PHDays VI member stories: how Moxy Marlinspike defeated the FBI, and John Bambenek figured out hacker No. 1
In early April, all the major publications in the world wrote about Moxie Marlinspike. A billion of WhatsApp users received mandatory end-to-end traffic encryption based on the algorithms of its messenger Signal. In a month, on May 17 and 18, Moxie will be available on the PHDays VI forum. Not only he, but also Rahul Sasi, Paul Vixie, Andrei Masalovich, John Bambenek, will speak at the event.

At birth in 1980, Moxie was named Matthew Rosenfeld. In the late 90s he moved to San Francisco. The sea and hacking are the two main passions of a man who chose the pseudonym Moksi Marlinspike. Marlinspike means rigging for punching the strands of the cable, and Moxie means courage.
')
The personal site of Marlinspike is not accidentally called the Orwellian term thoughtcrime.org (“thought crime”). After the development in 2009 of the WPA Cracker online service and the MitM SSL attacks, stripping intelligence services began to give Moxie increased attention. At airports, he became the object of particularly close "additional screening." A little later, his mobile number was found in the contacts of Jacob Appelbaum, a WikiLeaks activist, and the pressure on Moxie increased. Once, Moxie was held for several hours at the airport, confiscating all the devices.
Intelligence agencies seem to have in vain angered Marlinspike. In 2010, he and Stuart Anderson created Whisper Systems. The products of the new company - TextSecure protected messaging system and RedPhone call encryption program - have earned high marks from specialists. Utilities were free, unlike most analogs, and worked well. But in 2011, the company was sold on Twitter and the development stalled. Marlinspike left for the position of head of the information security department.
After leaving Twitter after a year and a half, Marlinspike reanimated his brainchild by organizing the non-profit organization Open Whisper Systems and continuing to develop TextSecure and RedPhone. Fortunately, Twitter didn’t put a stick in the wheels and allowed to make applications publicly available.
Today, both products are replaced by Signal messenger, released on iOS and Android. Signal is recommended not only by the Edward Snowden, but also by the human rights organization Electronic Frontier Foundation. In the EFF rankings, he scored seven points out of seven, which makes him one of the safest. For comparison, Skype has one point in this table, Viber has two, ordinary Telegram chats have four, and seven have secret chats.
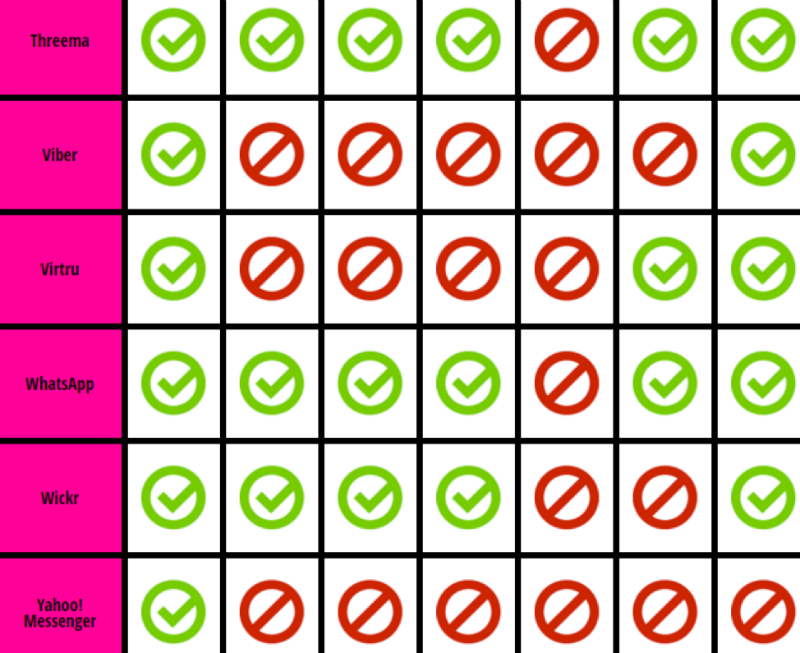
In December 2015, Pavel Durov, responding to the criticism of Snowden and Marlinspike about the lack of security of standard correspondence in Telegram, stated that the average user of his messenger prefers synchronization to encryption. The secret chats have the encryption key on the device, not on the remote server, so they cannot be synchronized via the cloud.
Until November 2014, WhatsApp had two out of seven points in the EEF rating, and after starting cooperation with Open Whisper Systems, it was six out of seven. Not everyone was happy. Barack Obama called it a “problem,” and British Prime Minister David Cameron promised to ban WhatsApp if he wins the election. Since April 5, 2016, end-to-end encryption has been working for all WhatsApp users. Now the owners of the messenger, even if desired, can not give anything to the special services. No video, no voice traffic, no correspondence, no photos.
When young people ask Moxie about the first steps in a software developer’s career, he advises them not to rush. “My friend,” wrote Moxy in 2011 at Slashdot , “recently joked: most programmers learned about technology before they knew themselves. If you are young, spend a year of your life experimenting in which much of your life will be focused on discoveries, not on earning. Take musical instruments with your friends, learn three chords and go on tour. Find an abandoned boat and cross the ocean. Hitchhike to Alaska. Build a fleet of airships or drone. "

