IBM is working to strengthen information protection of "connected" cars

Cars are becoming more and more perfect day by day, and not least because of the computerization of many auto systems. Vehicles "get smarter", they are equipped with computer control systems. These systems are connected to external servers, the global network and other smart cars. Computerization of cars has gone so far that cars are now sometimes called "computers on wheels." And Martin Borrett (Martin Borrett), CTO IBM Security Europe, speaks of modern machines as "small data centers on wheels."
Like any computer system, a car can be hacked, which is what the modern car thieves are trying to do (and not unsuccessfully, it should be noted). Therefore, over time, there are more and more serious security threats. The case may not only be hijacking: hackers, in theory, have the ability to intercept the control of robotic cars, forcing such systems to carry out their own commands. The problem is becoming more urgent with an increase in the number of robots So this year it was announced that in the UK on conventional roads will begin to test unmanned trucks, and unmanned cars will appear on the roads of this (and not only) the country already in 2017.
Soon, “data centers on wheels” will become a mass phenomenon, and if you don’t think in advance about their protection, then the problem of hacking computer robots can become mass. To protect the system, according to some experts, you need not after the car is ready, but during the creation of the car, introducing appropriate security systems.
')
IBM offers a multi-layered security system for “connected” cars, including the following levels: secure identification, secure data storage, secure access and communications, tamper detection and protection, security operations and command execution.
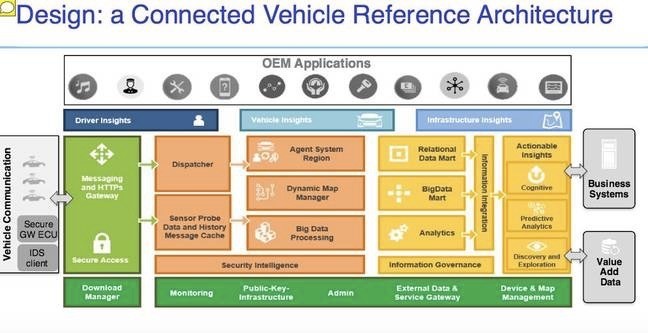
Offered car security architecture from IBM
IBM has teamed up with Giesecke & Devrient, an information security company for many years, to develop the appropriate architecture and its implementation. The purpose of the tandem - the creation of a system of cryptographic protection of the connected vehicle. The crypto chip and the system of digital keys for cars have already been submitted by partners .
IBM also developed a prototype of the IDS (Intrusion Detection System) hacking detection system, which is based on interaction with a number of company services. Information of the car in this case is transmitted to the "cloud", where it is analyzed using IBM services. This allows you to detect unusual activity of the system (which may indicate hacking).
Now the corporation is negotiating with the largest car manufacturers regarding the implementation of its system in the cars of new models. Martin Borrett at the InterConnect 2016 conference held last month in Las Vegas presented an interesting presentation on this issue .
The general report of the corporation “Driving security: Cyber assurance for next-generation vehicles” can be downloaded here.
Work on the project is underway, and very actively, so that soon we can expect the emergence of a solid car security architecture, which can (and should) be implemented during the production of cars. To introduce a similar system is necessary even before the mass appearance of robotic cars on the roads. According to the experts of the corporation, by 2026 all the cars rolling on the roads will be “connected”. And if we want to see such a future, it is necessary to understand how to protect smart cars. At the same time, buyers should trust new technologies and systems, and it’s not so easy to get such trust from them.
Source: https://habr.com/ru/post/280776/
All Articles