structure. The picture number 5 presents the first message in the connection. TIA Portal sends this message to initiate the connection. We explain the general structure. The first 2 selected fields are the TPKT and ISO8073 protocols. Their contents are described in the relevant documentation. The next byte 0x72 is the beginning of the message from the S7CommPlus. The version number differs between the various protocol options. The field length does not take into account the frame boundary. If there is no frame boundary, then subsequent data is transmitted in additional messages. After the field length, the cell type is transmitted. The subtype further defines the messages. The sequence number is incremented by 1 for each message. Additional data is transmitted in the form of attribute blocks (attribute blocks).
The data is formed according to the following block attributes. Picture 6 shows the first attributes of the previous picture. Each attribute begins with byte 0xA3. This block contains a string. The line starts with its length and contains the value.

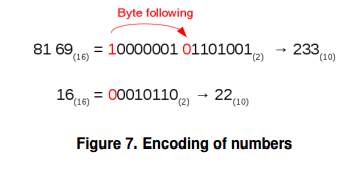
In attribute blocks, values are encoded in a special way. The value may have a variable length. The first bits of each byte are moved to the beginning of the next byte. Picture 7 explains the decoding of the attribute identifier and the field length from the previous example. If the value is stored inside an attribute block, no encoding is applied.
S7CommPlus protocol defines anti-repeat. For this, the PLC sends a random value of 25 bytes in the reply message. The value is defined between 0x06 and 0x7f. Byte anti-replay is calculated by the following formula.

All further messages sent by TIAPortal should use anti-replay byte in their 24 byte. Attribute blocks highlighted in gray should also be displayed.

A special message is used to transfer the program. (Picture 10). Each message carries one POU element. The block number indicates the location in the PLC memory.
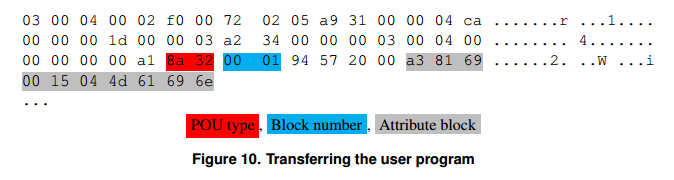
Several attribute blocks make up the message header. In addition to the actual byte code, meta-information is recorded in S7. This meta information determines the required memory (required), the date the block was created, the block number, the language used, the source code, and the security features. TIA Portal can use this information to verify the code.
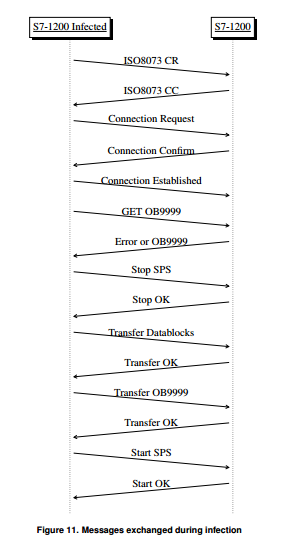
During the transfer of the user program, some messages are exchanged that are not required for the process.
These inappropriate messages lead to an increase in the memory required for the virus, so you can skip them. Picture 11 shows the necessary messages for a successful injection.
Transfer started. In order to avoid reinfection, the virus checks the target and tries to download a copy of itself. Downloading an additional code is possible only after stopping the PLC. When the program is loaded, the PLC starts up again.
Based on the protocol analysis, the program transfer can be recorded, modified and sent again to the PLC. All necessary messages are known.
To store the commands in the virus, we use a static block of global data (DB). Additional DBs are used to store temporary variables and as a receive / transfer data buffer. The permanent block data stores all messages necessary for infection. This block cannot be generated using TIA Portla and must be written by hand.

