Intel security hardware technology: a new word in the protection of biometric applications. Part one
Biometric technologies allow computers to recognize people by their unique characteristics. The progress in this area is impressive. What was previously known only in narrow scientific circles, today is available to everyone. Fingerprint scanner in a smartphone or in the workplace, for example, no one is surprised. At first glance, biometric authentication is a reliable barrier to outsiders. Indeed, there are not two people in the world who look alike in everything. But biometric applications that can reliably protect systems from intruders, also need protection.

Today we will talk about Intel hardware technologies that are able to take the protection of biometric applications to a new level.
The username and password have been used to identify users for many years. Under this security model, a person who needs to confirm that he has the right to use a certain service is enough to enter a name and password. This includes logging into the computer and accessing the functionality of various online services, such as social networks and online banks. The disadvantages of this security model are obvious for a variety of reasons. Here are some of them.
Login with password
In order to increase the strength of passwords to hacking and make life easier for users, more and more service providers are beginning to use biometric identification technologies to organize access to their systems. Thanks to these technologies, users do not need to remember passwords. For identification, voice, face, fingerprint or iris recognition is used. Biometric identification, in comparison with traditional security systems, has certain features.
The work of the biometric identity recognition system can be divided into five steps.
The scheme of the biometric recognition of users
In biometric authentication systems, the most valuable data for an attacker are user biometric templates. These templates can be presented in the form of raw data obtained from sensors, in the form of a set of characteristic features already stored in the original data stored in memory, in the form of registered biometric standards stored in a database.
In general, if a biometric application is designed without considering the need for proper data protection, an attacker can gain access to raw data or characteristic sets. This can be done during an attack while executing an application, using a rootkit or other malicious program. In addition, an attacker can use an attack when an application is not running, during which he is able to obtain biometric templates registered in the system if they are stored, for example, on a local disk.
Moreover, the attacker can intercept the flow of data on the data bus on the way from the sensor to the processor. Also, using a camera or microphone in the immediate vicinity of the user, an attacker can collect his biometric data, such as photographs of a person or voice recordings, in order to be used to perform a replay attack.
Types of attacks on the application of biometric recognition of users
From the point of view of developing a biometric identity recognition service, application design principles should provide end-to-end data protection in order to ensure the secure handling of confidential information. These principles include the following.
The Intel platform offers various hardware technologies to meet the security requirements of applications that perform user biometric verification. Consider three sets of Intel technologies aimed at solving this problem: Intel Software Guard Extensions, Intel Virtual Machine Extensions and Intel Identity Protection.
Biometric user identification technologies are being used more and more widely. The fact is that they provide an increased level of security. Since biometrics is based on the unique characteristics of a person: face, voice, fingerprints, iris, identification data is very difficult to steal. Biometric technologies take the place of traditional authentication methods using a password, they simplify and speed up the work.
However, with the widespread introduction of biometric technologies into various devices, the heterogeneity and openness of the platform led to the emergence of some potential threats. One of these threats is that developers need to consider how safe the work of biometric identification will be on various terminal devices. In particular, the following should be considered.
In order to design securely protected solutions, developers can use the technology of creating a trusted execution environment (Trusted Execution Environment, TEE).
TEE is an isolated, trusted execution environment for an application, separated from the usual, so-called “functionally rich execution environment” (Rich Execution Environment, REE). In accordance with the Global Platform TEE System Architecture specification , at the highest level, TEE is an environment that meets the following requirements.
Intel Software Guard Extensions (Intel SGX) allows developers to create and deploy secure applications on open platforms. These are new features of the Intel microprocessor architecture, including a set of new instructions and changes in the memory access mechanism.
Intel SGX works by allocating memory areas that store code and data that is protected at the hardware level. Protected areas of memory are called enclaves. Data stored in the enclave is available only to the code that is located in it. The code from the enclave can be invoked using special instructions. An enclave can be created and loaded as a Windows DLL.
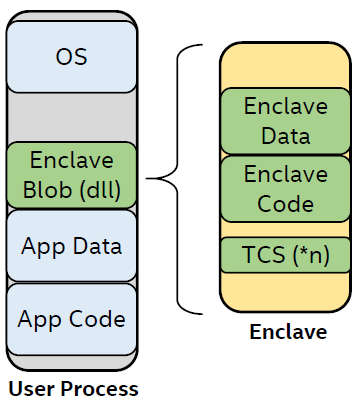
Secure runtime embedded in the process
According to the Intel SGX design model , applications using this technology consist of two parts: untrusted and trusted. When an application is executed, it calls the special instructions of the Intel SGX in order to create an enclave that is placed in a trusted area of memory. When a trusted function is called, the code is executed inside the enclave, unencrypted data is available only inside the enclave. Access to them from the outside is completely closed. After the trusted function completes, the enclave data will remain in the trusted memory.

