PHDays VI: hackers could not take the city entirely

4,200 people from around the world witnessed a lively and somewhat insane holiday called Positive Hack Days VI. In two days, hundreds of events took place on the site. At first glance, hackers felt like full masters of the situation. In fact - in the conditions of maximum protection, no one has advanced beyond the perimeter of the DMZ.
Perhaps in a few weeks or months the city would still have fallen. Such protection is not cracked by cavalry assault. But viewers could not watch the purposeful attack stretched in time. They wanted to see the village being heated and the power line wiring harness. To improve the entertainment, it was decided to slightly reduce the level of security by turning off some of the systems. And here everyone saw what insufficient attention to information security is. Hackers used any mistake: they successfully attacked GSM / SS7, disconnected the systems of the smart home, deleted backup copies of important systems, and deduced money from the RBS.
')
The forum clearly showed what happens with an unsecured critical infrastructure. Information security specialists are able to provide a very high level of protection without disrupting the process - but they very rarely turn around like at PHDays. After disabling the protective equipment, the attackers penetrated the technological network of the automated control system through the corporate network, attacked the physical equipment of the system, hacked the hydropower station, discharged water, and disconnected the power lines.
Anyway, it’s not possible to capture the city of CityF entirely - and to win the competition - not a single team of hackers. Detailed raitapes and the results of the competitions are expected very soon, and now we will tell about several performances of the second day (read the story about the best moments of the first day here ).
Rules of war
“At Positive Hack Days is an amazing audience. I was very impressed, ”said Jan Neutze, director of cybersecurity at Microsoft Europe, who came to Moscow to talk about the development of security standards in the field of international cyber conflict. It turns out that Microsoft has a formed position on the issue of "silent" wars, which, however, should not be surprising: the company's budget is comparable with the gross product of some countries. According to Neutze, cyber attacks cost businesses $ 3 trillion. The number of hacks last year grew by 78%, the data of 160 million users were stolen. The average time to detect hacking was 229 days.
According to Neutze, the governments of 16 countries have already declared the use of cyber attacks, and 45 have announced active cyber defense measures. About 100 countries are currently developing legislation for their cyberspace. “The main thing is a critical infrastructure,” said Neutze. - The legislation of each country should clearly state that special services and the military have no right to attack this sphere. This is a global catastrophe. ”
Attacks on corporate email increased by 270%
At the section “Technologies of Protection and Attacks - 2016: who will make a breakthrough,” the leading experts of Positive Technologies Expert Security Center told about the latest significant developments in the field of protection and attack.
Dmitry Sklyarov shared news from the world of reverse engineering. Among other things, he spoke about the found vulnerabilities in the Secret Net Studio information protection system. Its operation allows attackers to elevate their privileges from guest access to the administrator. Sklyarov noted that at the moment there are no serious studies of certified products, therefore it is necessary to encourage manufacturers to donate software for testing to independent researchers and not to be limited to FSTEC certification only.
Dmitry Kurbatov believes that you should not rely on mobile communications. He presented the results of studies of the security of SS7 networks, conducted in 2015 by Positive Technologies. Statistics are disappointing: every mobile network is vulnerable. In 89% of cases, it is possible to intercept an incoming SMS message, in 58% of cases - to determine the location of the subscriber, and in 50% - to listen to calls. So, intercepting incoming SMS messages can be used to gain access to the messenger account and e-wallet.
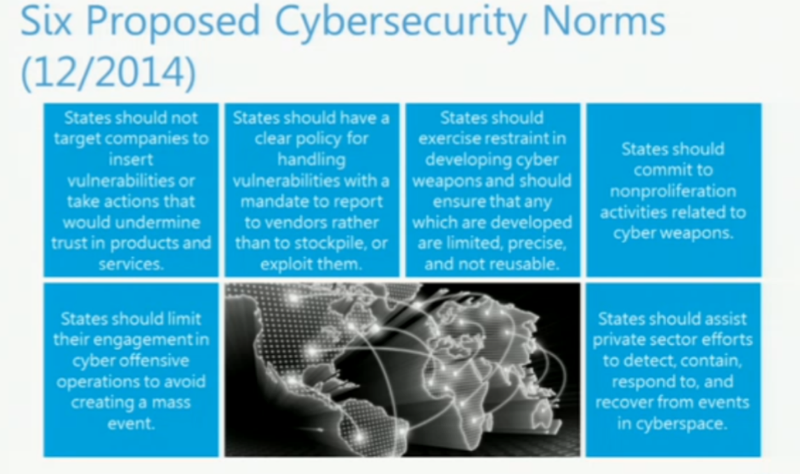
One of the trends of the last year was attacks with the compromise of corporate mail. According to the FBI, their number increased by 270%. On average, the damage from the attack on the victim is 25-75 thousand dollars. Positive Technologies has also been subjected to such an attack. The details of the incident told Vladimir Kropotov.
