The backdoor in the Linux kernel of the Chinese manufacturer ARM opens up access to the smartphone with one command
The Chinese company Allwinner is engaged in the production of components for many models of inexpensive Android devices, personal computers on the ARM platform and other devices. Information security researchers have discovered a backdoor in the Linux kernel, which the company supplies with its products: it allows you to access any device using one simple command.
What is the problem
To gain access to Android devices, which contain a backdoor in the software, you just need to send the word “rootmydevice” to any undocumented debugging process. As a result, any such process with any UID can get root-rights:
')
echo "rootmydevice" > /proc/sunxi_debug/sunxi_debug The backdoor code , which allows local privilege escalation on Android-based ARM devices, is contained in the public version of the Allwinner firmware created for the company's devices. The basic version of Android does not contain this backdoor. Apparently, the Allwinner developers mistakenly did not remove part of the debugging code, which led to the appearance of such a dangerous error.
A bit of history
Initially, the Linux 3.4-sunxi kernel was created to support the Android operating system on tablets running on Allwinner ARM, but later it was used to port Linux to various Allwinner processors — devices like Banana Pi, micro-PC, Orange Pi, and others.
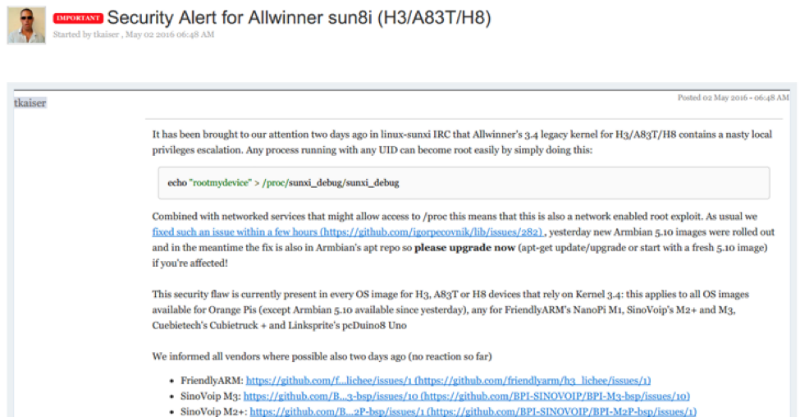
At the forum of the Armbian operating system, a moderator under the nickname Tkaiser noted that in the case of “use in conjunction with network services that open access to / proc”, the remote operation of the backdoor is also possible. In addition, the specialist said that at the moment the security error is contained in all images of the 3.4 kernel used on the A83T, H3 and H8 devices.
Experts at Positive Technologies recommend, if possible, not to use devices running the OS based on the version of the Linux 3.4-sunxi kernel from Allwinner until all the details of the incident have been clarified.
However, even the use of firmware and devices of well-known manufacturers also does not guarantee complete security. In March 2016, it became aware of the critical vulnerability of Cisco Nexus 3000 routers, which allowed them to get remote access. Earlier in 2015, a vulnerability that allowed attackers to gain access to virtually any data was found in Dell laptops.
In addition, in February of the same year, it became aware of the Superfish program, which since the summer of 2014 was supplied with Lenovo laptops of the G, U, Y, Z, S, Flex, Miix, Yoga and E series. The utility listened for traffic, including HTTPS , forged SSL certificates of third-party sites, analyzed user search queries and inserted advertisements on the pages of third-party resources. After the scandal, Lenovo released an official letter in which it recognized the problem of Superfish and presented various ways to remove the utility. Later, the vendor site was hacked by hackers from Lizard Squad - the attack was made in retaliation for creating the Superfish program.
Source: https://habr.com/ru/post/300988/
All Articles