The scheme of the application using Intel SGX
The purpose of the Intel SGX technology is to allow high-level protection of those parts of the application, access to which unauthorized persons should be completely excluded. In particular, the important data that the application operates are protected.
The attack surface, or trusted computing base (Trusted Computing Base, TCB), with this approach is reduced to the application itself and the processor on which its code is executed. Even malware that can bypass the operating system, VMM, BIOS, drivers, can not steal what the authors of the application want to keep secret.
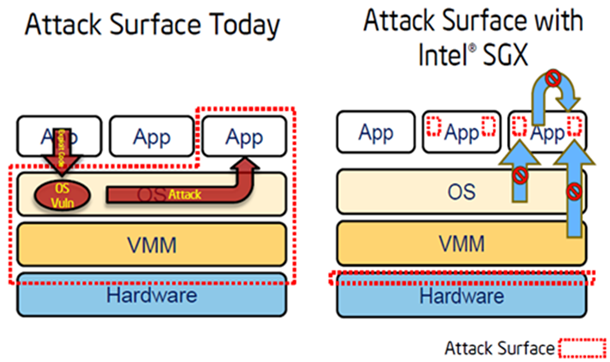
Reduced attack surface when using Intel SGX
Before we discuss the proposal to improve the security of biometric systems, we must pay attention to what needs to be protected.
The confidential data about the biometric characteristics of the user should be treated with care: are they processed in the application, are they stored on disk, are they sent to a remote service?
Modules for processing biometric data, including - obtaining samples, identifying characteristic features, search for matches, should be protected from computer viruses and other malicious software. In addition, it is necessary that the output of the system cannot be faked.
We offer an architectural solution, the scheme of which is shown below.