The transferred code is added to the user program already running on the PLC. Additional OBs and required DBs added. The user program code is original and has not been fixed. The OB unit is automatically detected by the PLC and executed.
habrastorage.org/files/7d7/479/d4c/7d7479d4c7ba4fbdbde958ed124016ca.png
During the functioning of the virus, we implement various functions to demonstrate the possibility of the influence of the virus.
(Server management and control)
Our worm will attempt to connect to a C & C server. The communication protocol is TCP. Through the C & C server you can organize the execution of various functions.
After the worm connects to the C & C server, connections to additional clients in the PLC network can be initiated using the built-in Socks4 proxy.
Operation (PLC code execution) may be stopped due to a violation of the cycle time. The worm performs (realizes) an infinite loop that triggers an error condition in the PLC (DoS attack).
The worm can control the output of the PLC. When using the system function "POKE", various variables within the process can be changed.
TIA Portal can check the user program in the PLC and can detect both changes and additions of various functions (POU elements). (Picture 14). The area of functions used by the virus is highlighted in red. The analysis of these functions is not possible, because TIA Portal only analyzes the XML code. In addition, due to the use of TIA Portala errors, the worm can cause application crashes when it crashes.
To effect infection, the PLC should stop for approximately 10 seconds. The user program will not be executed at this time. An interrupt can be seen and logged in to the PLC.
The worm generates unusual network traffic. During the network scanning and infection phase, many suspicious packets are sent.
Since the virus is in the PLC memory and is part of the user program, as a result of the restart or power outage the worm will remain in the device.
Through TIA Portal, you can return to the factory settings, which will lead to the complete removal of data from the PLC, including the worm.
The worm is recorded in the OB9999 block; when overwriting this block, the worm will be deleted.
The maximum cycle time is fixed in the settings. The default limit is 150 ms. The worm must not violate this limit. We measured the PLC cycle time without any user program — it is 0 ms. Then we infected S7 with our worm and measured the cycle time again. The maximum measured cycle time is 7ms. This is 4.7% of the allowable limit.
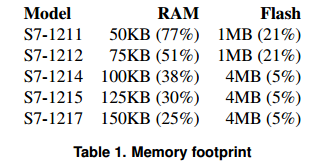
The worm requires 38.5 kB of RAM for storage. 9 KB (23.3%) is needed to execute malicious code. Additionally, you need 216.6 KB of flash memory. The table displays the available memory in various models.
The S7-1200v3 PLC offers 3 different protection functions. We will analyze each of them and assess if they will protect the PLC from virus injection. Analysis based on TIA Portl V11, Update 5 and S7-1200v3 with firmware 3.0.2
Knowhow protection protects the user program from unauthorized access, without the correct password unauthorized access and modification of the program blocks is impossible. Knowhow protection is implemented using attribute blocks. These blocks are written to the PLC during program download. The blocks are displayed in the picture 15. The saved password hash, generated on the basis of the password P, is calculated using the following formula:

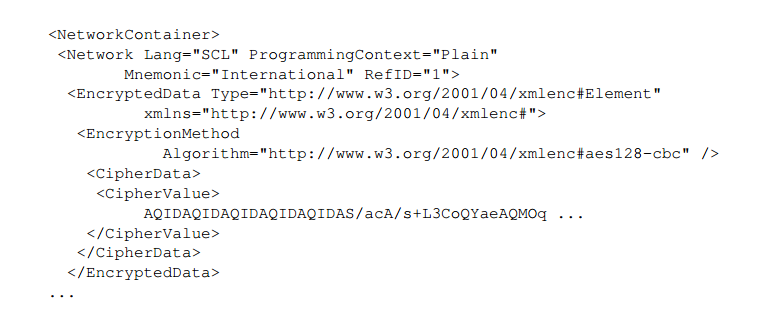
TIA Portal evaluates a block attribute. If the flag is set, TIA Portal prohibits reading and writing to the corresponding blocks information without the correct password. The source PLC code is encrypted using AES128-CBC. This prevents access to the code. Figure 16 shows the encrypted source code.
No integrity check. A block can be read and modified despite knowhow protection. Protection is implemented by TIA Portala, not PLC. When using self-written tools to read and write blocks on a PLC, any access is granted. Even the knowhow security flag can be reset as a result of access using TIAPortal. AES-key can be retrieved or retrieved. The encryption key can be obtained from the password hash. The password hash can be read using self-written software. The key is calculated by the following formula:

