Overview of options for organizing access to corporate network services from the Internet

© Alexei Kivshenko, 1880
This article provides an overview of five options for solving the problem of organizing access to corporate network services from the Internet. The review provides an analysis of options for safety and feasibility, which will help to understand the essence of the issue, refresh and systematize their knowledge as novice professionals, and more experienced. Article materials can be used to justify your design decisions.
When considering options as an example, take the network in which you want to publish:
- Corporate mail server (Web-mail).
- Corporate Terminal Server (RDP).
- Extranet service for counterparties (Web-API).
Option 1. Flat network
In this embodiment, all the nodes of the corporate network are contained in one, common to all networks (the “Internal network”), within which communication between them is not limited. The network is connected to the Internet through a border router / firewall (hereinafter referred to as IFW ).
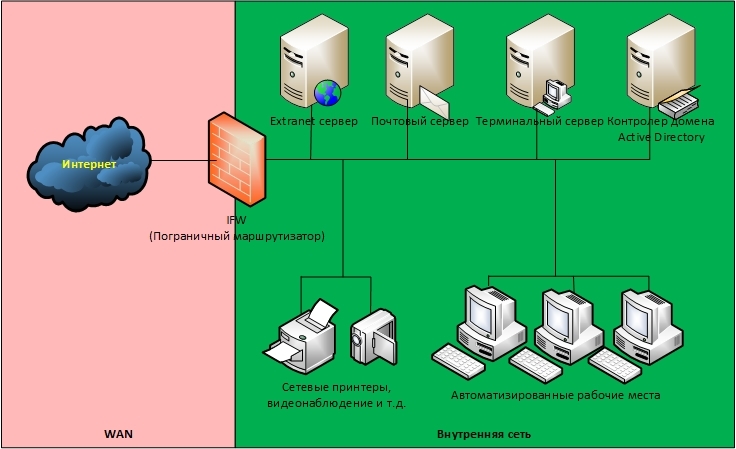
Access nodes in the Internet through NAT , and access to services from the Internet through Port forwarding .
')
Advantages of the option :
- Minimum requirements for the IFW functionality (can be done on almost anyone, even a home router).
- Minimum requirements for knowledge of the specialist implementing the option.
Disadvantages option :
- The minimum level of security. In the case of a hack, in which the Intruder gains control over one of the servers published on the Internet, all other nodes and communication channels of the corporate network become available to him for further attack.
Analogy with real life
Such a network can be compared with a company where staff and customers are in the same common room (open space)

© hrmaximum.ru
Option 2. DMZ
To eliminate the previously mentioned deficiency, network nodes accessible from the Internet are placed in a dedicated segment — the demilitarized zone (DMZ). The DMZ is organized using firewalls that separate it from the Internet ( IFW ) and from the internal network ( DFW ).
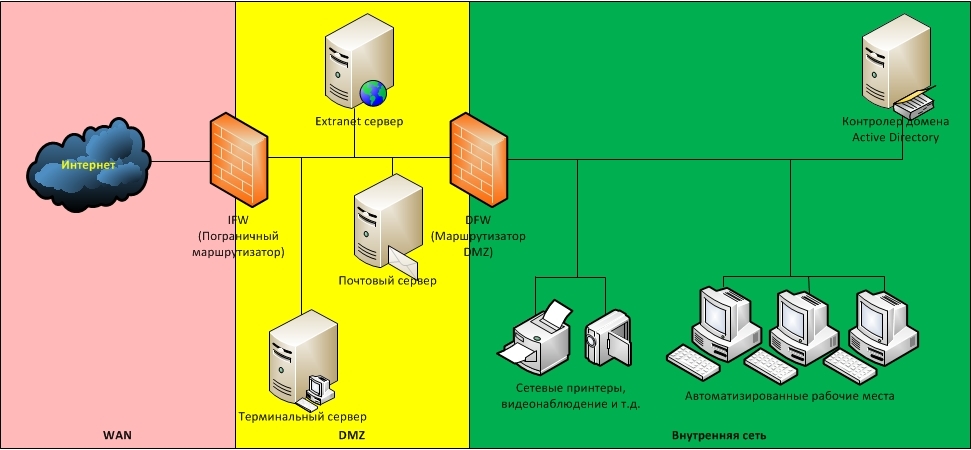
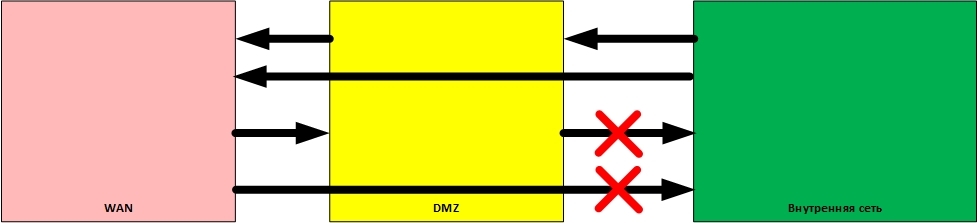
The rules for filtering firewalls are as follows:
- From the internal network, you can initiate connections in the DMZ and in the WAN (Wide Area Network).