Implementation of a crack-resistant biometric system using Intel SGX
The subsystem that performs the acquisition, processing, and comparison of biometric data is located inside the Intel SGX Enclave, the trusted part of the client, and is responsible for handling the biometric data. Data leakage prevention and program integrity during its execution are guaranteed. Usually, such subsystems are implemented as software modules. And software implementations of anything can be hacked, for example - with the help of malware.
In the proposed architectural solution, the protected part of the application, containing the code and data, is loaded into the enclave. For both code and data, a procedure for calculating benchmarks, the so-called “measuring”, is performed. As soon as the application code and data are loaded into the enclave, they are protected from any external software access. Thus, the implementation of algorithms for processing biometric information can be considered trusted. At the same time, the proposed solution is distinguished by high speed and scalability associated with execution on the central processor. This is especially true for the implementation of those parts of biometric systems, which is important high performance. For example - for biometric data recognition functions.
Intel SGX technology offers a feature to encrypt and protect the integrity of the confidential contents of an enclave for storing it outside the enclave. For example - on disk, so that the application can reuse all this later. Data can be safely transferred between enclaves using the so-called Seal Key, a hardware key, with which this data can be “sealed”. The Seal Key is unique to the CPU and to the existing enclave environment. In combination with other services, such as Monotonic Counter or Trusted Time, which are provided by the software of the Intel SGX platform, this solution can be used to protect against various types of attacks.
Monotonic Counter can be used to implement a security policy designed to protect against replay attacks. Trusted Time can be used to enforce time-based security policies. Both that and another - in the form of "sealed" data (Sealed Data).
The enclave is responsible for performing encryption on the algorithm chosen for it. In other words, the developer can choose any encryption platform, in accordance with the system security requirements. Thus, we can provide user biometric data storage in the enclave and be sure that the raw biometric data will not be available outside the enclave, in the untrusted part of the application.
Sometimes a client implementation of biometric recognition needs to connect to a remote server to perform an authentication procedure using a cloud database, rather than local storage. The server can verify that it interacts with client software that has been correctly loaded and initialized on a platform that supports Intel SGX using an attestation mechanism. The same goes for biometric authentication. Within the framework of Intel SGX, this is the mechanism by which some part of the system can verify that within the enclave, on a platform that supports this functionality, it is safe to execute exactly the code that should be executed there.
To begin with, this module creates a report on the authenticity of the client part of the system, which can be checked, tied to a specific platform thanks to the data recorded in the CPU at the production stage. In addition, the report includes information about the user who performs the session of biometric recognition. The server checks the report to verify that it is interacting with a device that supports Intel SGX, and that the user has access to the system. The client and the server, at the first connection, conduct an initialization session, during which “sealed” secret data is safely transmitted to the client part of the system using the appropriate capabilities of the Intel SGX.
This data, which can only be printed by the application that sealed it, is used to establish secure connections to the server in the future, without the need to constantly authenticate the client platform. Such data includes “salt”, encryption key, security policy, certificate, and so on. After that, the data of biometric characteristics and the results of authentication can be transmitted via a secure communication channel between the client and the server.
Attacking dynamic data is one of the most common methodologies for attacking systems. This technique can be used by rootkits and other malware to intercept specified functions and create a copy of the data or modify them in memory during program execution. In the case of biometric recognition of users, the malicious code can receive biometric data taken from sensors and a biometric data template of a registered user from memory.
The traditional mechanism of software protection against unauthorized access to memory is not reliable enough. Both protected and malicious code are executed with the same privilege level (ring-0 or ring-3). Thus, malicious code can easily affect the protected code in order to disable protection.
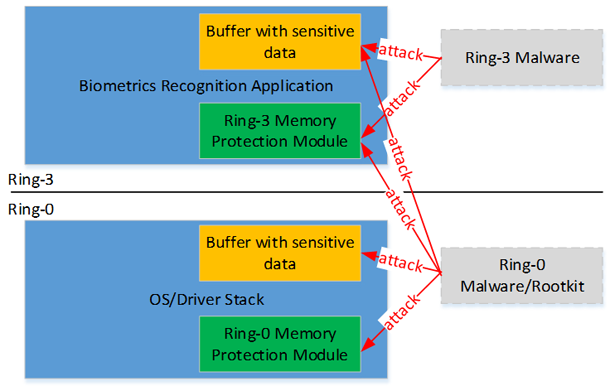
The attacker can affect the security module and access the buffer with sensitive information.
Virtual Machine Extensions (VMX) is a instruction set that supports the virtualization of processor hardware . The basic principle of his work is as follows.
This is how the relationship between the hardware, the operating system, and the application with VMX turned on and off looks like.
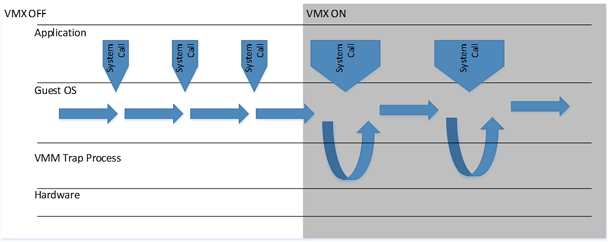
Various responses to system calls with VMX turned on and off
Using the VMX trap function, implemented on a hardware level, a memory protection mechanism based on hardware virtualization can provide faster and more secure memory protection than without using it. The basic idea here is to place a VMM-based memory monitoring module between the operating system and the hardware. When the application is loaded, a memory allocation table is created for areas containing trusted code and data. After building the table, during any memory access operation, VMM can intercept these operations, then compare the address of the memory access instruction (EIP) and the memory address in the previously constructed table. Then, the memory protection module can determine if this operation is valid and refer to the appropriate procedure.
Theft of personal data is a growing global problem that affects both individuals and companies. It requires an easy-to-use but safe solution, since hackers are constantly inventing ways to get user names and passwords. And they never stopped and will not stop searching for new methods to steal this data. If you are a client of some organization and interact with it via the Internet, or a regular computer user, Intel Identity Protection (Intel IPT) technology can give you powerful tools that will help you avoid the threat of personal data theft. In particular, we are talking about the possibility of binding the user's physical device to the accounts of services on the Internet that use the capabilities of Intel IPT.
Traditionally, one-time passwords (OTP) are used as part of two-factor authentication. Such a scheme combines what the user knows (username and password), and what he has (usually a token, a hardware security key, or a key fob that generates six-digit numbers that are valid only for a short period of time and are accessible by request).
In the case of using Intel IPT as part of the OTP technology, unique six-digit numbers, used only once, are generated every thirty seconds using an integrated processor that is protected from unauthorized access and isolated from the operating system. Since the identity is processed inside a protected physical device, it cannot be hacked using malware or deleted.

