Antivirus as a threat
Most people do not consider anti-virus protection as a source of additional threat. Antiviruses are perceived as trusted applications, which at the expense of some performance losses can protect the information system from a variety of attacks. As a result, antivirus is often the only means of protecting end users, and a bunch of several antiviruses are the main solution for enterprise security.
But, like any complex program, antivirus software is vulnerable to vulnerabilities. The processes of anti-virus products, as a rule, are trusted and run in privileged mode, with high access rights. This makes antiviruses an interesting target for intruders, since their operation can lead to the compromise of the entire system.
')
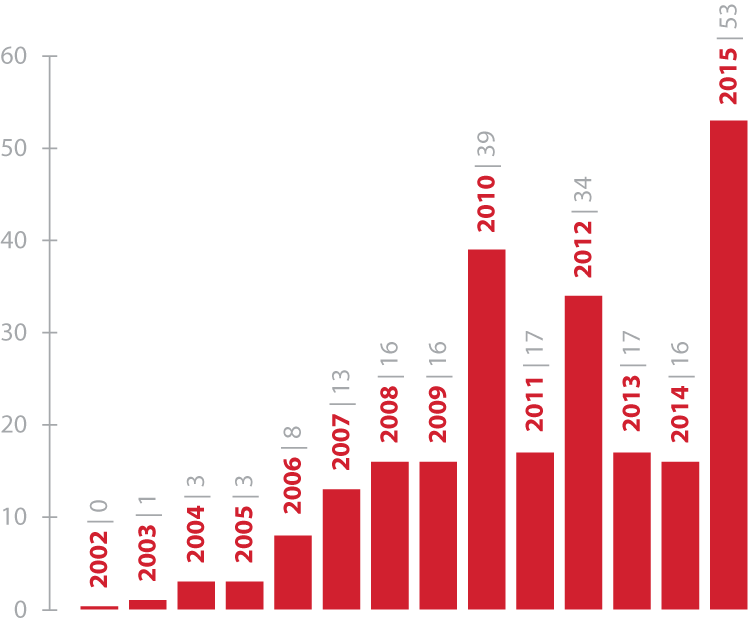
In recent years, there has been a growing interest in security vulnerabilities in general and antiviruses in particular. This is evidenced by the increase in the number of exploits published on exploit-db and similar resources. The graph above shows the number of vulnerabilities found in known antivirus products for each year over the past 15 years.
At the beginning of the zero years, materials about vulnerabilities in anti-virus protection tools appeared extremely rarely, and over the past year, more than fifty exploits were published, most of which are based on critically dangerous antivirus vulnerabilities and associated with authentication bypass, privilege escalation and remote code execution. In particular, in 2015, vulnerabilities were found in ESET , Avast , BitDefender, Symantec , Kaspersky Lab, FireEye , Malwarebytes products.
In addition to independent researchers, since 2014, the Google Project Zero team has joined the search for security vulnerabilities. They found a significant portion of antivirus vulnerabilities published over the past year. It is natural that government organizations are also showing interest in this topic: we have already talked about the research of Russian antiviruses that are being conducted by Western intelligence agencies .
It is difficult to make accurate predictions about how this trend will develop further, but some assumptions can be made on the basis of exploits published in the first quarter of 2016. Their brief descriptions are presented below.
Attacks using vulnerable antiviruses
TrendMicro
On January 11, 2016, a Tavis Ormandy researcher on the Google Security Research team discovered the critically dangerous TrendMicro antivirus vulnerability leading to remote code execution.
When installing the antivirus, the default component is the Password Manager component, which is set by the installer to autoload. This module is written in JavaScript using node.js. It opens a lot of RPC ports for processing API requests via HTTP. The vulnerability was found in the openUrlInDefaultBrowser API function, which calls ShellExecute () without checking the arguments passed, thereby allowing the execution of arbitrary code.
x = new XMLHttpRequest() x.open("GET", "https://localhost:49155/api/ openUrlInDefaultBrowser?url=c:/windows/system32/calc.exe true); try { x.send(); } catch (e) {}; The patch was released a week after treatment.
exploit-db.com/exploits/39218
McAfee Application Control
On January 12, experts from the Austrian company SEC Consult published a report on the successful circumvention of the McAfee Application Control protection. This application prohibits the launch of applications not defined in the white list, and is intended primarily to protect critical infrastructures. Considered version 6.1.3.353 for Windows. We found ways to launch unauthorized applications bypassing protection, methods for launching arbitrary code, bypassing software DEP implemented in McAfee Application Control, bypassing UAC when McAfee product protection is on, bypassing write protection to the white list. To top it off, vulnerabilities in the swin1.sys driver were found leading to a system crash.
exploit-db.com/docs/39228.pdf
Quickheal
On February 19, Researcher Fitzl Csaba wrote a proof-of-concept that exploits a vulnerability in the popular Indian anti-virus QuickHeal 16.00. The webssx.sys driver was exposed to CVE-2015-8285, the operation of which leads to an increase in privileges or causes a BSOD. The driver is created without the
FILE\_DEVICE\_SECURE\_OPEN , which allows any user to interact with this driver bypassing the ACL. The researcher found the IOCTL code and the required size of the buffer transferred to the driver, leading to the invocation of the vulnerable function. Due to insufficient verification of the received data from the input buffer, an integer overflow occurred in the argument passed to the memcpy function.exploit-db.com/exploits/39475
Comodo
On February 29, hacker Greg Linares discovered a vulnerability in Comodo's GeekBuddy module, leading to local privilege escalation. The GeekBuddy module, when executed, runs several processes, one of which tries to load the shfolder.dll library. Since instead of the absolute path in the file launched by GeekBuddy, only the name of the library is strictly specified, dll substitution is possible. If you put a malicious shfolder.dll in C: \ ProgramData \ Comodo \ lps4 \ temp \ and start the client update or wait until it starts automatically, the user can elevate the privileges to the SYSTEM level and completely compromise the system.
