Collecting Checkpoint Firewall Logs (OPSEC LEA)
OPSEC LEA (Log Export API) - an interface that allows you to receive logs from the management server (Checkpoint SmartCenter).
At the core of OPSEC LEA is a client-server architecture. Checkpoint SmartCenter acts as a server, which listens to incoming connections on port 18184 of the TCP (by default). The OPSEC LEA client connects to the Server at the above port and receives logs.
Fw1-loggrabber is software that supports OPSEC LEA and is designed to receive logs from management servers (Checkpoint SmartCenter - hereinafter SC). Fw1-loggrabber can output the resulting logs to the screen, redirect to a file or to a syslog.
There are versions of this software both under Linux and under Windows (under windows, syslog output is not supported).
Given:
get logs from SC and transfer them via syslog to an external syslog server.
To solve this problem, we will use the fw1-loggrabber and SC communication technology called “sslca”, which requires authentication. It is also possible to use other mechanisms, including those without authentication, which are described in the fw1-loggrabber MAN. We will use sslca firstly because it provides a more secure connection (due to authentication), and Checkpoint itself promises to continue its support in future products.
The layout of the stand is shown in the figure below.
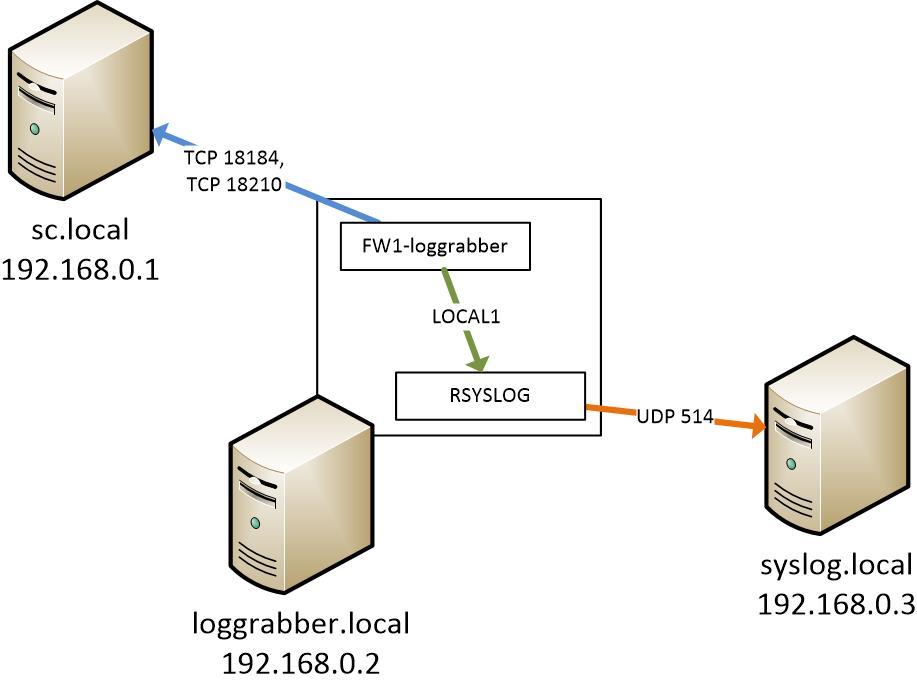
Figure 1 - Scheme stand FW1-loggrabber
')
To solve the problem will need to perform:
To install, you need to download the loggrabber software itself (https://sourceforge.net/projects/fw1-loggrabber/), unpack the archive and run the INSTALL.sh file from the root account in the unpacked folder:
The installation script copies the loggrabber files to / usr / local / fw1-loggrabber. This completes the installation. Go to the setting.
Having connected to the management console of the sc.local server using the SmartConsole graphical client, create a Syslogclient object (see Figure 2).
In the field “host” we indicate the object that represents the host loggraber.local, in the table “Client Entities” we select “LEA”. Press the "Communicate" button to set the SIC to establish a connection. The passphrase used to create the SIC needs to be remembered, it will be needed later. We copy and save the object DN in the text file - CN = Syslogclient, O = cpmgmt.hemltd.ru.ukwt9b, since You will need it in the next step.
