The structural model of the access control system of an enterprise with tenants and their customers
At one enterprise, whose main activity is the provision of offices and warehousing services, it became necessary to establish an ACS. Clients of the enterprise are organizations and individual entrepreneurs engaged in trade, procurement and production activities. In turn, they have a large number of their own customers.
Requirements for the system, in addition to the usual requirements for the accounting of working time of employees of the landlord and tenants, include requirements for the control of customers by tenants, in terms of prohibiting the export of goods without a mark on payment or export authorization. Also, it is necessary to take into account the presence of part-timers both at the main enterprise and at the tenants.
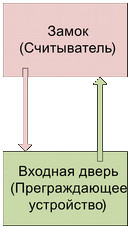
Let's build a structural model of access control to the territory with one access point. Any access point is equipped with a lock, for the opening of which there is a set of keys. The simplest model of such a system includes four entities that play certain roles, for example, for an apartment with one entrance door:
')

However, even with the most detailed description of entities, they are not a model of the system, because there are no connections between them. For example, when describing a door, we should know what apartment it belongs to. Establishing connections between entities (objects), we fix the result of interaction between them and set the relationship as a set of attributes: the door to the apartment is installed on January 1, 2000 (the Date attribute), the door lock is set on January 2, 2000 (the Date attribute) by master P. P. Petrov. (attribute Master).

Since each of the related objects may have its own “look” at the connection between them, two connections need to be considered. For example, the link Lock # Doors is a set of attributes,
Doors link # Lock - attribute set
Installing a second lock on the door means the appearance not only of a new instance of an entity (without changing its role), but also changing its “dimension” - from a one-dimensional Lock to a multi-dimensional Locks . Similarly, the installation of the second door will change the "dimension" of the corresponding entity:
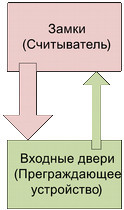
The preservation of roles when entities change (for example, their dimensions) determines the preservation and structure of the relations between them. We still consider two connections between multidimensional entities (objects), but the connections themselves become multidimensional, with the number of components in the connection Lock # Doors equals the number of locks in the system, and the connection Doors # Lock - the number of doors.
The most interesting connections from the point of view of the access control system are the connections between the Keys object and the Locks object (the roles of the Identifier and the Blocking Device). It is in these connections that you can keep track of at what moment which lock was opened or closed and which key. Communication Keys # Locks , for example,

may have the form:
Communication Locks # Keys , in turn, may have attributes related to the moments of receiving, losing and replacing keys.
In any case, the objects include the elements of the system, whose attributes practically do not change during the observation period, unlike connections, whose attributes can significantly change during the same time. The choice of a set of attributes for system elements is entirely determined by the system designer during its modeling.
In a real access control system, you need to take into account a number of new roles and their performing objects. Add to the structural model you need the role Owner identifier, the object that performs this role, we call the Visitor , and also change the performers of some roles:
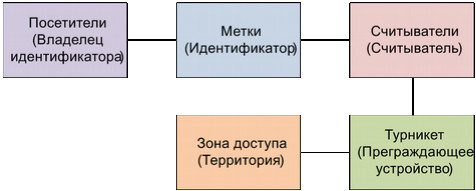
Tags # Visitors :
Such a connection allows:
uniquely identify the visitor by tag (only one entry in the link can have Tag Status = Active);
give the employee a one-time or one-day temporary pass to replace the forgotten one;
set the validity of the temporary pass.
Communication Visitors # Tags :
Such a connection allows you to organize, for example, the accrual of penalty points for an employee who has lost an access card or who regularly forgets it.
Communication Readers Tags :
This connection allows you to keep a log of events with the reader.
Communication Tags # Readers will not be installed, since there are no significant attributes for it.
Reception of the status Entrance is authorized, does not mean yet that the input has taken place. In order to display the attributes associated with the transition, we will add links between the tags and the turnstile.
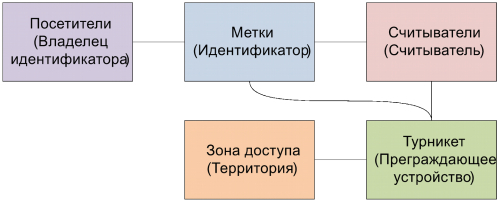
The connection between the tag and the reader should indicate which tag is which reader and when it is determined, as well as fix the status of the tag.
Communication Tags #Ticket :
Such a connection allows you to keep records of transitions through the turnstile by each visitor in accordance with his tag.
Communication Turnstile Tags :
This link allows you to keep a log of visitors and transitions. If it is impossible to determine the transition direction (the turnstile is open with buttons in both directions), and the transition has been made, the transition time with an undefined direction and an empty tag name is indicated.
Communications between the turnstile and readers, as well as the turnstile and access zone can be used to account for the operation of devices, for example, communication Turnstile Readers :
In order to determine the direction of the transition in the links of the Tag # Turnstile and Turnstile # Tags you need to know the position of the visitor (tag) in relation to the access zone. It is convenient to keep the corresponding attribute in the connection between the label and the access zone, therefore, we will create the corresponding connection:
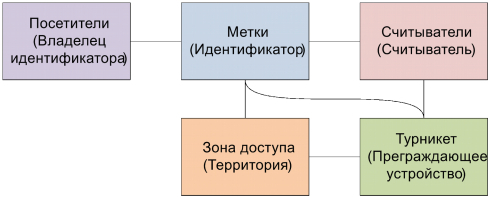
Access_Links # Tags :
Such a relationship allows you to determine the position of the Visitor at any time, as well as provide control over the change of positions in the presence of several access zones. For example, the Visitor cannot get into the interior, if he did not enter through the turnstile.
Link Tags # Access Zone :
Such a relationship allows you to obtain the necessary data to account for working time, taking into account the actual time spent in the territory. However, this data is not enough. Firstly, we need information about the company-employer (firms-employers), and secondly - information about the work schedule. To account for such information, we will add a new Firm object in the role of the Employer and establish links between it and the employees (Visitors).
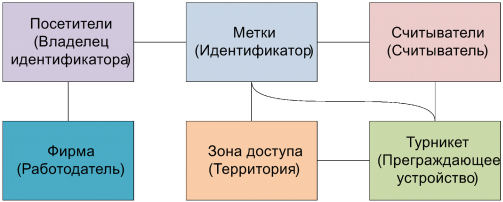
Communication Visitors # Firm :
Such a relationship contains all the data necessary for the accounting of working hours, as well as the resolution of possible conflict situations. Accounting data are based on a comparison of actual data and work schedules. Data on the schedule of work contained in the connection of the Company # Visitors :
Such communication allows to take into account the data on the work schedule for each employee, as well as to prohibit or allow entry to the Zone of access on non-working days. Data for communication are generated outside the access control system and must come from firms.
Now we will consider control over clients of firms. Such visitors are buyers or suppliers (or their representatives) of firms. Firms for them are not in the role of the Employer, but in the role of the Supplier or the Buyer. Thus, the object has several roles:
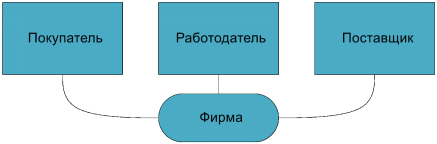
The number of connections between the visitor and the company changes accordingly. And although now every visitor can play the roles of an Employee, Buyer or Supplier, in the framework of the structural model, we leave him only one role - the Owner of the identifier. But the increase in the number of connections

