Mobile Device Management with Microsoft Intune
Want to allow employees to use a personal laptop, tablet, phone as a worker - easily! But how to protect, separate personal information from the working? But what about the applications? Need to configure all devices according to company policies? And if someone loses their device with important working information?
Let's find out the answers to these and other questions.
Employees can use their personal devices at work for personal purposes if company policies allow it. So why not let them use a personal device for work tasks?
')
“Take Your Own Device to Work” - this is how the BYOD (Bring Your Own Device) concept sounds. The BYOD trend removes the boundaries between private life and work. For IT professionals, it is better to control the situation rather than deal with it with administrative means. The permission to use their own devices is also a tool to increase employee loyalty, which is important for any company.
The desire of employees to work remotely obvious. There are a lot of specialists who not only want, but can also work remotely. For this you need to have a certain level of self-control, but this is quite realistic.
However, despite the undeniable advantages, the introduction of BYOD is associated with security and manageability issues. There is a possibility of loss, theft of the device, infection with malware. But if you look at it, the business benefits of BYOD outweigh the disadvantages.
Today there are a lot of large and small companies on the market that provide MDM (Mobile Device Management) service.
Many who tried to create, promote their decision, but not all "survived."
Let's go to Intune. There is a lot of theoretical information, reviews about Intune from Microsoft. In short, this is a cloud service for managing mobile devices based on Windows, iOS, Android, as well as computers running Windows.
There are several configurations using Intune. I identified two main ones:
This article will look at mobile device management for a small business with a stand-alone configuration.
The advantages of this solution include the following: the need for deployment, maintenance and scalability disappears, because The solution is cloudy, Microsoft regularly updates and improves it.
Also simplified subscription scheme based on the number of users and not devices. For one user will have to pay $ 6.00 USD per month. The subscription includes 20 GB of space in the cloud for applications.
But do not rush to purchase a subscription. There are 30 days of the trial period for 100 users, after which you can extend the trial period for another 30 days by specifying the payment card number. Total 60 days to try and understand if you need Intune.
So you decided to try. After registration, the Intune control panel and the central administration will be available. Next, the administrator creates users manually in the control panel or imports from a CSV file in the admin center. Sample CSV file . Each created user will have a login in the form of UserName @ CompanyName .onmicrosoft.com or its own domain name.
The whole management process can be divided into 5 basic steps:

To register, you must install the Company Portal application on the user's device.
To make it easier for administrators to communicate with users, Microsoft provides a list of links , this information will help them when registering devices with Intune and performing various tasks on devices after registration.
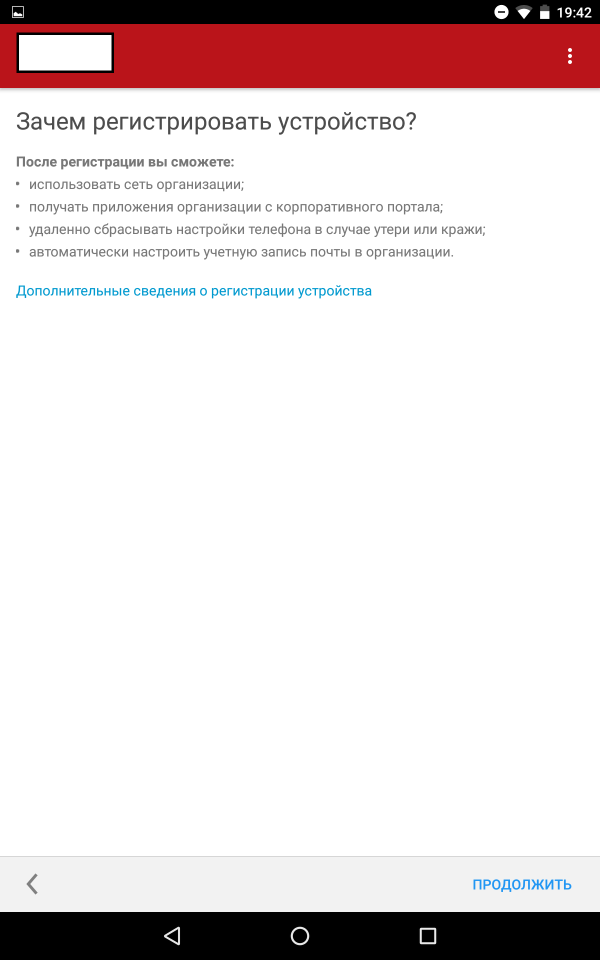
After the user has installed the application and logged in, his device will be registered.
The application "Company Portal" contains three main tabs:
After the device is registered, it can be controlled.
All registered devices and users are added to the corresponding branches in the control panel of the “Groups” tab.
The administrator can group devices (device group) and users (user group) by the available criteria or directly assign group membership for further distribution of their management, similar to collections in SCCM 2012.
Intune supports the installation of many different applications, including applications from the application store, web applications and applications developed internally.
There are two types of application installation:
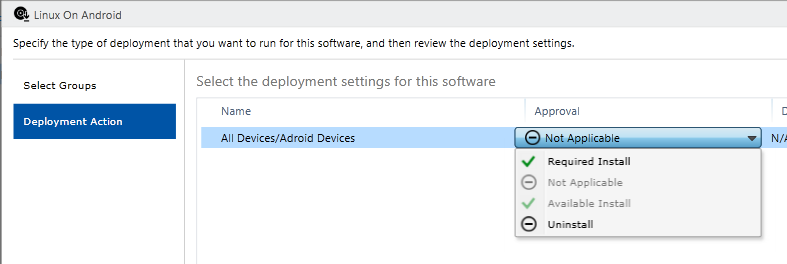
After the application is added and available in the list of applications, it remains only to deploy it on users' devices. Selecting in the context menu “Manage Deployment ...” we assign the application to a user group or device group.