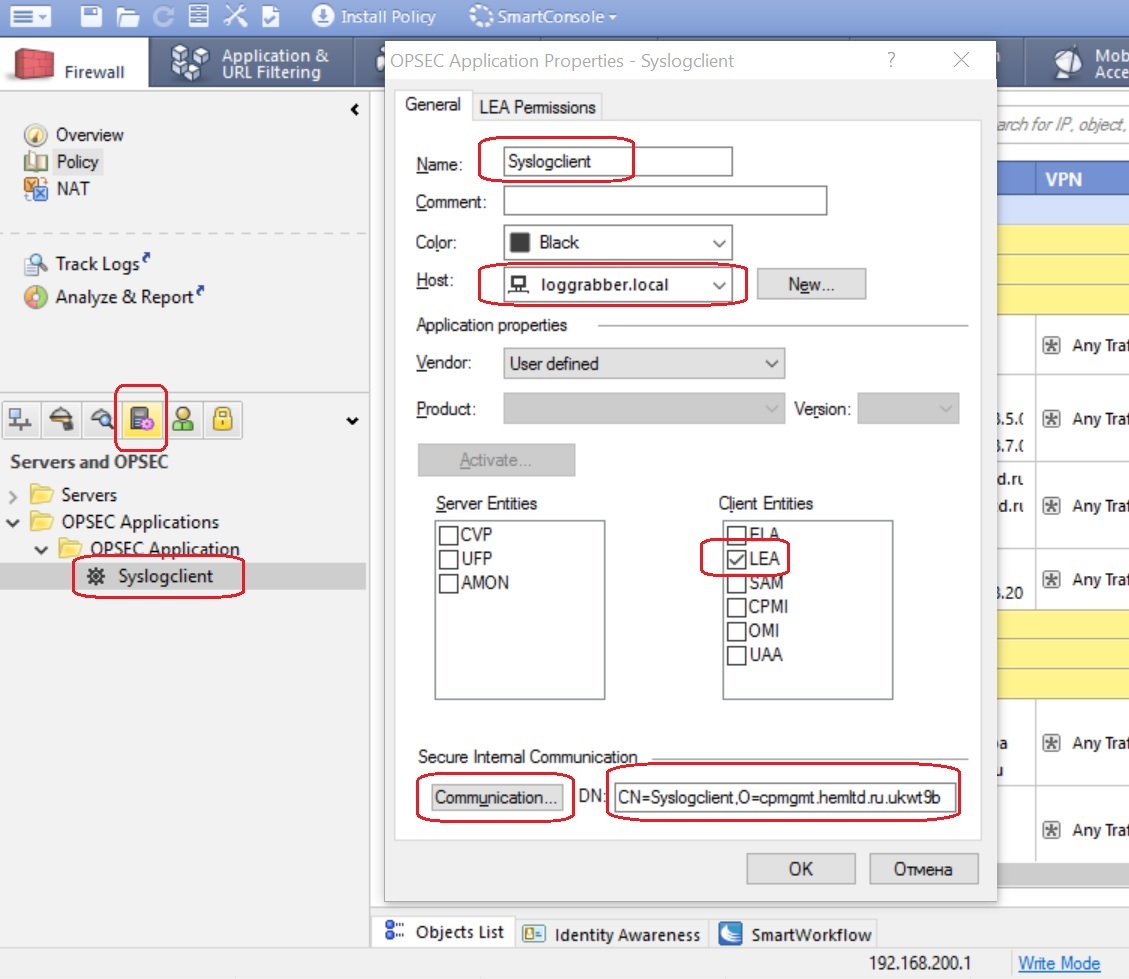
Figure 2 - Configuring the OPSEC object in Checkpoint
We also record the Checkpoint Management Server DN (sc.local), which can be found by clicking on the “Test SIC status” button in the “General” menu of the object corresponding to the Checkpoint Management Server in the graphical console interface (see Figure 3). In this example, it is: cn = cp_mgmt, o = cpmgmt.hemltd.ru.ukwt9b
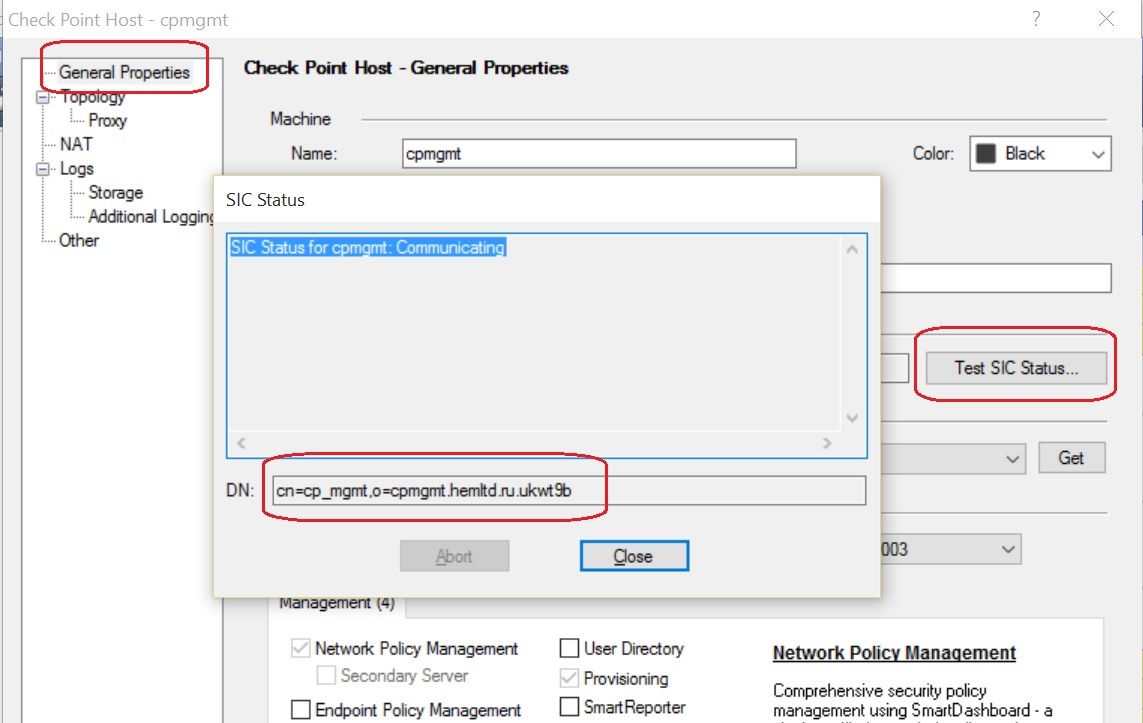
Figure 3 - Checkpoint Management Server DN (sc.local)
Connect to the Checkpoint management server (sc.local) via ssh, go into expert mode and add (or modify) the following lines to the $ FWDIR / conf / fwopsec.conf file:
Then restart Checkpoint services:
Through the Checkpoint graphical management console, we create firewall rules that allow traffic to tcp 18184 and tcp 18210 ports (tcp 18210 ports receive a certificate from the Checkpoint server loggrabber.local) in the direction from the loggrabber.local server to sc.local.
Install policy.
On the server loggrabber.local, install the opsec_pull utility from the opsec-tools package or from the OPSEC SDK. This utility is needed to establish a SIC connection between fw1-loggrabber and the Checkpoint management server.
We receive a certificate from the Checkpoint management server by the command:
The resulting file is placed in the fw1-loggraber folder: / usr / local / fw1-loggrabber
Modify the /usr/local/fw1-loggrabber/etc/lea.conf file as follows:
As lea_server ip, specify the IP address of the sc.local server. As opsec_sic_name, specify the DN of the OPSEC LEA object created in step 2. As lea_server opsec_entity_sic_name specify the Checkpoint server DN obtained in step 2. opsec_sslca_file should indicate the full path to the certificate file obtained from the Checkpoint server (described at the beginning of this stage).
Modify the /usr/local/fw1-loggrabber/etc/fw1-loggrabber.conf file as follows:
Run fw1-loggrabber:
Add to the rsyslog configuration file:
And restart rsyslog:
Thus, the logs received by fw1-loggrabber on the server loggrabber.local (192.168.0.2) from the Checkpoint server sc.local (192.168.0.1) are redirected to LOCAL1 rsyslog facilitation, which sends them to the syslog.local server ( 192.168.0.3), as shown in Figure 1.
At the core of OPSEC LEA is a client-server architecture. Checkpoint SmartCenter acts as a server, which listens to incoming connections on port 18184 of the TCP (by default). The OPSEC LEA client connects to the Server at the above port and receives logs.
Fw1-loggrabber is software that supports OPSEC LEA and is designed to receive logs from management servers (Checkpoint SmartCenter - hereinafter SC). Fw1-loggrabber can output the resulting logs to the screen, redirect to a file or to a syslog.
There are versions of this software both under Linux and under Windows (under windows, syslog output is not supported).
Given:
- Checkpoint Management Server. Software version Checkpoint - R77.30 (sc.local);
- Server with CentOS 6.6 (loggraber.local);
- Syslog server (syslog.local).
Task:
get logs from SC and transfer them via syslog to an external syslog server.
Decision:
To solve this problem, we will use the fw1-loggrabber and SC communication technology called “sslca”, which requires authentication. It is also possible to use other mechanisms, including those without authentication, which are described in the fw1-loggrabber MAN. We will use sslca firstly because it provides a more secure connection (due to authentication), and Checkpoint itself promises to continue its support in future products.
The layout of the stand is shown in the figure below.

Figure 1 - Scheme stand FW1-loggrabber
')
To solve the problem will need to perform:
- Installing fw1-loggrabber on the server loggrabber.local;
- Creating an OPSEC LEA object on the side of Checkpoint SC;
- Setting up a Checkpoint management server;
- Configure fw1-loggrabber.
