Bank payment infrastructure protection
On April 1, the Bank of Russia published (and this is not a joke) a review of unauthorized transfers of means of payment, in which it gave data not only on the volumes and number of unauthorized transactions made using electronic means of payment (including payment cards and remote banking systems) but also described the reasons that led to unauthorized operations and increase the risk of their implementation.
According to experts of the Bank of Russia, it is precisely the lack of security of the local infrastructure of the local area network (LAN) of money transfer operators, that is, banks, operators of payment infrastructure services, and the use of social engineering methods for their employees (for example, sending electronic messages containing malicious information). code or links to malicious sites) can lead to attacks on information infrastructure, including ATMs of credit institutions and servers systematic way such devices. And the focus in the actions of the attackers is shifting - if they had previously acted against bank customers, attacking jobs, with installed money transfer software (client-bank or Internet bank), including mobile devices, in 2015 the number targeted attacks on the operating system (payment infrastructure of credit institutions and payment systems.
In order to minimize the risks of damage from the implementation of various cyber threats, credit organizations, as well as payment clearing and operational centers of payment systems, it is necessary to strengthen control over the use of organizational measures and technical information protection tools caused by information security requirements developed and approved by the Bank of Russia, in particular , Provisions №382-. In particular, the Bank of Russia recommends that in the operation of information infrastructure facilities used when interacting with payment systems, including payment systems in which funds are transferred using payment cards, to provide:
')