The use of Intel IPT technology in the interaction of the client and server, authentication based on a one-time password
If your company already uses two-factor authentication, you are familiar with various inconveniences and organizational problems that arise when using hardware tokens.
Intel IPT with OTP support is a hardware token embedded in the system chipset. In this case, the supplier of information security solutions can be chosen independently. The built-in token eliminates the use of a separate physical device, which simplifies, for example, a two-factor VPN connection procedure. At the same time Intel IPT works with almost no delays, simplifying and facilitating the daily work of users.
Through the use of Intel ITP technology with OTP support, Intel provides a hardware root of trust, proof of the authenticity of a specific device based on an Intel processor, various websites, financial institutions, network services. All these services receive an additional guarantee that the person who has the right to do so enters the account, and not the malicious program or the attacker. Systems using Intel IPT with OTP provide additional personal data protection and transaction verification methods that can be used in solutions that implement various multifactor authentication schemes.
We talked about how Intel SGX, VMX and IPT technologies can increase the security of biometric systems. But on this our story is not over. Next time, read about Intel AES-NI, Secure Key and Intel RealSense.

Today we will talk about Intel hardware technologies that are able to take the protection of biometric applications to a new level.
Advantages of biometrics over traditional security systems
The username and password have been used to identify users for many years. Under this security model, a person who needs to confirm that he has the right to use a certain service is enough to enter a name and password. This includes logging into the computer and accessing the functionality of various online services, such as social networks and online banks. The disadvantages of this security model are obvious for a variety of reasons. Here are some of them.
- Simple passwords, like “123456” or “hello” can be cracked by brute force or dictionary attack.
') - Difficult passwords are hard to remember.
- Many people use the same passwords in different systems.
- If someone forgets the password, then, after providing additional information about himself, he can reset the password.

