How MasterCard Develops Biometric Identification
Reliable and universal identification - imperative. Passwords and PIN codes can not be kept in my head, so the search for a universal identification tool is continuously ongoing. MasterCard company is actively developing the “purchase by selfie”, in other words - the biometric identification of the cardholder when making a payment. Most recently, a semi-annual MasterCard and International Card Service (ICS) pilot project was completed in the Netherlands to test this feature among MasterCard cardholders. The results are encouraging: most of the participants would like to continue using fingerprint and / or face recognition technology (77%) for making a purchase. And in the summer of 2016, the technology will be available in the USA, Canada and some European countries.
Let's go through the history of biometric identification systems and try to look into the future.
Past
Anyone is unique, but there are not many options to identify him. The most accurate genetic examination, but to use it instead of entering the PIN-code is not too convenient. The “veteran” of the market - identification with the help of fingerprints - is familiar and well worked out, although it is not completely protected from fraudsters. In particular, in one of the episodes of the popular program Destroyers of Legends, the presenters easily misled the fingerprints using a copy of a latex fingerprint, a ballistic gel, and even paper.
')
In addition, not all devices are equipped with a fingerprint scanner. The same problem with identification according to the pattern of the iris / retina or blood vessels on the fingers. These methods are very reliable, but require complex and expensive equipment. That is why over the past decade, security experts have carefully looked at smartphones.
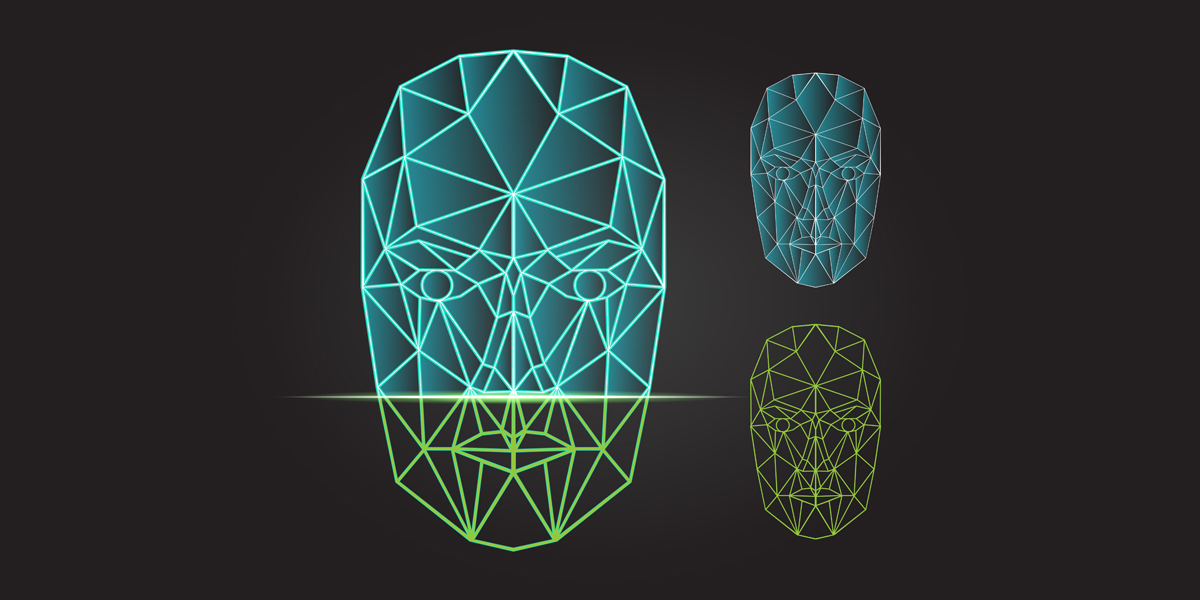
Today, even on the most budget models, cameras with a resolution of 5-7 megapixels are installed, and processor resources are easily enough for 3D models. Well, a person without a smartphone is quite difficult to find. In general, nothing prevents to realize a rather simple idea - identification by face geometry.
The present
It would seem that there is nothing revolutionary in this way. Every person looking at another homo sapiens identifies him by external signs, and above all by his face. In principle, to teach the car to do the same is easy. But there is one caveat - a person can extrapolate and understand that a bearded tourist standing on passport control and a clean-shaven young person in the photo in his passport are essentially the same person. But to teach the computer to think like a person was not easy, the service developers had to drink more than one hundred cups of coffee.
But the result is impressive: instead of entering the PIN code, just launch the Identity Check application (free, available for iOS 7 / Android 4.1 and higher), look at the camera and blink at the signal. The last action is necessary to protect against replacing a living person with a printed photo. In addition to the convenience of payments (no need to keep in mind the PIN-code, and generally carry a plastic card with you), experts predict a decrease in the number of fraudulent transactions. The fact is that using a stolen card is quite simple (in some cases you don’t even need to know the PIN). If the attacker took possession of the smartphone on which the application is installed, then he will have to:
1) run it (we hope all those who read these lines use Lock Screen);
2) somehow photograph the blinking owner of the device.
The task of the category of impracticable. In addition, a stolen smartphone can (and should) be promptly blocked by the owner.
Also, the payment system, receiving additional information from the smartphone, can build behavioral patterns for each cardholder. And in case of suspicion of fraud, reject the transaction or require further confirmation of identity.
It is noteworthy that, using behavioral patterns, the system can begin to "worry" even before the attacker began to spend your money. For comparison: if a plastic card was stolen from you and it began to boldly withdraw money somewhere in Uganda, the bank will also raise the alarm. But it will happen after conducting at least one transaction.
At the same time, MasterCard is constantly improving the algorithms for creating behavioral patterns, so that the system does not make mistakes, taking atypical transactions as suspicious. According to Ajay Bhalla, president of the Enterprise Security Solutions division of MasterCard, this is a very urgent problem, because according to statistics, every sixth plastic card holder has at least once encountered a failure in an operation that was mistakenly considered fraudulent.
Some more facts about security and MasterCard
In 1983, a security hologram appeared on MasterCard cards. Subsequently, this successful experience was borrowed by other players in the payment systems market.
In 1989, in order to more accurately and conveniently identify, they began to place a strip on the cards for the owner’s signature.
In 1995, the first chip card (EMV) was introduced.
And a little more infographics ...

In 1989, in order to more accurately and conveniently identify, they began to place a strip on the cards for the owner’s signature.
In 1995, the first chip card (EMV) was introduced.
And a little more infographics ...

Future
What next? Next in line is heart rate identification. For this, any wearable cardio sensor can be used (as an option, a fitness bracelet with a corresponding function, in particular, pilot testing was conducted with the Nymi Band). MasterCard believes that this technology is convenient because there is no need to do extra manipulations. Confirmation from the sensor comes constantly, that is, the smartphone is all the time "aware" that it is in the hands of the owner, and is permanently ready for payment.
There is a lot of work ahead. It is necessary to solve the problem of recognition of the heart rate in different situations (otherwise it will be a problem to buy a bottle of water after a run), and people with arrhythmia could optimize the algorithm in order to use the novelty. In the end, not everyone will want to acquire cardio sensors. That is why today the most promising is the identification by photo, fingerprint, or a combination of these methods.
Source: https://habr.com/ru/post/301058/
All Articles