* fixed by the manufacturer SSA-833048
Conclusion: This protection does not help against the virus.
Copy protection prohibits duplication of the user program on the second PLC. The serial number of the target PLC is stored in the user program, in order to prevent the user program from downloading to another PLC via TIA Portal. The serial number is stored in a separate attribute block.
The integrity of an attribute block is not protected. Stored serial number can be changed or moved or deleted. The PLC does not check the serial number itself. The check is implemented only with the help of TIA Portal.
* fixed by the manufacturer SSA-833048
Conclusion: This protection does not help against the virus.
Access protection prevents access to the PLC using the S7CommPlus protocol without a password. There are 3 different levels of protection available. The table shows the different levels of protection:
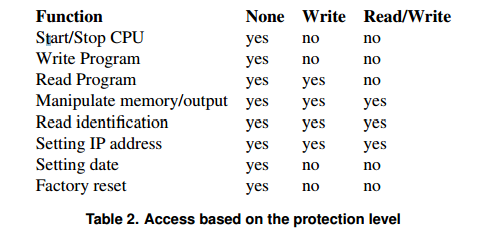
Authentication uses a mechanism to respond to a request.
Conclusion: Access protection can protect the PLC from a virus attack. Write protection prevents any code changes in the PLC. Using the query response mechanism is relatively safe. If the password used is not known, the worm cannot infect the PLC. Access protection is disabled by default.
In this paper, we demonstrate the capabilities of a worm for a PLC. Such a virus is a new threat in industrial networks. Traditionally, such networks are well protected from outside attacks. With the introduction of an already infected worm, the PLC makes other devices not only the target of the attack, but also the sources of the attack. Infected PLCs can be distributed by distributors, or infection can occur during transport. The worm can spread inside the controller and does not require any standard PCs or servers. Thus, it can not be detected by antivirus. Moreover, the operator has very little ability to detect malicious code in the PLC.
As you know, for every tricky nut, there is a threaded bolt. Personally, the author believes that the problem of industrial automation security is slightly inflated, due to the lack of a unified unified environment for executing malicious code on different PLCs from different manufacturers. Orientation to Siemens, Allen-Bradley, Honeywell, B & R, etc. manufacturers poses the task of writing a virus under a strictly defined device.
In general, the principle of the spread of the virus within a network consisting of controllers, base / engineering stations and control panels - deserves special attention. In addition, the example of StuxNet seems to have shown the world a possible situation. How and why the attack was implemented - is unlikely to know. But everyone likes to give it as an example ...
In modern realities, a greater threat is a non-compromise in the performance of work and subsequent maintenance. The profession itself “Programmer of Industrial Process Control Systems”, “Programmer of Controllers for Industrial Process Control Systems”, etc., are also becoming very popular. which leads to a growing number of low-skilled personnel.
So while we are frightened by the future industrial SkyNet, we must remain attentive to the executable code.
This article does not have the character of "attribution" of authorship. Only translation and some personal thoughts about it.
Authors: Ralf Spenneberg, Maik Brüggemann, Hendrik Schwartke
Source: OpenSource Security Ralf Spenneberg
Modern industrial processes are controlled by programmable logic controllers (PLCs). Many PLCs sold today have Ethernet ports onboard and can communicate via IP. Taking Siemens SIMATIC S7-1200 as a basis, we will demonstrate a virus. This vulnerability does not require any additional PC for distribution. The worm lives and works only in the PLC. It scans the network for new targets (PLC), attacks them and replicates itself on the found targets. The main, main program running on the affected PLC is not modified. The affected device begins to scan the network in search of a new target. We will analyze the effect of the virus on the target and possible methods for reducing negative consequences.
')
1. Introduction
IT systems are critical components in modern industrial processes. These processes would not have been possible without modern communication networks. Unfortunately, with the use of IT systems and communication networks in industrial systems, the user is exposed to attacks that have long been known in IT. These hacker attacks can harm industrial systems in many ways. They can lead to large financial losses, but at the same time can have a negative impact on the lives and health of others. The effectiveness of these attacks has been demonstrated by Stuxnet . Siemens PLCs have been modified to prevent Iran from enriching nuclear fuel. The virus spread through station PCs, exploiting MS Windows vulnerabilities. The PLC software was modified so that the centrifuges used in the process were destroyed. The worm needed a computer to spread and attack the PLC through the PC. This article will demonstrate a virus / worm that spreads only through a PLC. PC or server is not required. The worm can be brought to the station via an already compromised PLC. The virus spreads to the following PLCs by copying itself and infecting the rest of the PLCs, working simultaneously with the user program.
The experiments were conducted on Siemens SIMATIC S7-1200v3. The virus was written in the programming language ST.
2. Related research directions
2015, BlackHat, USA 2015 - Maylwar launched at the PLC .
They implemented an intermediate server using the PLC communication capabilities. We use similar capabilities to implement the protocol used to distribute a virus program. Using this protocol, the worm can spread directly from the PLC to another PLC. The worm does not require further support from the system. Instead of using the already well-known Simatic S7-300, we used the new S7-1200v3 in our work.
3. A bit about the PLC architecture
The controller architecture is simple. It is based on a central processing unit (CPU) and optional expansion modules for digital and analog I / O. The CPU is responsible for starting and controlling the operating system of the PLC and starts the user program. Also, the CPU is responsible for communication (switching) with additional devices and controls the process.
The process image stores the status of all inputs / outputs. The user program runs cyclically. The process status is updated by the CPU at the beginning and at the end of each cycle. The cycle is limited by the cycle time. If the limit is reached, the PLC stops the user program and generates an error.