- From the DMZ, it is possible to initiate connections in the WAN.
- From the WAN, you can initiate connections in the DMZ.
- Initiation of connections from the WAN and DMZ to the internal network is prohibited.
Advantages of the option:
- Increased network security against hacking of individual services. Even if one of the servers is hacked, the Intruder will not be able to access resources on the internal network (for example, network printers, video surveillance systems, etc.).
Disadvantages option:
- By itself, the removal of servers in the DMZ does not increase their security.
- An additional ME is required to separate the DMZ from the internal network.
Analogy with real life
This version of the network architecture is similar to the organization of the working and client zones in a company, where clients can only be in the client zone, and staff can be in both the client and work zones. DMZ segment - this is exactly the analogue of the client zone.

© autobam.ru
Option 3. Separation of services on the Front-End and Back-End
As noted earlier, hosting a server in the DMZ in no way improves the security of the service itself. One of the ways to correct the situation is to divide the functional of the service into two parts: Front-End and Back-End . In addition, each part is located on a separate server, between which the network interaction is organized. Front-End servers that implement the functionality of interaction with clients located on the Internet are placed in the DMZ, and the Back-End servers that implement the rest of the functionality are left on the internal network. For the interaction between them on the DFW create rules that allow the initiation of connections from the Front-End to the Back-End.
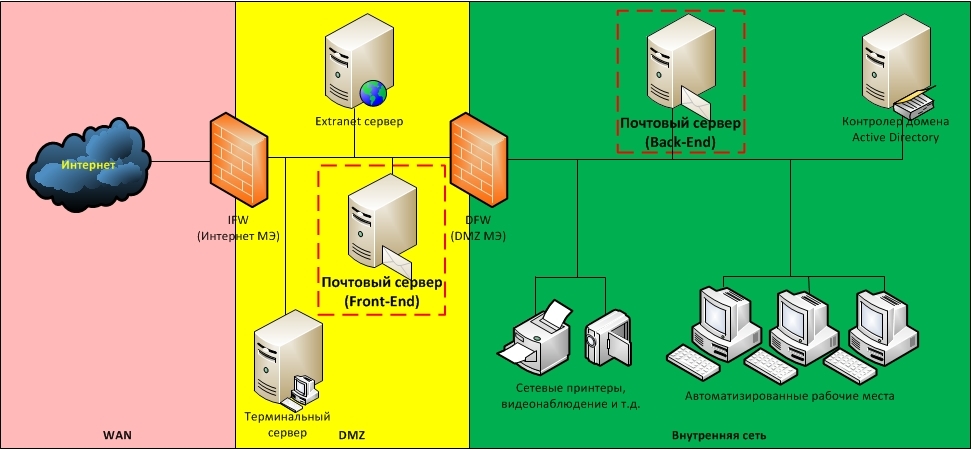
As an example, consider a corporate mail service that serves customers both from within the network and from the Internet. Clients from the inside use POP3 / SMTP, and clients from the Internet work through a Web interface. Usually at the implementation stage, companies choose the easiest way to deploy a service and put all its components on one server. Then, as the need to ensure information security is realized, the functionality of the service is divided into parts, and the part that is responsible for servicing clients from the Internet (Front-End) is transferred to a separate server, which interacts with the server that implements the remaining functionality (Back -End). At the same time, the Front-End is placed in the DMZ, and the Back-End remains in the internal segment. For communication between the Front-End and the Back-End on the DFW, create a rule allowing the initiation of connections from the Front-End to the Back-End.
Advantages of the option:
- In the general case, attacks directed against the protected service can “stumble” on the Front-End, which will allow neutralizing or significantly reducing the possible damage. For example, attacks such as TCP SYN Flood or slow http read , directed at the service, will lead to the fact that the Front-End server may be unavailable, while the Back-End will continue to function normally and serve users.
- In the general case, the Back-End server may not have access to the Internet, which, if it is hacked (for example, locally running malicious code), will make it difficult to manage it remotely from the Internet.
