How to legally obtain information about users of the site from their social. nets

What information about users can be obtained from the social. networks, which methods are illegal and punished, how to legally obtain data and more. others are discussed in the article.
Without exaggeration, today personalized marketing is gaining more relevance when we offer the user exactly what he needs, write or call him at the most appropriate moment and always call by name.
All this is impossible without additional information about customers. Therefore, the automatic collection of key information about each user comes to the fore, in order to understand his motives, interests, preferences, and with a high probability of bringing it to the point of purchase.
')
We have already told you what benefits can be obtained by tracking the actions of each user on the site (clicks, visited pages, entered data, referral sources, etc.) and recording it in an individual card of each.
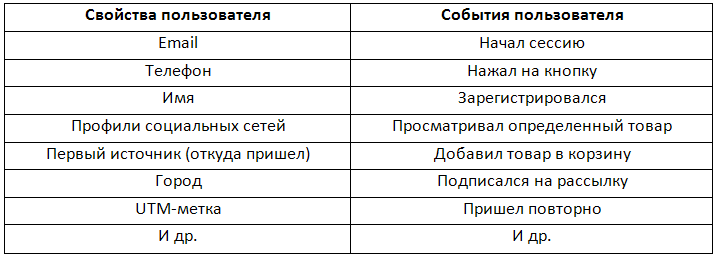
Today we will understand what information can be obtained from the user from the social. networks. Here is a list of data that can be obtained legally:
- The name is the simplest property that can be pulled from the social. networks. In order not to scare the user, in most forms it makes sense to ask only for email or phone. The fewer items to fill, the better. But the trouble is, users love when they are addressed by name. In this case, the name can be pulled from the social. networks;
- Link to profile in social. Networks - helps to individually approach communication with the client, you can go to the user profile and find interesting information on its page that will help you better understand it and bring it to the purchase. This may not help in all areas, because users light in the social. networks are not all aspects of their lives;
- Avatar is an additional attribute that helps your employees (support, sales department) feel the effect of live communication and add more sincere emotions to communication.
How to punish for fraud and what applies to it
Not everyone knows that social phishing (clickjacking) is an illegal and deceptive method of getting user contacts from social networks. networks. If previously such companies remained unpunished, now the situation has changed (for example, Yandex announced a downgrade in the search for those sites that use clickjacking).
We fully support this and we ourselves have always opposed social phishing.
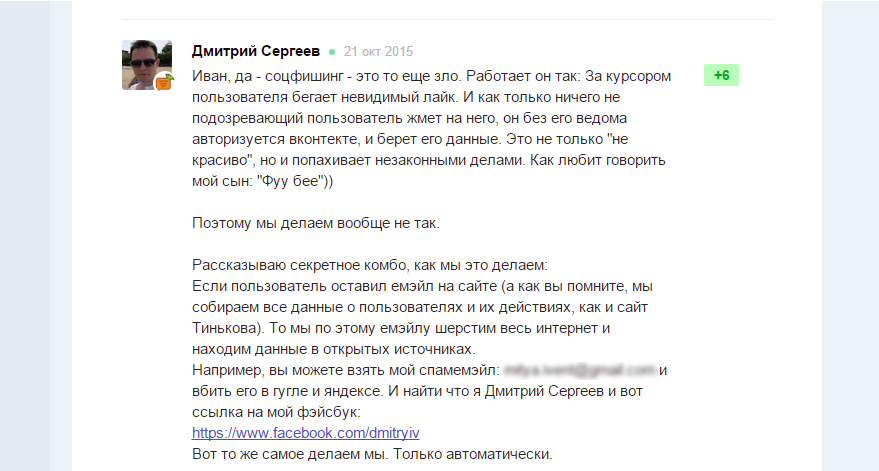
The essence of social phishing is very simple. When a user enters the site, an invisible layer (frame) is loaded, on which the Like button (from the social button) is located. network. In this case, the user does not see any button, which means that his data is obtained fraudulently.
The user clicks to any place on the site, gets on this invisible button (she runs the cursor). Thus, he gives permission to view his profile and his data is transferred to the gray service.
The idea that you can get data without the consent of the visitor says a lot about this method.
There is a way to recognize the presence of such an invisible like - when you hover over it, instead of the usual cursor, you will see the hand icon with the index finger (as when hovering over a link).
How to legally get information about a user from his social. network.
