Attackers use a set of exploits for cyber attacks on Android users
Specialists of the well-known company Blue Coat have discovered an exploit kit, which is used by attackers to automatically install malware (drive-by download) on smartphones running an outdated version of Android. Automatic installation of an ransomware program called Cyber.Police is achieved by using two exploits: the first is similar to an exploit from the leaked Hacking Team source code archive (Android library libxslt), and the second one is called Towelroot , which allows you to bypass Android security mechanisms and get root privileges on device.

The cyber attack vector is a malicious website with a special JavaScript code exploit libxslt, which initiates a drive-by download. After that, the owner of the device is loaded with a modification of the Towelroot exploit, which allows him to get maximum root privileges on Android ( CVE-2014-3153 ). The first drive-by exploit is relevant for users of Android versions from 4.0.3 to 4.4.4. During the first exploit, as well as the installation of the malicious application, Android does not display any warnings or notifications to the user. ESET anti-virus products detect Towelroot LPE exploit as Android / Exploit.Towel.F .
')
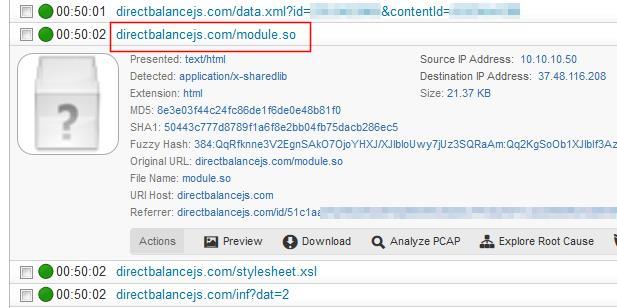
Fig. Information about the Towelroot exploit file (module.so), which is loaded by the libxslt drive-by exploit. ( Blue Coat data )
Users of older versions of Android should consider the relevance of such a mechanism to compromise their device. You should also take into account the fact that manufacturers of outdated models of devices running such Android versions do not release updates for them, which means that users will not be able to correct this situation and will remain potential victims of the above-described scheme of intruders.
Blue Coat specialists were able to detect 224 unique models of devices that were infected with a similar scheme. All of them were running Android versions from 4.0.3 to 4.4.4.

Fig. The screen of the user's device blocked by the extortionist. ( Blue Coat data )
An extortionist installed by exploits is called Cyber.Police and intimidates users with a warning from law enforcement. The lock screen displays the device name, IP address, country of location, and Android version. Extortionist does not encrypt data on the device, but simply locks its screen, leaving the user with no opportunity to work with it. Detected by ESET antivirus products like Android / Locker.HR .
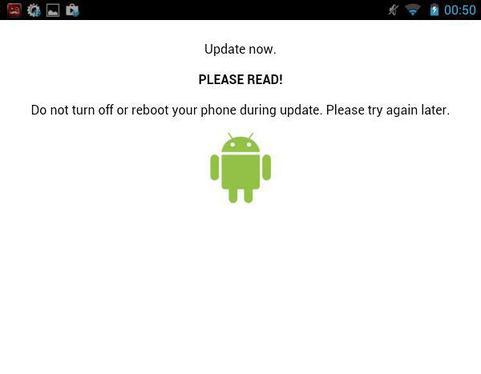
Fig. A message that is displayed by a malware to the user immediately after its installation. The actions of the extortionist are disguised as a legitimate Android update. ( Blue Coat data )
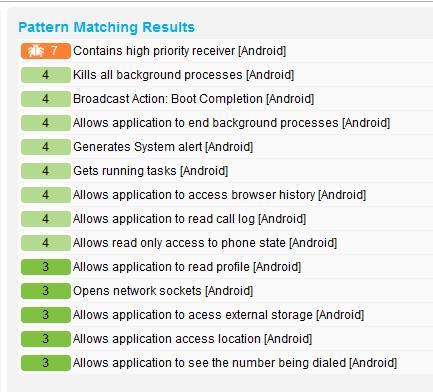
Fig. A list of ransomware system functions Android. It can be seen that the application specializes in killing other processes, opening network sockets, as well as obtaining various information about the device. ( Blue Coat data )
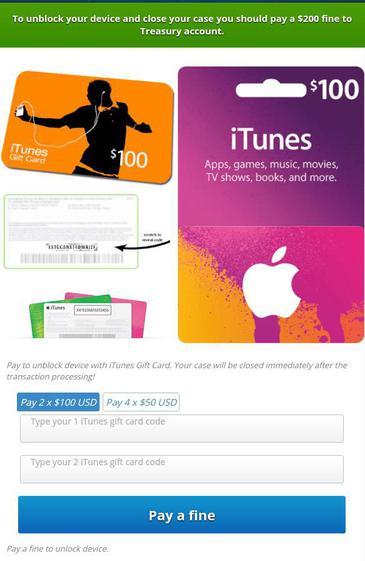
Fig. Information about paying a ransom of $ 200, payment is made using iTunes gift cards. This payment mechanism distinguishes this extortionist from others, since in their case payment is made using bitcoins. ( Blue Coat data )