- Front-End is well suited for hosting an application-level firewall (for example, a Web application firewall) or an intrusion prevention system (IPS, for example snort).
Disadvantages option:
- For communication between the Front-End and the Back-End on the DFW , a rule is created that allows the initiation of a connection from the DMZ to the internal network, which creates threats associated with the use of this rule by other nodes in the DMZ (for example, by implementing IP spoofing, ARP) attacks. poisoning, etc.)
- Not all services can be divided into Front-End and Back-End.
- The company should implement the business processes of updating the rules for firewalling.
- The company must implement mechanisms for protection against attacks from the Offenders who have access to the server in the DMZ.
Notes
- In real life, even without dividing servers into Front-End and Back-End servers from the DMZ, it is often necessary to contact servers located on the internal network, therefore the indicated disadvantages of this option will also be true for the previous option considered.
- If we consider the protection of applications that work through the Web interface, then even if the server does not support separation of functions on the Front-End and Back-End, using http reverse proxy servers (for example, nginx) as the Front-End will minimize the risks associated with attacks on denial of service. For example, SYN flood attacks can make http reverse proxy inaccessible while the back-end will continue to work.
Analogy with real life
This option is essentially similar to the organization of labor, in which for highly loaded workers use assistants - secretaries. Then the Back-End will be the equivalent of a busy employee, and the Front-End will be the equivalent of a secretary.

© mln.kz
Option 4. Protected DMZ
The DMZ is the part of the network that is accessible from the Internet and, as a result, is at the highest risk of node compromise. The DMZ design and the approaches used in it should ensure maximum survivability in conditions when the Intruder has gained control of one of the nodes in the DMZ. As a possible attack, we consider attacks that affect almost all information systems that work with default settings:
- Cam-table overflow
- ARP poisoning
- Rogue DHCP Server
- DHCP starvation
- VLAN hopping
- MAC flood
- UDP flood
- TCP SYN flood
- TCP session hijacking
- TCP reset
- Attacks to Web Applications
- Attacks to bypass authentication and authorization on behalf of a legitimate user (for example, password recovery, PSK, etc.)
- Attacks on vulnerabilities in network services, for example:
Most of these attacks (at least from 1 to 10) are based on the vulnerabilities of the architecture of modern Ethernet / IP networks, which consist of the ability of the Intruder to fake MAC packets and IP addresses in network packets. Operation of these vulnerabilities is sometimes distinguished as a separate type of attack:
Therefore, the construction of the DMZ protection system will begin with consideration of the methods of protection against IP and MAC spoofing.
Note
The following methods of protection against these attacks are not the only possible ones. There are other ways.
MAC spoofing protection
Schematically, the attacks associated with the substitution of MAC addresses can be illustrated as follows:
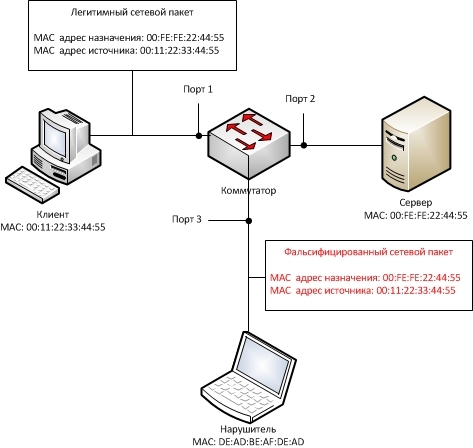
The neutralization of this attack can be the filtering of MAC addresses on the switch ports. For example, traffic on port 3 should only be passed if the DE: AD: BE: AF: DE: AD MAC address is specified in the source or destination address (in some cases).