A user program consists of Program Organization Units (POU). They contain instructions for monitoring and controlling the PLC. The program for Siemens SIMATIC S7-1200 consists of:
- Organization Blocks - Organization Block (OB) - Where the user program is introduced.
- Data Block (DB) - The data block is global memory.
- Function (FC) - functions
- Function Block - functions with stored local memory.
This article also uses the TCON and TDISCON system functions. Using these functions, you can initialize or break a TCP connection with an arbitrary system. Data can be sent and received using the TRCV and TSEND commands.
4. Computer Worms
Computer worms have been known since 1988 and are a well-known type of malware. Each virus attack can be described in the following phases:
- definition of a possible goal
- spread to target
- use of purpose
- execution of malicious code
On the PLC, the worm must perform the same function. The article demonstrates the implementation of each of the necessary steps.
5. Implementation of a virus for Siemens SIMATIC S7-1200
5.1 Architecture
Like any other worm, the virus was written with some special features. The development took into account the specific limitations and conditions of the PLC. The condition should not be violation of the maximum cycle time. The virus should interrupt its execution for a few milliseconds. Execution can be continued during the following cycles. At the beginning of each cycle, the virus code was called again. This allowed not to violate the maximum cycle time.
Phased code execution is shown in the picture below. The execution of the virus began with the initialization of the connection with a possible goal. First of all after the connection, the virus checked whether the target was already digitized. If no infection was detected, the virus stops the user's program from running on purpose in order to allow the transfer of its own code.
After copying and running the infected PLC directly, the worm continues to search for the next possible target.

5.2 Search and target definition
The virus begins scanning for possible targets. Siemens SIMATIC PLCs can be recognized by TCP port 102. This port can be closed using an external firewall. No other service uses this port. The S7-1200 initializes a TCP connection using TCON. The use of this command is shown in Listing 3, line 4. The IP address and port are written in line 9.
As soon as the block is called up - the PLC will try to establish communication. This happens asynchronously. The following cycles confirm the connection status. Return Value DONE (line 5) - signals whether the connection is established. If TRUE, the infection continues. If the IP address and port are unavailable - no error is displayed. Each cycle increases the counter reading by 1.

If after 200 cycles the connection was not established, the worm executes the following code. Although the connection was not established, the TDISCON unit is called to free the line for the next connection. In line 13, the IP address is incremented. Thereby, all 24 subnets are scanned for open port 102 / TCP.

5.3. Infection
During the infection phase, the worm copies itself to the attacked PLC. Typically, the software is loaded onto the controller using the Siemens TIA-Portal software. The worm mimics TIA-Portal and implements the proprietary Siemens protocol. For the analysis of the protocol and its subsequent implementation, we used Wireshark.
5.3.1. Transmission Protocol Description
In this article, the protocol will be named S7CommPlus. This is a binary protocol that uses the TPKT and ISO8073 protocols. Both of these protocols use port 102 / TCP.
S7CommPlus main functions:
- PLC control
- Start / Stop PLC
- Reading and writing variables
- Transfer of the program (loading / unloading)
- Debugging
- Provision of debug information
- Accident Notification
5.3.2. Code
Each message used by S7CommPlus has the same structure. The picture number 5 presents the first message in the connection. TIA Portal sends this message to initiate the connection. We explain the general structure. The first 2 selected fields are the TPKT and ISO8073 protocols. Their contents are described in the relevant documentation. The next byte 0x72 is the beginning of the message from the S7CommPlus. The version number differs between the various protocol options. The field length does not take into account the frame boundary. If there is no frame boundary, then subsequent data is transmitted in additional messages. After the field length, the cell type is transmitted. The subtype further defines the messages. The sequence number is incremented by 1 for each message. Additional data is transmitted in the form of attribute blocks (attribute blocks).