allows you to collect and store all the information necessary to monitor tenant customers.
Communication Visitors # Buyer # Firm :
This relationship allows you to allow the exit of the buyer, depending on the conditions imposed by the supplier (all three times are not zero). Similarly, in connection Visitors # Supplier # Firm :
contains the data necessary to allow the supplier to leave the territory.
Thus, we have built a fairly simple structural model of access control systems, allowing to solve all the problems facing such systems, as well as a number of additional tasks.
In the following, the data editing control system and their storage will be described, as well as an example implementation with a description of the devices used.
Requirements for the system, in addition to the usual requirements for the accounting of working time of employees of the landlord and tenants, include requirements for the control of customers by tenants, in terms of prohibiting the export of goods without a mark on payment or export authorization. Also, it is necessary to take into account the presence of part-timers both at the main enterprise and at the tenants.
Features of the structural model
Let's build a structural model of access control to the territory with one access point. Any access point is equipped with a lock, for the opening of which there is a set of keys. The simplest model of such a system includes four entities that play certain roles, for example, for an apartment with one entrance door:
')

However, even with the most detailed description of entities, they are not a model of the system, because there are no connections between them. For example, when describing a door, we should know what apartment it belongs to. Establishing connections between entities (objects), we fix the result of interaction between them and set the relationship as a set of attributes: the door to the apartment is installed on January 1, 2000 (the Date attribute), the door lock is set on January 2, 2000 (the Date attribute) by master P. P. Petrov. (attribute Master).

Since each of the related objects may have its own “look” at the connection between them, two connections need to be considered. For example, the link Lock # Doors is a set of attributes,
{" ", " ", " "} Doors link # Lock - attribute set
{" ", " ", " ", [" "]} 
Installing a second lock on the door means the appearance not only of a new instance of an entity (without changing its role), but also changing its “dimension” - from a one-dimensional Lock to a multi-dimensional Locks . Similarly, the installation of the second door will change the "dimension" of the corresponding entity:

The preservation of roles when entities change (for example, their dimensions) determines the preservation and structure of the relations between them. We still consider two connections between multidimensional entities (objects), but the connections themselves become multidimensional, with the number of components in the connection Lock # Doors equals the number of locks in the system, and the connection Doors # Lock - the number of doors.
The most interesting connections from the point of view of the access control system are the connections between the Keys object and the Locks object (the roles of the Identifier and the Blocking Device). It is in these connections that you can keep track of at what moment which lock was opened or closed and which key. Communication Keys # Locks , for example,

may have the form:
[{" ", " (/)", " "}, {}, ..., {}] Communication Locks # Keys , in turn, may have attributes related to the moments of receiving, losing and replacing keys.
In any case, the objects include the elements of the system, whose attributes practically do not change during the observation period, unlike connections, whose attributes can significantly change during the same time. The choice of a set of attributes for system elements is entirely determined by the system designer during its modeling.
Roles and objects of the structural model
In a real access control system, you need to take into account a number of new roles and their performing objects. Add to the structural model you need the role Owner identifier, the object that performs this role, we call the Visitor , and also change the performers of some roles:

Tags # Visitors :
[{ " ", " ", " ": (, , ) ", " ", " ", " ": (, )}, ...] Such a connection allows:
uniquely identify the visitor by tag (only one entry in the link can have Tag Status = Active);
give the employee a one-time or one-day temporary pass to replace the forgotten one;
set the validity of the temporary pass.
Communication Visitors # Tags :
[{" ", " ", " "}, ...] Such a connection allows you to organize, for example, the accrual of penalty points for an employee who has lost an access card or who regularly forgets it.
Communication Readers Tags :
[{ " ", " ", " ": ( , , , ), " "}, ...] This connection allows you to keep a log of events with the reader.
Communication Tags # Readers will not be installed, since there are no significant attributes for it.
Reception of the status Entrance is authorized, does not mean yet that the input has taken place. In order to display the attributes associated with the transition, we will add links between the tags and the turnstile.

The connection between the tag and the reader should indicate which tag is which reader and when it is determined, as well as fix the status of the tag.
Communication Tags #Ticket :
[{ " ", " ", "": (, ), " "}, ...] Such a connection allows you to keep records of transitions through the turnstile by each visitor in accordance with his tag.
Communication Turnstile Tags :
{ " ", [" ", "": (, , ), " "]} This link allows you to keep a log of visitors and transitions. If it is impossible to determine the transition direction (the turnstile is open with buttons in both directions), and the transition has been made, the transition time with an undefined direction and an empty tag name is indicated.
Communications between the turnstile and readers, as well as the turnstile and access zone can be used to account for the operation of devices, for example, communication Turnstile Readers :
{" ", [" c", ["": (, , ) ," "]]} In order to determine the direction of the transition in the links of the Tag # Turnstile and Turnstile # Tags you need to know the position of the visitor (tag) in relation to the access zone. It is convenient to keep the corresponding attribute in the connection between the label and the access zone, therefore, we will create the corresponding connection:

Access_Links # Tags :
{" ", [" ", " ", ""]} Such a relationship allows you to determine the position of the Visitor at any time, as well as provide control over the change of positions in the presence of several access zones. For example, the Visitor cannot get into the interior, if he did not enter through the turnstile.
Link Tags # Access Zone :
[{" ", " ", " ", " ", " "}] Such a relationship allows you to obtain the necessary data to account for working time, taking into account the actual time spent in the territory. However, this data is not enough. Firstly, we need information about the company-employer (firms-employers), and secondly - information about the work schedule. To account for such information, we will add a new Firm object in the role of the Employer and establish links between it and the employees (Visitors).

Communication Visitors # Firm :
[{" ", " ", " ", " ", " ", " ", " ", " "}] Such a relationship contains all the data necessary for the accounting of working hours, as well as the resolution of possible conflict situations. Accounting data are based on a comparison of actual data and work schedules. Data on the schedule of work contained in the connection of the Company # Visitors :
{" ", [" ", " ", " ", ["", " ", " ", " "]]} Such communication allows to take into account the data on the work schedule for each employee, as well as to prohibit or allow entry to the Zone of access on non-working days. Data for communication are generated outside the access control system and must come from firms.
Now we will consider control over clients of firms. Such visitors are buyers or suppliers (or their representatives) of firms. Firms for them are not in the role of the Employer, but in the role of the Supplier or the Buyer. Thus, the object has several roles:

The number of connections between the visitor and the company changes accordingly. And although now every visitor can play the roles of an Employee, Buyer or Supplier, in the framework of the structural model, we leave him only one role - the Owner of the identifier. But the increase in the number of connections

allows you to collect and store all the information necessary to monitor tenant customers.
Communication Visitors # Buyer # Firm :
[{" ", " ", " ", " ", " "}] This relationship allows you to allow the exit of the buyer, depending on the conditions imposed by the supplier (all three times are not zero). Similarly, in connection Visitors # Supplier # Firm :
[{" ", " ", " ", " "}] contains the data necessary to allow the supplier to leave the territory.
Thus, we have built a fairly simple structural model of access control systems, allowing to solve all the problems facing such systems, as well as a number of additional tasks.
In the following, the data editing control system and their storage will be described, as well as an example implementation with a description of the devices used.
Source: https://habr.com/ru/post/283586/
All Articles