IP spoofing protection
The IP spoofing attack scheme is similar to the previous one, except that the Intruder does not fake a MAC, but an IP address. IP spoofing protection can be implemented by splitting the DMZ IP network into smaller IP subnetworks and further filtering traffic on the router interfaces, by analogy with the previously considered MAC filtering. Below is an example of a DMZ design implementing this principle:
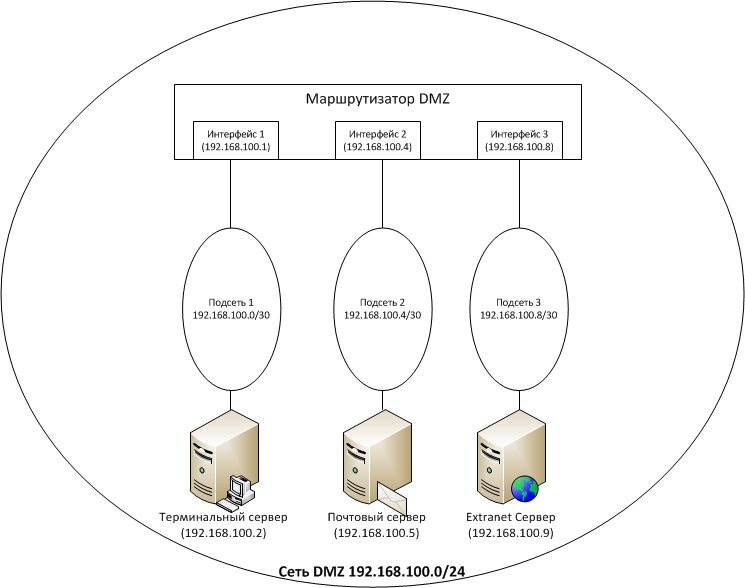
There are 3 nodes in the DMZ:
- Terminal Server (192.168.100.2)
- Mail Server (192.168.100.5)
- Extranet server (192.168.100.9)
For the DMZ, the IP network 192.168.100.0/24 is allocated, in this network there are 3 IP subnets (by the number of servers):
Subnet 1 - 192.168.100.0/30 for the terminal server (192.168.100.2)
Subnet 2 - 192.168.100.4/30 for the mail server (192.168.100.5)
Subnet 3 - 192.168.100.8/30 for the mail server (192.168.100.9)
In practice, network separation into similar subnets is implemented using VLAN technology. However, its use generates risks, protection from which we now consider.
VLAN hopping protection
To protect against this attack, the switch disables the ability to automatically negotiate the types ( trunk / access ) of the ports, and the administrator assigns the types manually. In addition, organizational measures prohibit the use of the so-called native VLAN .
Protection against attacks related to DHCP
Despite the fact that DHCP is designed to automate the configuration of IP addresses of workstations, in some companies there are cases when IP addresses for servers are issued via DHCP, but this is a pretty bad practice. Therefore, to protect against the Rogue DHCP Server , DHCP starvation, it is recommended that you completely refuse DHCP in the DMZ.
Protection against MAC flood attacks
To protect against MAC flood, the switch ports are configured to limit the maximum intensity of broadcast traffic (since usually these attacks generate broadcast traffic (broadcast)). Attacks related to the use of specific (unicast) network addresses will be blocked by MAC filtering, which we discussed earlier.
Protection against attacks UDP flood
Protection against this type of attack is similar to protection against MAC flood, except that filtering is performed at the IP (L3) level.
Protection against attacks TCP SYN flood
To protect against this attack are possible options:
- Protection on the network using TCP SYN Cookie technology.
- Protection at the firewall level (provided that the DMZ is divided into subnets) by limiting the traffic intensity containing TCP SYN requests.
Protection against attacks on network services and web applications
There is no universal solution to this problem, but the established practice is the introduction of software vulnerability management processes (detection, installation of patches, etc., for example ), as well as the use of intrusion detection and prevention systems (IDS / IPS).
Protection against bypassing authentication tools
As for the previous case, there is no universal solution to this problem.
Usually in case of a large number of unsuccessful authorization attempts, accounts are blocked in order to avoid selection of authentication data (for example, a password). But this approach is quite controversial, and here's why.
First, the intruder can carry out the selection of authentication information with an intensity that does not lead to account lockout (there are cases when a password was selected for several months with an interval between attempts of several tens of minutes).
Secondly, this feature can be used for denial of service attacks, in which the intruder will deliberately conduct a large number of authorization attempts in order to block accounts.
The most effective option from attacks of this class would be the use of IDS / IPS systems, which, when detecting password attempts, will block not the account, but the source from which this selection occurs (for example, block the IP address of the Offender).
The final list of protective measures for this option:
- The DMZ is divided into IP subnets on the basis of a separate subnet for each node.
- IP addresses are assigned manually by administrators. DHCP is not used.
- On the network interfaces to which the DMZ nodes are connected, MAC and IP filtering, restrictions on the intensity of broadcast traffic and traffic containing TCP SYN requests are activated.
- The switches disable auto negotiation of port types, prohibit the use of a native VLAN.
- On the DMZ nodes and internal network servers to which these nodes are connected, the TCP SYN Cookie is configured.
- With respect to the DMZ nodes (and preferably the rest of the network), software vulnerability management is being implemented.
- In the DMZ segment, IDS / IPS intrusion detection and prevention systems are being implemented.
Advantages of the option:
- High security.
