Certification and certification: why is it necessary?
Many organizations, such as banks and insurance companies, undergo established certification and certification procedures to confirm compliance with regulatory requirements. Abroad these are requirements such as Sarbanes Oxley, HIPAA, FERC and Basel III; along with international standards, we have the requirements of the Bank of Russia, etc. Other companies consider certification and certification procedures a way of confirming the transparency of their business.

What approaches are used in attestation and certification, how is recertification organized, how is all this arranged? About this - below.
Certification or certification?
Although these terms are often used as synonyms, there are important differences between them. Certification, in fact, confirms the correctness of certain facts. For example:
In addition, the attestation process can be deeper and extend to the processes of managing user identification information and establishing users in the system, creating accounts.
Examples:
Recertification
')
Recertification is the current process of re-confirming the rights, privileges and authorities granted to the user. It guarantees the correct authorization of users for access to IT systems and information. Re-certification is very important in the field of management, in projects with high risks and strict regulatory requirements. In particular, this applies to banks and insurance companies where it is required to prove that the procedures and methods of control provide the appropriate certification and certification.
Often, these are manual procedures where personnel enter detailed access privileges for each user and each type of system.
Levels of difficulty for recertification
In terms of re-certification, there are several levels of complexity, as the table explains.
Level 1: no certification, no regular account reporting.
Level 2: re-certification is implemented as a regular manual procedure.
A typical example of level 2 is when organizations regularly manually compile lists of all employees and their rights in all systems, while the head of the department controls the lists of their employees, confirming and correcting their rights. This gives a certain degree of transparency and documentation.
The disadvantages of the approach are as follows:
Level 3: re-certification of individual rights through automated processes and requests, as well as approval procedures. Organizations can improve the correctness of assignment of rights by implementing continuous re-certification processes. The initial rights assigned to this process are controlled through well-documented request / approval procedures, and users retain the appropriate rights during recertification.
Continuous certification is best implemented using an automated identity management system (Identity Management System, IDM), which includes workflow components. This will allow to use during the recertification the same procedures that were used in the assignment of rights. Automation facilitates manual labor. The risk of obtaining an incomplete picture is eliminated, as in the second level, since well-formalized and documented processes are used for assigning rights.