Login with password
In order to increase the strength of passwords to hacking and make life easier for users, more and more service providers are beginning to use biometric identification technologies to organize access to their systems. Thanks to these technologies, users do not need to remember passwords. For identification, voice, face, fingerprint or iris recognition is used. Biometric identification, in comparison with traditional security systems, has certain features.
- Biometrics allows you to generate a long and complex password that offers a higher level of protection to counter the brute force attack.
- Biometric systems require developers to create more secure applications that are involved in the process of recognizing biometric information. The fact is that biological information is a part of the human body and cannot be easily changed. If the biometric information is stolen, it is not easy for the user to cancel his “biometric password”. An attacker, using stolen data, can create a copy of the body part of interest to him and, in the future, use it to pass biometric verification in other user accounts.
- Some biological characteristics, such as features of the face or voice, are characterized by a high level of false matches. As a result, user biometric recognition systems typically use a variety of characteristics to improve recognition accuracy.
- Some biometric characteristics of a person can be copied. For example, record a voice, print a photo, make a false finger from gelatin, silicone or latex with a fingerprint. It is important that the test module for survivability, that is, recognition of a person as a living object, be present in the biometric identification system. It is necessary for the system to be able to distinguish biometric information coming from a real person and fake.
How biometric identification works
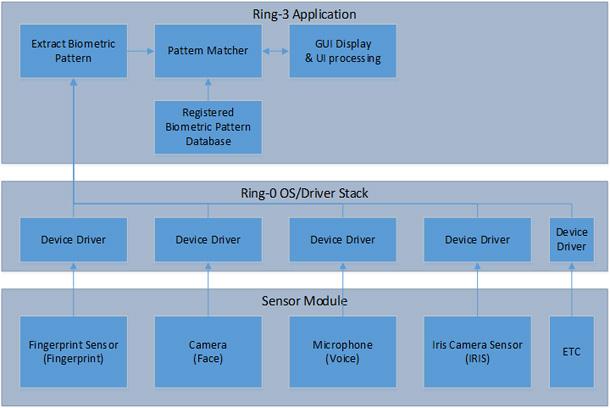
The work of the biometric identity recognition system can be divided into five steps.
- Biometric information is collected using sensors that are connected to a computer through an I / O port.
- The format and speed of data receipt is controlled by the device driver. The driver working with the Ring-0 privilege level processes the data, brings it into a form that meets the requirements of the operating system. The data is then sent to the biometric verification application, which is executed with the Ring-3 privilege level.
- As soon as the application receives the initial data, it performs their preliminary processing, extracting from them the characteristic features - biometric templates.
- The extracted templates are sent to the recognition system, which compares them with those registered in the database.
- As soon as a match is found, the recognition system sends a message about this (MATCH) to the main application. The user is notified of the successful login, he gets the opportunity to work with its closed resources.

The scheme of the biometric recognition of users
Attack model
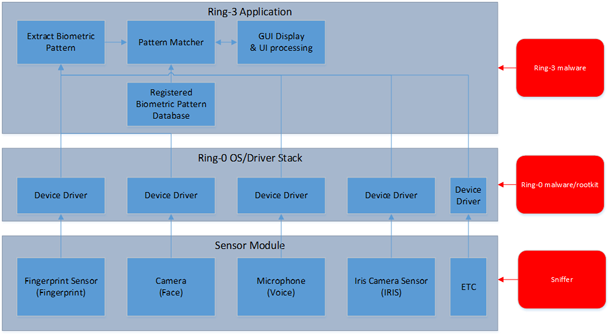
In biometric authentication systems, the most valuable data for an attacker are user biometric templates. These templates can be presented in the form of raw data obtained from sensors, in the form of a set of characteristic features already stored in the original data stored in memory, in the form of registered biometric standards stored in a database.
In general, if a biometric application is designed without considering the need for proper data protection, an attacker can gain access to raw data or characteristic sets. This can be done during an attack while executing an application, using a rootkit or other malicious program. In addition, an attacker can use an attack when an application is not running, during which he is able to obtain biometric templates registered in the system if they are stored, for example, on a local disk.
Moreover, the attacker can intercept the flow of data on the data bus on the way from the sensor to the processor. Also, using a camera or microphone in the immediate vicinity of the user, an attacker can collect his biometric data, such as photographs of a person or voice recordings, in order to be used to perform a replay attack.