5.3.3. Attribute blocks (Blocks Attributes)
The data is formed according to the following block attributes. Picture 6 shows the first attributes of the previous picture. Each attribute begins with byte 0xA3. This block contains a string. The line starts with its length and contains the value.

5.3.4 Value Coding
In attribute blocks, values are encoded in a special way. The value may have a variable length. The first bits of each byte are moved to the beginning of the next byte. Picture 7 explains the decoding of the attribute identifier and the field length from the previous example. If the value is stored inside an attribute block, no encoding is applied.

5.3.5. Anti-replay mechanism
S7CommPlus protocol defines anti-repeat. For this, the PLC sends a random value of 25 bytes in the reply message. The value is defined between 0x06 and 0x7f. Byte anti-replay is calculated by the following formula.

All further messages sent by TIAPortal should use anti-replay byte in their 24 byte. Attribute blocks highlighted in gray should also be displayed.

5.3.6. Program transfer
A special message is used to transfer the program. (Picture 10). Each message carries one POU element. The block number indicates the location in the PLC memory.

Several attribute blocks make up the message header. In addition to the actual byte code, meta-information is recorded in S7. This meta information determines the required memory (required), the date the block was created, the block number, the language used, the source code, and the security features. TIA Portal can use this information to verify the code.
5.3.7. Identifying required messages
During the transfer of the user program, some messages are exchanged that are not required for the process.
These inappropriate messages lead to an increase in the memory required for the virus, so you can skip them. Picture 11 shows the necessary messages for a successful injection.
Transfer started. In order to avoid reinfection, the virus checks the target and tries to download a copy of itself. Downloading an additional code is possible only after stopping the PLC. When the program is loaded, the PLC starts up again.

5.3.8. General implementation
Based on the protocol analysis, the program transfer can be recorded, modified and sent again to the PLC. All necessary messages are known.
To store the commands in the virus, we use a static block of global data (DB). Additional DBs are used to store temporary variables and as a receive / transfer data buffer. The permanent block data stores all messages necessary for infection. This block cannot be generated using TIA Portla and must be written by hand.

6. Run the virus
The transferred code is added to the user program already running on the PLC. Additional OBs and required DBs added. The user program code is original and has not been fixed. The OB unit is automatically detected by the PLC and executed.
habrastorage.org/files/7d7/479/d4c/7d7479d4c7ba4fbdbde958ed124016ca.png
7. Perform Malware Functions
During the functioning of the virus, we implement various functions to demonstrate the possibility of the influence of the virus.
7.1. Command & Control Server
(Server management and control)
Our worm will attempt to connect to a C & C server. The communication protocol is TCP. Through the C & C server you can organize the execution of various functions.
7.2. Socks4 proxy
After the worm connects to the C & C server, connections to additional clients in the PLC network can be initiated using the built-in Socks4 proxy.
7.3. Service failure
Operation (PLC code execution) may be stopped due to a violation of the cycle time. The worm performs (realizes) an infinite loop that triggers an error condition in the PLC (DoS attack).
7.4 Output Manipulation
The worm can control the output of the PLC. When using the system function "POKE", various variables within the process can be changed.
8. Virus detection. Opposition Worm Resources
8.1 Virus Detection
8.1.1. TIA Portal
TIA Portal can check the user program in the PLC and can detect both changes and additions of various functions (POU elements). (Picture 14). The area of functions used by the virus is highlighted in red. The analysis of these functions is not possible, because TIA Portal only analyzes the XML code. In addition, due to the use of TIA Portala errors, the worm can cause application crashes when it crashes.
8.1.2. PLC stop
To effect infection, the PLC should stop for approximately 10 seconds. The user program will not be executed at this time. An interrupt can be seen and logged in to the PLC.
8.1.3. Network traffic
The worm generates unusual network traffic. During the network scanning and infection phase, many suspicious packets are sent.
8.2 Opposition
8.2.1. PLC restart
Since the virus is in the PLC memory and is part of the user program, as a result of the restart or power outage the worm will remain in the device.
8.2.2. Reset to factory settings
Through TIA Portal, you can return to the factory settings, which will lead to the complete removal of data from the PLC, including the worm.
8.2.3. Download program
The worm is recorded in the OB9999 block; when overwriting this block, the worm will be deleted.
8.3. Worm Resources
8.3.1. Cycle time
The maximum cycle time is fixed in the settings. The default limit is 150 ms. The worm must not violate this limit. We measured the PLC cycle time without any user program — it is 0 ms. Then we infected S7 with our worm and measured the cycle time again. The maximum measured cycle time is 7ms. This is 4.7% of the allowable limit.
8.3.2. Memory
The worm requires 38.5 kB of RAM for storage. 9 KB (23.3%) is needed to execute malicious code. Additionally, you need 216.6 KB of flash memory. The table displays the available memory in various models.