exploit-db.com/exploits/39508
Avast
On March 4, Google Security Research continued to publish Avast Antivirus vulnerabilities. This time, the error related to memory corruption when parsing digital certificates was closed. Tavis Ormandy created an executable PE file that Avast “crashed” with an error while scanning. According to the researcher, the error is related to memory corruption when parsing the file digital signature.
exploit-db.com/exploits/39530
McAfee VirusScan
On March 7, Maurizio Agazzini published an article about another vulnerability in McAfee products. The researcher has written an exploit that allows you to bypass the security restrictions of the McAfee VirusScan Enterprise 8.8 antivirus. Using the found vulnerability, a user with local administrator rights could bypass security restrictions by disabling the antivirus - without knowing its password.
The vulnerability was fixed with a February 25 patch, although the exploit’s first exploits by McAfee date back to the fall of 2014.
exploit-db.com/exploits/39531
Avira
March 16th critically dangerous vulnerability found in Avira antivirus. It is expected that the antivirus should be able to handle PE files without fail. However, when testing Avira antivirus scanning in PE files, a heap underflow vulnerability was discovered. The error was reproduced when parsing the section table headers. If the section header had an excessively large RVA, Avira saved the calculated offset to the buffer on the heap and recorded the data controlled by the attacker (data from
section->PointerToRawData in the source file). The vulnerability led to RCE with NT\_AUTHORITY\SYSTEM privileges. Patch released on March 18th.exploit-db.com/exploits/39600
And again Comodo
March 19 published a report on critically dangerous vulnerabilities in Comodo antivirus. This product includes an x86 emulator used to automatically unpack and monitor obfuscated executable files. It is assumed that the emulator executes the malicious code safely for a short period of time, thereby allowing the sample to be unpacked or to detect some interesting behavioral trait.
In addition to problems related to memory corruption, the emulator was found to contain the arguments of some dangerous emulated API calls that are passed to real API functions during scanning. Several wrappers simply extract the arguments from the emulated address space and transfer them directly to the system calls, while executing with the
NT\_AUTHORITY\SYSTEM privileges. The results of the calls are then returned to the emulator and the code execution continues.This allows for various attack scenarios. For example, read, delete, list and use cryptographic keys, interact with smart cards and other devices. This is possible because the arguments of the CryptoAPI functions are passed by the emulator directly to the real API. Another example of a threat was reading any registry keys when using a wrapper over
RegQueryValueEx , whose arguments are passed to the real API directly.This attack vector is quite indicative, since an attacker can trigger the execution of malicious code in an emulator — simply by sending the victim an email or sending it via a link to an infected site. A patch fixing the vulnerability was released on March 22.
exploit-db.com/exploits/39599
On March 14, 2016, a critically dangerous error was detected in the Comodo antivirus engine. The execution of arbitrary code was possible when the anti-virus unpacked malicious files protected by the PackMan protector. Packman is a little-known open source packer, Comodo unpacks it during the scan.
When processing files compressed with this packer with certain options, compression parameters are read directly from the input file without validation. Using fuzzing, it was revealed that in the
CAEPACKManUnpack::DoUnpack\_With\_NormalPack you can pass the pointer pksDeCodeBuffer.ptr to an arbitrary address, which allows an attacker to free an arbitrary address with the free () function. The vulnerability allows an attacker to execute code with NT\_AUTHORITY\SYSTEM privileges. The patch was released on March 22.exploit-db.com/exploits/39601
What to do
Despite the vulnerability of antiviruses, completely abandon them difficult. In those cases when it is necessary to analyze large volumes of files, the antivirus engines cope with the work faster than alternative solutions (for example, sandboxes). This is achieved through advanced static analysis.
In our opinion, when building an effective protection system based on antivirus solutions, both detection accuracy and minimization of risks introduced by the protection tool should be achieved. Here are some promising areas for this task:
- Accuracy and speed of detection is enhanced by scanning with several anti-virus engines of various manufacturers. Such an opportunity is provided by some online services (for example, Virustotal.com) - however, in this case, you need to upload your files to a third-party resource, that is, there is a risk of leakage of confidential data to “third parties”. It would be logical to organize such a scan on a local server, without any extra requests to third-party applications.
- Security risks can be reduced by examining suspicious files in an isolated safe environment. At the same time, it should be understood that modern malware already knows how to analyze the environment and bypass some sandboxes, or not to manifest itself in them. Therefore, it is necessary to use “traps” that are as close as possible to the working system, where you can observe the behavior of the malware for a long time and imperceptibly.
“Even having detected malware, the antivirus cannot detect all objects that have been adversely affected in the past, until it is detected.” Therefore, it is desirable that the protective system allows for retrospective analysis.
We use these and other technologies in the development of the PT MultiScanner system.
Source: https://habr.com/ru/post/283448/
All Articles