Cisco supports these recommendations and, in view of the fact that the infrastructure of many credit institutions and other participants of payment systems is built on the solutions of our company, it offers to learn more about Cisco’s approach to ensuring information security of the internal network. Still, many people can talk about how to protect the perimeter, but only a few say about the security of the internal network.

A key Cisco technology that allows you to implement access control and segment payment infrastructure by various criteria (geographic, organizational, logical, technological, priority, etc.) is TrustSec, implemented on a wide range of Cisco network equipment, ranging from entry-level switches and routers and ending with kernel switches and virtual routers and switches. With this technology, you can localize any security problem, preventing it from spreading across the entire infrastructure, as well as implement the principle of minimum privileges at the network level.

However, the implementation of protection mechanisms at the network infrastructure level has always been associated with a number of difficulties, namely the need to manually configure dozens and hundreds of access control lists (Access Control List, ACL) on each network device, which could also differ (albeit slightly) in its teams. With an increase in the number of devices and the dynamism of the protected environment, this turned into a nightmare for the specialists responsible for maintaining the network infrastructure.
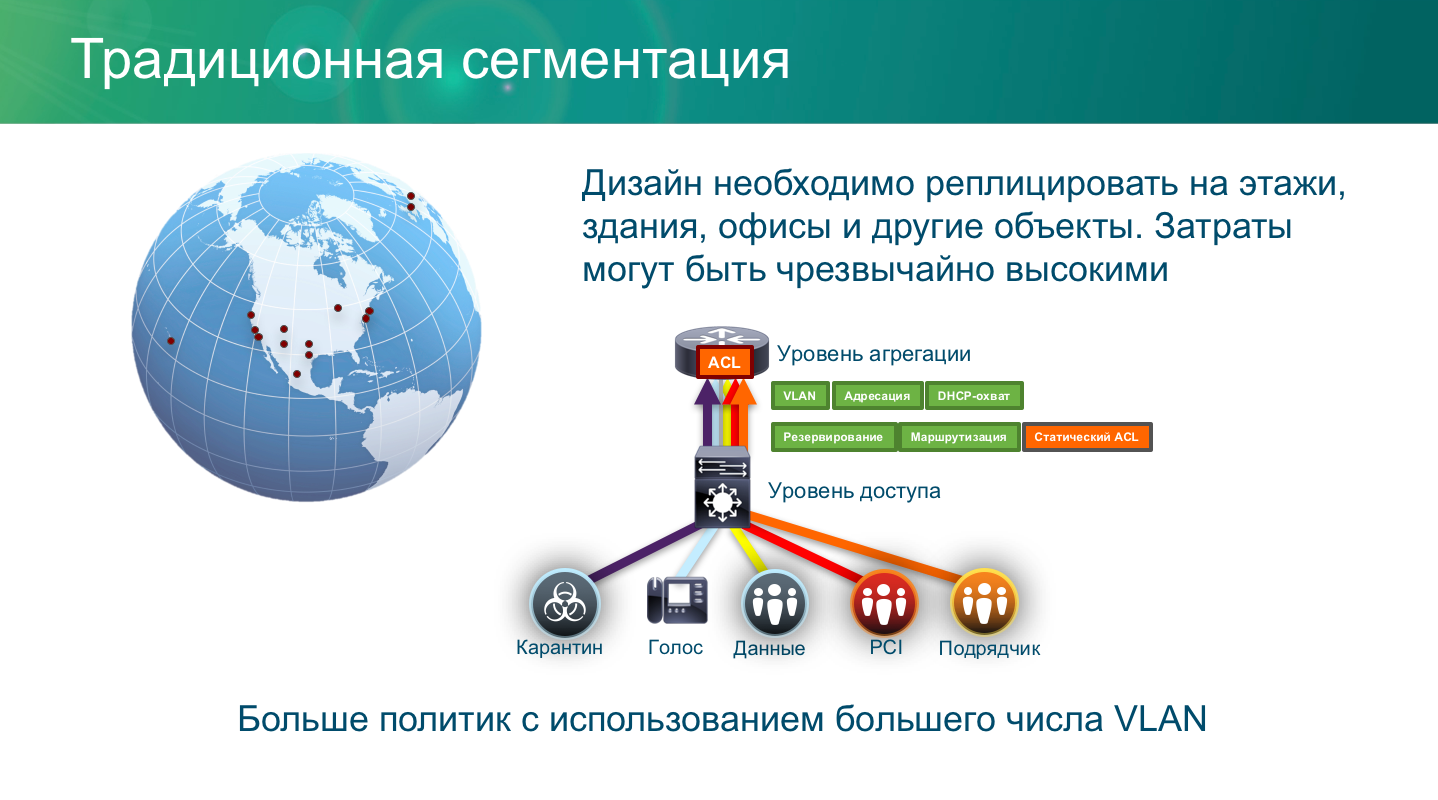
The Cisco TrustSec technology and its monitoring and management system - the Cisco Identity Service Engine (ISE) has taken the edge off the issue by fully automating all the routine tasks of setting up infrastructure security. In particular, with the help of Cisco ISE, a role-based matrix of access for bank employees (or groups of employees) to objects and groups of payment infrastructure objects is set, which itself, without manual labor, is translated into settings of a specific switch or router model. In this case, Cisco ISE also monitors the relevance of the current settings of network equipment and their compliance with the adopted security policy.

