ESET specialists released a tool to decrypt TeslaCrypt files
Our specialists have released a special service tool - a decrypter (decryptor) of TeslaCrypt encrypted files with the extortioner. The TeslaCryptDecryptor application will help to decrypt files for users who are affected by the activities of the new TeslaCrypt malware v3 and v4. Creation of the tool became possible after the cybercriminals behind its development closed the project, and one of our analysts managed to get a universal key for decrypting files.

One of our anti-virus experts, Igor Kabina, who monitored the activities of this malicious program and the changes associated with it, is the author of this tool. We noticed a decrease in TeslaCrypt activity a few weeks ago, when it became obvious that the authors are going to refuse to support their “product”. At the same time, other cybercriminals, who earned on the distribution of TeslaCrypt, began to switch to another extortionist CryptProjectXXX .
')
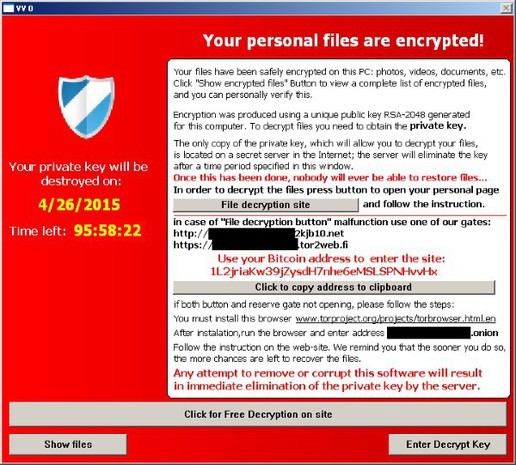
Fig. TeslaCrypt redemption window.
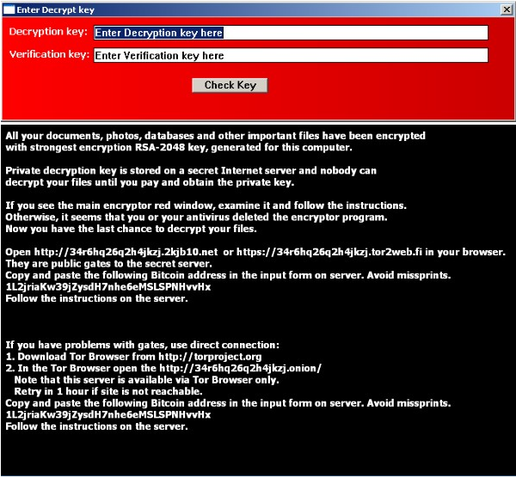
Fig. Input window interface including TeslaCrypt.
ESET antivirus products detect ransomware malicious files like Win32 / Filecoder.TeslaCrypt . Extortionist can use extensions such as .xxx, .ttt, .micro, .mp3 for encrypted files.
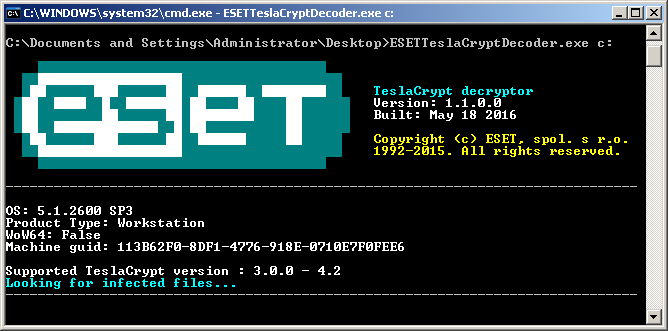
Fig. Interface tool ESETTeslaCryptDecryptor.
ESETTeslaCryptDecryptor is best run with a drive letter argument, i.e., for example, "ESETTeslaCryptDecryptor.exe C :." The program will automatically search for files encrypted on the volume with their subsequent decryption.
In addition, the program supports the following command line keys:
It must be emphasized that extortionists remain one of the most dangerous computer threats today, therefore preventing infection by this type of malware is very important. You should regularly install updates for the OS, as well as the software used. In addition, you should use reliable security solutions and use data backup. Backup is one of the main mechanisms to protect against the destructive activities of extortionists.
We also advise all users to be very careful when following links in emails or browsers, as well as when opening files in attachments. This is especially true for messages that come from unknown sources or just look suspicious.

One of our anti-virus experts, Igor Kabina, who monitored the activities of this malicious program and the changes associated with it, is the author of this tool. We noticed a decrease in TeslaCrypt activity a few weeks ago, when it became obvious that the authors are going to refuse to support their “product”. At the same time, other cybercriminals, who earned on the distribution of TeslaCrypt, began to switch to another extortionist CryptProjectXXX .
')

Fig. TeslaCrypt redemption window.

Fig. Input window interface including TeslaCrypt.
ESET antivirus products detect ransomware malicious files like Win32 / Filecoder.TeslaCrypt . Extortionist can use extensions such as .xxx, .ttt, .micro, .mp3 for encrypted files.

Fig. Interface tool ESETTeslaCryptDecryptor.
ESETTeslaCryptDecryptor is best run with a drive letter argument, i.e., for example, "ESETTeslaCryptDecryptor.exe C :." The program will automatically search for files encrypted on the volume with their subsequent decryption.
In addition, the program supports the following command line keys:
- / s - start in silent mode;
- / f - launch in “forced” mode;
- / d - start in debug mode;
- / n - just list the files encrypted by the extortioner (without automatic decryption);
- / h or /? - Help parameters;
It must be emphasized that extortionists remain one of the most dangerous computer threats today, therefore preventing infection by this type of malware is very important. You should regularly install updates for the OS, as well as the software used. In addition, you should use reliable security solutions and use data backup. Backup is one of the main mechanisms to protect against the destructive activities of extortionists.
We also advise all users to be very careful when following links in emails or browsers, as well as when opening files in attachments. This is especially true for messages that come from unknown sources or just look suspicious.
Source: https://habr.com/ru/post/302270/
All Articles