1. Installing fw1-loggrabber
To install, you need to download the loggrabber software itself (https://sourceforge.net/projects/fw1-loggrabber/), unpack the archive and run the INSTALL.sh file from the root account in the unpacked folder:
# gzip –d fw1-loggrabber-1.11.1-linux.tar.gz # tar xvf fw1-loggrabber-1.11.1-linux.tar # cd fw1-loggrabber-1.11.1-linux # ./INSTALL.sh The installation script copies the loggrabber files to / usr / local / fw1-loggrabber. This completes the installation. Go to the setting.
2. Creating an OPSEC LEA Object
Having connected to the management console of the sc.local server using the SmartConsole graphical client, create a Syslogclient object (see Figure 2).
In the field “host” we indicate the object that represents the host loggraber.local, in the table “Client Entities” we select “LEA”. Press the "Communicate" button to set the SIC to establish a connection. The passphrase used to create the SIC needs to be remembered, it will be needed later. We copy and save the object DN in the text file - CN = Syslogclient, O = cpmgmt.hemltd.ru.ukwt9b, since You will need it in the next step.

Figure 2 - Configuring the OPSEC object in Checkpoint
We also record the Checkpoint Management Server DN (sc.local), which can be found by clicking on the “Test SIC status” button in the “General” menu of the object corresponding to the Checkpoint Management Server in the graphical console interface (see Figure 3). In this example, it is: cn = cp_mgmt, o = cpmgmt.hemltd.ru.ukwt9b

Figure 3 - Checkpoint Management Server DN (sc.local)
3. Configure Checkpoint Management Server
Connect to the Checkpoint management server (sc.local) via ssh, go into expert mode and add (or modify) the following lines to the $ FWDIR / conf / fwopsec.conf file:
lea_server port 0 lea server auth_port 18184 lea server auth_type sslca Then restart Checkpoint services:
# cpstop # cpstart Through the Checkpoint graphical management console, we create firewall rules that allow traffic to tcp 18184 and tcp 18210 ports (tcp 18210 ports receive a certificate from the Checkpoint server loggrabber.local) in the direction from the loggrabber.local server to sc.local.
Install policy.
4. Configure FW1-loggrabber
On the server loggrabber.local, install the opsec_pull utility from the opsec-tools package or from the OPSEC SDK. This utility is needed to establish a SIC connection between fw1-loggrabber and the Checkpoint management server.
We receive a certificate from the Checkpoint management server by the command:
# opsec_pull_cert -h 192.168.0.1 -n Syslogclient -p < , SIC 2> The resulting file is placed in the fw1-loggraber folder: / usr / local / fw1-loggrabber
Modify the /usr/local/fw1-loggrabber/etc/lea.conf file as follows:
lea_server auth_type sslca lea_server ip 192.168.0.1 lea server port 0 lea_server auth_port 18184 opsec_sic_name "CN=Syslogclient,O=cpmgmt.hemltd.ru.ukwt9b" opsec_sslca_file /usr/local/fw1-loggrabber/opsec.p12 lea_server opsec_entity_sic_name "cn=cp_mgmt,o=cpmgmt.hemltd.ru.ukwt9b" As lea_server ip, specify the IP address of the sc.local server. As opsec_sic_name, specify the DN of the OPSEC LEA object created in step 2. As lea_server opsec_entity_sic_name specify the Checkpoint server DN obtained in step 2. opsec_sslca_file should indicate the full path to the certificate file obtained from the Checkpoint server (described at the beginning of this stage).
Modify the /usr/local/fw1-loggrabber/etc/fw1-loggrabber.conf file as follows:
DEBUG_LEVEL="0" # debug, 3 FW1_LOGFILE="fw.log" # Checkpoint FW1_OUTPUT="logs" # , loggrabber Checkpoint. files, loggrabber FW1_TYPE="ng" # Checkpoint (Checkpoint FW-1 4.1) 2000 FW1_MODE="normal" # audit – , normal – ONLINE_MODE="yes" # . No – loggrabber RESOLVE_MODE="no" # DNS SHOW_FIELDNAMES="yes" # RECORD_SEPARATOR="|" # DATEFORMAT="std" # LOGGING_CONFIGURATION=syslog # loggrabber syslog, file OUTPUT_FILE_PREFIX="fw1-loggrabber" # ( ) OUTPUT_FILE_ROTATESIZE=104857600 # SYSLOG_FACILITY="LOCAL1" # syslog facility Run fw1-loggrabber:
/usr/local/fw1-loggrabber/bin/fw1-loggrabber Add to the rsyslog configuration file:
LOCAL1.* @192.168.0.3 And restart rsyslog:
/etc/init.d/rsyslog restart Thus, the logs received by fw1-loggrabber on the server loggrabber.local (192.168.0.2) from the Checkpoint server sc.local (192.168.0.1) are redirected to LOCAL1 rsyslog facilitation, which sends them to the syslog.local server ( 192.168.0.3), as shown in Figure 1.
Source: https://habr.com/ru/post/281164/
All Articles