Types of attacks on the application of biometric recognition of users
From the point of view of developing a biometric identity recognition service, application design principles should provide end-to-end data protection in order to ensure the secure handling of confidential information. These principles include the following.
- Providing a trusted execution environment for the application to preserve the integrity of its code.
- Protection of the memory area, which contains biometric templates, from other applications.
- Storing confidential data using cryptographic encryption methods. Encryption needs to be applied at all stages of working with such data. Namely, when they are in memory or in local storage, when data is exchanged with other applications running on the same computer or on a remote server.
Use of Intel hardware security technology in biometrics
The Intel platform offers various hardware technologies to meet the security requirements of applications that perform user biometric verification. Consider three sets of Intel technologies aimed at solving this problem: Intel Software Guard Extensions, Intel Virtual Machine Extensions and Intel Identity Protection.
Trusted Runtime Organization with Intel Software Guard Extensions
Biometric user identification technologies are being used more and more widely. The fact is that they provide an increased level of security. Since biometrics is based on the unique characteristics of a person: face, voice, fingerprints, iris, identification data is very difficult to steal. Biometric technologies take the place of traditional authentication methods using a password, they simplify and speed up the work.
However, with the widespread introduction of biometric technologies into various devices, the heterogeneity and openness of the platform led to the emergence of some potential threats. One of these threats is that developers need to consider how safe the work of biometric identification will be on various terminal devices. In particular, the following should be considered.
- How to safely execute on the end device modules for taking biometric samples, extracting characteristic features, comparing templates.
- How to secure the storage of biometric data templates.
- How to establish a secure communication channel between the end device and the cloud database of biological characteristics in order to perform the authentication procedure or other operations.
In order to design securely protected solutions, developers can use the technology of creating a trusted execution environment (Trusted Execution Environment, TEE).
Trusted application execution environment
TEE is an isolated, trusted execution environment for an application, separated from the usual, so-called “functionally rich execution environment” (Rich Execution Environment, REE). In accordance with the Global Platform TEE System Architecture specification , at the highest level, TEE is an environment that meets the following requirements.
- It is guaranteed that any code running inside the TEE is authentic and complete.
- The resources with which this code operates are protected from leaks. Namely, the trusted execution environment of applications must prevent all known types of attacks on software, performed locally or remotely, as well as some external attacks on hardware.
- The resources and code are protected from unauthorized tracing; the progress of the application cannot be affected externally using debugging and testing tools.
Intel Software Guard Extensions Technology Overview
Intel Software Guard Extensions (Intel SGX) allows developers to create and deploy secure applications on open platforms. These are new features of the Intel microprocessor architecture, including a set of new instructions and changes in the memory access mechanism.
Intel SGX works by allocating memory areas that store code and data that is protected at the hardware level. Protected areas of memory are called enclaves. Data stored in the enclave is available only to the code that is located in it. The code from the enclave can be invoked using special instructions. An enclave can be created and loaded as a Windows DLL.

Secure runtime embedded in the process
According to the Intel SGX design model , applications using this technology consist of two parts: untrusted and trusted. When an application is executed, it calls the special instructions of the Intel SGX in order to create an enclave that is placed in a trusted area of memory. When a trusted function is called, the code is executed inside the enclave, unencrypted data is available only inside the enclave. Access to them from the outside is completely closed. After the trusted function completes, the enclave data will remain in the trusted memory.

The scheme of the application using Intel SGX
The purpose of the Intel SGX technology is to allow high-level protection of those parts of the application, access to which unauthorized persons should be completely excluded. In particular, the important data that the application operates are protected.
The attack surface, or trusted computing base (Trusted Computing Base, TCB), with this approach is reduced to the application itself and the processor on which its code is executed. Even malware that can bypass the operating system, VMM, BIOS, drivers, can not steal what the authors of the application want to keep secret.