“Banks should regularly analyze the security of their mobile applications,” Artem Chaykin believes. “Many mobile banking applications do not correctly work with the data they receive.” He told the audience about the evolution of malware and the nuances of the mechanisms for protecting users of banking applications.
Heartbleed, Shellshock, Ghost, Badlock is an incomplete list of vulnerabilities that have become a brand. Not only developers interested in the attention of the press. There was a kind of trend, when researchers come up with a whole PR campaign to talk about the vulnerabilities found. But which of them are really critically dangerous, and about which you can say "much ado about nothing"? Arseny Reutov understood this question.
“Your data can be leaked almost for free if you use vulnerable software,” Yulia Voronova is sure. According to the expert, attackers rarely attack a specific customer, mostly they are repelled by product vulnerabilities. Hackers find vulnerabilities, exploit, and only then search for users of vulnerable products and attack them. “But not everything is as bad as before. The defense ceases to be catching up and becomes advancing, ”summed up Julia.
SIEM or not SIEM, that is the question

Alexey Lukatsky gathered representatives of leading developers of SIEM systems in order to understand the purpose of this class of products. Questions were posed as tough as possible. Does SIEM really benefit or is it just another “pull-out” of money from customers? And the difference between their products. The section brought together Evgeny Afonin (HP ArcSight), Olesya Shelestova (founder of RUSIEM), Vladimir Bengin (MaxPatrol SIEM), Vladimir Skakunov (Splunk), Roman Andreev (IBM QRadar).
Alexey Lukatsky cited the survey data for 2014, which was held among 800 companies from around the world in 30 industries that implemented SIEM. 74% of companies answered that SIEM had no effect on the level of security: the number of incidents did not decrease. “Customers often expect that SIEM will work like a silver bullet, that, once installed, the system will catch something for them,” Roman Andreev commented on the survey results. “It is possible that three quarters of respondents simply did not have an understanding of what they should catch.” The audience noted that the task of the SIEM is to identify incidents and investigate them, and not to influence the number of dangerous events. Yevgeny Shumsky from IBM offered to come to terms with these figures as the inevitable evil caused by the increased complexity of products of this class: “The SIEM systems are so diverse that each customer uses them in his own way. They are used as antifraud – systems, security service KPIs are calculated, and the detection of incidents is automated. For some companies, SIEM is simply a need to go to the dashboard once a month and see what happened on the router. ”
“I do not agree with the survey figures,” said Vladimir Bengin (Positive Technologies). - The situation is even worse. Over the past six months, we have implemented 15 MaxPatrol SIEM projects, conducted dozens of pilot projects, and, otherwise, communicated with hundreds of customers. And it should be noted that almost all SIEM already have. However, in the literal sense of the word "lies on the shelf": according to our statistics, one out of ten SIEM-systems works effectively, as manufacturers of systems of this class only sell functionality. Who has more ticks in the comparative table - he won. Their main mistake is that they do not sell the expertise. In practice, SIEM systems work only in those companies (and there are few of them) where a department of a dozen security specialists is formed. We do not like this approach - it just does not work. Therefore, Positive Technologies has taken a different path, making a system capable of working practically out of the box. In our paradigm, SIEM is just one of the building blocks of the future platform. ”
Criminals can be calculated by domain
Information Security Threat Analyst Fidelis Cybersecurity John Bambenek spoke at the forum on “Identifying security incidents by exploiting the resiliency properties of the attacker's infrastructure.” He gave examples of techniques that attackers use, spoke about the algorithms for generating domain names. There are such patterns when malefactors register a large number of domains or services again and again. In the context of the investigation, knowing the patterns of their behavior, you can track the criminal until he makes a mistake. “A criminal must always be lucky. In the long run, this is difficult. The more they act, the greater the likelihood of error, ”says John. We touched on a similar topic in the Positive Technologies blog on Habré.
Andrei Masalovich about the poisoned drop
Of great interest was the report of Andrei Masalovich "The Survivor". He told how information attacks are being prepared. A whole arsenal of information tools is used in the “war for brains”. In particular, in the duo of the troll and the bot is now a new player - Fairy with a pipette. The traditional market lives on a three-dimensional explosion model. Artificial information bursts act on the analog of a two-dimensional wave: a drop falling on water gives circles, and if it falls into a good place, it gives a big wave. This is how the Fairy works with a pipette that drips a poisoned drop into the right place.