However, as in the case of level 2, there is not enough transparency. The names of the rights and powers are clear to technical specialists, but not to the managers who approve them. In addition, this approach is not very convenient, since it requires individual work with a large number of rights.
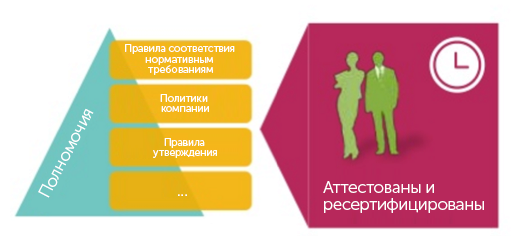
Level 4: assumes continuous recertification at several levels using business roles. Descriptive roles are used to assign rights, rights do not need to be assigned individually. This gives a number of advantages. The first is transparency. Unclear technical names are replaced by descriptive roles, so responsibility for granting rights and authority can be shifted from IT staff to business leaders. The latter understand better who needs access. This reduces the risk of assigning excess rights. In addition, the procedure for changing rights in case of organizational or technical changes is simplified.
For example, when an employee moves from finance to the marketing department, her rights to access financial data are automatically revoked and access to the required marketing information is provided.
The use of roles also helps to conduct mass certification, which may be necessary, for example, in the case of a major reorganization or for the recertification of a large amount of rights. Companies can use a phased recertification process based on roles in the organization. A manager simply needs to assign roles to employees (like “procurement manager”), and you don’t even need to know what rights are really associated with these roles.
Finally, if necessary, to increase the level of security, the recertification procedure may include definitions of business roles.
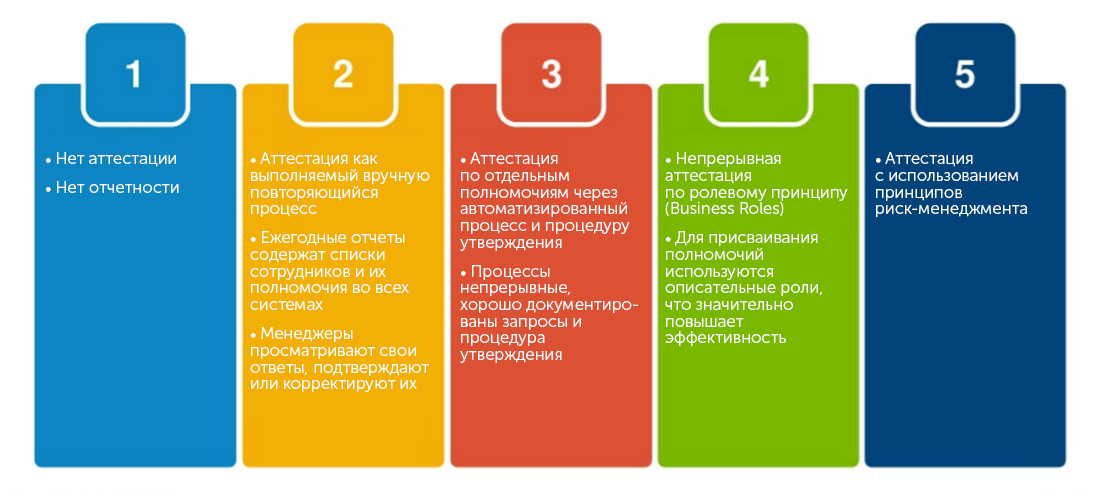
Level 5: re-certification using risk management principles.
Risk management methods are rapidly becoming part of the certification and recertification processes. Instead of analyzing all users, all access privileges or all data, organizations focus on areas of greatest risk. And for this you need to understand:
Level 5 certification systems enable organizations to answer these questions, adding an element of intelligence to the certification process.
Implementing Dell One Identity Manager Certification and Certification
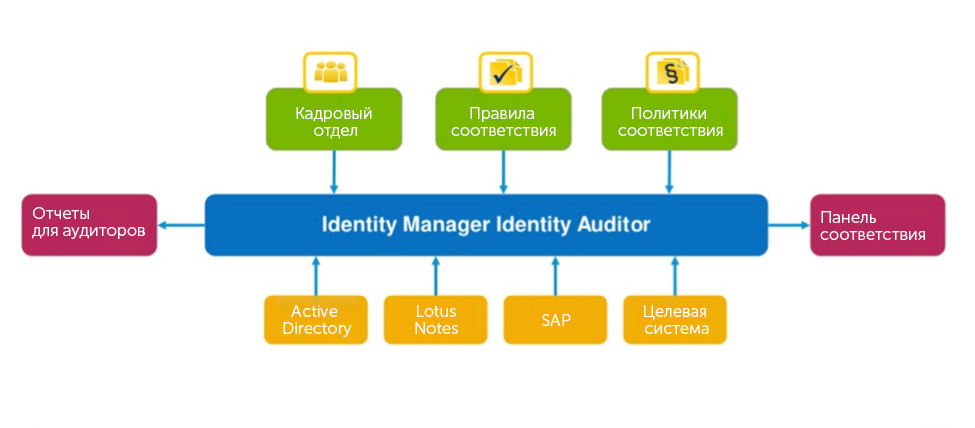
How can you implement a modern certification and certification architecture that uses business roles to manage the assignment of rights? With Dell One Identity Manager, an identity and accounting management solution designed not only for re-certification tasks, but for managing the entire life cycle of accounts. Identity Manager includes a set of processes and technologies for maintaining and updating user and account identification. It allows you to synchronize credentials, create and delete accounts, manage attributes, permissions and user rights.
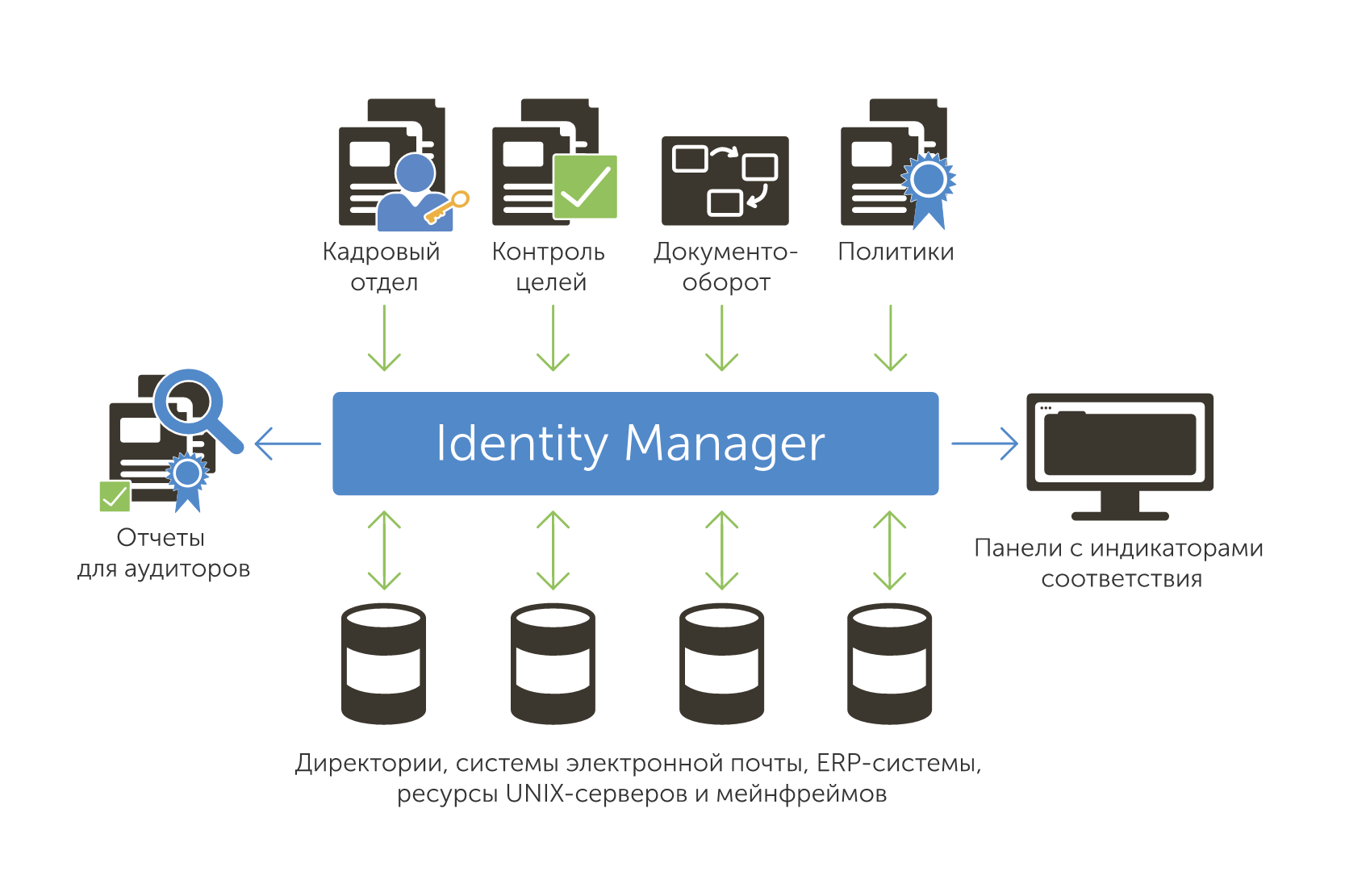
The Identity Manager architecture contains two main components:
This architecture meets stringent requirements and provides security in accordance with standards adopted in different countries, it also allows you to manage not only rights, but also more complex data than permissions, such as:
Certification and Re-certification Panels
Validation and recertification panels are useful monitoring tools that help organizations monitor attestation and recertification status as a continuous process. They show the status of many certification processes and provide answers to the following questions:

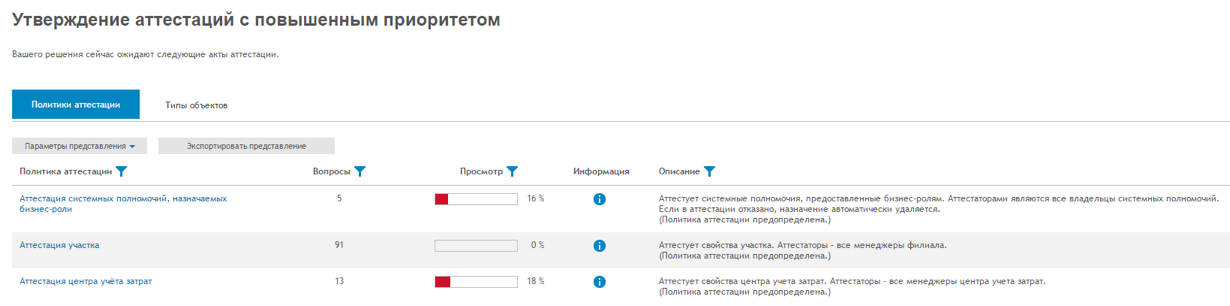
For example, the Identity Manager Evaluation and Re-certification Panels contain charts showing the status of the evaluation policies.
Conclusion
Many organizations now face the challenge of meeting regulatory requirements and reducing risk. In particular, rights tracking tools in IT systems are increasingly in demand, and organizations want to use more advanced methods to achieve a higher level of attestation and recertification. Leading companies introduce modern certification and recertification architectures, where business roles are applied to control assigned rights, and certification and recertification panels help identify potential problems and control the process.