But it is not enough to segment the network, localizing information security incidents, and also to control access to objects of the payment infrastructure. It is necessary to monitor everything happening in real time and promptly respond to any abnormal situations and obvious manifestations of the actions of intruders. However, applying traditional approaches in the form of installing intrusion prevention systems or antiviruses on infrastructure facilities inside it is not always possible. Either the segment basically does not allow the installation of an intrusion detection system, or the SPAN port on the switch is already busy, or the server is already loaded with a payment application and you cannot install an antivirus on it. In the end, we should not forget about the principle of economic expediency - even though the bank owns large sums of money, this does not mean that he can spend it without looking at ensuring the security of his and his clients. We need a healthy balance between security and its value.
Cisco offers a balanced solution in the form of Cyber Threat Defense, which allows you to monitor anomalies within the bank’s network by analyzing NetFlow collected from network equipment. Originally designed to detect problems on the network, NetFlow can also be used for security purposes, as was used in Cisco Cyber Threat Defense. Using each switch or router as an intrusion detection system sensor, we can save on the protection system by implementing only a system for collecting and analyzing data from a security point of view. In fact, we are turning the entire network into an anomalous activity monitoring system.
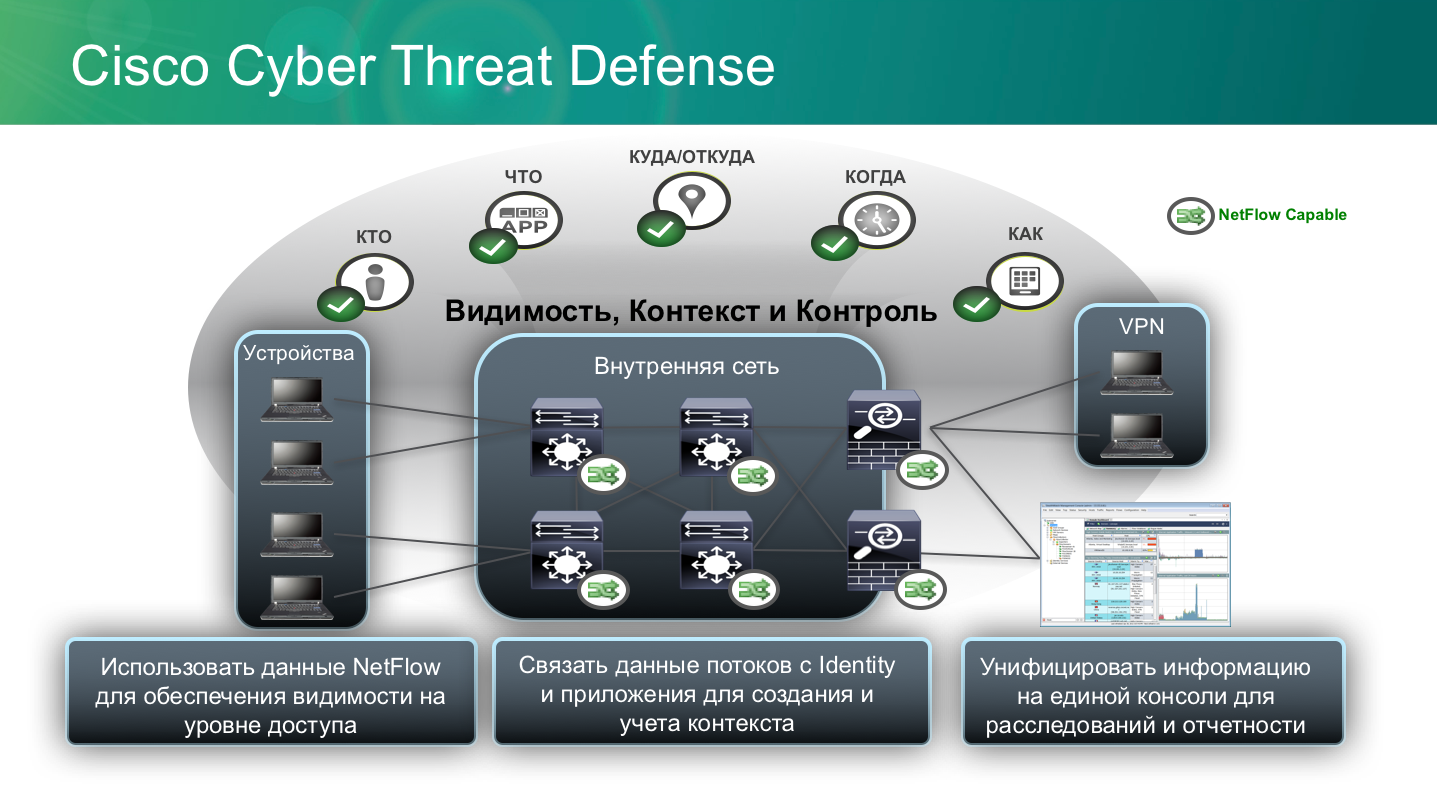
But what to do with ATMs, cashiers computers, servers that do not support NetFlow? To solve this problem, Cisco has developed a new protocol zFlow, which is designed specifically for monitoring anomalies at the terminal device level. Being implemented in the Cisco AnyConnect protection agent, this protocol can collect information about what is happening at the application layer of the payment infrastructure and pass this information to the Cyber Threat Defense solution to correlate with anomalies at the network level collected using NetFlow.

