We are looking for vulnerabilities using google
Any search for vulnerabilities in web resources begins with intelligence and information gathering.
Intelligence can be both active - brutfors files and directories of the site, launch vulnerability scanners, manual viewing of the site, and passive - search for information in different search engines. Sometimes it happens that the vulnerability becomes known even before the opening of the first page of the site.
How is this possible?
Search robots, without stopping roaming the Internet, in addition to information useful to the average user, often fix what can be used by attackers when attacking a web resource. For example, script errors and files with sensitive information (starting from configuration files and logs, ending with files with authentication data and database backups).
From the point of view of the search robot, the error message about the execution of the sql query is plain text, inseparable, for example, from the description of the goods on the page. If suddenly the search robot came across a file with the extension .sql, which for some reason turned out to be in the working folder of the site, it will be perceived as part of the content of the site and will also be indexed (including, possibly, the passwords specified in it).
Such information can be found knowing well-established, often unique, keywords that help separate “vulnerable pages” from pages that do not contain vulnerabilities.
A huge database of special requests using keywords (called dorks) exists on exploit-db.com and is known as the Google Hack Database.
')
Why google?
Dorks are primarily focused on google for two reasons:
- the most flexible syntax of keywords (shown in Table 1) and special characters (shown in Table 2);
- google index is still more complete than other search engines;
Table 1 - Main google keywords
Table 2 - special characters google requests
It should be understood that any search engine query is a search by words only.
It is useless to search for meta-characters on the page (quotes, brackets, punctuation, etc.). Even search by exact phrase specified in quotes is a search by words, followed by search for exact match already in the results.
All Google Hack Database tracks are divided logically into 14 categories and are presented in table 3.
Table 3 - Google Hack Database Categories
Dorks are more often focused on searching all the Internet sites. But nothing prevents to limit the search area on any site or sites.
Each request to google can be focused on a specific site by adding the keyword "site: somesite.com" to the request. This keyword can be added to any roadmap.
Automate the search for vulnerabilities
So the idea was born to write a simple utility that automates the search for vulnerabilities using a search engine (google) and based on the Google Hack Database.
The utility is a script written on nodejs using phantomjs. To be precise, the script is interpreted by phantomjs itself.
Phantomjs is a full-fledged web browser without a graphical interface, managed by js-code and has a convenient API.
The utility has received quite understandable name - dorks. By running it on the command line (without options), we get a short help with a few examples of use:

Figure 1 - A list of the main options dorks
The general syntax of the utility: dork "command" "list of options."
A detailed description of all options is presented in Table 4.
Table 4 - Syntax dorks
Using the ghdb command, you can get all the tracks with exploit-db on an arbitrary request, or specify the entire category. If you specify a category of 0, then the entire base will be unloaded (about 4.5 thousand Dorks).
The list of categories currently available is presented in Figure 2.
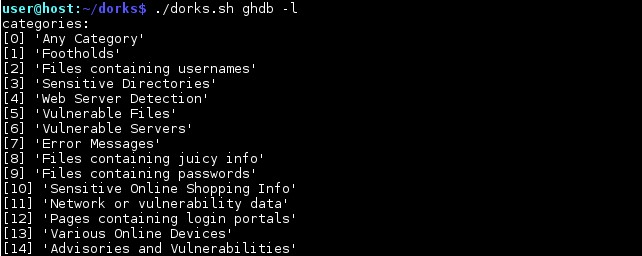
Figure 2 - A list of available categories of GHDB Dorks
The google team will make the substitution of each dork into a google search engine and analyze the result for matches. Dorks on which something was found will be saved to a file.
The utility supports different search modes:
• 1 dork and 1 website;
• 1 dork and many sites;
• 1 site and many dorkov;
• many sites and many dorkov;
The list of dorks and sites can be specified both through an argument or through a file.
Demonstration of work
Let's try to look for any vulnerabilities using the example of searching for error messages. By the command: dorks ghdb –c 7 –o errors.dorks all known “Error Messages” category tracks will be loaded as shown in Figure 3.
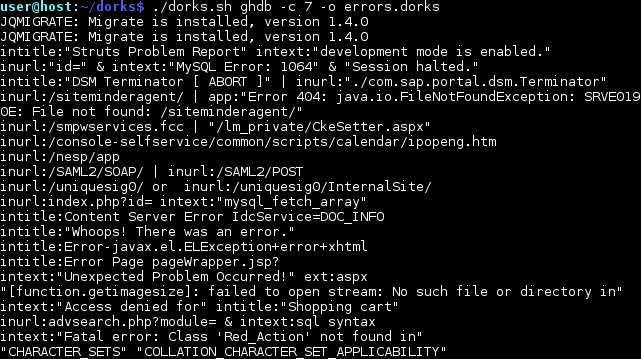
Figure 3 - Download all known Dorks category “Error Messages”
The tracks are uploaded and saved to a file. It now remains to "incite" them to any site (see Figure 4).