Disadvantages option:
- Increased requirements for the functionality of the equipment.
- Man-hours implementation and support.
Analogy with real life
If earlier we compared the DMZ with a client zone equipped with sofas and ottomans, then the protected DMZ will look more like an armored cashier.

© valmax.com.ua
Option 5. Back connect
The protection measures considered in the previous version were based on the presence of a device (switch / router / firewall) on the network capable of implementing them. But in practice, for example, when using a virtual infrastructure (virtual switches often have very limited capabilities), such a device may not exist.
Under these conditions, many of the previously considered attacks become accessible to the offender, the most dangerous of which will be:
- attacks that allow to intercept and modify traffic (ARP Poisoning, CAM table overflow + TCP session hijacking, etc.);
- attacks related to the exploitation of vulnerabilities of internal network servers to which you can initiate connections from the DMZ (which is possible by circumventing the DFW filtering rules due to IP and MAC spoofing).
The next important feature that we have not previously considered, but which does not cease to be this less important, is that automated workstations (AWP) of users can also be a source (for example, when infected with viruses or Trojans) of harmful effects on the server.
Thus, we are faced with the task of protecting the intranet servers from intruder attacks from both the DMZ and the intranet (an ARM Trojan infection can be interpreted as an Intruder’s actions from the intranet).
The approach proposed further is aimed at reducing the number of channels through which the Intruder can attack servers, and there are at least two such channels. The first is a rule on DFW that allows access to the internal network server from the DMZ (even if it is restricted by IP addresses), and the second is the network port open on the server that requests for connection requests are expected.
You can close the specified channels if the internal network server itself builds connections to the server in the DMZ and will do this using cryptographically secure network protocols. Then there will be no open port, no rules on the DFW .
But the problem is that ordinary server services cannot work in this way, and for the implementation of this approach it is necessary to apply network tunneling implemented, for example, using SSH or VPN, and within the tunnels to allow connections from the server in the DMZ to the internal network server .
The general scheme of this option is as follows:
- An SSH / VPN server is installed on the server in the DMZ, and an SSH / VPN client is installed on the server on the internal network.
- The internal network server initiates the building of a network tunnel to the server in the DMZ. The tunnel is built with mutual authentication of the client and server.
- The server from the DMZ within the built tunnel initiates a connection to the server on the internal network, through which the protected data is transmitted.
- On the internal network server, a local firewall is configured to filter traffic passing through the tunnel.
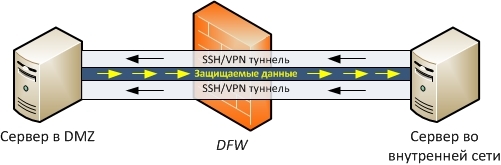
The use of this option in practice has shown that it is convenient to build network tunnels using OpenVPN , since it has the following important properties:
- Cross platform You can organize communication on servers with different operating systems.
- The ability to build tunnels with mutual authentication of the client and server.
- The possibility of using certified cryptography .
At first glance it may seem that this scheme is unnecessarily complicated and that, since the local network server still needs to install a local firewall, it is easier to make the server from the DMZ, as usual, connect to the internal network server itself, but encrypted connection. Indeed, this option will close many problems, but it will not be able to provide the main thing - protection against attacks on server vulnerabilities of the internal network, accomplished by circumventing the firewall using IP and MAC spoofing.
Advantages of the option:
- Architectural reduction of the number of attack vectors on the protected server of the internal network.
- Ensuring security in the absence of filtering network traffic.
- Protection of data transmitted over the network from unauthorized viewing and modification.
- The possibility of selectively increasing the level of security services.
- The possibility of implementing a two-circuit protection system, where the first circuit is provided using firewalling, and the second is organized on the basis of this option.
Disadvantages option:
- The implementation and maintenance of this protection option requires additional labor costs.
- Incompatibility with network intrusion detection and prevention systems (IDS / IPS).
- Additional computational load on the server.
Analogy with real life
The main point of this option is that the trustee establishes a connection with the non-trusted, which is similar to the situation when, when issuing loans, the Banks themselves call the potential borrower to verify the data.

© comfoson.890m.com
Conclusion
So, we have considered all five declared options for organizing access to corporate network services from the Internet. Which one is better, which is worse, is difficult to say, since everything depends, ultimately, on the information that needs to be protected and the resources that the company has for protection. If there are no resources, no knowledge, then the first option will be optimal. If the information is very valuable, then a combination of the fourth and fifth options will provide an unsurpassed level of security.
Source: https://habr.com/ru/post/302068/
All Articles