9. Security features
The S7-1200v3 PLC offers 3 different protection functions. We will analyze each of them and assess if they will protect the PLC from virus injection. Analysis based on TIA Portl V11, Update 5 and S7-1200v3 with firmware 3.0.2
9.1. Knowhow protection
Knowhow protection protects the user program from unauthorized access, without the correct password unauthorized access and modification of the program blocks is impossible. Knowhow protection is implemented using attribute blocks. These blocks are written to the PLC during program download. The blocks are displayed in the picture 15. The saved password hash, generated on the basis of the password P, is calculated using the following formula:

TIA Portal evaluates a block attribute. If the flag is set, TIA Portal prohibits reading and writing to the corresponding blocks information without the correct password. The source PLC code is encrypted using AES128-CBC. This prevents access to the code. Figure 16 shows the encrypted source code.

9.1.1. Method vulnerability
No integrity check. A block can be read and modified despite knowhow protection. Protection is implemented by TIA Portala, not PLC. When using self-written tools to read and write blocks on a PLC, any access is granted. Even the knowhow security flag can be reset as a result of access using TIAPortal. AES-key can be retrieved or retrieved. The encryption key can be obtained from the password hash. The password hash can be read using self-written software. The key is calculated by the following formula:

* fixed by the manufacturer SSA-833048
Conclusion: This protection does not help against the virus.
9.2. Copy Protection
Copy protection prohibits duplication of the user program on the second PLC. The serial number of the target PLC is stored in the user program, in order to prevent the user program from downloading to another PLC via TIA Portal. The serial number is stored in a separate attribute block.
9.2.1. Method vulnerability
The integrity of an attribute block is not protected. Stored serial number can be changed or moved or deleted. The PLC does not check the serial number itself. The check is implemented only with the help of TIA Portal.
* fixed by the manufacturer SSA-833048
Conclusion: This protection does not help against the virus.
9.3. Access protection
Access protection prevents access to the PLC using the S7CommPlus protocol without a password. There are 3 different levels of protection available. The table shows the different levels of protection:

Authentication uses a mechanism to respond to a request.
Conclusion: Access protection can protect the PLC from a virus attack. Write protection prevents any code changes in the PLC. Using the query response mechanism is relatively safe. If the password used is not known, the worm cannot infect the PLC. Access protection is disabled by default.
10. Conclusion
In this paper, we demonstrate the capabilities of a worm for a PLC. Such a virus is a new threat in industrial networks. Traditionally, such networks are well protected from outside attacks. With the introduction of an already infected worm, the PLC makes other devices not only the target of the attack, but also the sources of the attack. Infected PLCs can be distributed by distributors, or infection can occur during transport. The worm can spread inside the controller and does not require any standard PCs or servers. Thus, it can not be detected by antivirus. Moreover, the operator has very little ability to detect malicious code in the PLC.
From the author of the translation
As you know, for every tricky nut, there is a threaded bolt. Personally, the author believes that the problem of industrial automation security is slightly inflated, due to the lack of a unified unified environment for executing malicious code on different PLCs from different manufacturers. Orientation to Siemens, Allen-Bradley, Honeywell, B & R, etc. manufacturers poses the task of writing a virus under a strictly defined device.
In general, the principle of the spread of the virus within a network consisting of controllers, base / engineering stations and control panels - deserves special attention. In addition, the example of StuxNet seems to have shown the world a possible situation. How and why the attack was implemented - is unlikely to know. But everyone likes to give it as an example ...
In modern realities, a greater threat is a non-compromise in the performance of work and subsequent maintenance. The profession itself “Programmer of Industrial Process Control Systems”, “Programmer of Controllers for Industrial Process Control Systems”, etc., are also becoming very popular. which leads to a growing number of low-skilled personnel.
So while we are frightened by the future industrial SkyNet, we must remain attentive to the executable code.
Source: https://habr.com/ru/post/302276/
All Articles