Reduced attack surface when using Intel SGX
Enhancing biometric application security with Intel SGX
Before we discuss the proposal to improve the security of biometric systems, we must pay attention to what needs to be protected.
The confidential data about the biometric characteristics of the user should be treated with care: are they processed in the application, are they stored on disk, are they sent to a remote service?
Modules for processing biometric data, including - obtaining samples, identifying characteristic features, search for matches, should be protected from computer viruses and other malicious software. In addition, it is necessary that the output of the system cannot be faked.
We offer an architectural solution, the scheme of which is shown below.

Implementation of a crack-resistant biometric system using Intel SGX
The subsystem that performs the acquisition, processing, and comparison of biometric data is located inside the Intel SGX Enclave, the trusted part of the client, and is responsible for handling the biometric data. Data leakage prevention and program integrity during its execution are guaranteed. Usually, such subsystems are implemented as software modules. And software implementations of anything can be hacked, for example - with the help of malware.
In the proposed architectural solution, the protected part of the application, containing the code and data, is loaded into the enclave. For both code and data, a procedure for calculating benchmarks, the so-called “measuring”, is performed. As soon as the application code and data are loaded into the enclave, they are protected from any external software access. Thus, the implementation of algorithms for processing biometric information can be considered trusted. At the same time, the proposed solution is distinguished by high speed and scalability associated with execution on the central processor. This is especially true for the implementation of those parts of biometric systems, which is important high performance. For example - for biometric data recognition functions.
Intel SGX technology offers a feature to encrypt and protect the integrity of the confidential contents of an enclave for storing it outside the enclave. For example - on disk, so that the application can reuse all this later. Data can be safely transferred between enclaves using the so-called Seal Key, a hardware key, with which this data can be “sealed”. The Seal Key is unique to the CPU and to the existing enclave environment. In combination with other services, such as Monotonic Counter or Trusted Time, which are provided by the software of the Intel SGX platform, this solution can be used to protect against various types of attacks.
Monotonic Counter can be used to implement a security policy designed to protect against replay attacks. Trusted Time can be used to enforce time-based security policies. Both that and another - in the form of "sealed" data (Sealed Data).
The enclave is responsible for performing encryption on the algorithm chosen for it. In other words, the developer can choose any encryption platform, in accordance with the system security requirements. Thus, we can provide user biometric data storage in the enclave and be sure that the raw biometric data will not be available outside the enclave, in the untrusted part of the application.
Sometimes a client implementation of biometric recognition needs to connect to a remote server to perform an authentication procedure using a cloud database, rather than local storage. The server can verify that it interacts with client software that has been correctly loaded and initialized on a platform that supports Intel SGX using an attestation mechanism. The same goes for biometric authentication. Within the framework of Intel SGX, this is the mechanism by which some part of the system can verify that within the enclave, on a platform that supports this functionality, it is safe to execute exactly the code that should be executed there.
To begin with, this module creates a report on the authenticity of the client part of the system, which can be checked, tied to a specific platform thanks to the data recorded in the CPU at the production stage. In addition, the report includes information about the user who performs the session of biometric recognition. The server checks the report to verify that it is interacting with a device that supports Intel SGX, and that the user has access to the system. The client and the server, at the first connection, conduct an initialization session, during which “sealed” secret data is safely transmitted to the client part of the system using the appropriate capabilities of the Intel SGX.
This data, which can only be printed by the application that sealed it, is used to establish secure connections to the server in the future, without the need to constantly authenticate the client platform. Such data includes “salt”, encryption key, security policy, certificate, and so on. After that, the data of biometric characteristics and the results of authentication can be transmitted via a secure communication channel between the client and the server.
Memory Protection with Virtual Machine Extensions
Attacking dynamic data is one of the most common methodologies for attacking systems. This technique can be used by rootkits and other malware to intercept specified functions and create a copy of the data or modify them in memory during program execution. In the case of biometric recognition of users, the malicious code can receive biometric data taken from sensors and a biometric data template of a registered user from memory.
The weakness of the traditional software mechanism of protection against unauthorized access to memory
The traditional mechanism of software protection against unauthorized access to memory is not reliable enough. Both protected and malicious code are executed with the same privilege level (ring-0 or ring-3). Thus, malicious code can easily affect the protected code in order to disable protection.

