For the year, Google analyzed 760,000 hacking sites and announced a new tool to alert webmasters.
During the study, conducted from July 2014 to June 2015, Google employees identified 760,935 hacking facts of 313,190 sites, which the company identified as potentially dangerous for the user, as stated in the corresponding report . The collected statistics was used to develop a new notification system for webmasters, which will inform the latter about the hacking site.
The development was presented at the 25th International World Wide Web Consortium, in the same place where other Google employees announced their draft protocol for transferring data between web pages and USB devices .
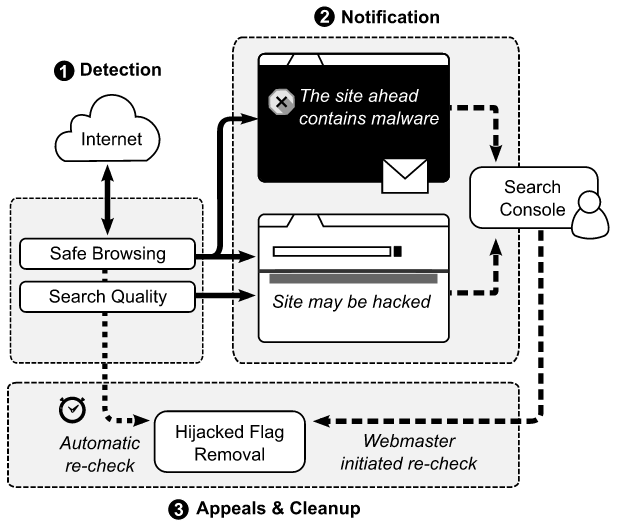
According to the company, in 75% of cases of direct communication with webmasters via e-mail, the latter promptly eliminated the effects of hacking and “cleaned” their sites. In cases where there was no contact information, “Browsing” was used - a browser notification that showed significantly less efficiency (only 54%).
')
With the standard "This site may harm your computer" alert, only 43% of resources were cleared.
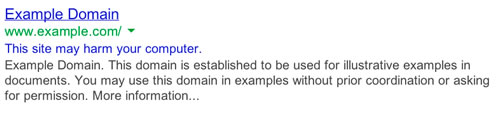
Self alert in search results. Not the most noticeable, frankly
The company also claims that it is possible to increase the effectiveness of “cleaning” hacked sites by providing recommendations on countering hackers (it increases the effectiveness of webmaster's actions by 62% and reduces the time to “clean” the site to, on average, three days).
Also, according to the statistics of the same Google, almost 12% of sites are subjected to infection again within just a month after recovery.
"To improve the efficiency of the cleaning process of web pages, we focus on three main points: advanced notifications for webmasters, which provide more precise information about the malware that infected a resource, equipping them with tools and preventive work, preventing information gaps resource ", noted in Google.
In the future, Google plans to warn webmasters about outdated software, to establish communication and promote additional measures of protection, such as, for example, the introduction of additional authentication.
The development was presented at the 25th International World Wide Web Consortium, in the same place where other Google employees announced their draft protocol for transferring data between web pages and USB devices .

According to the company, in 75% of cases of direct communication with webmasters via e-mail, the latter promptly eliminated the effects of hacking and “cleaned” their sites. In cases where there was no contact information, “Browsing” was used - a browser notification that showed significantly less efficiency (only 54%).
')
With the standard "This site may harm your computer" alert, only 43% of resources were cleared.

Self alert in search results. Not the most noticeable, frankly
The company also claims that it is possible to increase the effectiveness of “cleaning” hacked sites by providing recommendations on countering hackers (it increases the effectiveness of webmaster's actions by 62% and reduces the time to “clean” the site to, on average, three days).
Also, according to the statistics of the same Google, almost 12% of sites are subjected to infection again within just a month after recovery.
"To improve the efficiency of the cleaning process of web pages, we focus on three main points: advanced notifications for webmasters, which provide more precise information about the malware that infected a resource, equipping them with tools and preventive work, preventing information gaps resource ", noted in Google.
In the future, Google plans to warn webmasters about outdated software, to establish communication and promote additional measures of protection, such as, for example, the introduction of additional authentication.
Source: https://habr.com/ru/post/281985/
All Articles