What approaches are used in attestation and certification, how is recertification organized, how is all this arranged? About this - below.
Certification or certification?
Although these terms are often used as synonyms, there are important differences between them. Certification, in fact, confirms the correctness of certain facts. For example:
- Assigning access rights to users (through AD group membership, SAP roles, or role composition).
- Assigning specific roles to technical roles or permissions / groups, for example, assigning ACLs to an AD group or transactions and authorization codes for the SAP role.
- Assigning system roles to specific business roles.
- Assigning business roles to specific employees.
In addition, the attestation process can be deeper and extend to the processes of managing user identification information and establishing users in the system, creating accounts.
Examples:
- Validation of the rule (such as conflicting access).
- Validation of approval processes (approval) for specified IT resources.
- Confirmation that the employee is part of the organization.
Recertification
')
Recertification is the current process of re-confirming the rights, privileges and authorities granted to the user. It guarantees the correct authorization of users for access to IT systems and information. Re-certification is very important in the field of management, in projects with high risks and strict regulatory requirements. In particular, this applies to banks and insurance companies where it is required to prove that the procedures and methods of control provide the appropriate certification and certification.
Often, these are manual procedures where personnel enter detailed access privileges for each user and each type of system.
Levels of difficulty for recertification
In terms of re-certification, there are several levels of complexity, as the table explains.
| Level | Description | Restrictions |
| Level 1. No re-certification, no regular reporting. | No re-certification, no reporting | No transparency and documentation |
| Level 2. Recertification as a repetitive manual process | The organization draws up an annual report with a list of employees and their rights in all systems. Managers review these rights and confirm or adjust them for their employees. | Minimal transparency and documentation |
| Level 3. Re-certification of individual rights using automated processes and requests, approval procedures | Re-certification processes are automated and regular, well-documented request and approval procedures. | Minimal transparency, greater complexity of processing requests for rights |
| Level 4. Continuous multi-level recertification using business roles | The use of descriptive roles for assignment of rights significantly increases the efficiency of recertification | No risk management perspective |
| Level 5. Re-certification using risk management principles | An organization may analyze re-certification information in terms of risks. | Not |
Level 1: no certification, no regular account reporting.
Level 2: re-certification is implemented as a regular manual procedure.
A typical example of level 2 is when organizations regularly manually compile lists of all employees and their rights in all systems, while the head of the department controls the lists of their employees, confirming and correcting their rights. This gives a certain degree of transparency and documentation.