The following options are available:
The application assigned to the corresponding group will appear on the user device.
Intune uses policies that will help configure many settings and modes of operation for devices:
Naturally, the list of available parameters in different OSs is different, even at the level of the same OS, different options are available in different versions, and the administrator will not have a sweetness if the users have too wide variation of operating system versions. But when creating a configuration, prompts are available, with minimum OS version requirements.
Although Intune provides a wide range of options for configuring devices, a situation may arise when the required parameter is not available. In many cases, this problem can be solved with a custom policy that allows you to configure OMA-URI settings — this is a common standard for configuring mobile devices to set the required values.
Settings are deployed in the same way as applications are deployed.
After deploying applications and policies, the administrator monitors the status on the respective tabs.
The administrator will be notified of problems in Intune using an alert.
Alerts let you track what's happening in Microsoft Intune. For example, a malicious program was detected on the computer or a conflict between two Intune policies was detected.
On the tab with the devices there is a very useful list of filters with which you can find devices with different status.
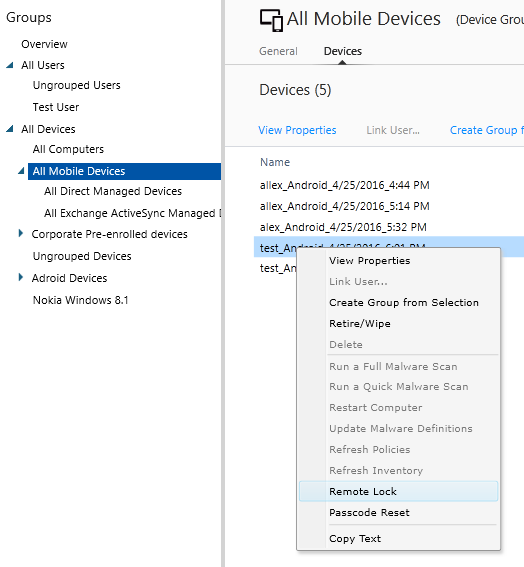
In case of loss by the employee of the mobile device or its theft, you can delete corporate data and applications from the device, you can also perform a full cleaning. If necessary, you can reset the secret code or remotely lock the device.
Everything is quite simple: we find the name of the user, select the necessary one from his devices, and in the context menu choose the necessary action:
As a conclusion, I would like to mention the maturity of the product, because some more years ago Intune was damp for corporate use. Today it is one of the few stable solutions with full support and updates. In addition, it integrates with SCCM, which is important for large corporations.
List of useful resources
https://docs.microsoft.com/en-us/intune/
https://blogs.technet.microsoft.com/microsoftintune/
Let's find out the answers to these and other questions.
Employees can use their personal devices at work for personal purposes if company policies allow it. So why not let them use a personal device for work tasks?
')
“Take Your Own Device to Work” - this is how the BYOD (Bring Your Own Device) concept sounds. The BYOD trend removes the boundaries between private life and work. For IT professionals, it is better to control the situation rather than deal with it with administrative means. The permission to use their own devices is also a tool to increase employee loyalty, which is important for any company.
The desire of employees to work remotely obvious. There are a lot of specialists who not only want, but can also work remotely. For this you need to have a certain level of self-control, but this is quite realistic.
However, despite the undeniable advantages, the introduction of BYOD is associated with security and manageability issues. There is a possibility of loss, theft of the device, infection with malware. But if you look at it, the business benefits of BYOD outweigh the disadvantages.
Today there are a lot of large and small companies on the market that provide MDM (Mobile Device Management) service.
List of existing solutions
Microsoft Intune
AirWatch by VMWare
Citrix xenmobile
BlackBerry Enterprise Service
SAP Afaria
Symantec Mobile Management
Good technology
MaaS360 by Fiberlink
Dell Mobile Management
MobileIron
Centrify
Filewave
LANDESK
MobiControl
Sophos mobile control
Excitor MobiControl
Amtel
Tangoe Matrix Mobility
Kaseya BYOD
Absolute manage
BoxTone
SOTI
FAMOC
AirWatch by VMWare
Citrix xenmobile
BlackBerry Enterprise Service
SAP Afaria
Symantec Mobile Management
Good technology
MaaS360 by Fiberlink
Dell Mobile Management
MobileIron
Centrify
Filewave
LANDESK
MobiControl
Sophos mobile control
Excitor MobiControl
Amtel
Tangoe Matrix Mobility
Kaseya BYOD
Absolute manage
BoxTone
SOTI
FAMOC
Many who tried to create, promote their decision, but not all "survived."
Let's go to Intune. There is a lot of theoretical information, reviews about Intune from Microsoft. In short, this is a cloud service for managing mobile devices based on Windows, iOS, Android, as well as computers running Windows.
There are several configurations using Intune. I identified two main ones:
- Autonomous - Intune
- Hybrid - Intune + SCCM 2012 or Intune + SCCM 2012 + Azure
This article will look at mobile device management for a small business with a stand-alone configuration.
The advantages of this solution include the following: the need for deployment, maintenance and scalability disappears, because The solution is cloudy, Microsoft regularly updates and improves it.
Also simplified subscription scheme based on the number of users and not devices. For one user will have to pay $ 6.00 USD per month. The subscription includes 20 GB of space in the cloud for applications.
But do not rush to purchase a subscription. There are 30 days of the trial period for 100 users, after which you can extend the trial period for another 30 days by specifying the payment card number. Total 60 days to try and understand if you need Intune.
So you decided to try. After registration, the Intune control panel and the central administration will be available. Next, the administrator creates users manually in the control panel or imports from a CSV file in the admin center. Sample CSV file . Each created user will have a login in the form of UserName @ CompanyName .onmicrosoft.com or its own domain name.
The whole management process can be divided into 5 basic steps:

check in
To register, you must install the Company Portal application on the user's device.
Links to the application
To make it easier for administrators to communicate with users, Microsoft provides a list of links , this information will help them when registering devices with Intune and performing various tasks on devices after registration.
After the user has installed the application and logged in, his device will be registered.
Screenshots of registration steps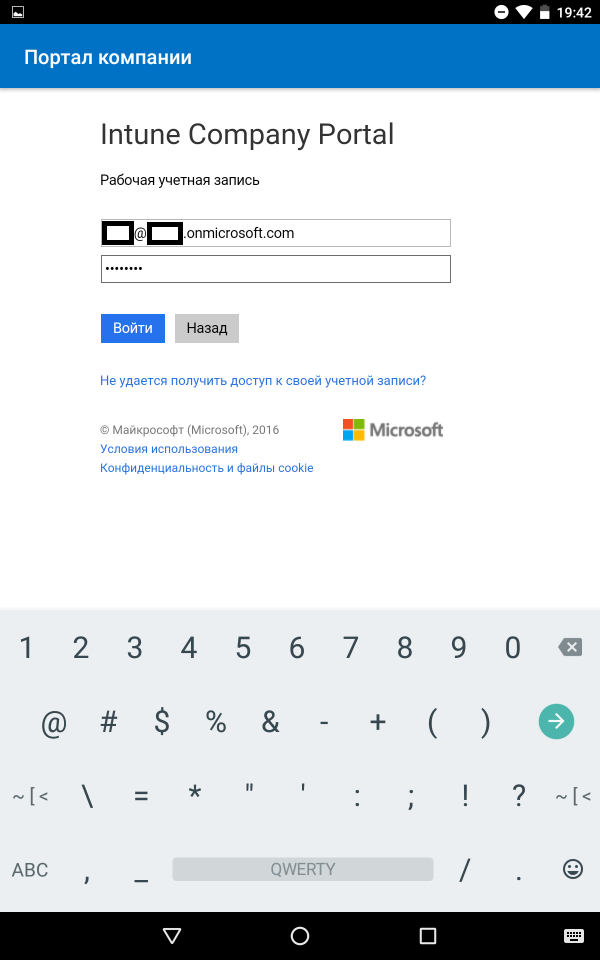
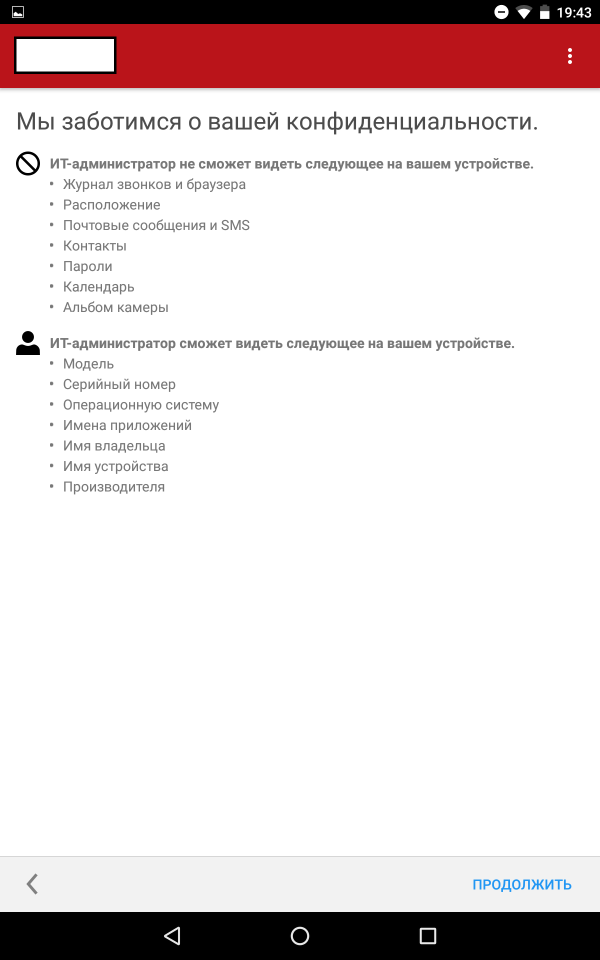
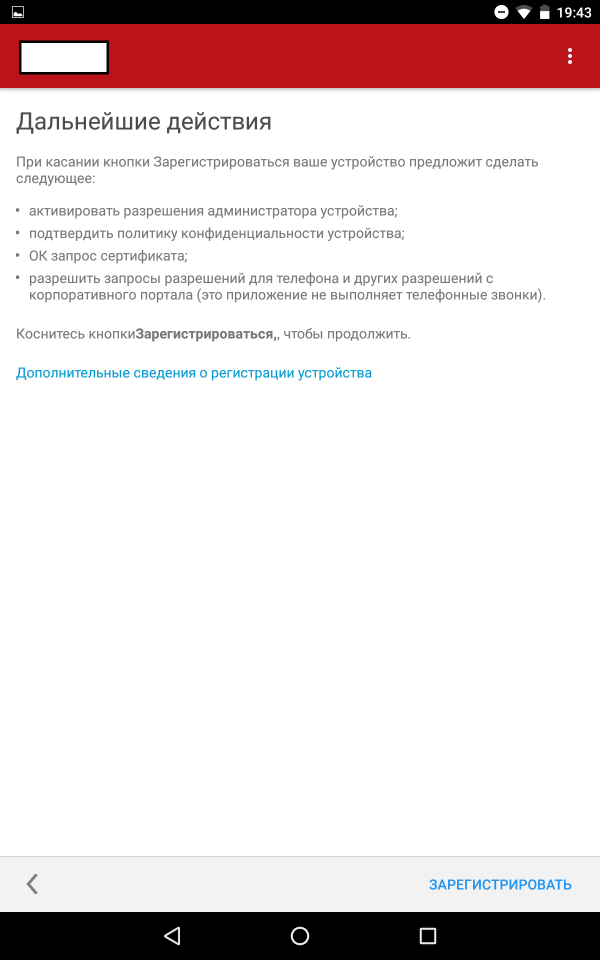
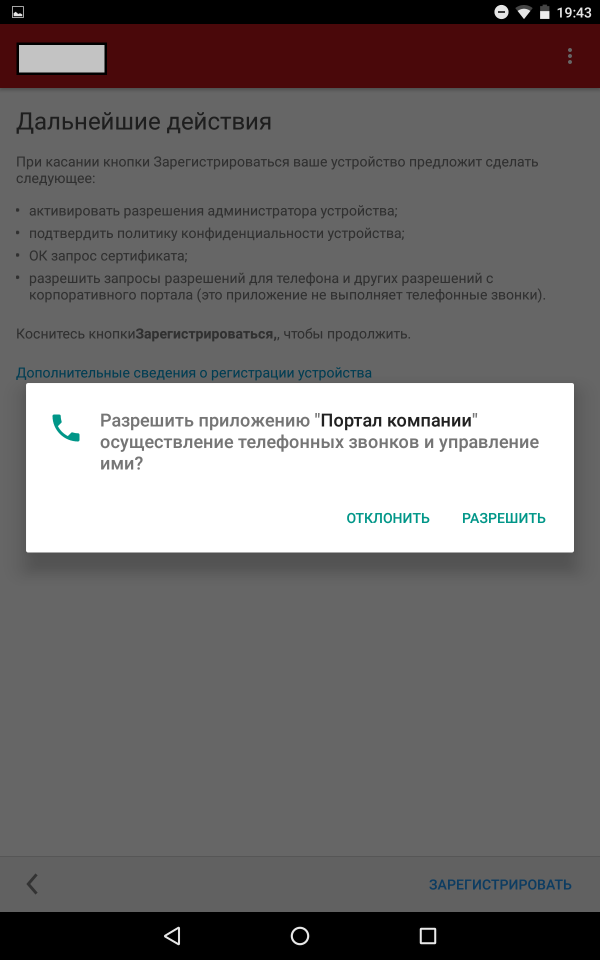
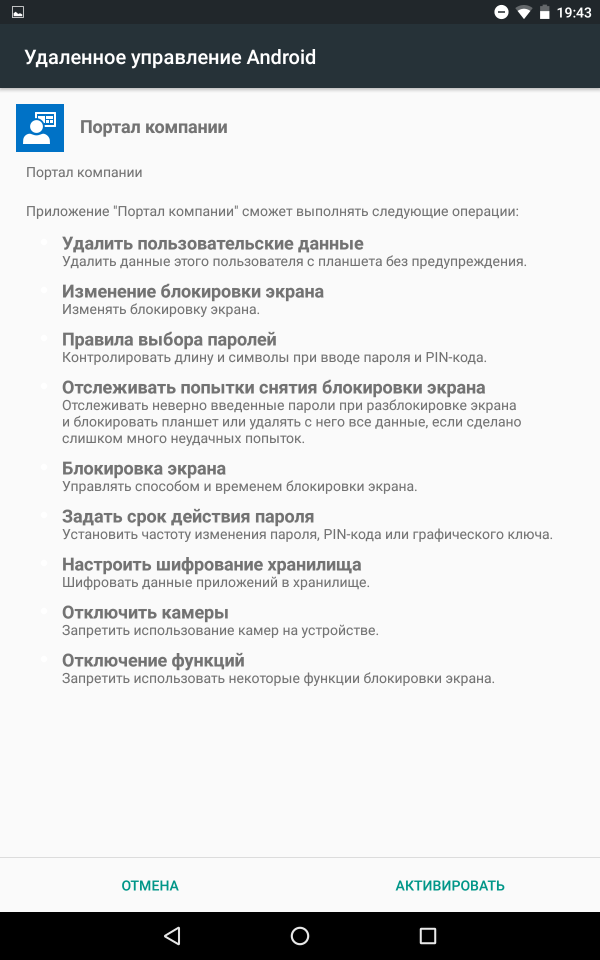
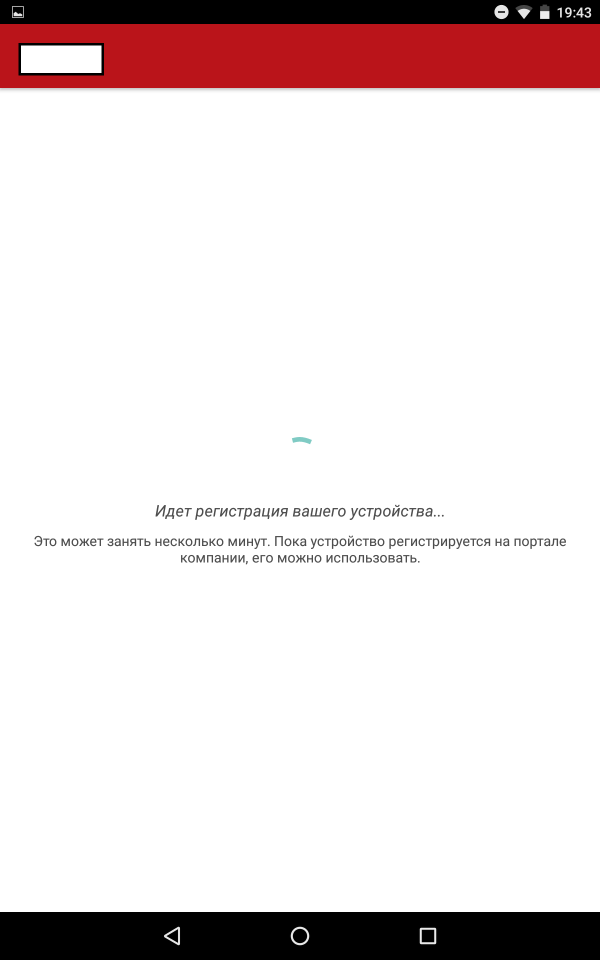