Perhaps the most intriguing part of the speech was the demonstration of examples of social portraits of participants in mass discussions - politicians, media people, ordinary users, recruiters and their victims. Looking at these cards, you will involuntarily shudder: even if a person does not disclose information about himself in his account, you can still calculate it just by studying the second circle of his friends. Naturally, a similar method of express analysis of a social portrait is also used for security purposes, which Masalovich showed by the example of the portraits of extremists.
Ethics of the seller of vulnerabilities

The presentation by Alfonso de Gregorio was devoted to the exploit market, its participants, the activity of the zero-day vulnerability broker and relevant aspects of business ethics.
“Once a Japanese colleague asked me one delicate question,” says Alfonso. —What do I think about the moral side of a process like trading zero-day vulnerability information and exploits? Frankly, at that moment the ethical side was worrying me much less economically. The more interesting question for me was who was to blame more: those who exploit vulnerabilities, or developers of low-quality software? ”
Alfonso formulated the ethics of the vendor of vulnerabilities. The first rule: do not cooperate with companies that are seen in violation of human rights. The second rule: do not threaten the health of people: for example, do not sell vulnerabilities in medical equipment. Likewise, you can not trade in stolen insider information. The third rule: avoid conflicts of interest. Another prohibition concerns over-exploitation: the seller must specify the maximum number of attacks or targets. In addition, according to the ethical design of Alfonso de Gregorio, you cannot play for both teams in one match, that is, to help both the attackers and the defenders.
200 dollars per minute
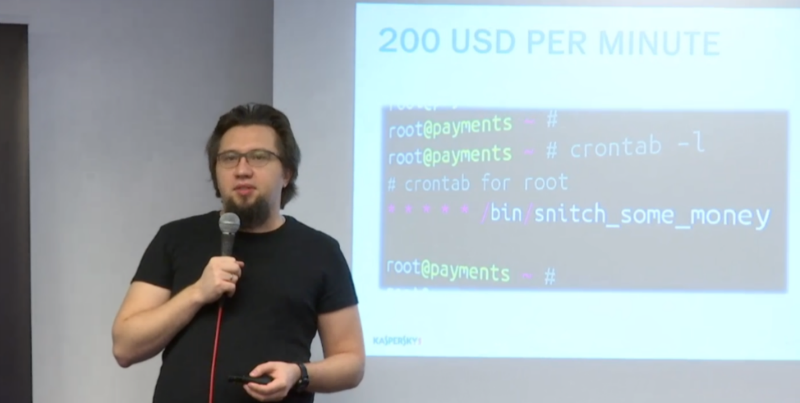
Sergey Golovanov from Kaspersky Lab spoke about an incident in one of the banks when a team of security experts from the LK was called in with the words “Come as soon as possible. An hour is not tolerated. Every minute costs us 200 dollars. ”
On the way to the bank, we were a little nervous going around traffic jams. There was a suspicion that they had heard some kind of “marketing bullshit” - the voiced figure seemed to us an artistic exaggeration. Upon arrival, it turned out that the crontab was in the system. All it was: every minute 200 dollars flew away to an unknown recipient. And such transactions were carried out within a few weeks.
After this work began. The bank was a server on Linux with open access via SSH. The server looked directly into the processing. Communication between the bank and the processing went through HTTP using POST requests. These requests determined where to transfer money, from which account and so on. How did the bank notice incorrect transactions? Imagine: there is such a specialist processing center at night. Peace and quiet, no transactions. And only one bank sends 200 dollars every minute. From the processing center called the bank. What are you guys doing? The bankers checked and were very surprised. They did not do this. The crontab script simply sent money to the "kurlu".
They called the admin and asked him for the password for SSH. The password was Sonic17. We looked at the authorization logs and see that the guys brute force their password by three attempts per week. It took them two months! The attackers found out the base word of the password, and then began to sort through the numbers. They did this on Saturdays, so we knew that they were not Jews. Began to look for the entry point. Found An info – .asp script was found on the website of an online bank serving legal entities. It was no different from info.asp. The only difference is that there was a line at the bottom that sent a SQL query, which is immediately executed on the database of the bank. At first they decided that it was the developer who was mistaken. The security service has already taken a soldering iron and began to look for it. But we asked them to wait and began to deal with the script that made the request to the online bank database. After that, the exe file that made the tunnel started working on this base. Looking at this path, it was possible to find out the entire list of used trojans: Meterpreter and Mimikatz in PowerShell, Powerpreter in obvious and PuTTY plink in whitelisted. Requests went from a web application through all corporate network!
Sergey's entire report “Copycat effect. From cyber prospecting to street theft "and dozens of other speeches can be viewed at www.phdays.ru/broadcast .
The details of Positive Hack Days VI can be monitored on the forum site and on Twitter on the hashtag # phdays .
Source: https://habr.com/ru/post/301510/
All Articles