How a secure printing system is implemented on a follow-me printing device

Suppose you are a bank, an oil company, or just a paranoiac. You want to:
- Cleaners, enemies, and reptilians did not take documents from printers.
- The printer’s memory has been safely cleaned after printing.
- There was no non-targeted print.
- Large tasks were automatically redirected to devices with a cheap print.
- When sending a job to print 50 times (as a panicked user often does), only one crawled out.
- That the texts were filtered by stop words, and the pictures were recognized and also not printed, if they contain confidential data (not all solutions have it).
- In rare cases, there’s also that in the documents on the fly the word “to the right” should be replaced by “to the left” in order to mislead the potential adversary.
It is expensive, but has long been used in financial institutions. There the print looks like this: you send the job to the print server, it processes the file (if necessary, sends it to the security officer for manual approval, but not all solutions also have this feature), and then gives to a specific printer only when you enter a pin and show your fingerprint directly on the device so that the document will fall into your hands. Or do not attach your smart card like a personal pass to the building.
I'll tell you more.
Entertaining statistics
According to various surveys and reports, about 20% of employees print less than 10 sheets per working day. 11–50 sheets - 61% of employees, 51–100 sheets - 12% of employees, more than 100 sheets - 7% of employees. 70% of respondents use one side of a sheet, ≈50% of respondents are not worried about the number of printed pages (according to VTsIOM). 40% of printouts could be printed in duplex and b / w (data from Nuance Communications).
')
How secure printing works
Secure printing allows you to identify each user and give him printouts only to him. At the same time, it does not matter to you where the task came from - you can send a document to print from St. Petersburg, then come to a meeting at your office in Moscow, enter the code on the printer (or log in using a card or biometrically) and get it exactly where you came. Ideally (if the timeout is sufficient and the security policies allow you to do this) it goes something like this:
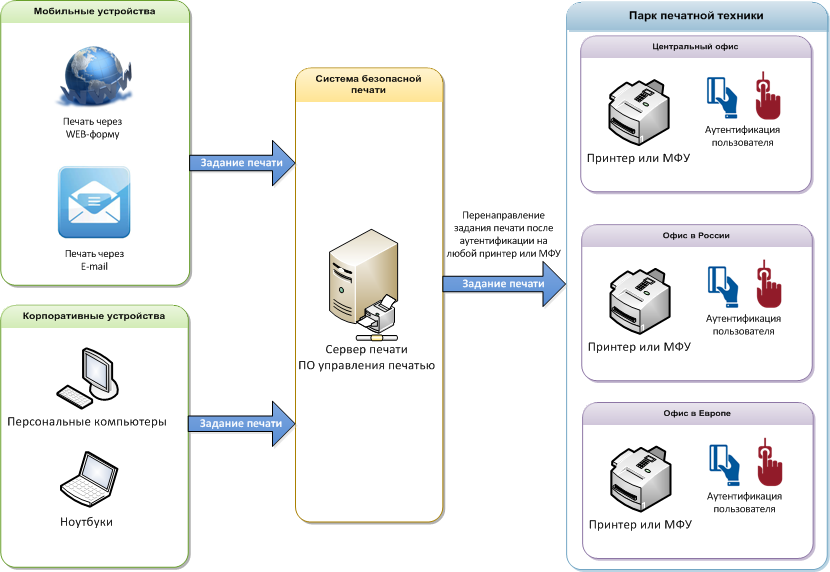
Unlike conventional printing, the following happens:
- Modern printers with built-in management software or multifunction printers (or modules for your hardware) are purchased, which provide user identification.
- All of them are united in a network managed by a print server, on which one of the secure printing systems is installed.
- When you send a print job, it enters the secure printing system. Then DLP checks the files (more on that later), and then waits for your authentication on one of the printers. As a rule, you must either enter a pin, or, in more serious cases, attach your RFID tag (pass to the building) or your finger to the biometric reader.
- After that, the printing system removes all traces of the document from the printer’s memory (especially if the HDD is used there, where document images may remain after an unexpected power outage).
Where and why is used
Given the price of introducing identifiers on printers, as a rule, the main reason is security, sometimes excessive, turning into paranoia. Price bites: from 400 euros per authentication kit for 1 device to 1000 euros depending on the type of reader. Plus, we need controllers for old printers and multifunction printers (most of the new ones have support right in the OS).
The second reason for the introduction, oddly enough, is saving. In the five-year term, it turns out cheaper. The fact is that instead of putting separate printers in each office, you can get by the storey multifunction printers and output the entire stream to them, but knowing that each document is taken personally by the employee. For example, on some floors, this is how it is implemented, and the binding goes either to the task pin or to the RFID tag of the building pass.
If the user decides not to enter or enter a pin, it will not be printed.
If the user panicked and sent 30 identical documents to print, one will be displayed (well, or 30, if specifically configured this way).
As a rule, safe printing excludes non-target printing. Given the total identification, each “left” printout has a full name.
The final effect is the loss of documents that users send to print and forget to pick up (usually those up to 20% in the stream), the lack of reprint of documents, a sharp decline in printing personal documents, cheapening due to the application of rules and conditions for redirecting tasks to more productive devices, control color printing and forced conversion to black-and-white or double-sided printing for certain user groups (document types, time, etc.), reporting.
Big brother is watching you
Joy of the information security department in total control:
- There is an option to manually confirm each document (not all solutions).
- There is a fully automatic leak control mode.
- Individual solutions have a mode of confirming only the documents causing questions from the robot.
- The user identifies himself before printing.
- There is information about who, what, where, when printed.