Figure 4 - Search for vulnerabilities of the interested site in the google cache
After some time, several pages containing errors are found on the site under study (see Figure 5).

Figure 5 - Error Messages Found
The result, in the file result.txt we get the full list of dorks that lead to the appearance of an error.
Figure 6 shows the result of a site error search.
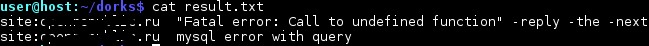
Figure 6 - Result of finding errors
The cache on this track displays a full backtrace, revealing the absolute paths of the scripts, the content management system, and the type of database (see Figure 7).
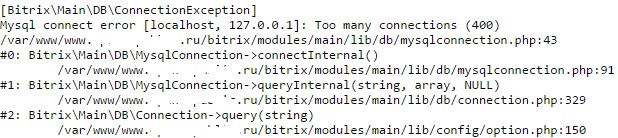
Figure 7 - Disclosure of Site Device Information
However, it should be borne in mind that not all the tracks from GHDB give a true result. Also, google may not find an exact match and show a similar result.
In this case, it is wiser to use your personal list of dorks. For example, you should always look for files with “unusual” extensions, examples of which are shown in Figure 8.
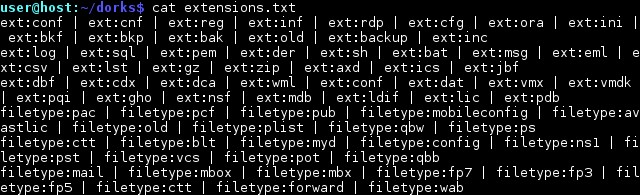
Figure 8 - A list of file extensions that are not typical for a regular web resource
As a result, at the command of dorks google –D extensions.txt –f bank, from the very first request google begins to give away sites with “unusual” file extensions (see Figure 9).

Figure 9 - Search for “bad” file types on banking sites
It should be borne in mind that google does not accept requests longer than 32 words.
Using the dorks google –d intext command: ”error | warning | notice | syntax” –f university
You can search for PHP interpreter errors on the training sites (see Figure 10).
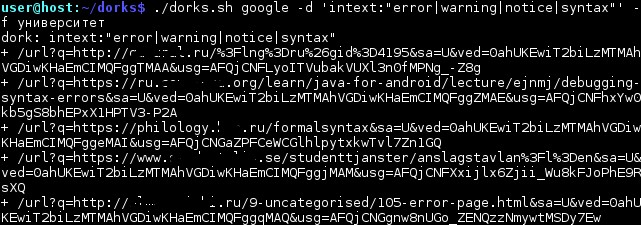
Figure 10 - Search for PHP runtime errors
Sometimes it’s not convenient to use any one or two categories of dorks.
For example, if it is known that the site is powered by the wordpress engine, then wordpress docs are needed. In this case, it is convenient to use the Google Hack Database search. The dorks ghdb –q wordpress –o command wordpress_dorks.txt will load all the docs for Wordpress, as shown in Figure 11:
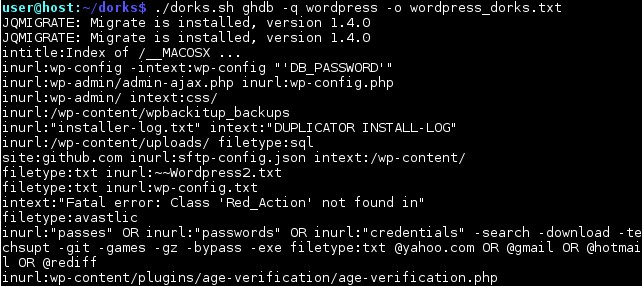
Figure 11 - Search dorks related to Wordpress
Let's go back to the banks again and use the dorks google –D wordpress_dords.txt –f command to try to find something interesting related to wordpress (see Figure 12).