The already mentioned Cisco ISE and Cisco AnyConnect make it possible to implement another task recommended by the Bank of Russia in its review in order to increase the security of the payment infrastructure. We are talking about the control of the functioning of remedies, including countermeasures to malicious code. It is often the case that computers connecting to the bank’s network either have no protection at all, or these tools do not work, or they have an outdated configuration or an irrelevant anti-virus database. What to do in this case? To let such devices into the network or block their access? If it is allowed, then who will take responsibility if the incident starts precisely because of the incompatibility of the settings of the plug-in node with the security policy? Cisco has a technology that will help in this case - it is about the Network Admission Control or NAC, which allows you to control device access, based on their compliance assessment established in a particular organization rules. When you first connect (and also at set intervals) a computer, ATM, PoS terminal, server, or even an IP phone, surveillance camera, or ACS turnstile to the network infrastructure, the Cisco ISE system checks for installed patches, lengths of passwords used, and hard disk encryption , the current version of the antivirus database, the presence of a VPN client or other protective agent, and after passing all the checks, allows them to connect to the payment infrastructure. In case of failure of any of the “tests”, the device can be placed in quarantine, where, in automatic or automated mode, it will be brought into full compliance with the requirements of the policies, after which its access will be allowed. Such a NAC mechanism allows not only regular updating of protection tools, including and countering malicious code, but also to monitor the current status of these tools.
The last urgent task identified by the Bank of Russia in its review is monitoring signs of abnormal functioning of the payment infrastructure. In addition to the already named Cisco Cyber Threat Defense, this task can be solved with the help of other Cisco technologies and solutions that allow monitoring of various anomalies:
Unfortunately, we have to admit that there is no silver bullet in the field of information security and one solution, even the best, cannot solve the problem. And this is not the desire of the manufacturer to sell more of their decisions. Simply, the threats today are so diverse, and the networks are so dynamic and built on different principles, that a single solution simply cannot exist. Back in 1998, when I was working on ISS solutions, in their presentations as one of the future security systems and security systems desired by many security personnel, one “On” button was drawn (without the “Off” option). Almost 20 years have passed since then, and this button never appeared. Therefore, we have to use different approaches, different technologies, different solutions to protect against modern threats and fulfill all regulatory requirements. And one firewall and antivirus, as it was before, can not do ...
And in conclusion, I would again like to give a link to a material published a year ago about how we see a modern network, which itself turns into a protection system. We have been talking about this for a long time and the new review of the Bank of Russia only confirms our correctness - the network should be able to protect itself, without hinged decisions (although in some cases they are also very, very useful).
According to experts of the Bank of Russia, it is precisely the lack of security of the local infrastructure of the local area network (LAN) of money transfer operators, that is, banks, operators of payment infrastructure services, and the use of social engineering methods for their employees (for example, sending electronic messages containing malicious information). code or links to malicious sites) can lead to attacks on information infrastructure, including ATMs of credit institutions and servers systematic way such devices. And the focus in the actions of the attackers is shifting - if they had previously acted against bank customers, attacking jobs, with installed money transfer software (client-bank or Internet bank), including mobile devices, in 2015 the number targeted attacks on the operating system (payment infrastructure of credit institutions and payment systems.
In order to minimize the risks of damage from the implementation of various cyber threats, credit organizations, as well as payment clearing and operational centers of payment systems, it is necessary to strengthen control over the use of organizational measures and technical information protection tools caused by information security requirements developed and approved by the Bank of Russia, in particular , Provisions №382-. In particular, the Bank of Russia recommends that in the operation of information infrastructure facilities used when interacting with payment systems, including payment systems in which funds are transferred using payment cards, to provide:
- control of access to objects of the payment infrastructure of persons engaged in their operation and maintenance, as well as granting access rights to objects solely for the performance of official duties;
- LAN segmentation and location of payment infrastructure facilities in dedicated LAN segments;
- monitoring network activity, including accessing a proxy server, monitoring firewall configurations, and, if available, using intrusion detection and prevention tools;
- monitoring the appearance of signs of abnormal functioning of the payment infrastructure, manifested both at the application and at the network level;
- control of the operation and regular updating of software designed to protect information, including means of protection against the effects of malicious code.
')
Cisco supports these recommendations and, in view of the fact that the infrastructure of many credit institutions and other participants of payment systems is built on the solutions of our company, it offers to learn more about Cisco’s approach to ensuring information security of the internal network. Still, many people can talk about how to protect the perimeter, but only a few say about the security of the internal network.