The drone loves another PHDays VI member - Rahul Sasi. In the film "Interstellar" the main character with his daughter intercepts the management of the UAV; Rahul does about the same thing. In 2015, he developed the Maldrone backdoor for hijacking Parrot AR.Drone 2.0 quadcopters and DJI Phantom. Working in conjunction with the Skyjack exploit, the Maldrone virus allows you to steal the drones themselves, intercept the video signal from the captured devices and even create a flying army infecting nearby drones. By the end of 2016, the number of only American UAVs will reach 2.5 million, which makes you look closely at the research of Rahul.
On PHDays IV, Rahul Sacy will talk about his other project - the creation of an automated security system based on artificial intelligence. Most traditional web application security scanners are unable to detect logical security errors. The speaker will demonstrate how to create a tool for identifying such errors based on machine learning technologies. Some details of the project can be found in an article published in The Register.

Black hats hit not only for the strong and the rich. In the announcement of his performance on BlackHat, John Bambenek (John Bambenek) described the tragedy that occurred in March 2014 in Romania. The extortionist program demoralized the user to such an extent that he killed himself and his 4-year-old son. The man who picked up the “policeman” virus on the adult site took for granted the message that he would face a huge fine or imprisonment for 11 years.
In an interview with The News Gazette, Bambenek said that he considered participation in the Tovar operation as his main professional achievement. In June 2014, 150 specialists from 13 countries were able to find the organizer of one of the most dangerous hacker groups in history - Evgenia Bogachev a. A native of Anapa, known under the pseudonym of lucky12345 and slavik, stole about $ 100 million from citizens and US companies. He is also credited with developing the cryptoLocker extortionate software and creating the GameOver Zeus botnet. “Bogachev and his team committed cybercrimes that cannot be imagined even in science fiction films,” said the prosecutor involved in the investigation of the case. In 2016, the FBI included Bogachev in the list of the most wanted cybercriminals, with the highest reward ($ 3 million) awarded to a Russian.
The 38-year-old Bambenek began writing computer programs at the age of 6 years. He conducted his first hacker research before entering college. The study was paid for by the US Air Force, where John planned to pursue a career after receiving a degree in astrophysics. However, a knee injury in a climbing trip, put an end to a career in the Air Force. The first major job for John was Ernst & Young, where he became the project manager (and, perhaps , went to the same dining room with the creator of WhatsApp, Jan Kum, who worked after the university in the department of information security Ernst & Young).
In addition to hunting for cybercriminals, Bambenek helps schoolchildren in Tanzania with the help of a charitable foundation organized by him, he loves steaks and brings up four children.
Moscow really liked John. He compared his visit to the city in 2015 (where he came to PHDays) with an explosion. We hope that participation in the forum in 2016 will be another unforgettable adventure for Bambenek. John will tell you how to identify intruders, using the features of the criminal network infrastructure that they create. Bambenek's advice on protection from ransomware viruses can be found on the SANS Technology Institute website.

