Firewalls Palo Alto Networks VM-Series
Palo Alto Networks was founded in 2005 by Nir Zuk and a group of senior engineers of companies leading in the field of network security - Check Point, Cisco, NetScreen, McAfee, Juniper Networks, and is developing new-generation firewalls to monitor application performance. and users in corporate networks. The target audience of the company are large organizations engaged in education and health care, as well as financial sector companies.
The main idea of this firewall is that security policies do not apply to ports or IP addresses, but to specific directory service users and applications. Moreover, it provides tremendous opportunities for monitoring application traffic, user actions and transmitted content through the use of unique identification technologies.
')
To identify the applications used, Palo Alto Networks developed a unique traffic classification technology, called App-ID. It does not depend on ports, protocols, masking or encryption methods and is based on several detection principles: identification of the data exchange protocol and its decryption, classification of transmitted data, use of context signatures to scan application traffic, heuristic analysis of unknown data.
Using the full range of methods, the Palo Alto Networks equipment accurately isolates unknown applications and, moreover, allows you to monitor various scenarios of their use. As for corporate applications, the user can manually install classifiers and work with them.
Firewalls Palo Alto Networks offer another technology - User-ID, which is needed to identify users in the controlled networks. It supports integration with popular user repositories (Microsoft Exchange Server, Novell eDirectory, Microsoft AD) and remote access servers (Citrix XenApp, Microsoft Terminal Services), as well as an XML API for integration with third-party user repositories (proxy, wireless equipment, etc.). .).
Even through authorized applications, an authorized user may gain access to unsafe content or accidentally open access to confidential information. For this reason, it was decided that the firewall should analyze the transmitted content, and all the techniques that allow working with content are combined into one technology - Content-ID. Today, it includes full-featured IPS, URL filtering, DLP subsystem, network antivirus and AntiSpyware.
All of the above functions are embodied in all product lines of Palo Alto Networks:
- PA-5000 Series - High Performance Data Center and Service Provider Solutions
- PA-4000, PA-3000, PA-2000 Series - solutions of different performance for use in large companies
- PA-500, PA-200 - junior models for use in branches and small companies
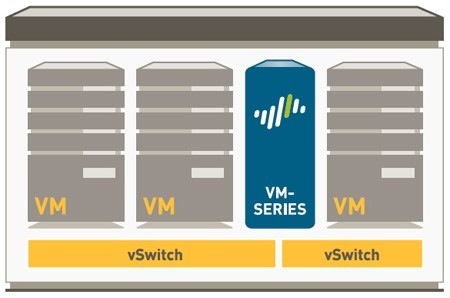
- VM-Series - a virtual firewall series that allows you to get all the capabilities of Palo Alto Networks solutions without the need to buy expensive equipment and easily integrates into VMware virtual infrastructure
Firewalls Palo Alto Networks of the VM series were initially focused on protecting virtual infrastructure from external and internal threats, and today they are actively used both in software data centers and in various clouds - private, public, hybrid.
Palo Alto Networks VM Series is running the PAN-OS operating system, which manages the hardware and software components of the Palo Alto Networks firewall. It supports a huge number of functions and services that provide a guaranteed reliable and secure environment. Also in PAN-OS, the control and traffic processing logic is separated, which makes it possible to maintain controllability by the firewall even in the event of a sharp increase in traffic.
If you need to manage multiple devices of Palo Alto Networks, you can use the specialized management platform Palo Alto Networks Panorama. Panorama is a reliable centralized management tool and allows you to monitor network activity.
With Panorama, you can manage a distributed network of physical and / or virtual firewalls of Palo Alto Networks centrally, while monitoring traffic across each deployed firewall and managing configurations and security policies.

Another tool worth attention is VMware NSX - a network virtualization platform for a virtual data center that is responsible for creating networks on existing network equipment. NSX allows you to create a flexible pool of network resources, deploy fully independent software networks, and apply virtualization principles to your network infrastructure.
An important component of VMware NSX are the components of the VMware NSX Service Composer and VMware NSX Distributed Firewall (DFW). VMware NSX DFW is a distributed firewall implemented in the context of the NSX itself. It provides stateful filtering capabilities and operates at the hypervisor core level, which provides high performance.
The firewall is managed through the vCenter user interface. The rules created in the DFW can be set at the VM, cluster, port group, DVS, logical switches, and so on. NSX DFW supports vMotion, and the current active connections remain intact at the time of the workload.
The embedded VMware NSX Service Composer component defines a new use pattern for networks and security services. It allows you to create multi-level security policies that are independent of the current infrastructure and the specified topology.
Security policies are assigned to virtual machine groups and automatically applied to new VMs added to the group. It turns out that in Service Composer you can create security groups (Security Group) and security policies (Policy Group).
When creating security groups, the administrator can choose between static and dynamic groups that include or exclude objects such as virtual machines, vNIC, vSphere clusters, logical switches, and so on.
As for Security Policy (SP), they determine the network and security policies applied to a specific security group. For example, SP can be created to redirect to Palo Alto Networks VM-Series of any type of traffic. For a security policy to work, it must be tied to a group or set of security groups.
In one of the articles of our blog, we looked at a practical example related to the configuration of dynamic security policies and the elimination of detected errors.

In a fictional organization, three virtual machines of the HR department were deployed, two of which acted as a web server, and one as a database server. Each of the virtual machines was connected to the same logical switch (VXLAN).
Traffic protection was provided as follows: the traffic from the web server to the database server was covered by the Palo Alto Networks VM series firewall, and the traffic from the web server to the web server was NSX DFW.
A detailed guide to the analysis of all the problems you encounter can be found here .
PS Other materials from our blog on Habré:
Source: https://habr.com/ru/post/280866/
All Articles