Open Server-status in the Electronic Government of Kazakhstan or how to get a database of citizens
Earlier we reported on vulnerabilities on the portal of "Electronic Government" of Kazakhstan, the causes of which were developer errors. Now we want to talk about one vulnerability, the cause of which was not the developers, but rather the administrators. One “insignificant” detail, which can lead to colossal consequences and a repetition of the situation with Turkish citizens, when the entire base of the Turkish population was laid out online.
The error described in this article was transmitted to the developers of the ES and corrected; accordingly, the exploitation of the vulnerability is no longer possible. In view of this, we believe this publication will not entail the leakage of anyone's personal data. But we can not guarantee that the documents of our citizens were no longer received by the attackers and were not saved for any action.
So, on the e-government portal, when requesting this or that help, the user receives a direct link to the document in * .PDF format, which looks like this:
')
The admin error is the overall availability of Server Status, which in turn reveals all transmitted GET requests (shown in the figure below).
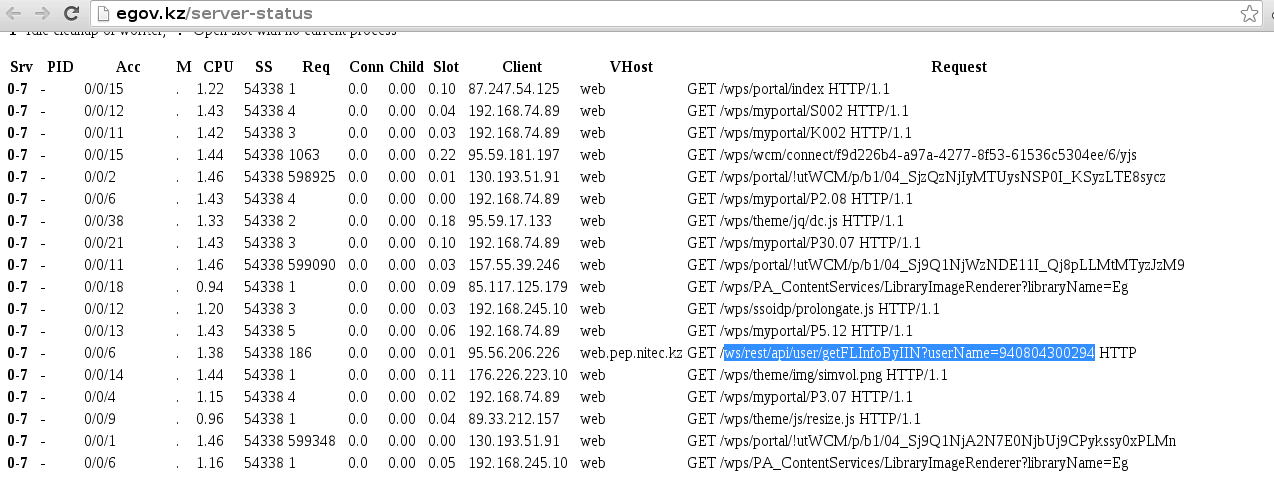
Further more interesting. A direct link could download the document without authorization, and this allows an attacker to conduct a brute-force attack to retrieve all the issued documents, or documents of a specific person on his IIN. As a result, all documents issued by the e-government, regardless of the request processing point (at home at their own computer, Population Service Center, mobile device) were available to third parties.
So, using a minor error, which many mistakenly consider as such, you can make a large-scale attack on the theft of documents. All it takes is some free time and a simple script to automate the process.
A small counter was written for analysis, which showed that it was possible to download more than 50,000 documents (or about 10GB) of citizens of the Republic of Kazakhstan for a week. And these are not only innocuous address references of citizens, but also various documents with sensitive information, such as certificates on the availability of real estate.
This is how the “insignificant” vulnerability due to incorrect administrator settings can lead to the merging of the citizens database.
The error described in this article was transmitted to the developers of the ES and corrected; accordingly, the exploitation of the vulnerability is no longer possible. In view of this, we believe this publication will not entail the leakage of anyone's personal data. But we can not guarantee that the documents of our citizens were no longer received by the attackers and were not saved for any action.
So, on the e-government portal, when requesting this or that help, the user receives a direct link to the document in * .PDF format, which looks like this:
')
http://egov.kz/shepDownloadPdf?favorId( )&iin=( )The admin error is the overall availability of Server Status, which in turn reveals all transmitted GET requests (shown in the figure below).

Further more interesting. A direct link could download the document without authorization, and this allows an attacker to conduct a brute-force attack to retrieve all the issued documents, or documents of a specific person on his IIN. As a result, all documents issued by the e-government, regardless of the request processing point (at home at their own computer, Population Service Center, mobile device) were available to third parties.
So, using a minor error, which many mistakenly consider as such, you can make a large-scale attack on the theft of documents. All it takes is some free time and a simple script to automate the process.
A small counter was written for analysis, which showed that it was possible to download more than 50,000 documents (or about 10GB) of citizens of the Republic of Kazakhstan for a week. And these are not only innocuous address references of citizens, but also various documents with sensitive information, such as certificates on the availability of real estate.
This is how the “insignificant” vulnerability due to incorrect administrator settings can lead to the merging of the citizens database.
Source: https://habr.com/ru/post/281849/
All Articles