Paul Vixie, the founder of Internet Systems Consortium, will also come to Moscow. For his pioneering achievements in 2014, he was included in the Internet Hall of Fame . There are only a few dozen names in this list!
Since 1980, Vixie has been developing Internet protocols and software architecture for UNIX systems. Created the Cron program (for BSD and Linux), is considered the main author and technical architect of the DNS server BIND 4.9 and BIND 8. He is the author and co-author of about a dozen RFC documents, mainly on DNS and similar topics. Received a PhD from Keio University for his work related to DNS and DNSSEC.
In his report, Vixie will show how to secure the DNS and use it to protect other objects on the local or global network. He will tell you about DNS cache substitution, security extensions for the DNS protocol (DNSSEC), DDoS attacks, transmission rate limiting, DNS firewall and passive DNS monitoring.

The speeches of Lieutenant Colonel FAPSI, retired Andrei Masalovich, are a little like typical reports on information security. This is a bright show, they can observe the exploitation of vulnerabilities on the Pentagon site or the fate of the secret Chinese aircraft carrier. “I’m not an Olympic champion, and not even a master - I’m, let's say, a first-ranking player,” he said in an interview with Forbes. But the stories of Masalovich are so fascinating that listeners are often asked to extend his speech (as it was on PHDays V).
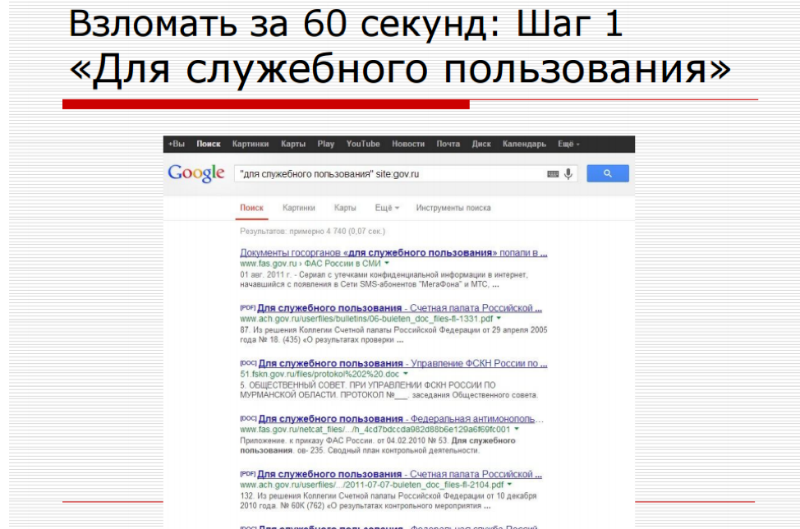
In 2014, Masalovich’s report “ Life after Snowden ” ranked second in social networks among several dozen PHDays IV reports. The slides with the “Documents” section of VKontakte, where anyone can find scans of other people's documents, enjoyed particular attention.
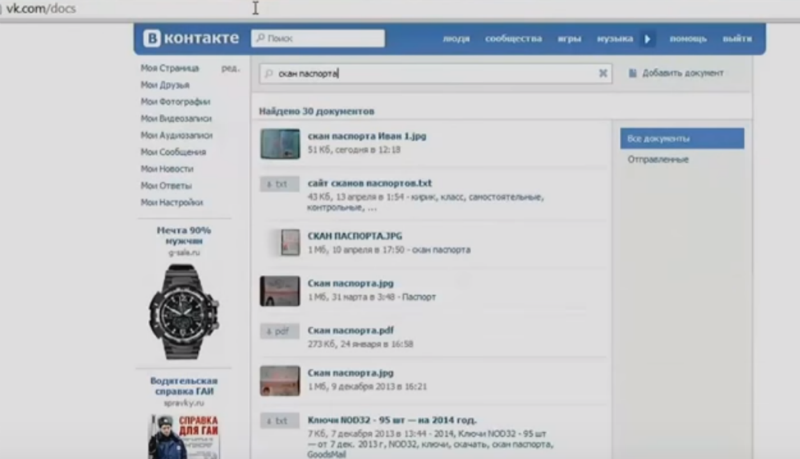
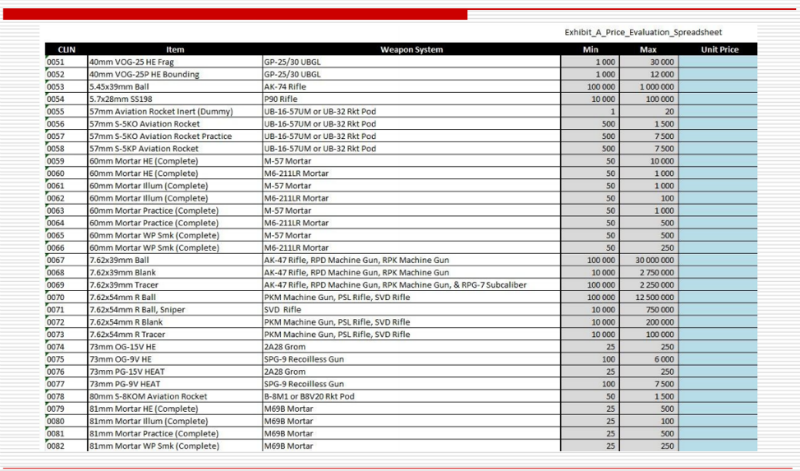
The study of the Pentagon’s tender documents right during the PHDays report did not go unnoticed by the American special services. The winner of the scholarship of the Russian Academy of Sciences "Outstanding Scientist of Russia" included in the base of the CIA as the head of a group of hackers named Leshy.
In the past two years, the main theme of speeches by Andrei Masalovich is the identification and prevention of harmful information impact. His report “The Survivor ” is one of the five most anticipated performances in the PHDays VI program. Andrei will talk about how information attacks are prepared, how to recognize them in the early stages and counter them. Analyzes the features of perception and dissemination of information in social networks using trolls and bots. Consider the method of express analysis of social portraits of participants in mass discussions - ordinary users, politicians, media people, teenagers, recruiters and their victims.
