Vulnerabilities in the proxy connection: how antiviruses reduce the security of the Internet browser

Traditionally, browsers include utilities for verifying certificates issued by websites, which allows them to verify their authenticity.
Ideally, security solutions should be completely transparent: they should not install any type of certificate and not use interception techniques (for example, man-in-the-middle through TLS-proxy) for analyzing user connections. This allows you to avoid incidents related to various relevant vulnerabilities, minimizing the impact on connection performance for devices.
')
However, not all anti-virus systems are what they seem to be, and many of them are often more dangerous than useful for the cyber security of users, as was stated in a recent study by Concordia University (Montreal, Canada). Its authors came to the conclusion that today many antiviruses reduce the security threshold of an Internet browser.
To filter SSL / TLS- protected traffic, some antiviruses and parental control applications place TLS proxies between client communication nodes.
The study studied the work of these proxies, because There are known problems in other, more mature, TLS traffic processing engines (for example, browsers or shared TLS libraries). Compared to standard proxies, client-side TLS proxies introduce their own unique limitations, and therefore must be analyzed for additional attack directions: in particular, proxies can trust their own root certificates to external content and use their own trust center of certification centers (bypassing the operating system and browser).
Covering the existing and new attack lines, the researchers created a comprehensive system for analyzing such client TLS proxies. Using this system, the authors of the study made a thorough analysis of eight antivirus programs and four parental control applications for Windows OS, which perform the TLS-proxy function, along with two additional products that only import the root certificate.
Systems analysis revealed that some of the products tested had a negative impact on the protection of a TLS connection. In particular, it was found that four products are vulnerable when attacking with the interception of messages and the substitution of keys under the man-in-the-middle attack (MITM) and two more when TLS filtering is enabled. Some of these products also trick browsers, which as a result of this believe that the TLS connection is more secure than it actually is, for example, artificially updating the version of TLS on the client’s server.
The study was performed to identify new risks added by TLS interception tools that may be used by millions of users.

Figure 1. Illustration of MITM attacks against a content control application that intercepts TLS, resulting in its own root certificate of the allegedly issuer of external certificates. In addition, TLS settings are not transparent to browsers, and therefore they can be lowered proxy to an undesirable level. All the SSL / TLS versions shown are the highest that can be used between connection nodes, given that MITM supports TLS 1.2.
The table below shows the list of products tested in the study. Items in bold are products that can establish a root certificate and a proxy for TLS connections. These products were analyzed by researchers.
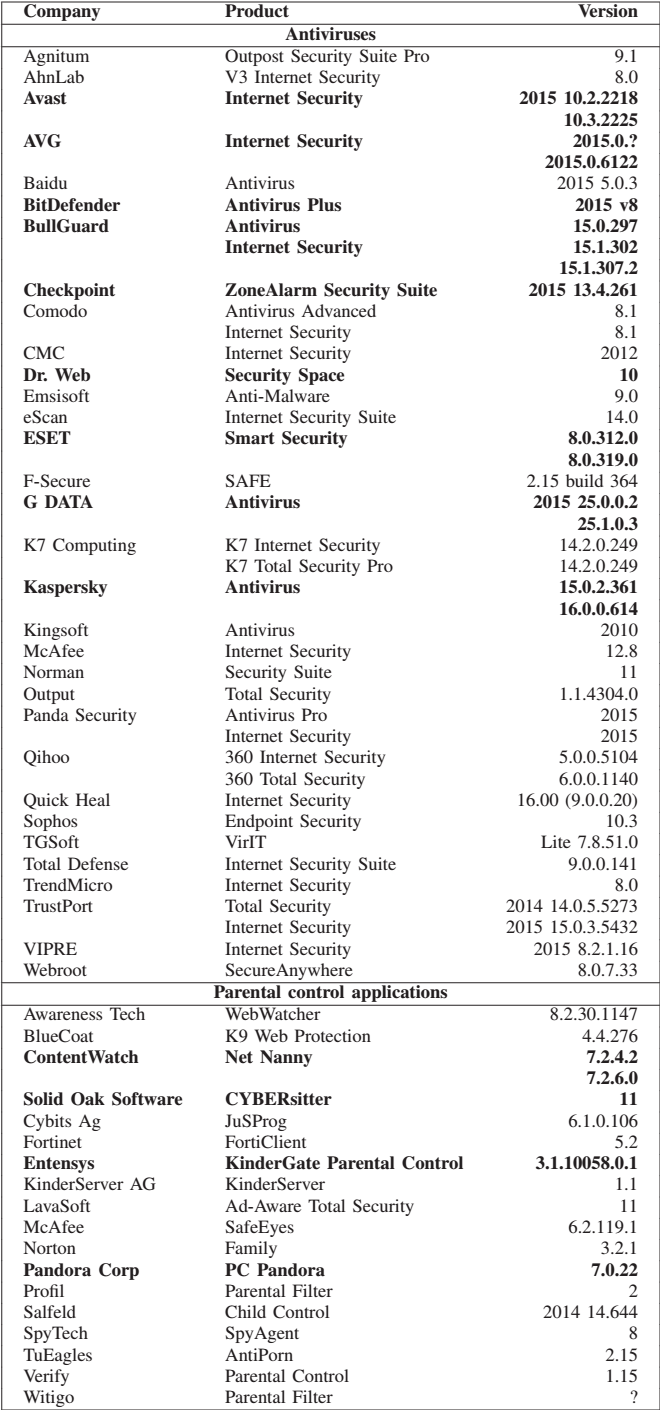
As a result, those anti-virus systems that are marked as vulnerable in the study can potentially lead to deception of browsers who will trust any certificate, even if they should not trust it.
For more information on the methodology and results of the research conducted by specialists from Concordia University, see here .
Source: https://habr.com/ru/post/301016/
All Articles