Let us tell you with an example of how we organized it in the Carrot Quest service. In addition to collecting data from the social. networks, the service collects all the key information about each user (their actions on the site, sources of transition and much more). Here is how this information looks in each user's card:
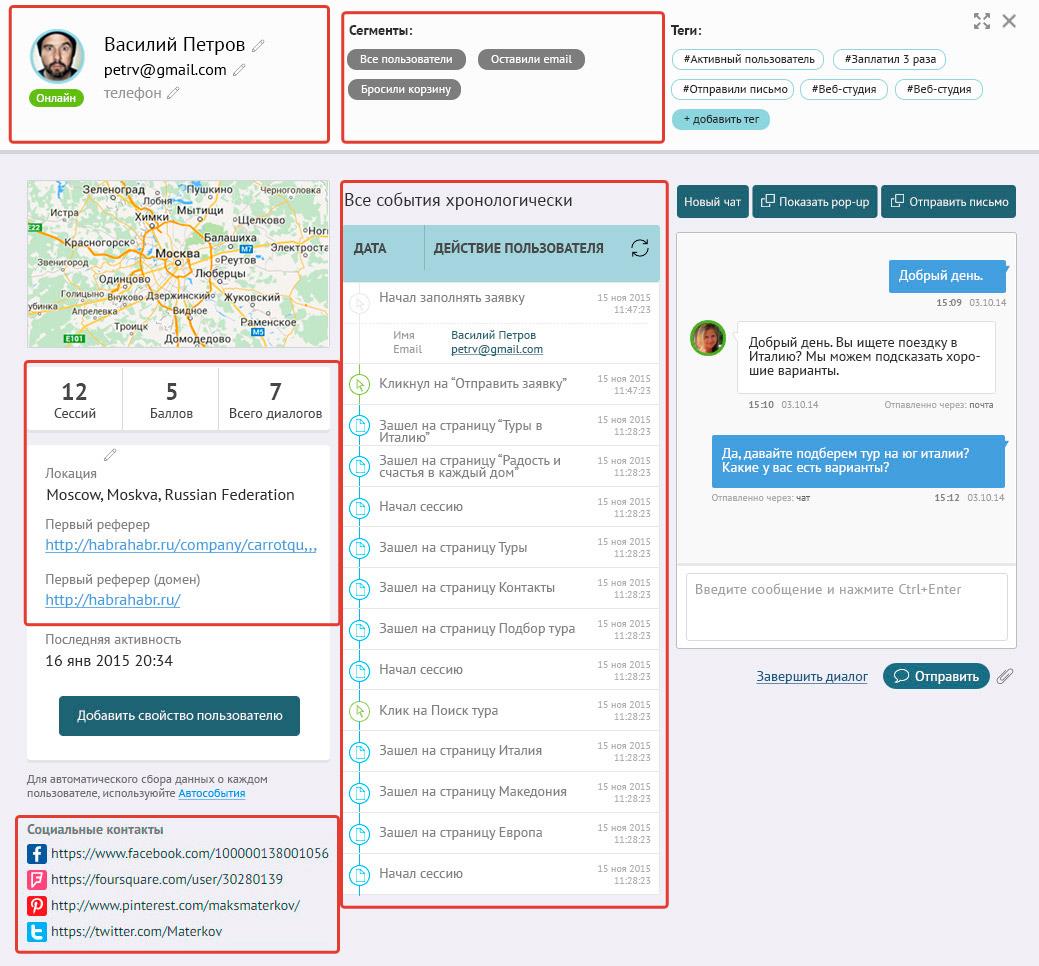
Let's take a closer look at how we organized the collection of data about users from social. networks:
Data is loaded only if the user voluntarily left his email. Then we simply automate what each of you can do manually: we are looking for information on this email in the social. networks.
Check for yourself. For example, you can take the user's email and enter it in the search on Facebook, it will show you the user profile.
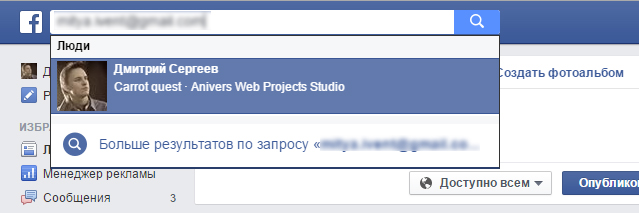
All this is done automatically, no matter what your site traffic, the profile is checked for everyone who left an email. Further, the data is simply loaded into the user's card.
If the user does not leave his email, then neither you nor Carrot Quest will learn anything about this user from public sources.