On May 17 and 18, Moxie Marlinspike, Rahul Sasi, Paul Vixie, Andrei Masalovich, John Bambenek and dozens of other information security experts will speak at the Positive Hack Days VI forum in Moscow. On the website phdays.ru you can familiarize yourself with the preliminary program of the event and choose the best way to get to the event.
Obama and Cameron vs. Marlinspike

At birth in 1980, Moxie was named Matthew Rosenfeld. In the late 90s he moved to San Francisco. The sea and hacking are the two main passions of a man who chose the pseudonym Moksi Marlinspike. Marlinspike means rigging for punching the strands of the cable, and Moxie means courage.
')
The personal site of Marlinspike is not accidentally called the Orwellian term thoughtcrime.org (“thought crime”). After the development in 2009 of the WPA Cracker online service and the MitM SSL attacks, stripping intelligence services began to give Moxie increased attention. At airports, he became the object of particularly close "additional screening." A little later, his mobile number was found in the contacts of Jacob Appelbaum, a WikiLeaks activist, and the pressure on Moxie increased. Once, Moxie was held for several hours at the airport, confiscating all the devices.
Intelligence agencies seem to have in vain angered Marlinspike. In 2010, he and Stuart Anderson created Whisper Systems. The products of the new company - TextSecure protected messaging system and RedPhone call encryption program - have earned high marks from specialists. Utilities were free, unlike most analogs, and worked well. But in 2011, the company was sold on Twitter and the development stalled. Marlinspike left for the position of head of the information security department.
After leaving Twitter after a year and a half, Marlinspike reanimated his brainchild by organizing the non-profit organization Open Whisper Systems and continuing to develop TextSecure and RedPhone. Fortunately, Twitter didn’t put a stick in the wheels and allowed to make applications publicly available.
Today, both products are replaced by Signal messenger, released on iOS and Android. Signal is recommended not only by the Edward Snowden, but also by the human rights organization Electronic Frontier Foundation. In the EFF rankings, he scored seven points out of seven, which makes him one of the safest. For comparison, Skype has one point in this table, Viber has two, ordinary Telegram chats have four, and seven have secret chats.