A key Cisco technology that allows you to implement access control and segment payment infrastructure by various criteria (geographic, organizational, logical, technological, priority, etc.) is TrustSec, implemented on a wide range of Cisco network equipment, ranging from entry-level switches and routers and ending with kernel switches and virtual routers and switches. With this technology, you can localize any security problem, preventing it from spreading across the entire infrastructure, as well as implement the principle of minimum privileges at the network level.

However, the implementation of protection mechanisms at the network infrastructure level has always been associated with a number of difficulties, namely the need to manually configure dozens and hundreds of access control lists (Access Control List, ACL) on each network device, which could also differ (albeit slightly) in its teams. With an increase in the number of devices and the dynamism of the protected environment, this turned into a nightmare for the specialists responsible for maintaining the network infrastructure.

The Cisco TrustSec technology and its monitoring and management system - the Cisco Identity Service Engine (ISE) has taken the edge off the issue by fully automating all the routine tasks of setting up infrastructure security. In particular, with the help of Cisco ISE, a role-based matrix of access for bank employees (or groups of employees) to objects and groups of payment infrastructure objects is set, which itself, without manual labor, is translated into settings of a specific switch or router model. In this case, Cisco ISE also monitors the relevance of the current settings of network equipment and their compliance with the adopted security policy.

But it is not enough to segment the network, localizing information security incidents, and also to control access to objects of the payment infrastructure. It is necessary to monitor everything happening in real time and promptly respond to any abnormal situations and obvious manifestations of the actions of intruders. However, applying traditional approaches in the form of installing intrusion prevention systems or antiviruses on infrastructure facilities inside it is not always possible. Either the segment basically does not allow the installation of an intrusion detection system, or the SPAN port on the switch is already busy, or the server is already loaded with a payment application and you cannot install an antivirus on it. In the end, we should not forget about the principle of economic expediency - even though the bank owns large sums of money, this does not mean that he can spend it without looking at ensuring the security of his and his clients. We need a healthy balance between security and its value.
Cisco offers a balanced solution in the form of Cyber Threat Defense, which allows you to monitor anomalies within the bank’s network by analyzing NetFlow collected from network equipment. Originally designed to detect problems on the network, NetFlow can also be used for security purposes, as was used in Cisco Cyber Threat Defense. Using each switch or router as an intrusion detection system sensor, we can save on the protection system by implementing only a system for collecting and analyzing data from a security point of view. In fact, we are turning the entire network into an anomalous activity monitoring system.

But what to do with ATMs, cashiers computers, servers that do not support NetFlow? To solve this problem, Cisco has developed a new protocol zFlow, which is designed specifically for monitoring anomalies at the terminal device level. Being implemented in the Cisco AnyConnect protection agent, this protocol can collect information about what is happening at the application layer of the payment infrastructure and pass this information to the Cyber Threat Defense solution to correlate with anomalies at the network level collected using NetFlow.

The already mentioned Cisco ISE and Cisco AnyConnect make it possible to implement another task recommended by the Bank of Russia in its review in order to increase the security of the payment infrastructure. We are talking about the control of the functioning of remedies, including countermeasures to malicious code. It is often the case that computers connecting to the bank’s network either have no protection at all, or these tools do not work, or they have an outdated configuration or an irrelevant anti-virus database. What to do in this case? To let such devices into the network or block their access? If it is allowed, then who will take responsibility if the incident starts precisely because of the incompatibility of the settings of the plug-in node with the security policy? Cisco has a technology that will help in this case - it is about the Network Admission Control or NAC, which allows you to control device access, based on their compliance assessment established in a particular organization rules. When you first connect (and also at set intervals) a computer, ATM, PoS terminal, server, or even an IP phone, surveillance camera, or ACS turnstile to the network infrastructure, the Cisco ISE system checks for installed patches, lengths of passwords used, and hard disk encryption , the current version of the antivirus database, the presence of a VPN client or other protective agent, and after passing all the checks, allows them to connect to the payment infrastructure. In case of failure of any of the “tests”, the device can be placed in quarantine, where, in automatic or automated mode, it will be brought into full compliance with the requirements of the policies, after which its access will be allowed. Such a NAC mechanism allows not only regular updating of protection tools, including and countering malicious code, but also to monitor the current status of these tools.
The last urgent task identified by the Bank of Russia in its review is monitoring signs of abnormal functioning of the payment infrastructure. In addition to the already named Cisco Cyber Threat Defense, this task can be solved with the help of other Cisco technologies and solutions that allow monitoring of various anomalies:
- Cisco OpenDNS detects anomalies in DNS traffic, in which malicious code often hides commands received from outside, as well as data sent from the compromised node or segment.
- Cisco Cognitive Threat Analytics detects abnormal behavior in proxy logs.
- Cisco Advanced Malware Protection detects malicious activity in files that fall inside the payment infrastructure through various channels — email, Web traffic, FTP traffic, transfer via shared resources, and so on.
- Cisco FirePOWER Services detects malicious activity “on the fly” in network traffic passing through routers, firewalls or intrusion prevention systems.
Unfortunately, we have to admit that there is no silver bullet in the field of information security and one solution, even the best, cannot solve the problem. And this is not the desire of the manufacturer to sell more of their decisions. Simply, the threats today are so diverse, and the networks are so dynamic and built on different principles, that a single solution simply cannot exist. Back in 1998, when I was working on ISS solutions, in their presentations as one of the future security systems and security systems desired by many security personnel, one “On” button was drawn (without the “Off” option). Almost 20 years have passed since then, and this button never appeared. Therefore, we have to use different approaches, different technologies, different solutions to protect against modern threats and fulfill all regulatory requirements. And one firewall and antivirus, as it was before, can not do ...
And in conclusion, I would again like to give a link to a material published a year ago about how we see a modern network, which itself turns into a protection system. We have been talking about this for a long time and the new review of the Bank of Russia only confirms our correctness - the network should be able to protect itself, without hinged decisions (although in some cases they are also very, very useful).
Source: https://habr.com/ru/post/280712/
All Articles