The disadvantages of the approach are as follows:
- It is laborious and time consuming. Often you have to export files, manually merge them and hand them to the printout of long Excel tables. And making changes to the structure of rights and powers will require recertification and a significant amount of manual operations.
- Lack of transparency often leads to unnecessary work and giving users extra rights. Often the rights in the report are described by technical terms that managers do not fully understand or do not understand at all. And this is exactly what creates risks: the rights assigned to users can exceed those they need to work.
- The risk of incomplete picture: re-certification is based on rights that do not always include rights assigned since the last certification. For example, an important combination of rights temporarily assigned to personnel after certification is not included in the report and is beyond the scope of attention.
Level 3: re-certification of individual rights through automated processes and requests, as well as approval procedures. Organizations can improve the correctness of assignment of rights by implementing continuous re-certification processes. The initial rights assigned to this process are controlled through well-documented request / approval procedures, and users retain the appropriate rights during recertification.
Continuous certification is best implemented using an automated identity management system (Identity Management System, IDM), which includes workflow components. This will allow to use during the recertification the same procedures that were used in the assignment of rights. Automation facilitates manual labor. The risk of obtaining an incomplete picture is eliminated, as in the second level, since well-formalized and documented processes are used for assigning rights.

However, as in the case of level 2, there is not enough transparency. The names of the rights and powers are clear to technical specialists, but not to the managers who approve them. In addition, this approach is not very convenient, since it requires individual work with a large number of rights.
Level 4: assumes continuous recertification at several levels using business roles. Descriptive roles are used to assign rights, rights do not need to be assigned individually. This gives a number of advantages. The first is transparency. Unclear technical names are replaced by descriptive roles, so responsibility for granting rights and authority can be shifted from IT staff to business leaders. The latter understand better who needs access. This reduces the risk of assigning excess rights. In addition, the procedure for changing rights in case of organizational or technical changes is simplified.
For example, when an employee moves from finance to the marketing department, her rights to access financial data are automatically revoked and access to the required marketing information is provided.
The use of roles also helps to conduct mass certification, which may be necessary, for example, in the case of a major reorganization or for the recertification of a large amount of rights. Companies can use a phased recertification process based on roles in the organization. A manager simply needs to assign roles to employees (like “procurement manager”), and you don’t even need to know what rights are really associated with these roles.
Finally, if necessary, to increase the level of security, the recertification procedure may include definitions of business roles.

Level 5: re-certification using risk management principles.
Risk management methods are rapidly becoming part of the certification and recertification processes. Instead of analyzing all users, all access privileges or all data, organizations focus on areas of greatest risk. And for this you need to understand:
- What systems contain the most critical data?
- Who has access to these systems?
- What powers and rights do they have to change something there?
- Does user access violate the principle of segregation of duties?
Level 5 certification systems enable organizations to answer these questions, adding an element of intelligence to the certification process.
Implementing Dell One Identity Manager Certification and Certification
How can you implement a modern certification and certification architecture that uses business roles to manage the assignment of rights? With Dell One Identity Manager, an identity and accounting management solution designed not only for re-certification tasks, but for managing the entire life cycle of accounts. Identity Manager includes a set of processes and technologies for maintaining and updating user and account identification. It allows you to synchronize credentials, create and delete accounts, manage attributes, permissions and user rights.

The Identity Manager architecture contains two main components:
- The object of certification, essentially representing an interactive report for evaluators. It is important that included in this report: it displays all relevant information, gives a clear picture of the process.

- Certification policy, which determines who, how and under what conditions should perform certification for each object.
This architecture meets stringent requirements and provides security in accordance with standards adopted in different countries, it also allows you to manage not only rights, but also more complex data than permissions, such as:
- Objects, such as processes, personal statuses, request and approval procedures, business roles, web interface versions, and regulatory compliance rules.
- Triggers, which in addition to the usual planning can add, delete, change user rights, add or disable accounts.

Certification and Re-certification Panels
Validation and recertification panels are useful monitoring tools that help organizations monitor attestation and recertification status as a continuous process. They show the status of many certification processes and provide answers to the following questions:
- How many objects are certified or recertified?
- How does this compare with previous certification and recertification processes?
- How to compare different units for work efficiency?

For example, the Identity Manager Evaluation and Re-certification Panels contain charts showing the status of the evaluation policies.
Conclusion
Many organizations now face the challenge of meeting regulatory requirements and reducing risk. In particular, rights tracking tools in IT systems are increasingly in demand, and organizations want to use more advanced methods to achieve a higher level of attestation and recertification. Leading companies introduce modern certification and recertification architectures, where business roles are applied to control assigned rights, and certification and recertification panels help identify potential problems and control the process.
Source: https://habr.com/ru/post/280962/
All Articles