The attacker can affect the security module and access the buffer with sensitive information.
Memory Protection Based on Virtual Machine Extensions
Virtual Machine Extensions (VMX) is a instruction set that supports the virtualization of processor hardware . The basic principle of his work is as follows.
- Ignoring basic CPU operations, such as load / save, branch instructions, arithmetic and logical operations.
- Monitoring (trapping) privileged instructions, such as manipulating a memory control block, I / O instructions, or updating the associative translation buffer.
- If a privileged instruction is executed, interrupt execution and set the processor to VMX root mode for further processing.
This is how the relationship between the hardware, the operating system, and the application with VMX turned on and off looks like.

Various responses to system calls with VMX turned on and off
Using the VMX trap function, implemented on a hardware level, a memory protection mechanism based on hardware virtualization can provide faster and more secure memory protection than without using it. The basic idea here is to place a VMM-based memory monitoring module between the operating system and the hardware. When the application is loaded, a memory allocation table is created for areas containing trusted code and data. After building the table, during any memory access operation, VMM can intercept these operations, then compare the address of the memory access instruction (EIP) and the memory address in the previously constructed table. Then, the memory protection module can determine if this operation is valid and refer to the appropriate procedure.
Multi-factor authentication using Intel Identity Protection and one-time passwords
Theft of personal data is a growing global problem that affects both individuals and companies. It requires an easy-to-use but safe solution, since hackers are constantly inventing ways to get user names and passwords. And they never stopped and will not stop searching for new methods to steal this data. If you are a client of some organization and interact with it via the Internet, or a regular computer user, Intel Identity Protection (Intel IPT) technology can give you powerful tools that will help you avoid the threat of personal data theft. In particular, we are talking about the possibility of binding the user's physical device to the accounts of services on the Internet that use the capabilities of Intel IPT.
Traditionally, one-time passwords (OTP) are used as part of two-factor authentication. Such a scheme combines what the user knows (username and password), and what he has (usually a token, a hardware security key, or a key fob that generates six-digit numbers that are valid only for a short period of time and are accessible by request).
In the case of using Intel IPT as part of the OTP technology, unique six-digit numbers, used only once, are generated every thirty seconds using an integrated processor that is protected from unauthorized access and isolated from the operating system. Since the identity is processed inside a protected physical device, it cannot be hacked using malware or deleted.

The use of Intel IPT technology in the interaction of the client and server, authentication based on a one-time password
If your company already uses two-factor authentication, you are familiar with various inconveniences and organizational problems that arise when using hardware tokens.
Intel IPT with OTP support is a hardware token embedded in the system chipset. In this case, the supplier of information security solutions can be chosen independently. The built-in token eliminates the use of a separate physical device, which simplifies, for example, a two-factor VPN connection procedure. At the same time Intel IPT works with almost no delays, simplifying and facilitating the daily work of users.
Through the use of Intel ITP technology with OTP support, Intel provides a hardware root of trust, proof of the authenticity of a specific device based on an Intel processor, various websites, financial institutions, network services. All these services receive an additional guarantee that the person who has the right to do so enters the account, and not the malicious program or the attacker. Systems using Intel IPT with OTP provide additional personal data protection and transaction verification methods that can be used in solutions that implement various multifactor authentication schemes.
Results
We talked about how Intel SGX, VMX and IPT technologies can increase the security of biometric systems. But on this our story is not over. Next time, read about Intel AES-NI, Secure Key and Intel RealSense.
Source: https://habr.com/ru/post/281989/
All Articles