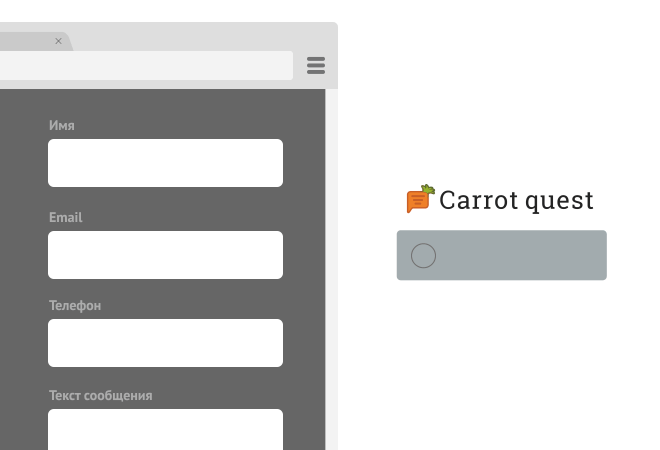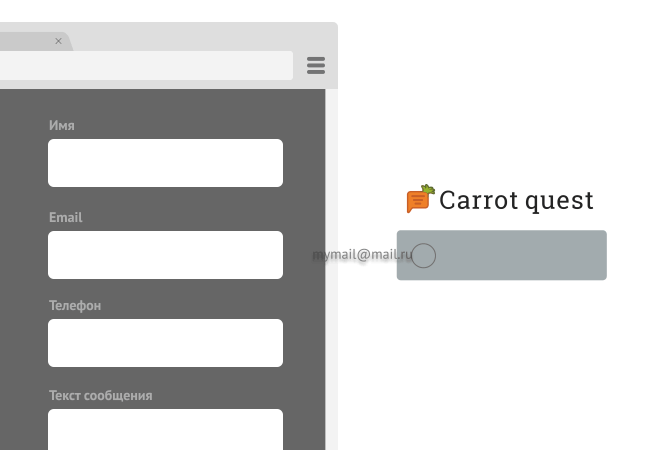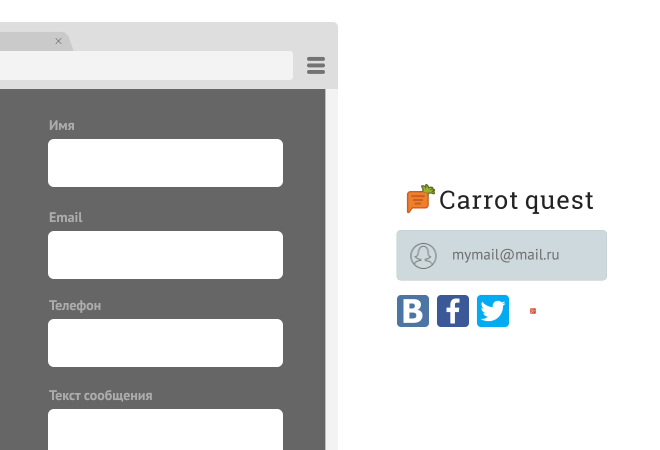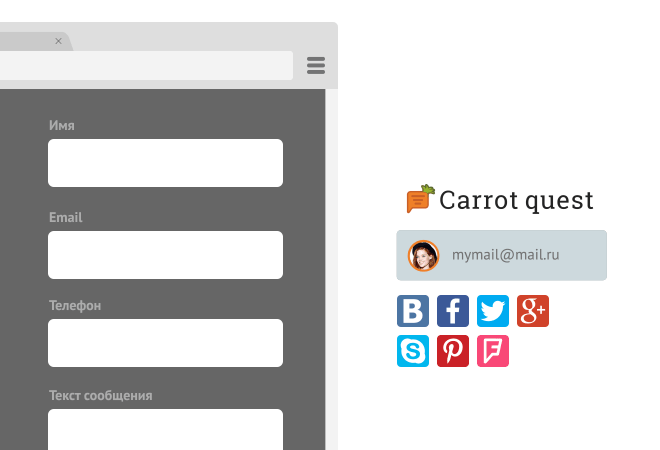
Thus, do not find users who have banned access to their data. And this is good, we are convinced that this is correct. Be honest with your customers.
Be careful. With pleasure, the team of Carrot Quest service, which knows all the information about each user on your site and with this knowledge in mind, helps guide the user to purchase, both manually and automatically.
Source: https://habr.com/ru/post/300110/
All Articles