Figure 12 - Wordpress Vulnerability Scan
It is worth noting that a search on Google Hack Database does not perceive words shorter than 4 characters. For example, if the CMS site is not known, but the language is known - PHP. In this case, you can manually filter the necessary one with the help of the pipe and the dorks –c all | system search utility. findstr / I php> php_dorks.txt (see figure 13):

Figure 13 - Search all roads where PHP is mentioned
Search for vulnerabilities or some sensitive information in a search engine should be searched only if there is a significant index on this site. For example, if the site has 10-15 pages indexed, then it is foolish to look for something in this way. Check the size of the index is simple - just enter in the search box google "site: somesite.com". An example of a site with an insufficient index is shown in Figure 14.

Figure 14 - Checking the size of the site index
Now about the unpleasant ... Periodically google can request a captcha - there's nothing to be done about it - it will have to be entered. For example, in my case, when searching the category “Error Messages” (90 dorks), the captcha fell out only once.
It is worth adding that phantomjs supports work in the same way through a proxy, both via http and through socks interface. To enable proxy mode, you need to uncomment the corresponding line in dorks.bat or dorks.sh.
The tool is available as github.com/USSCltd/dorks source code and requires only phantomjs for its work.
Intelligence can be both active - brutfors files and directories of the site, launch vulnerability scanners, manual viewing of the site, and passive - search for information in different search engines. Sometimes it happens that the vulnerability becomes known even before the opening of the first page of the site.
How is this possible?
Search robots, without stopping roaming the Internet, in addition to information useful to the average user, often fix what can be used by attackers when attacking a web resource. For example, script errors and files with sensitive information (starting from configuration files and logs, ending with files with authentication data and database backups).
From the point of view of the search robot, the error message about the execution of the sql query is plain text, inseparable, for example, from the description of the goods on the page. If suddenly the search robot came across a file with the extension .sql, which for some reason turned out to be in the working folder of the site, it will be perceived as part of the content of the site and will also be indexed (including, possibly, the passwords specified in it).
Such information can be found knowing well-established, often unique, keywords that help separate “vulnerable pages” from pages that do not contain vulnerabilities.
A huge database of special requests using keywords (called dorks) exists on exploit-db.com and is known as the Google Hack Database.
')
Why google?
Dorks are primarily focused on google for two reasons:
- the most flexible syntax of keywords (shown in Table 1) and special characters (shown in Table 2);
- google index is still more complete than other search engines;
Table 1 - Main google keywords
| Keyword | Meaning | Example |
| site | Search only on the specified site. Only url | site: somesite.ru - will find all pages on this domain and subdomains |
| inurl | Search by words in uri. Unlike cl. words “site” looking for matches after site name | inurl: news - will find all the pages where this word will appear in the uri |
| intext | Search in the body of the page | intext: “traffic jams” - completely analogous to the usual query “traffic jams” |
| intitle | Search in the page header. Text enclosed between <title> tags | intitle: "index of" - will find all the pages with the directory listing |
| ext | Search for pages with the specified extension | ext: pdf - will find all pdf files |
| filetype | Currently, completely similar to Cl. the word “ext” | filetype: pdf - similar |
| related | Search sites with similar topics | related: google.ru - will show its counterparts |
| link | Search sites that link to this | link: somesite.ru - will find all sites that have a link to this |
| define | Show word definition | define: 0day - term definition |
| cache | Show cached content (if available) | cache: google.com - will open the page from the cache |
Table 2 - special characters google requests
| Symbol | Meaning | Example |
| “ | Exact phrase | intitle: “RouterOS router configuration page” - search for routers |
| * | Any text | inurl: “bitrix * mcart” - search sites on bitrix with the vulnerable module mcart |
| . | Any character | Index.of - similar to the query index of |