Fig. Information about gift cards iTunes, which displays the extortionist. ( Blue Coat data )
In such cases of malware infection, we recommend making timely backup copies of the data stored on the device, so that in the future you can safely reset the device and restore the user data on it. For Android users, it is also relevant to install released updates on it. Google updates Android at least once a month, which allows it to quickly close the detectable vulnerabilities in this mobile OS. Information about vulnerabilities that Google closes regularly appears on our blog. We also recommend using antivirus software for Android, our ESET Mobile Security antivirus product successfully detects the exploit used by hackers, as well as the malware itself.

The cyber attack vector is a malicious website with a special JavaScript code exploit libxslt, which initiates a drive-by download. After that, the owner of the device is loaded with a modification of the Towelroot exploit, which allows him to get maximum root privileges on Android ( CVE-2014-3153 ). The first drive-by exploit is relevant for users of Android versions from 4.0.3 to 4.4.4. During the first exploit, as well as the installation of the malicious application, Android does not display any warnings or notifications to the user. ESET anti-virus products detect Towelroot LPE exploit as Android / Exploit.Towel.F .
')

Fig. Information about the Towelroot exploit file (module.so), which is loaded by the libxslt drive-by exploit. ( Blue Coat data )
Users of older versions of Android should consider the relevance of such a mechanism to compromise their device. You should also take into account the fact that manufacturers of outdated models of devices running such Android versions do not release updates for them, which means that users will not be able to correct this situation and will remain potential victims of the above-described scheme of intruders.
Blue Coat specialists were able to detect 224 unique models of devices that were infected with a similar scheme. All of them were running Android versions from 4.0.3 to 4.4.4.

Fig. The screen of the user's device blocked by the extortionist. ( Blue Coat data )
An extortionist installed by exploits is called Cyber.Police and intimidates users with a warning from law enforcement. The lock screen displays the device name, IP address, country of location, and Android version. Extortionist does not encrypt data on the device, but simply locks its screen, leaving the user with no opportunity to work with it. Detected by ESET antivirus products like Android / Locker.HR .

Fig. A message that is displayed by a malware to the user immediately after its installation. The actions of the extortionist are disguised as a legitimate Android update. ( Blue Coat data )

Fig. A list of ransomware system functions Android. It can be seen that the application specializes in killing other processes, opening network sockets, as well as obtaining various information about the device. ( Blue Coat data )

Fig. Information about paying a ransom of $ 200, payment is made using iTunes gift cards. This payment mechanism distinguishes this extortionist from others, since in their case payment is made using bitcoins. ( Blue Coat data )

Fig. Information about gift cards iTunes, which displays the extortionist. ( Blue Coat data )
In such cases of malware infection, we recommend making timely backup copies of the data stored on the device, so that in the future you can safely reset the device and restore the user data on it. For Android users, it is also relevant to install released updates on it. Google updates Android at least once a month, which allows it to quickly close the detectable vulnerabilities in this mobile OS. Information about vulnerabilities that Google closes regularly appears on our blog. We also recommend using antivirus software for Android, our ESET Mobile Security antivirus product successfully detects the exploit used by hackers, as well as the malware itself.
Source: https://habr.com/ru/post/282886/
All Articles