As a rule, the operations are as follows:
- At the “cool” integrations, a list of stop words is made at the very beginning (or the list of filters is imported from the leak prevention system - all these are DLP functions). Anything that should not be printed in the office will not be displayed at the print server level, and a notification will be created for the IB. Some systems can also be trained by specifying documents that need control, there are either the simplest neural networks by words or not very complex heuristics.
- Each document is scanned for compliance with filters, and information is collected not only from the text part: everything that can be converted to text is transformed. In particular, images are recognized, the benefit of ABBYY is a very fast OCR-module, which by its quality raises a number of questions about where else Big Brother uses it already outside the corporate market.
- When a suspicious document or a configured control rule (by groups of employees, by the length of the document, etc.), manual control is performed. The principle of escalation depends on the specific software used for the server, there are usually many settings.
- Automatic transformations can be performed with the document: for example, delete all names, underestimate the resolution of drawings to 12 dpi, give random numbers instead of financial indicators, etc. Replacing the “right” with “left” and “north” with “south” is not a joke , we had similar situations in practice. These solutions are very rare and, as a rule, very specialized.
- Printing policies are applied: for example, forced transfer to b / w for this user who does not have rights to color printing. The most common policy is to send documents over 100 pages to a printer with the lowest cost per print in the office and mailing a notification to the user about it.
- And, finally, only after that the document enters the queue to wait for the arrival of the user to the printer and two-factor authentication. Out of the box are supported AD Username / Password, PIN codes, contactless cards: HID (I, II), EM-Marine, Mifare, iClass, Hitag, Cotag, Legic, Indala, ISO, Deister, Paxton, ordinary magnetic cards, barcodes codes and biometric scanners (fingerprints).
Implementation experience
One large oil company developed a secure printing system for remote offices. The main office is in a rented business center. The building is large, several floors, the system was built centrally at once to all offices. Integration is such that wherever it is sent - you can get it in another city within 24 hours.
Multifunction printers and printers were located in printer rooms protected by access control systems, but for greater security, access controllers with multifunctional devices with authentication using a contactless card were also used.
Since the trash bin remained the last link in the printouts, shredders were installed instead of them, able to grind clips, chewing gum and even not very large parts of the human body. But not teeth. With my teeth, I had to invent something else.
A mobile print policy was set up - when an employee typed from a tablet or phone, there was a floor via a Wi-Fi router, and the task was already queued for the nearest printer.
"Their" devices, including mobile, were distinguished by certificates for Wi-Fi (802.1x).
The park was upgraded from three different sets of equipment purchased in layers with a difference of several years, and from different vendors. The freshest layer supported OS authentication technologies at the level of printing devices and multifunction printers, the rest required special controllers.
The idea of secure printing was brought by the information security, but it seemed that financiers were the most happy - they were able to tie all printing costs to specific departments. Then they also set up detailed reports on printed and copied tasks and set limits for various user groups: part of divisions were banned from color printing, limited to more than 20 pages of documents for a number of users, and only on working hours. For one of the departments, the forced conversion into b / w and forced duplex printing were set up.
The system administrators also began to smile when they realized that now the failure of the printer meant just a user’s hike to another without any special excesses. And the tantrum with an urgent replacement is no longer.
Limitations (on example of FollowMe)
Out of the box works with OS:
- Windows (starting with Win95).
- Apple Macintosh.
- AS / 400 iSeries.
- LINUX / UNIX.
- Other OS with LPR protocol support.
There is integration with Windows Active Directory, Novell eDirectory, OpenLDAP.
For solutions, for example, Nuance vendor needs a server with the following parameters: Windows 2003 Server SP2 (32/64 bit), Windows 2008 Server with Service Pack 1 (32/64 bit) or Windows Server 2008 R2 server (32/64 bit). Analogue Intel Xeon 64 for performance, at least 1 GB of free RAM (minimum 4 GB is recommended), 5 GB on the HDD for print job buffering and data processing (10 GB is recommended). If users are working with OpenOffice and MS Office, then more installations will be needed on the server (in the case of MS, this means another license).
You can print the file in the usual way or via email, or give the URL through the corporate portal to the page you want to print (this is often used for mobile printing).
Links
- List of vendors:
Ringdale is one of the leaders in printing technology, a comprehensive FollowMe solution allows companies to reduce printing costs, improve printing efficiency and safety ( Ringdale FollowMe Printing );
Nuance - a transnational corporation, a manufacturer of software in the field of communications, speech and image recognition, printing, solutions: SafeCom and Equitrac ;
YSoft is a European company that specializes in managing access to printed documents using ID cards and readers, SafeQ .
HP is a leading global manufacturer of hardware and software, in particular printing equipment and printing systems, HP Access Control solutions and HP Imaging and Printing Security Center ,
ThinPrint - a good solution on the market for optimizing printing, tight integration with solutions from leading global manufacturers of terminal access technologies and virtualization, the implementation of secure printing, Personal Printing ;
MyQ is a European company specializing in print management and secure printing using access control and OCR character recognition technologies;
Artie is a Russian company, which includes ASUPiM solutions, an automated print management and monitoring system, as well as providing secure printing with OCR character recognition technologies, solutions: ASUPiM and PrintSafe .
Ubiquitech - develops a whole range of products for intelligent print management. For example, Ubiquitech EASY / VDMS Server is a ready-made server management solution for printing in SMB, HSPM / PSPM is a server solution for managing printing in large companies, Public Print solution is a solution for organizing paid printing services in libraries, airports, hotels, etc. . - My mail is OScherbakov@croc.ru.
Source: https://habr.com/ru/post/281793/
All Articles