IDS / IPS Suricata rule appearance statistics for new threats
Mandatory protection attribute for a large company - IDS / IPS (Intrusion Detection and Prevention System). There are a large number of commercial and open-source solutions on the market, and each of them has its advantages and disadvantages. But common to all solutions is the need for timely updating of the rules for detecting threats. Most IDS / IPSs allow you to use rules developed for Snort. One of the best-known rule providers is Emerging Threats, which has become part of Proofpoint.
We decided to collect release statistics for the pro (commercial version) and open (open-source version) sets of Emerging Threats for Suricata, since their syntax is similar to Snort, but at the same time it is slightly expanded, which gives more features.
From the rules.emergingthreats.net/changelogs page, the suricata and suricata-1.3 rule update logs have been compiled since 2015. The first thing that interested us was how many rules were issued to identify the exploitation of vulnerabilities. The rules for CVE, the rules of
To bind CVE to the rules, we
')
CVE-identifier can be contained both separately and in the msg field. From here, a CVE mapping for rules was obtained.
Since several similar rules may correspond to one attack, it was necessary to make a selection according to the uniqueness of the rules. The rules, slightly differing from each other by the msg field (having similarities greater than 0.99 according to the Jaro – Winkler algorithm), were not added to the sample. As a result, rules were selected that contain a mapping with CVE or one of the following markers in the msg field: attack response, exploit.

ET open statistics for 2015

The ratio of the rules of the ET open set for 2015
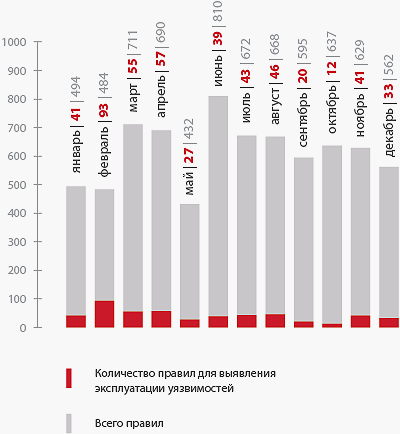
ET pro recruitment statistics for 2015
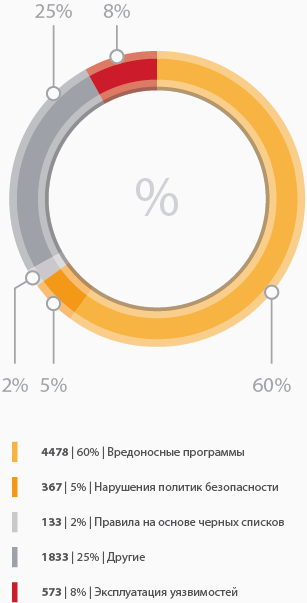
Ratio of rules from the ET pro set for 2015
As can be seen, in 2015 the number of rules issued to identify the exploitation of vulnerabilities did not exceed 10%. The largest area in the diagram is occupied by the rules for detecting the network activity of malicious programs.
The next step was to collect statistics covering the vulnerability regulations, published in 2015. Vulnerabilities with remote exploitation vector (AV: N) and CVSSv2-rating greater than 7.8 were selected. Of these, we selected those for which the rules were issued to identify the operation.
The diagram shows that only a small part of the vulnerabilities is covered by the rules. The first reason is that part of CVE is issued for cases that are impossible (encrypted traffic) or meaninglessly covered with rules (with detection and prevention of exploitation of vulnerabilities in web applications, WAF can cope better, for rules you will have to use cumbersome regular expressions, which will lead to slow down the system). The second reason is that details of the exploitation of a vulnerability are not always known, and experts do not have samples from which rules can be developed.
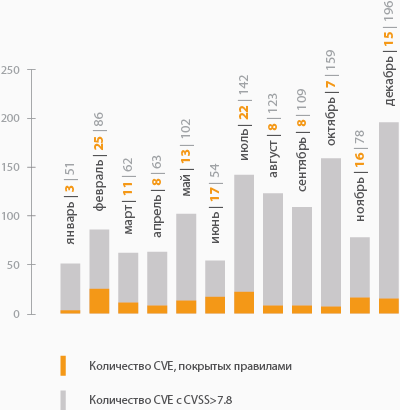
Vulnerability Coverage Statistics 2015
So, there is an acute shortage of rules for actual vulnerabilities. One of the reasons is the reluctance of vendors, as well as experts who find vulnerabilities and create rules for IDS / IPS, to share the technical details of the vulnerabilities found. The development of rules requires traffic patterns with exploitation of a vulnerability; if they exist, the coverage of new vulnerabilities by the rules will increase by several times, and the situation will not be so deplorable.
Posted by Alexey Lednev, Positive Technologies
We decided to collect release statistics for the pro (commercial version) and open (open-source version) sets of Emerging Threats for Suricata, since their syntax is similar to Snort, but at the same time it is slightly expanded, which gives more features.
From the rules.emergingthreats.net/changelogs page, the suricata and suricata-1.3 rule update logs have been compiled since 2015. The first thing that interested us was how many rules were issued to identify the exploitation of vulnerabilities. The rules for CVE, the rules of
attack response and exploit classes fall into this category. To bind CVE to the rules, we
sid-msg.map the current sid-msg.map file, as well as its change log. The file contains a mapping of sid-rules for their meta-information and has lines of the following form:')
2021138 || ET WEB_SERVER ElasticSearch Directory Traversal Attempt (CVE-2015-3337) || cve,2015-3337 2021139 || ET TROJAN H1N1 Loader CnC Beacon M1 || url,kernelmode.info/forum/viewtopic.php?f=16&t=3851 CVE-identifier can be contained both separately and in the msg field. From here, a CVE mapping for rules was obtained.
Since several similar rules may correspond to one attack, it was necessary to make a selection according to the uniqueness of the rules. The rules, slightly differing from each other by the msg field (having similarities greater than 0.99 according to the Jaro – Winkler algorithm), were not added to the sample. As a result, rules were selected that contain a mapping with CVE or one of the following markers in the msg field: attack response, exploit.

ET open statistics for 2015

The ratio of the rules of the ET open set for 2015

ET pro recruitment statistics for 2015

Ratio of rules from the ET pro set for 2015
As can be seen, in 2015 the number of rules issued to identify the exploitation of vulnerabilities did not exceed 10%. The largest area in the diagram is occupied by the rules for detecting the network activity of malicious programs.
The next step was to collect statistics covering the vulnerability regulations, published in 2015. Vulnerabilities with remote exploitation vector (AV: N) and CVSSv2-rating greater than 7.8 were selected. Of these, we selected those for which the rules were issued to identify the operation.
The diagram shows that only a small part of the vulnerabilities is covered by the rules. The first reason is that part of CVE is issued for cases that are impossible (encrypted traffic) or meaninglessly covered with rules (with detection and prevention of exploitation of vulnerabilities in web applications, WAF can cope better, for rules you will have to use cumbersome regular expressions, which will lead to slow down the system). The second reason is that details of the exploitation of a vulnerability are not always known, and experts do not have samples from which rules can be developed.

Vulnerability Coverage Statistics 2015
So, there is an acute shortage of rules for actual vulnerabilities. One of the reasons is the reluctance of vendors, as well as experts who find vulnerabilities and create rules for IDS / IPS, to share the technical details of the vulnerabilities found. The development of rules requires traffic patterns with exploitation of a vulnerability; if they exist, the coverage of new vulnerabilities by the rules will increase by several times, and the situation will not be so deplorable.
Posted by Alexey Lednev, Positive Technologies
Source: https://habr.com/ru/post/282029/
All Articles