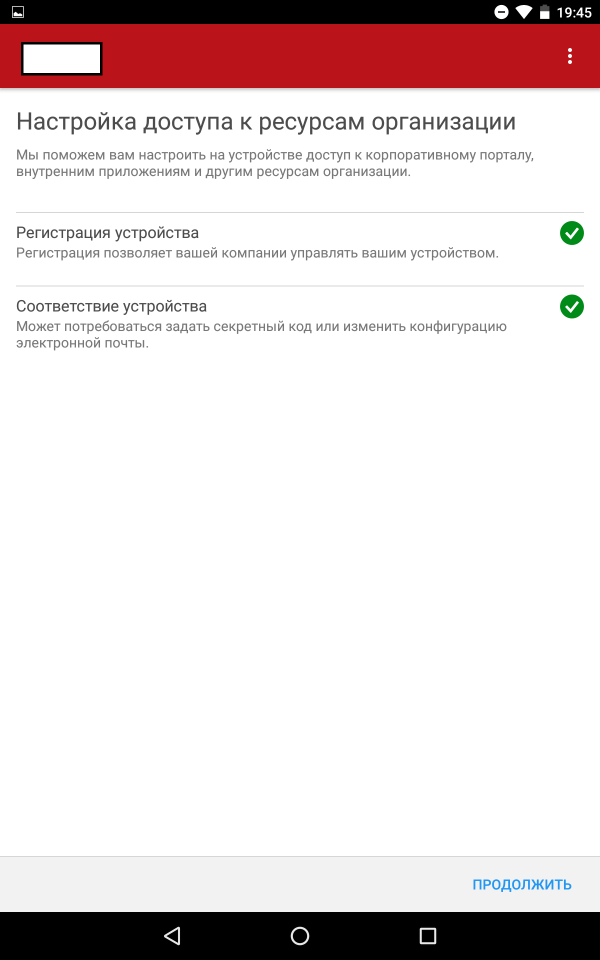
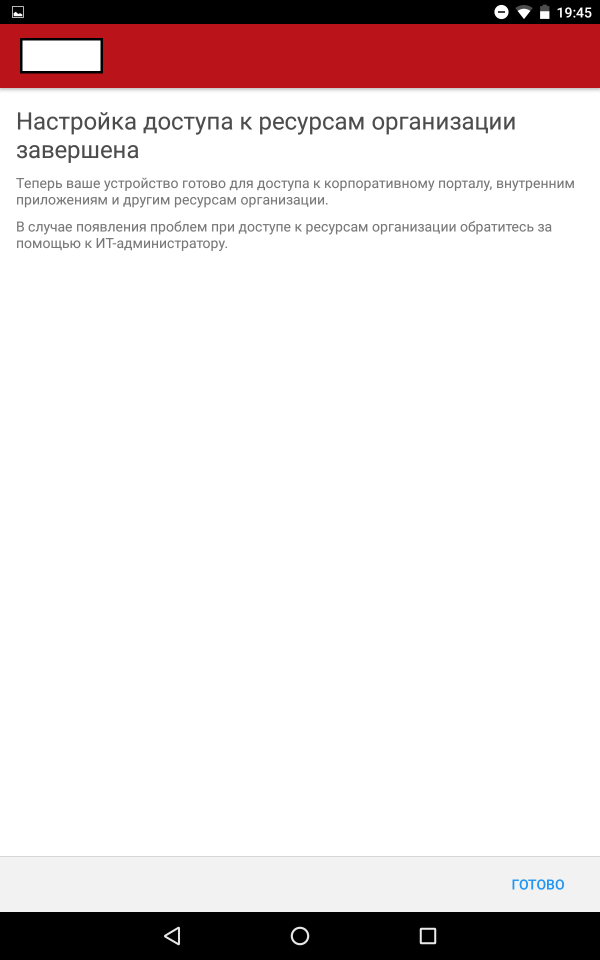