| - | Delete the word | error –warning - show all pages with error, but no warning |
| .. | Range | cve 2006..2016 - show vulnerabilities by year since 2006 |
| | | Logical "or" | linux | windows - show pages where either the first or the second word occurs |
It should be understood that any search engine query is a search by words only.
It is useless to search for meta-characters on the page (quotes, brackets, punctuation, etc.). Even search by exact phrase specified in quotes is a search by words, followed by search for exact match already in the results.
All Google Hack Database tracks are divided logically into 14 categories and are presented in table 3.
Table 3 - Google Hack Database Categories
| Category | What allows you to find | Example |
| Footholds | Web shells, public file managers | Find all the hacked sites where the listed web shell is flooded: (intitle: "phpshell" OR intitle: "c99shell" OR intitle: "r57shell" OR intitle: "PHP Shell" OR intitle: "phpRemoteView") `rwx`" uname " |
| Files containing usernames | Registry files, configuration files, logs, files containing the history of entered commands | Find all registry files containing account information: filetype: reg reg + intext: "internet account manager" |
| Sensitive directories | Directories with various information (personal documents, vpn configs, hidden repositories, etc.) | Find all listings of directories containing files related to vpn: "Config" intitle: "Index of" intext: vpn Sites containing git-repositories: (intext: "index of /.git") ("parent directory") |
| Web Server Detection | Version and other information about the web server | Find the JBoss server administrative consoles: inurl: "/ web-console /" intitle: "Administration Console" |
| Vulnerable Files | Scripts containing known vulnerabilities | Find sites that use a script that allows you to upload an arbitrary file from the server: allinurl: forcedownload.php? file = |
| Vulnerable Servers | Installation scripts, web shells, open administrative consoles, etc. | Find open PHPMyAdmin consoles running as root: intitle: phpMyAdmin "Welcome to phpMyAdmin ***" "running on * as root @ *" |
| Error Messages | Various errors and warnings often revealing important information - ranging from the CMS version to passwords | Sites that have errors in the execution of sql queries to the database: "Warning: mysql_query ()" "invalid query" |
| Files containing juicy info | Certificates, backups, emails, logs, sql scripts, etc. | Find initialization sql scripts: filetype: sql and "insert into" -site: github.com |
| Files containing passwords | All that may contain passwords - logs, sql-scripts, etc. | Logs mentioning passwords: filetype: log intext: password | pass | pw sql scripts containing passwords: ext: sql intext: username intext: password |
| Sensitive Online Shopping Info | Online Shopping Information | Find pincode: dcid = bn = pin code = |
| Network or vulnerability data | Information not directly related to the web resource, but affecting the network or other non-web services | Find automatic proxy configuration scripts containing information about the internal network: inurl: proxy | inurl: wpad ext: pac | ext: dat findproxyforurl |
| Pages containing login portals | Pages containing login forms | Web pages saplogon: intext: "2016 SAP AG. All rights reserved. "Intitle:" Logon " |
| Various Online Devices | Printers, routers, monitoring systems, etc. | Find printer configuration panel: intitle: " hp laserjet" inurl: SSI / Auth / set_ config_ deviceinfo. htm |
| Advisories and Vulnerabilities | Sites on vulnerable CMS versions | Find vulnerable plugins through which you can upload an arbitrary file to the server: inurl: fckeditor -intext: "ConfigIsEnabled = False" intext: ConfigIsEnabled |
Dorks are more often focused on searching all the Internet sites. But nothing prevents to limit the search area on any site or sites.
Each request to google can be focused on a specific site by adding the keyword "site: somesite.com" to the request. This keyword can be added to any roadmap.
Automate the search for vulnerabilities
So the idea was born to write a simple utility that automates the search for vulnerabilities using a search engine (google) and based on the Google Hack Database.
The utility is a script written on nodejs using phantomjs. To be precise, the script is interpreted by phantomjs itself.
Phantomjs is a full-fledged web browser without a graphical interface, managed by js-code and has a convenient API.
The utility has received quite understandable name - dorks. By running it on the command line (without options), we get a short help with a few examples of use:

Figure 1 - A list of the main options dorks
The general syntax of the utility: dork "command" "list of options."
A detailed description of all options is presented in Table 4.
Table 4 - Syntax dorks
| Team | Option | Description |
| ghdb | -l | Display a numbered list of Google Hack Database dork categories |
| -c "number or category name" | Download the tracks of the specified category by number or name | |
| -q "phrase" | Download tracks found on request | |
| -o "file" | Save result to file (only with -c | -q options) | |
| google | -d dork | Set a random dork (the option can be used many times; combination with the –D option is allowed) |
| -D "file" | Use dorks from file | |
| -s "site" | Set the site (the option can be used many times, the combination with the –S option is allowed) | |
| -S "file" | Use sites from file (brute force will be executed for each site independently) | |
| -f "filter" | Set additional keywords (will be added to each track) | |
| -t "number of ms" | Interval between requests to google | |
| -T "number of ms" | Timeout if captcha met | |
| -o "file" | Save the result to a file (only those tracks on which something was found will be saved) |
Using the ghdb command, you can get all the tracks with exploit-db on an arbitrary request, or specify the entire category. If you specify a category of 0, then the entire base will be unloaded (about 4.5 thousand Dorks).
The list of categories currently available is presented in Figure 2.

Figure 2 - A list of available categories of GHDB Dorks
The google team will make the substitution of each dork into a google search engine and analyze the result for matches. Dorks on which something was found will be saved to a file.
The utility supports different search modes:
• 1 dork and 1 website;
• 1 dork and many sites;
• 1 site and many dorkov;
• many sites and many dorkov;
The list of dorks and sites can be specified both through an argument or through a file.
Demonstration of work
Let's try to look for any vulnerabilities using the example of searching for error messages. By the command: dorks ghdb –c 7 –o errors.dorks all known “Error Messages” category tracks will be loaded as shown in Figure 3.

Figure 3 - Download all known Dorks category “Error Messages”
The tracks are uploaded and saved to a file. It now remains to "incite" them to any site (see Figure 4).

Figure 4 - Search for vulnerabilities of the interested site in the google cache
After some time, several pages containing errors are found on the site under study (see Figure 5).

Figure 5 - Error Messages Found
The result, in the file result.txt we get the full list of dorks that lead to the appearance of an error.
Figure 6 shows the result of a site error search.

Figure 6 - Result of finding errors
The cache on this track displays a full backtrace, revealing the absolute paths of the scripts, the content management system, and the type of database (see Figure 7).

Figure 7 - Disclosure of Site Device Information
However, it should be borne in mind that not all the tracks from GHDB give a true result. Also, google may not find an exact match and show a similar result.
In this case, it is wiser to use your personal list of dorks. For example, you should always look for files with “unusual” extensions, examples of which are shown in Figure 8.

Figure 8 - A list of file extensions that are not typical for a regular web resource
As a result, at the command of dorks google –D extensions.txt –f bank, from the very first request google begins to give away sites with “unusual” file extensions (see Figure 9).

Figure 9 - Search for “bad” file types on banking sites
It should be borne in mind that google does not accept requests longer than 32 words.
Using the dorks google –d intext command: ”error | warning | notice | syntax” –f university
You can search for PHP interpreter errors on the training sites (see Figure 10).

Figure 10 - Search for PHP runtime errors
Sometimes it’s not convenient to use any one or two categories of dorks.
For example, if it is known that the site is powered by the wordpress engine, then wordpress docs are needed. In this case, it is convenient to use the Google Hack Database search. The dorks ghdb –q wordpress –o command wordpress_dorks.txt will load all the docs for Wordpress, as shown in Figure 11:

Figure 11 - Search dorks related to Wordpress
Let's go back to the banks again and use the dorks google –D wordpress_dords.txt –f command to try to find something interesting related to wordpress (see Figure 12).

Figure 12 - Wordpress Vulnerability Scan
It is worth noting that a search on Google Hack Database does not perceive words shorter than 4 characters. For example, if the CMS site is not known, but the language is known - PHP. In this case, you can manually filter the necessary one with the help of the pipe and the dorks –c all | system search utility. findstr / I php> php_dorks.txt (see figure 13):

Figure 13 - Search all roads where PHP is mentioned
Search for vulnerabilities or some sensitive information in a search engine should be searched only if there is a significant index on this site. For example, if the site has 10-15 pages indexed, then it is foolish to look for something in this way. Check the size of the index is simple - just enter in the search box google "site: somesite.com". An example of a site with an insufficient index is shown in Figure 14.

Figure 14 - Checking the size of the site index
Now about the unpleasant ... Periodically google can request a captcha - there's nothing to be done about it - it will have to be entered. For example, in my case, when searching the category “Error Messages” (90 dorks), the captcha fell out only once.
It is worth adding that phantomjs supports work in the same way through a proxy, both via http and through socks interface. To enable proxy mode, you need to uncomment the corresponding line in dorks.bat or dorks.sh.
The tool is available as github.com/USSCltd/dorks source code and requires only phantomjs for its work.
Source: https://habr.com/ru/post/283210/
All Articles