In December 2015, Pavel Durov, responding to the criticism of Snowden and Marlinspike about the lack of security of standard correspondence in Telegram, stated that the average user of his messenger prefers synchronization to encryption. The secret chats have the encryption key on the device, not on the remote server, so they cannot be synchronized via the cloud.
Until November 2014, WhatsApp had two out of seven points in the EEF rating, and after starting cooperation with Open Whisper Systems, it was six out of seven. Not everyone was happy. Barack Obama called it a “problem,” and British Prime Minister David Cameron promised to ban WhatsApp if he wins the election. Since April 5, 2016, end-to-end encryption has been working for all WhatsApp users. Now the owners of the messenger, even if desired, can not give anything to the special services. No video, no voice traffic, no correspondence, no photos.
When young people ask Moxie about the first steps in a software developer’s career, he advises them not to rush. “My friend,” wrote Moxy in 2011 at Slashdot , “recently joked: most programmers learned about technology before they knew themselves. If you are young, spend a year of your life experimenting in which much of your life will be focused on discoveries, not on earning. Take musical instruments with your friends, learn three chords and go on tour. Find an abandoned boat and cross the ocean. Hitchhike to Alaska. Build a fleet of airships or drone. "
Rahul Sacy: artificial intelligence from the drones hijacker

The drone loves another PHDays VI member - Rahul Sasi. In the film "Interstellar" the main character with his daughter intercepts the management of the UAV; Rahul does about the same thing. In 2015, he developed the Maldrone backdoor for hijacking Parrot AR.Drone 2.0 quadcopters and DJI Phantom. Working in conjunction with the Skyjack exploit, the Maldrone virus allows you to steal the drones themselves, intercept the video signal from the captured devices and even create a flying army infecting nearby drones. By the end of 2016, the number of only American UAVs will reach 2.5 million, which makes you look closely at the research of Rahul.
On PHDays IV, Rahul Sacy will talk about his other project - the creation of an automated security system based on artificial intelligence. Most traditional web application security scanners are unable to detect logical security errors. The speaker will demonstrate how to create a tool for identifying such errors based on machine learning technologies. Some details of the project can be found in an article published in The Register.
John Bambenek: how to find the criminal number 1