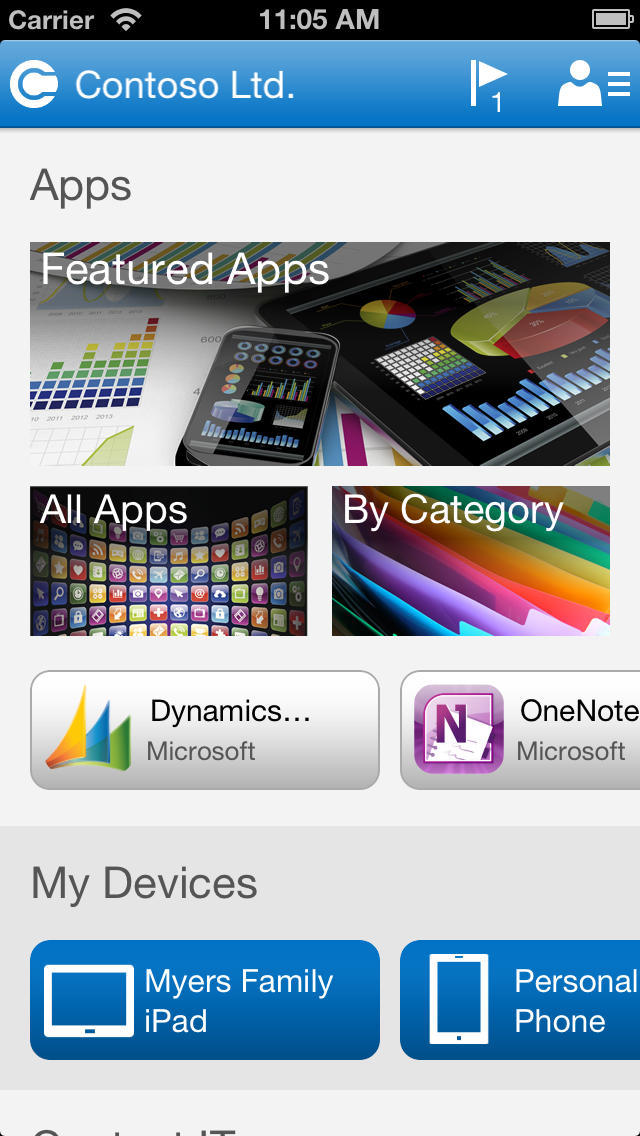
The application "Company Portal" contains three main tabs:
- Applications - list of all applications available to the user.
- My Devices - a list of user devices (maximum 5)
- Contact the IT department contact information for communication with the IT department
After the device is registered, it can be controlled.
All registered devices and users are added to the corresponding branches in the control panel of the “Groups” tab.
The administrator can group devices (device group) and users (user group) by the available criteria or directly assign group membership for further distribution of their management, similar to collections in SCCM 2012.
Deploying Applications
Intune supports the installation of many different applications, including applications from the application store, web applications and applications developed internally.
There are two types of application installation:
- Installer - specify the installation file for the application you want to deploy. For example, APK for Android
- External link - specify the link to the application page in the application store. For example, Microsoft Store for Windows Mobile
Add Application - Installer
Select the installation file:
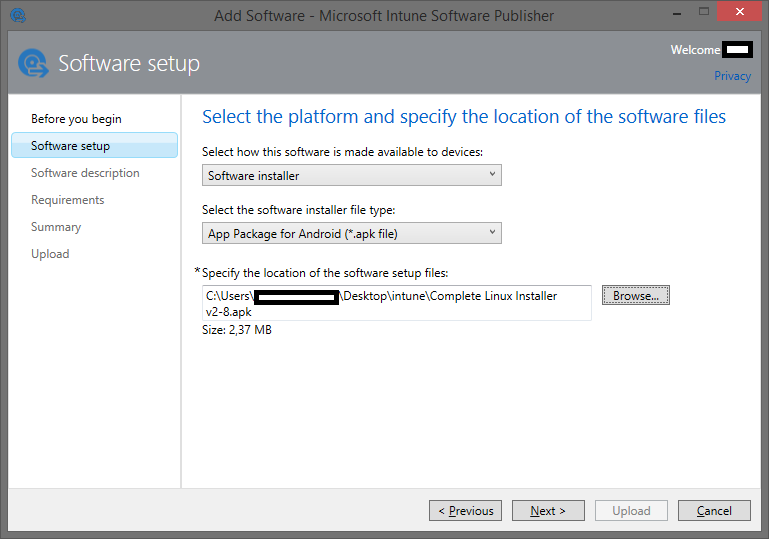
Fill in the description:
Set the requirements for the operating system version:

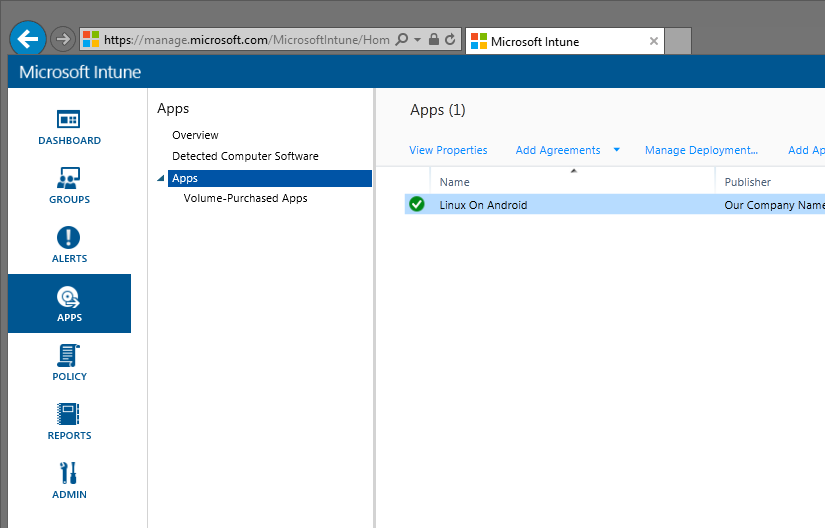
The application has been added to the list of applications in the control panel:

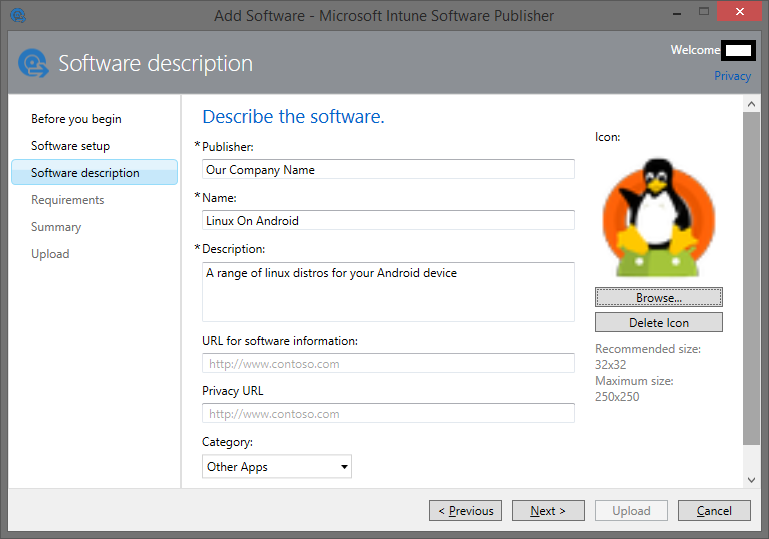
Fill in the description:

Set the requirements for the operating system version:

The application has been added to the list of applications in the control panel:

Adding an application - external link
Specify the link to the application in the market:
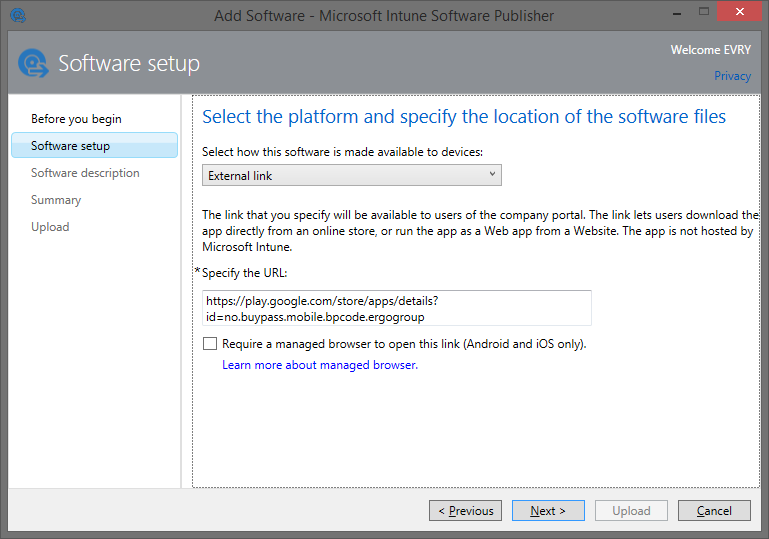
Fill in the description:
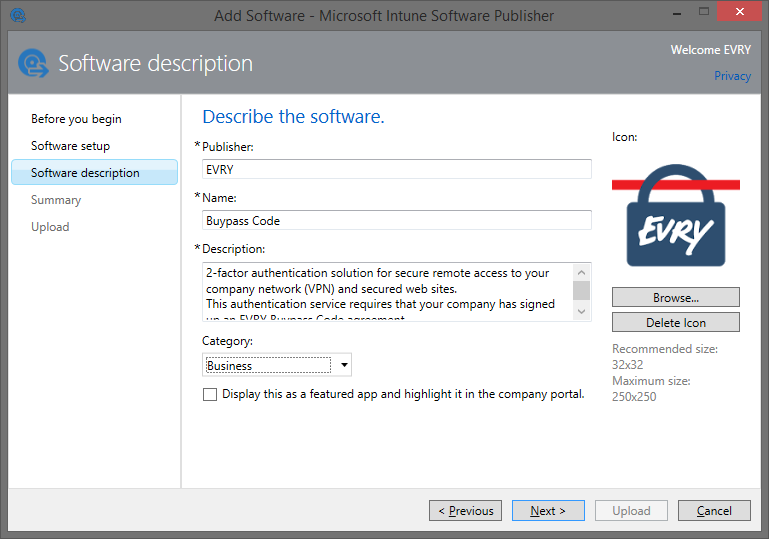

Fill in the description:

After the application is added and available in the list of applications, it remains only to deploy it on users' devices. Selecting in the context menu “Manage Deployment ...” we assign the application to a user group or device group.

The following options are available:
- Forced installation
- Available installation
- Deletion

The application assigned to the corresponding group will appear on the user device.
Display example on different devices
Android:

Windows Mobile:
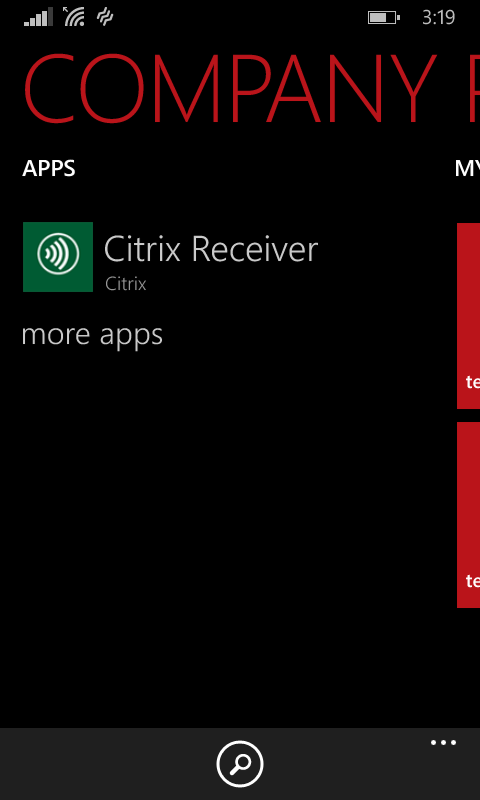
Windows 10
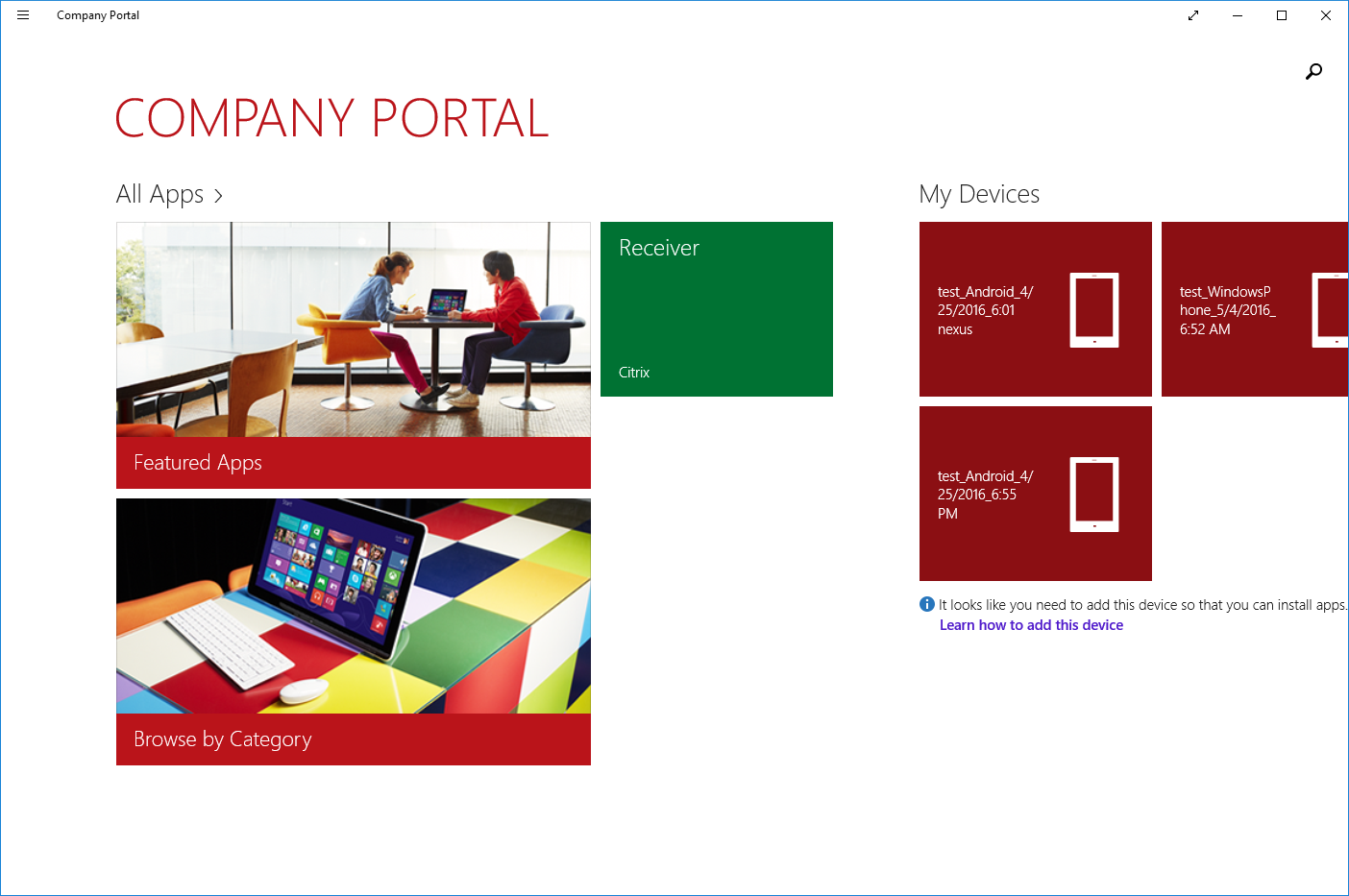
iOS:

Windows Mobile:

Windows 10

iOS:

Customization
Intune uses policies that will help configure many settings and modes of operation for devices:
- Equipment options, such as permission to use Bluetooth, NFC, ...
- Password options, including password length and quality
- Encryption options
- Browser settings, such as ban on saving cookies, jscript blocking
- Allowed and Denied Applications
- Compliance policies, such as OS version
Naturally, the list of available parameters in different OSs is different, even at the level of the same OS, different options are available in different versions, and the administrator will not have a sweetness if the users have too wide variation of operating system versions. But when creating a configuration, prompts are available, with minimum OS version requirements.
For example, a policy prohibiting the use of the camera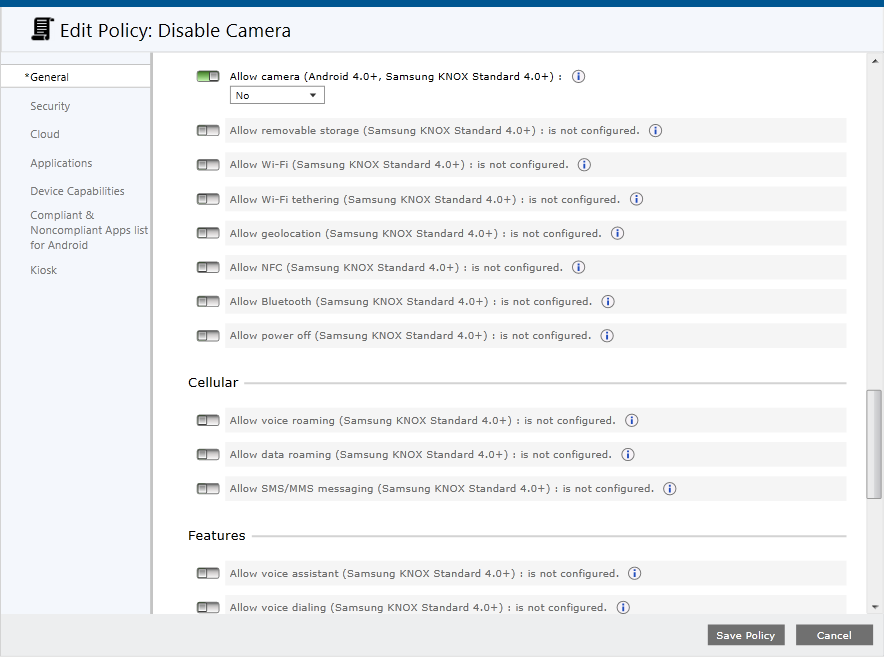
When starting the camera, the user will be notified:
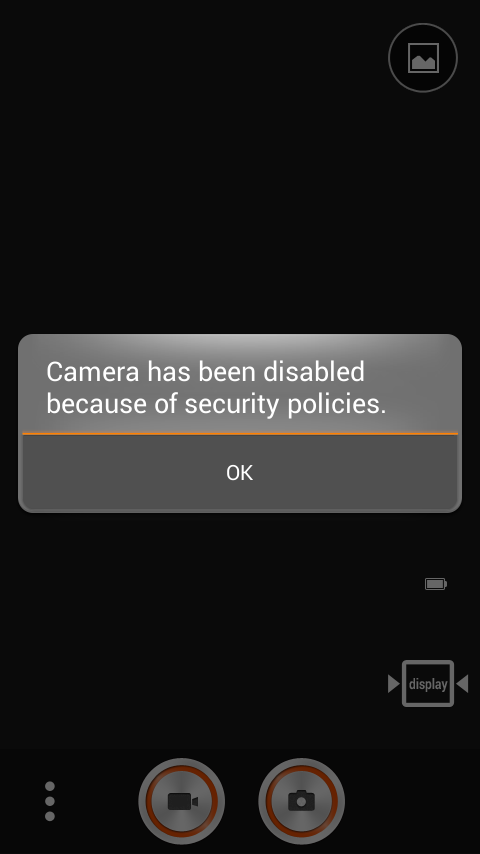

When starting the camera, the user will be notified:

Although Intune provides a wide range of options for configuring devices, a situation may arise when the required parameter is not available. In many cases, this problem can be solved with a custom policy that allows you to configure OMA-URI settings — this is a common standard for configuring mobile devices to set the required values.
Settings are deployed in the same way as applications are deployed.
Monitoring
After deploying applications and policies, the administrator monitors the status on the respective tabs.
The tab "Dashboard" displays the overall status of all components.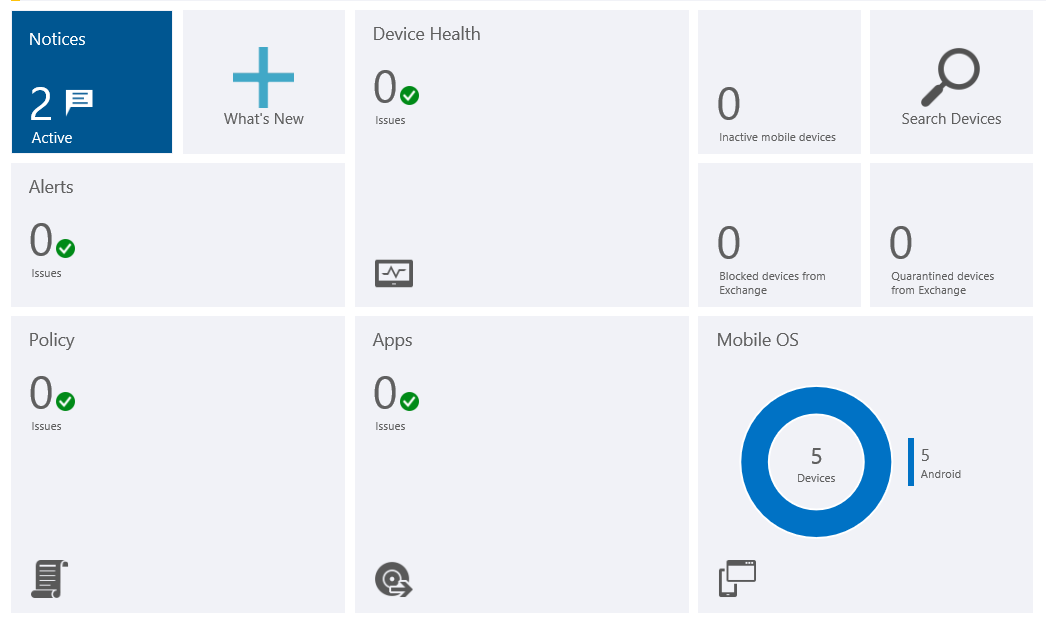

More detailed information on the status of applications is displayed in the '' APPS '' tab.
Clicking on the application we will see the details:
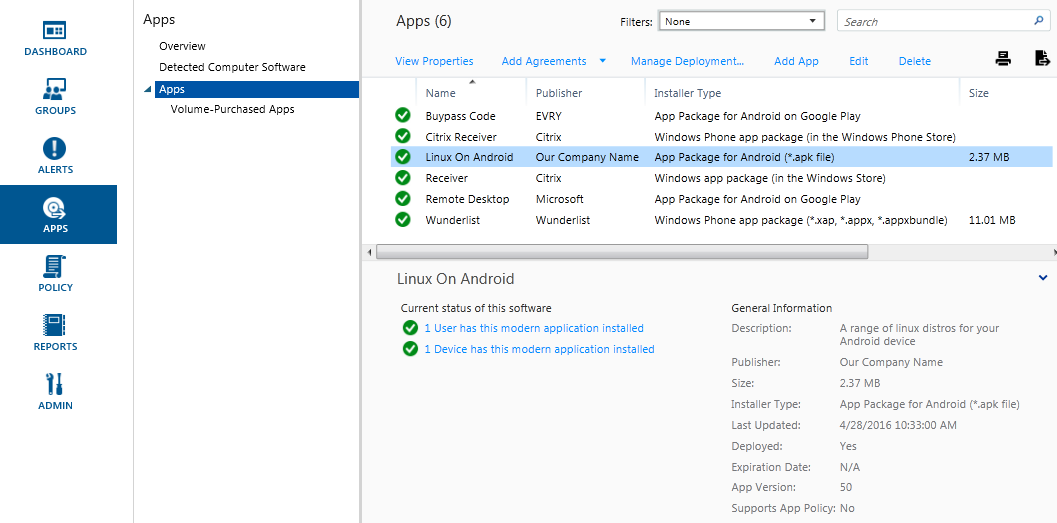

The administrator will be notified of problems in Intune using an alert.
Alerts let you track what's happening in Microsoft Intune. For example, a malicious program was detected on the computer or a conflict between two Intune policies was detected.
On the tab with the devices there is a very useful list of filters with which you can find devices with different status.
Filter list

Protection
In case of loss by the employee of the mobile device or its theft, you can delete corporate data and applications from the device, you can also perform a full cleaning. If necessary, you can reset the secret code or remotely lock the device.
Everything is quite simple: we find the name of the user, select the necessary one from his devices, and in the context menu choose the necessary action:

As a conclusion, I would like to mention the maturity of the product, because some more years ago Intune was damp for corporate use. Today it is one of the few stable solutions with full support and updates. In addition, it integrates with SCCM, which is important for large corporations.
List of useful resources
https://docs.microsoft.com/en-us/intune/
https://blogs.technet.microsoft.com/microsoftintune/
Source: https://habr.com/ru/post/301550/
All Articles