Black hats hit not only for the strong and the rich. In the announcement of his performance on BlackHat, John Bambenek (John Bambenek) described the tragedy that occurred in March 2014 in Romania. The extortionist program demoralized the user to such an extent that he killed himself and his 4-year-old son. The man who picked up the “policeman” virus on the adult site took for granted the message that he would face a huge fine or imprisonment for 11 years.
In an interview with The News Gazette, Bambenek said that he considered participation in the Tovar operation as his main professional achievement. In June 2014, 150 specialists from 13 countries were able to find the organizer of one of the most dangerous hacker groups in history - Evgenia Bogachev a. A native of Anapa, known under the pseudonym of lucky12345 and slavik, stole about $ 100 million from citizens and US companies. He is also credited with developing the cryptoLocker extortionate software and creating the GameOver Zeus botnet. “Bogachev and his team committed cybercrimes that cannot be imagined even in science fiction films,” said the prosecutor involved in the investigation of the case. In 2016, the FBI included Bogachev in the list of the most wanted cybercriminals, with the highest reward ($ 3 million) awarded to a Russian.
The 38-year-old Bambenek began writing computer programs at the age of 6 years. He conducted his first hacker research before entering college. The study was paid for by the US Air Force, where John planned to pursue a career after receiving a degree in astrophysics. However, a knee injury in a climbing trip, put an end to a career in the Air Force. The first major job for John was Ernst & Young, where he became the project manager (and, perhaps , went to the same dining room with the creator of WhatsApp, Jan Kum, who worked after the university in the department of information security Ernst & Young).
In addition to hunting for cybercriminals, Bambenek helps schoolchildren in Tanzania with the help of a charitable foundation organized by him, he loves steaks and brings up four children.
Moscow really liked John. He compared his visit to the city in 2015 (where he came to PHDays) with an explosion. We hope that participation in the forum in 2016 will be another unforgettable adventure for Bambenek. John will tell you how to identify intruders, using the features of the criminal network infrastructure that they create. Bambenek's advice on protection from ransomware viruses can be found on the SANS Technology Institute website.
Paul Vixie: DNS as a line of defense

Paul Vixie, the founder of Internet Systems Consortium, will also come to Moscow. For his pioneering achievements in 2014, he was included in the Internet Hall of Fame . There are only a few dozen names in this list!
Since 1980, Vixie has been developing Internet protocols and software architecture for UNIX systems. Created the Cron program (for BSD and Linux), is considered the main author and technical architect of the DNS server BIND 4.9 and BIND 8. He is the author and co-author of about a dozen RFC documents, mainly on DNS and similar topics. Received a PhD from Keio University for his work related to DNS and DNSSEC.
In his report, Vixie will show how to secure the DNS and use it to protect other objects on the local or global network. He will tell you about DNS cache substitution, security extensions for the DNS protocol (DNSSEC), DDoS attacks, transmission rate limiting, DNS firewall and passive DNS monitoring.
Andrei Masalovich: search for aircraft carrier in Google

The speeches of Lieutenant Colonel FAPSI, retired Andrei Masalovich, are a little like typical reports on information security. This is a bright show, they can observe the exploitation of vulnerabilities on the Pentagon site or the fate of the secret Chinese aircraft carrier. “I’m not an Olympic champion, and not even a master - I’m, let's say, a first-ranking player,” he said in an interview with Forbes. But the stories of Masalovich are so fascinating that listeners are often asked to extend his speech (as it was on PHDays V).

In 2014, Masalovich’s report “ Life after Snowden ” ranked second in social networks among several dozen PHDays IV reports. The slides with the “Documents” section of VKontakte, where anyone can find scans of other people's documents, enjoyed particular attention.

The study of the Pentagon’s tender documents right during the PHDays report did not go unnoticed by the American special services. The winner of the scholarship of the Russian Academy of Sciences "Outstanding Scientist of Russia" included in the base of the CIA as the head of a group of hackers named Leshy.

In the past two years, the main theme of speeches by Andrei Masalovich is the identification and prevention of harmful information impact. His report “The Survivor ” is one of the five most anticipated performances in the PHDays VI program. Andrei will talk about how information attacks are prepared, how to recognize them in the early stages and counter them. Analyzes the features of perception and dissemination of information in social networks using trolls and bots. Consider the method of express analysis of social portraits of participants in mass discussions - ordinary users, politicians, media people, teenagers, recruiters and their victims.
On May 17 and 18, Moxie Marlinspike, Rahul Sasi, Paul Vixie, Andrei Masalovich, John Bambenek and dozens of other information security experts will speak at the Positive Hack Days VI forum in Moscow. On the website phdays.ru you can familiarize yourself with the preliminary program of the event and choose the best way to get to the event.
Source: https://habr.com/ru/post/282209/
All Articles